Cyber Entrepreneurship Ecosystem Umkeprints Umk Edu My-PDF Free Download
To define the entrepreneurship. To explain the significance of Entrepreneurship. To explain the Entrepreneurship Development. To describe the Dynamics of Entrepreneurship Development. 1.1 Need and significance of Entrepreneurship Development in Global contexts It is said that an economy is an effect for which entrepreneurship is the cause.
Cyber Vigilance Cyber Security Cyber Strategy Foreword Next Three fundamental drivers that drive growth and create cyber risks: Managing cyber risk to grow and protect business value The Deloitte CSF is a business-driven, threat-based approach to conducting cyber assessments based on an organization's specific business, threats, and capabilities.
EcoSystem Bus and supports system programming All EcoSystem Bus programming is completed by using the EcoSystem Programmer, GRAFIK Eye QS Control Unit with EcoSystem Lighting Control System, or QuantumTM Software EcoSystem Bus Wiring EcoSystem Ballast Bus terminals only acc
risks for cyber incidents and cyber attacks.” Substantial: “a level which aims to minimise known cyber risks, cyber incidents and cyber attacks carried out by actors with limited skills and resources.” High: “level which aims to minimise the risk of state-of-the-art cyber attacks carried out by actors with significant skills and .
Cyber Security Training For School Staff. Agenda School cyber resilience in numbers Who is behind school cyber attacks? Cyber threats from outside the school Cyber threats from inside the school 4 key ways to defend yourself. of schools experienced some form of cyber
the 1st Edition of Botswana Cyber Security Report. This report contains content from a variety of sources and covers highly critical topics in cyber intelligence, cyber security trends, industry risk ranking and Cyber security skills gap. Over the last 6 years, we have consistently strived to demystify the state of Cyber security in Africa.
Cyber crimes pose a real threat today and are rising very rapidly both in intensity and complexity with the spread of internet and smart phones. As dismal as it may sound, cyber crime is outpacing cyber security. About 80 percent of cyber attacks are related to cyber crimes. More importantly, cyber crimes have
the cyber ecosystem, focusing only on a technical solution ignores interactions with other systems/sub-systems operating beyond an organizational boundary. We argue that technical approaches address only a subset of cyber security risks. Savage and Schneider [7] summarize this point by highlighting that cyber security is a holistic
Cyber Security Cyber security is designed to protect systems, networks and data from cyber crimes. Effective cyber security reduces the risk of a cyber attack and protects organizations from the deliberate exploitation of its assets. Business Continuity Business continuity provides the capability to
One characteristic of the BES Cyber Asset is a real-time scoping characteristic. The time horizon that is significant for BES Cyber Systems and BES Cyber Assets subject to the application of these Version 5 CIP Cyber Security Standards is defined as that which is material to real-time operations f
Cyber Assets consisted of BES Cyber Assets16 and Protected Cyber Assets17 within a BES Cyber System18 or associated Cyber Assets outside the BES Cyber System (i.e., Electronic Access Control or Monitoring Systems (EACMS) and
impact BES Cyber Systems located at a Control Center. x Medium Impact BES Cyber Systems with External Routable Connectivity t Only applies to medium impact BES Cyber Systems with External Routable Connectivity. This also excludes Cyber Assets in the BES Cyber System that cannot be
.Digimon Story Cyber Sleuth Faq Walkthrough Playstation 4 .Digimon Story Cyber Sleuth Digivolution Guide Levels .Getting Started With A Solid Stable Of Digimon In Digimon .Koromon Evolution Chart Cyber Sleuth .Koromon Evolution Chart Cyber Sleuth .26 True To Life Digimon Cyber Sleuth Farm Guide .All 240
What is Cyber Security? The term cyber security refers to all safeguards and measures implemented to reduce the likelihood of a digital security breach. Cyber security affects all computers and mobile devices across the board - all of which may be targeted by cyber criminals. Cyber security focuses heavily on privacy and
the cyber governance strategies, and establishing the right controls and capabilities to be cyber resilient. KPMG'S CYBER GOVERNANCE AND RESILIENCE APPROACH It is essential that leaders take control of allocating resources to deal with cyber security, actively manage governance and decision making over cyber security, and build an informed and
This Future Cyber Security Landscape paper illustrates this increasing national dependency, threat and vulnerability by providing a view of a possible cyber security future. As a companion paper to the DSTO Cyber S&T Plan: Cyber 2020 Vision, it provides Australian context to strategic investment in cyber
ing. Modern power systems are thus cyber-physical power systems (CPPS). Although the coupling of these two net-works brings some convenience, the power system is more vulnerable to intricate cyber environment, which puts the CPPS at the risk of cyber attacks [1], [2]. In general, external attacks on CPPS can be divided into physical attacks, cyber
cyber attacks. Today, cyber attacks are among the most critical business risks facing corporations. A cyber attack may damage the profit, customer relations, and the reputation of a company. Accordingly, it is crucial to focus on cyber and information security in the board room. 2. Cyber competences in the Board of Directors Board members need .
