A Novel Method For Secret Data Transmission Technique Via-PDF Free Download
THE SECRET SEVEN is the first adventure of the SECRET SEVEN SOCIETY The other books are called: SECOND The Secret Seven Adventure THIRD Well Done Secret Seven! FOURTH Secret Seven on the Trail FIFTH Go Ahead Secret Seven SIXTH Good Work Secret Seven SEVENTH Secret Seven Win Through EIGHTH Three Cheers Secret Seven NINTH Secret Seven Mystery
Bruksanvisning för bilstereo . Bruksanvisning for bilstereo . Instrukcja obsługi samochodowego odtwarzacza stereo . Operating Instructions for Car Stereo . 610-104 . SV . Bruksanvisning i original
View the Secret audit log to see which users have accessed the Secret. Delete the Secret. Change which template is being used to store and display information in this Secret. Secret Server – End User Guide Page 8 Editing a Secret To edit a Secret, navigate to its Secret V
10 tips och tricks för att lyckas med ert sap-projekt 20 SAPSANYTT 2/2015 De flesta projektledare känner säkert till Cobb’s paradox. Martin Cobb verkade som CIO för sekretariatet för Treasury Board of Canada 1995 då han ställde frågan
service i Norge och Finland drivs inom ramen för ett enskilt företag (NRK. 1 och Yleisradio), fin ns det i Sverige tre: Ett för tv (Sveriges Television , SVT ), ett för radio (Sveriges Radio , SR ) och ett för utbildnings program (Sveriges Utbildningsradio, UR, vilket till följd av sin begränsade storlek inte återfinns bland de 25 största
Hotell För hotell anges de tre klasserna A/B, C och D. Det betyder att den "normala" standarden C är acceptabel men att motiven för en högre standard är starka. Ljudklass C motsvarar de tidigare normkraven för hotell, ljudklass A/B motsvarar kraven för moderna hotell med hög standard och ljudklass D kan användas vid
LÄS NOGGRANT FÖLJANDE VILLKOR FÖR APPLE DEVELOPER PROGRAM LICENCE . Apple Developer Program License Agreement Syfte Du vill använda Apple-mjukvara (enligt definitionen nedan) för att utveckla en eller flera Applikationer (enligt definitionen nedan) för Apple-märkta produkter. . Applikationer som utvecklas för iOS-produkter, Apple .
EPA Test Method 1: EPA Test Method 2 EPA Test Method 3A. EPA Test Method 4 . Method 3A Oxygen & Carbon Dioxide . EPA Test Method 3A. Method 6C SO. 2. EPA Test Method 6C . Method 7E NOx . EPA Test Method 7E. Method 10 CO . EPA Test Method 10 . Method 25A Hydrocarbons (THC) EPA Test Method 25A. Method 30B Mercury (sorbent trap) EPA Test Method .
THE SEVEN SECRETS OF HIGHLY SUCCESSFUL RESEARCH STUDENTS 1 CONTENTS Secret 1: Care and maintenance of your supervisor 2 Secret 2: Write and show as you go 13 Secret 3: Be realistic 19 Secret 4: Say no to distractions 24 Secret 5: It s a job 29 Secret 6: Get help 33 Secret 7: You can do it! 39 Now do something 44
The Secret is no secret in this organization. It is at the heart of their success. My challenge to you is simple: learnThe Secret— then apply The Secret. If you do, your leadership and your life will be transformed forever! —John C. Maxwell Author of The 21 Irrefutable Laws of Leadership Founder of The INJOY Group x THE SECRET
och krav. Maskinerna skriver ut upp till fyra tum breda etiketter med direkt termoteknik och termotransferteknik och är lämpliga för en lång rad användningsområden på vertikala marknader. TD-seriens professionella etikettskrivare för . skrivbordet. Brothers nya avancerade 4-tums etikettskrivare för skrivbordet är effektiva och enkla att
Den kanadensiska språkvetaren Jim Cummins har visat i sin forskning från år 1979 att det kan ta 1 till 3 år för att lära sig ett vardagsspråk och mellan 5 till 7 år för att behärska ett akademiskt språk.4 Han införde två begrepp för att beskriva elevernas språkliga kompetens: BI
**Godkänd av MAN för upp till 120 000 km och Mercedes Benz, Volvo och Renault för upp till 100 000 km i enlighet med deras specifikationer. Faktiskt oljebyte beror på motortyp, körförhållanden, servicehistorik, OBD och bränslekvalitet. Se alltid tillverkarens instruktionsbok. Art.Nr. 159CAC Art.Nr. 159CAA Art.Nr. 159CAB Art.Nr. 217B1B
produktionen sker på ett reproducerbart sätt. Alla geler som produceras testas därför för att kontrollera att de upprätthåller den kvalité som krävs för produktion av läkemedel. De biologiska läkemedlen kan sorteras på olika egenskaper och för geler som separerar med
An Asahi Kasei Group Company Inledning Den här manualen innehåller handhavandeinstruktioner för webbportalen Senseair Dashboard med dess användare som tänkta läsare. Inledningsvis beskrivs några begrepp som lägger grunden för behörigheter i systemet. Därefter följer steg för steg instruktioner av alla funktioner i systemet.
