Challenges For Cloud Networking Security-PDF Free Download
Bruksanvisning för bilstereo . Bruksanvisning for bilstereo . Instrukcja obsługi samochodowego odtwarzacza stereo . Operating Instructions for Car Stereo . 610-104 . SV . Bruksanvisning i original
10 tips och tricks för att lyckas med ert sap-projekt 20 SAPSANYTT 2/2015 De flesta projektledare känner säkert till Cobb’s paradox. Martin Cobb verkade som CIO för sekretariatet för Treasury Board of Canada 1995 då han ställde frågan
service i Norge och Finland drivs inom ramen för ett enskilt företag (NRK. 1 och Yleisradio), fin ns det i Sverige tre: Ett för tv (Sveriges Television , SVT ), ett för radio (Sveriges Radio , SR ) och ett för utbildnings program (Sveriges Utbildningsradio, UR, vilket till följd av sin begränsade storlek inte återfinns bland de 25 största
Hotell För hotell anges de tre klasserna A/B, C och D. Det betyder att den "normala" standarden C är acceptabel men att motiven för en högre standard är starka. Ljudklass C motsvarar de tidigare normkraven för hotell, ljudklass A/B motsvarar kraven för moderna hotell med hög standard och ljudklass D kan användas vid
LÄS NOGGRANT FÖLJANDE VILLKOR FÖR APPLE DEVELOPER PROGRAM LICENCE . Apple Developer Program License Agreement Syfte Du vill använda Apple-mjukvara (enligt definitionen nedan) för att utveckla en eller flera Applikationer (enligt definitionen nedan) för Apple-märkta produkter. . Applikationer som utvecklas för iOS-produkter, Apple .
UNIT 5: Securing the Cloud: Cloud Information security fundamentals, Cloud security services, Design principles, Policy Implementation, Cloud Computing Security Challenges, Cloud Computing Security Architecture . Legal issues in cloud Computing. Data Security in Cloud: Business Continuity and Disaster
sites cloud mobile cloud social network iot cloud developer cloud java cloud node.js cloud app builder cloud cloud ng cloud cs oud database cloudinfrastructureexadata cloud database backup cloud block storage object storage compute nosql
He is authorized (ISC)2 Certified Cloud Security Professional (CCSP) and Certificate of Cloud Security Knowledge (CCSK) trainer. Regarding to cloud assessment, Rafael has conducted corresponding security assessment and audit, including public and private cloud security review, cloud appli
NIST and the Cloud Security Alliance, as well as major private and public cloud providers. Cloud services provide flexibility, fast provisioning and quicker go-to-market appeal. However, because of the cloud service models employed and the technologies used to enable cloud services, cloud computing presents different security risks and challenges
Source: 2022 Cloud Security Report sponsored by (ISC) 2. The top 3 cloud security challenges for organizations are misconfiguration of the cloud platform/wrong setup, insecure interfaces/APIs, and exfiltration of sensitive data. Source: 2022 Cloud Security Report sponsored by (ISC) 2 . 1.2.2 Major Threats and Challenges Facing Services
och krav. Maskinerna skriver ut upp till fyra tum breda etiketter med direkt termoteknik och termotransferteknik och är lämpliga för en lång rad användningsområden på vertikala marknader. TD-seriens professionella etikettskrivare för . skrivbordet. Brothers nya avancerade 4-tums etikettskrivare för skrivbordet är effektiva och enkla att
Den kanadensiska språkvetaren Jim Cummins har visat i sin forskning från år 1979 att det kan ta 1 till 3 år för att lära sig ett vardagsspråk och mellan 5 till 7 år för att behärska ett akademiskt språk.4 Han införde två begrepp för att beskriva elevernas språkliga kompetens: BI
**Godkänd av MAN för upp till 120 000 km och Mercedes Benz, Volvo och Renault för upp till 100 000 km i enlighet med deras specifikationer. Faktiskt oljebyte beror på motortyp, körförhållanden, servicehistorik, OBD och bränslekvalitet. Se alltid tillverkarens instruktionsbok. Art.Nr. 159CAC Art.Nr. 159CAA Art.Nr. 159CAB Art.Nr. 217B1B
produktionen sker på ett reproducerbart sätt. Alla geler som produceras testas därför för att kontrollera att de upprätthåller den kvalité som krävs för produktion av läkemedel. De biologiska läkemedlen kan sorteras på olika egenskaper och för geler som separerar med
An Asahi Kasei Group Company Inledning Den här manualen innehåller handhavandeinstruktioner för webbportalen Senseair Dashboard med dess användare som tänkta läsare. Inledningsvis beskrivs några begrepp som lägger grunden för behörigheter i systemet. Därefter följer steg för steg instruktioner av alla funktioner i systemet.