- Cyber Resilience Review - Cyber Infrastructure Survey Tool Cyber Security Advisors Protective Security Advisors 3 . Presenter's Name June 17, 2003 Critical Infrastructure Cyber Community (C3) DHS launched the C3 Program in February 2014 to complement the launch of the NIST . DHS Cyber Resources - Operations Focused .
- Cyber Resilience Review - Cyber Infrastructure Survey Tool Cyber Security Advisors Protective Security Advisors 3 . Presenter's Name June 17, 2003 Critical Infrastructure Cyber Community (C3) DHS launched the C3 Program in February 2014 to complement the launch of the NIST . DHS Cyber Resources - Operations Focused .
DHS Cyber Security Programs Cyber Resilience Review (CRR) Evaluate how CIKR providers manage cyber security of significant information services and assets Cyber Infrastructure Survey Tool (C-IST) Identify and document critical cyber security information including system-level configurations and functions, cyber security threats,
With our reliance on ICT and the value of this data come risks to its security, integrity and failure. This cyber risk can either have a natural cause or be man-made, where the latter can emerge from human failure, cyber criminality (e.g. extortion, fraud), cyberwar, and . Ten Key Questions on Cyber Risk and Cyber Risk Insurance 9 Table 1 .
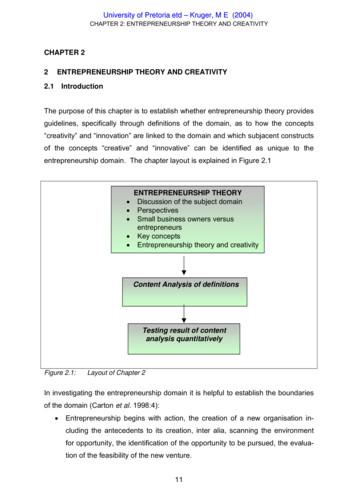
CHAPTER 2: ENTREPRENEURSHIP THEORY AND CREATIVITY ctives. epreneurs. reneurship. 3:49). thought on the meaning of entrepreneurship. One group focused on the characteris-tics of entrepreneurship (e.g. innovation, growth, uniqueness) while a second group focused on the outcomes of entrepreneurship (e.g. the creation of value).
identify and describe characterizations of technology entrepreneurship, digital techno-logy entrepreneurship, and digital entrepreneurship. With this new delineation of terms, we would like to foster discussion between researchers, entrepreneurs, and policy makers on the impact of digitization on entrepreneurship, and set a future research agenda.
Digital entrepreneurship is the phenomenon associated with digital entrepreneurial activity. While the expressions ‘ICT entrepreneurship’ and ‘digital entrepreneurship’ are widely used, we have opted to use only the expression ‘digital entrepreneurship’ in this
Academic entrepreneurship: time for a rethink? 9 As academic entrepreneurship has evolved, so too must scholarly analysis of academic entrepreneurship. There has been a rise in scholarly interest in academic entrepreneurship in the social sciences (e.g., economics, sociology, psychology, and political science) and several fields of business
Global Entrepreneurship Education II- FRAMEWORK TABLE 1: CASES BY LEARNER CATEGORY III- ENTREPRENEURSHIP EDUCATION IN CHINA The Maker Space of Tsinghua University High School: Extreme Learning Process (XLP) For Entrepreneurship Education Tsinghua x-lab: a University-based Platform For Creativity, Innovation and Entrepreneurship Education
Entrepreneurship Development and Management, Vasant Desai, HPH 2. Entrepreneurship Management, Bholanath Dutta, Excel Books 3. Entrepreneurial Development, Sangeeta Sharma, PHI 4. Entrepreneurship, Rajeev Roy, Oxford University Press. CONTENTS MODULE I – ENTREPRENEURSHIP 1. The Concept
To define corporate entrepreneurship, initially the term entrepreneurship must be defined. Secondly, it is important to define clearly what entrepreneurship in established companies means. The main problem with the preparation of scientific papers regarding entrepreneurship is the concretization of a conceptual framework (Shane & Venkataraman .