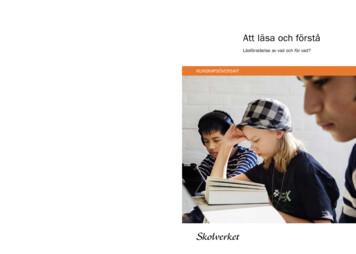
Att läsa och förstå Läsförståelse av vad och för vad? Att läsa och förstå. Skolverket. KUNSKAPSÖVERSIKT KUNSKAPSÖVERSIKT. Forskning visar att läsförståelsen påverkar möjlig heterna att tillägna sig kunskaper i alla skolämnen. Men vad kan skolan göra för att stödja elevers läs förståelse genom hela grundskolan?
This presentation and SAP's strategy and possible future developments are subject to change and may be changed by SAP at any time for any reason without notice. This document is 7 provided without a warranty of any kind, either express or implied, including but not limited to, the implied warranties of merchantability, fitness for a .
Secret Coders is a graphic novel series by Gene Luen Yang and Mike Holmes that combines logic puzzles and basic programming instruction with a page-turning mystery plot. The series is recommended for readers in grades 3 through 8 and includes four books: Secret Coders Secret Coders: Paths & Portals Secret Coders: Secrets & Sequences
Download novel the alchemist terjemahan. The alchemist (novel) plot. What books to read after the alchemist. The alchemist graphic novel free download. The alchemist novel in urdu pdf download. The alchemist novel price. The alchemist (novel) summary.
ActivityConnection.com - National Novel Writing Month: Write Your Own Novel - Page 1 of 28 Read Write National Novel Writing Month: Write Your Own Novel In November 1999, a challenge was made: write a 50,000-word novel in just 30 days. Writer Chris Baty posed this challenge to the 21 people in his writing group. The next year, another
sharing schemes by constructing threshold secret sharing A prior version appeared as “Leakage-Resilient Secret Sharing” [1] containing the same set of results. schemes that allow any set of tparties, out of nparties total, to reconstruct the secret. Furthermore, crucially, the secret is hid
4 1st verse: What and where is the secret place of the Most High? First, by way of definition, the ebrew word ba-se-ter translated secret place appears only seven times in the OT, five times in the Psalms. Along with secret place is also translated hidden part ó, òhidden place ó, shelter and covert in other scriptures. So, od ïs secret place is a .
Secret Wars 072 - Warzone - 1602 - Witch Hunter Angela 001 Secret Wars 073 - Warzone - Captain Marvel and the Carol Corps 001 Secret Wars 074 - Warzone - Mrs. Deadpool and the Howling Commandos 001 Secret Wars 075 -
Top Secret or Top Secret/SCI clearances represent the largest cohort of cleared professionals at 47%. At every career level, a Top Secret paid at least 8,000 more. TOTAL COMPENSATION BY CLEARANCE TOTAL COMPENSATION % OF RESPONDENTS % CHANGE FROM 2019 Confidential 82,707 1% 8% Secret 89,452 34% 2% Top Secret 107,872 14% 2%
Then, the low hit latency of the secret-dependent cacheline reveals the secret. For example, assuming the cacheline size is 64 bytes, if the victim loads a secret-dependent shared data array[s 64] in phase 2, where s is the secret. During phase 3, the attacker accesses array[768] with a low cache hit latency; it can infer the secret is s 768 .