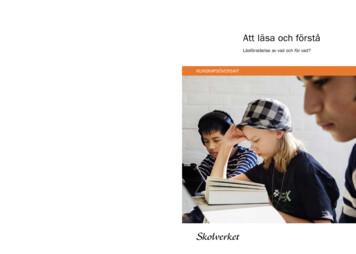
Att läsa och förstå Läsförståelse av vad och för vad? Att läsa och förstå. Skolverket. KUNSKAPSÖVERSIKT KUNSKAPSÖVERSIKT. Forskning visar att läsförståelsen påverkar möjlig heterna att tillägna sig kunskaper i alla skolämnen. Men vad kan skolan göra för att stödja elevers läs förståelse genom hela grundskolan?
This presentation and SAP's strategy and possible future developments are subject to change and may be changed by SAP at any time for any reason without notice. This document is 7 provided without a warranty of any kind, either express or implied, including but not limited to, the implied warranties of merchantability, fitness for a .
Chapter 6 Security in the Cloud 153 6.1 Chapter Overview 153 6.2 Cloud Security Challenges 158 6.3 Software-as-a-Service Security 162 6.3.1 Security Management (People) 164 6.3.2 Security Governance 165 6.3.3 Risk Management 165 6.3.4 Risk Assessment 165 6.3.5 Security Portfolio Management 166 6.3.6 Security Awareness 166
Acquiring this cloud security certification is a proof to the world that you have gained deep knowledge and hands-on experience on cloud security architecture, design, operations and . Plan Disaster Recovery (DR) and Business Continuity (BC) 4. Cloud Application Security Processes involving cloud software assurance and validation; and the use of
3 Cloud Computing Attacks a. Side channel attacks b. Service Hijacking c. DNS attacks d. Sql injection attacks e. Wrapping attacks f. Network sniffing g. Session ridding h. DOS / DDOS attacks 4 Securing Cloud computing a. Cloud security control layers b. Responsibilites in Cloud Security c. OWASP top 10 Cloud Security 5 Cloud Security Tools a.
Cloud security concerns - While adoption of cloud computing continues to surge, security concerns are showing no signs of abating. Reversing a multi-year downward trend, nine out of ten cybersecurity professionals confirm they are concerned about cloud security, up 11 percentage points from last year's cloud security survey. The top three cloud
THE WHITE BOOK OF Cloud Security Contents Preface 4 Acknowledgments 5 1: Is Cloud Computing Secure? 6 2: Cloud Security Simplified 14 3: Questions of Confidentiality 20 4: Ensuring Integrity 26 5: The Risk of Service Disruption 32 6: Putting It All Together 36 7: Data is King 40 8: The Cloud-Friendly Security Team 44 9: The Cloud Security Checklist 48 10: The Final Word on Cloud Security 54
When it comes to security, not all cloud providers . are created equal. If you find a cloud provider that is committed to data security—a provider with a security-first design—then improved security can . be a reason for you to move to the cloud. "We have invested in Oracle's security cloud services to enhance our ability to
Cisco Meraki: a complete cloud-managed networking solution - Wireless, switching, security, MDM, phones and cameras centrally managed over the web - Built from the ground up for cloud management - Integrated hardware, software, and cloud services Leader in cloud-managed networking - Among Cisco’s fastest-growing portfolios: over 100% annual .
Cisco Meraki: a complete cloud-managed networking solution - Wireless, switching, security, device management, voice, and cameras centrally managed over the web - Built from the ground up for cloud management - Integrated hardware, software, and cloud services Leader in cloud-managed networking
6. Broadly apply SDN principles to all networking and net-work services including security—from the data center and enterprise campus to the mobile and wireline networks used by service providers. THE CHALLENGES WITH NETWORKING SOFTWARE WHAT IS SDN? For the past year, software-defined networking (SDN) has been the buzz of the networking world.