2. Corporate entrepreneurship Even if the concept of Corporate Entrepreneurship already has a few decades, the definition of the phenomenon of Corporate Entrepreneurship is far from making the unanimity of the authors. Burgelman identify that corporate entrepreneurship refers to the process whereby the firms engage in diversification
entrepreneurship orientation. This paper seeks to address this research gap by proposing an initial social entrepreneurship orientation (SEO) scale based on input from scholars in the fields of entrepreneurship and social entrepreneurship. Design/methodology/approach - This study presented employed mixed-methods and a two stage design.
3. Determining the major factors that affect the students' attitude towards entrepreneurship at PSUT through three major factors: students' awareness towards entrepreneurship, students' perception towards the effect of entrepreneurship on the individual, and students' perception towards the effect of entrepreneurship on the society.
This is "Global Entrepreneurship and Intrapreneurship", chapter 11 from the bookChallenges and Opportunities in International Business(index.html)(v. 1.0). . Who is an entrepreneur, and what is entrepreneurship? 2. What do entrepreneurs do? 3. What is entrepreneurship across borders? 4. How does entrepreneurship lead to global start-ups?
CENTRE FOR ENTERPRISE AND ENTREPRENEURSHIP STUDIES, CENTRAL UNIVERSITY OF TECHNOLOGY, FREE STATE THE SECOND INTERNATIONAL CONFERENCE ON ENTREPRENEURSHIP DEVELOPMENT (ICED) 2019 Theme: Sustainable entrepreneurship development for the 4th Industrial Revolution Conference Chair: Professor Dennis Yao Dzansi Professor of Entrepreneurship
human capital entrepreneurship articles published in these top-tier mainstream manage-ment journals. Within the entrepreneurship journals, human capital entrepreneurship research was relatively consistent from its initiation through 2006. In 2007, Entrepreneurship Theory and Practice published an eight-article special issue focusing on human .
What is entrepreneurship? Students will be able to: a. Define and give examples of entrepreneurship. b. Draw conclusions as to what they can expect to learn in a course called "Entrepreneurship and Business". c. Explain why entrepreneurship is so important to the United States economy. Readings G pp. 4-7, 15, 17-21, SW pp. 3-6
4.1 Digital Entrepreneurship Defined 64 4.2 Digital Entrepreneurship Ecosystem 64 4.3 New Business Registrations, 2015-18 67 4.4 New ICT Company Registrations in Zambia 68 4.5 Sectoral Area of Focus for Early-Stage Digital Enterprises 69 4.6 Change in the Entrepreneurship Ecosystem, percent 70
entrepreneurship in a BeeHIVE social innovation program. Apart from academic journals and articles, some of the references and evidence for the literature review and past studies were taken from book reviews, Internet browser and extensive market surveys on social entrepreneurship. The book begins with a discussion on BeeHIVE social
1999: Ecosystem-Based Fisheries Management Ecosystem Principles Advisory Panel 2013: Implementing Ecosystem-Based Management – A Report to the National Ocean Council Ocean Research Advisory Panel 2014: Ecosystem Sciences and Management Working Group – Exploration of EBF
Funding Model for a Care Ecosystem Program 27 Section 4: Care Ecosystem Protocols 31 . Alliance for Aging Research, Administration on Aging, MetLife Foundation. (2012). Care Ecosystem Toolkit 7 . The Care Ecosystem has evidence-based protocols designed to support a PWD and the needs