The essential element of a trade secret is that it is secret. A trade secret is information that is not readily obtainable or easily discoverable by others except through the use of improper means.8 Moreover, to protect information as a trade secret, the owner must have taken steps to protect the secret that are
stood as addressing the case of a single-bit secret, we consider the case of long secrets. Speci cally, we explore the following new hypothesis: H 1.3 (SS is amortizable). For every access structure over nparties, and every su ciently long secret s, there exists a secret sharing scheme with small information ratio (e.g., sub-exponential in n).
of secret sharing is that the shares must leak absolutely no information about the secret, until the number of shares passes the threshold value. 3.2 A Simple 2-out-of-2 Scheme Believe it or not, we have already seen a simple secret-sharing scheme! In fact, it might even be best to think of one-time pad as the simplest secret-sharing scheme.
of just what a stream-of-consciousness novel really is. Numerous labels have been offered in efforts to define this unique approach: the "thought-stream novel" or 2 3 simply the "stream novel;" the "time novel;" the Shiv K. Kumar, Bergson and the Stream of Conscious ness Novel (New York, 1963), p. 2. Paul West, The Modern Novel (London, 1965 .
Novel Siti Nurbaya (kasih tak sampai) ini merupakan novel yang pertama kali mengangkat kisah permasalahan dalam perkawinan yang menghubungkan persoalan adat. Bahasa yang digunakan dalam novel ini adalah bahasa melayu baku. Novel Siti Nurbaya menyinggung tema kasih tak sampai, anti pemikiran paksa pengorbaanan, kolonialisme, dan keoderenan. Novel ini mejadi yang banyak dibaca dan digunakan .
script writer in the novels. Many novels are adapted into the movies such as, Charles Dickens’s novel Oliver . John Grisham’s novel The Firm, and Jane Austen’s novel Pride and Prejudice. Novel Pride and Prejudice, first published on January 28 1813, this is the famous of Jane Austen’s novel. Its manuscript was first written between .
The Problem with Root Cause Analysis Method A Method B Method C Method G Method E Method H Method J Method F Method D Method I No‐one can agree on "what is a root cause." Everyone says they do "root cause analysis,"yet everyone is doing something different!
The Secret Garden By Frances Hodgson Burnett Suggestions and Expectations This curriculum unit can be used in a variety of ways. Most chapters of the novel study focus on two chapters of The Secret Garden and are comprised of four different sections: Before You Read Vocabulary Building Comprehension Questions Activities
Object built-in type, 9 Object constructor, 32 Object.create() method, 70 Object.defineProperties() method, 43–44 Object.defineProperty() method, 39–41, 52 Object.freeze() method, 47, 61 Object.getOwnPropertyDescriptor() method, 44 Object.getPrototypeOf() method, 55 Object.isExtensible() method, 45, 46 Object.isFrozen() method, 47 Object.isSealed() method, 46
Gothic novel is more than just secret panels and wildly fleeing heroines and that it has contributed to the artistic development of the novel. In a recent revaluation of the Gothic novel, Robert D. Hume attempts to identify its distinctive characteristics. In order to do so, he divides the Gothic novel chronologically
Jun 07, 2021 · Barrett, Lorna Handbook For Homicide (LP) Shut-In Birchall, Katy The Secret Bridesmaid: A Novel Blackstock, Terri Aftermath Blau, Jessica Anya Mary Jane: A Novel Boulley, Angeline Fire Keeper's Daughter (YA) Cameron, W. Bruce A Dog's Courage: A Dog's Way Home Novel Chapman, Clay McLeod Whisper Down The Lane: A Novel Cherryh, C.J. Divergence
akuntansi musyarakah (sak no 106) Ayat tentang Musyarakah (Q.S. 39; 29) لًََّز ãَ åِاَ óِ îَخظَْ ó Þَْ ë Þٍجُزَِ ß ا äًَّ àَط لًَّجُرَ íَ åَ îظُِ Ûاَش
Collectively make tawbah to Allāh S so that you may acquire falāḥ [of this world and the Hereafter]. (24:31) The one who repents also becomes the beloved of Allāh S, Âَْ Èِﺑاﻮَّﺘﻟاَّﺐُّ ßُِ çﻪَّٰﻠﻟانَّاِ Verily, Allāh S loves those who are most repenting. (2:22
Secret Codes from the First World War Skill Level Grades 6-8 Learner Outcomes The learner will be able to: Understand the role secret codes played in the First World War Identify the reasons the United States joined the First World War Discuss ways to use secret codes in today’s society Educational Standard(s) Supported
Secret Management: current situation 11 Secret Management with Hashicorp's Vault Quelle / Max Mustermann best practices are widely known is usually seen as (very) important implementation is hard solutions are rare apps and frameworks not ready for modern secret management high automation still an exception (as opposed to external thread