Security in the cloud is a shared responsibility between the customer and the cloud provider like AWS, Azure, or Google. It requires users to secure everything in the cloud, while the cloud provider ensures the security of the cloud itself. In other words, cloud providers are responsible for securing the underlying
FlexPod Hybrid Cloud for Google Cloud Platform with NetApp Cloud Volumes ONTAP and Cisco Intersight TR-4939: FlexPod Hybrid Cloud for Google Cloud Platform with NetApp Cloud Volumes ONTAP and Cisco Intersight Ruchika Lahoti, NetApp Introduction Protecting data with disaster recovery (DR) is a critical goal for businesses continuity. DR allows .
Cloud bursting is the simplest and most common hybrid/multi-cloud cloud model scenario, in which an application that is executing in a private cloud bursts into a public cloud when the demand for computing capacity spikes. The advantage of such a hybrid cloud deployment from a cloud
Dell EMC Networking S4148F-ON 2.2 Dell EMC Networking S4248FB-ON The Dell EMC Networking S4248FB-ON is a 1-RU, multilayer switch with forty 10GbE ports, two 40GbE ports, and six 10/25/40/50/100GbE ports. Two S4248FB-ON switches are used as leaf switches in the examples in this guide. Dell EMC Networking S4248FB-ON 2.3 Dell EMC Networking Z9100-ON
Networking Fundamentals » Volume 5, TCP/IP Networking Page 3 SECTIoN 2 Networking Models The OSI model and the TCP/IP model are the prevalent methods to describe the interdependency of networking protocols. Both of these are conceptual models only and simply describe, not prescribe how networking
Networking 101 . Agenda Introduction Networking Defined Purpose of Networking Types of Networking Meet & Greets Recap Disney Agenda . Did You Know? Approximately 70 percent of all jobs are found through networking Most people you meet have at least 250 contacts
Docker Networking with Linux Guillaume Urvoy-Keller Reference Scenario Basic tools: bridges, VETH Basic tools 2: Networking in namespaces Minilab : Anatomy of a docker container networking environment (45 min) Docker (host-level) Networking Docker Networking Model Docker Swarm Docker Network Overlay Sources documents Laurent Bernaille blog .
Shared Services: This section covers standardized baselines to evaluate the security of cloud services. Cloud Migration: This section outlines the strategies and considerations of cloud migration, including explanations of common migration scenarios. Cloud Security Posture Management: This section defines Cloud Security Posture
cloud spectrum, and on all elements of cloud security. We mitigate the impact of a massive gap in cloud security skills, enabling knowledge transfer and the upskilling of in-house teams to help you move ahead with your cloud adoption and improve existing implementations. 4 Cloud Security Services 5
Index Terms - Security issues, Cloud Security, Cloud Architecture, Challenges, Automation of IT industry. 1. INTRODUCTION Cloud Computing has become a compelling force in the world of Information Technology. It is considered as one of the key features for data storage, security, access, reliable nature on costs.
licensed on a per virtual machine basis when sold stand-alone, and on a per-processor basis when sold as part of a VMware vCloud Suite. vCloud Networking and Security VCloud NetworkiNg aNd SeCurity StaNdard VCloud NetworkiNg aNd SeCurity adVaNCed Pricing and Licensing Price per VM 150 250 List Price (license only) 3,750 6,250
Effective Cloud security considerations for the Organisation / Service provider spans three key areas: Management Operation Technology . The German Federal Office for Information Security's security requirements for cloud computing providers Cloud security study of the Fraunhofer Institute for Secure Information .
Oracle Cloud customer deployments and uses vary; however, the cloud security shared responsibility model is inherent to the use of cloud services. In traditional on-premises data centre deployments, customers are responsible for all aspects of physical and logical security. In a cloud environment, the shared security model demonstrates how a
closely related to security; implementing privacy protection requires strong security capabilities. HUAWEI CLOUD has industry-leading experience and practice in terms of security. For details, see the HUAWEI CLOUD Security White Paper and White Paper for HUAWEI CLOUD Data Security. HUAWEI CLOUD adheres to a neutral attitude, and safeguards strict





![Notes Cloud Computing [6CS4-06] - jecrcfoundation](/img/241/unit-20i.jpg)