Navy Cyber Defense Operations Command-PDF Free Download
Command Library - String Operation Command Command Library - XML Command Command Library - Terminal Emulator Command (Per Customer Interest) Command Library - PDF Integration Command Command Library - FTP Command (Per Customer Interest) Command Library - PGP Command Command Library - Object Cloning
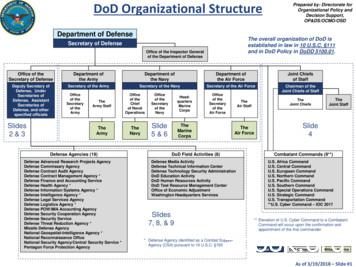
Defense Advanced Research Projects Agency. Defense Commissary Agency. Defense Contract Audit Agency. Defense Contract Management Agency * Defense Finance and Accounting Service. Defense Health Agency * Defense Information Systems Agency * Defense Intelligence Agency * Defense Legal Services Agency. Defense Logistics Agency * Defense POW/MIA .
Cyber Vigilance Cyber Security Cyber Strategy Foreword Next Three fundamental drivers that drive growth and create cyber risks: Managing cyber risk to grow and protect business value The Deloitte CSF is a business-driven, threat-based approach to conducting cyber assessments based on an organization's specific business, threats, and capabilities.
U. S. Navy Underwater Construction Teams Seabees We build -We fight -We Dive US Inventory UCT ONE, U.S. Navy (56) UCT TWO, U.S. Navy (56) 5 U.S. Army Engineer Dive Detachments, (120) What other Engineer Divers are out there? Allied Inventory Royal Thai Navy UCT (13) Philippine Navy UCT (30) Republic of Korea Navy UCT (15)
a Theater Special Operations Command North to exercise command and control of special operations forces conducting operations in the USNORTHCOM AOR. 15. NUMBER OF PAGES 111 14. SUBJECT TERMS Special Operations Forces (SOF), Homeland Security (HLS), Homeland Defense (HLD), US Northern Command (USNORTHCOM), Command and Control (C2), Joint Task
Other Shortcut Keys 28 Command Line Reference 30 Information for DaRT Notes Users 32 . Open command 39 Save command 39 Save As command 39 Close command 39 Recent Files command 39 Clear MRU List command 40 Remove Obsolete command 40 Auto Save command 40 Properties comman
Type the desired command or the command‟s alias at the command prompt. Command : LINE Command: L 2. Press ENTER on the keyboard. 3. Type an option at the command prompt. TIP: Many AutoCAD commands require you to press ENTER to complete the command. You know you are no longer in an AutoCAD command when you see a blank command line.
risks for cyber incidents and cyber attacks.” Substantial: “a level which aims to minimise known cyber risks, cyber incidents and cyber attacks carried out by actors with limited skills and resources.” High: “level which aims to minimise the risk of state-of-the-art cyber attacks carried out by actors with significant skills and .
Cyber Security Training For School Staff. Agenda School cyber resilience in numbers Who is behind school cyber attacks? Cyber threats from outside the school Cyber threats from inside the school 4 key ways to defend yourself. of schools experienced some form of cyber
the 1st Edition of Botswana Cyber Security Report. This report contains content from a variety of sources and covers highly critical topics in cyber intelligence, cyber security trends, industry risk ranking and Cyber security skills gap. Over the last 6 years, we have consistently strived to demystify the state of Cyber security in Africa.
Cyber crimes pose a real threat today and are rising very rapidly both in intensity and complexity with the spread of internet and smart phones. As dismal as it may sound, cyber crime is outpacing cyber security. About 80 percent of cyber attacks are related to cyber crimes. More importantly, cyber crimes have
Research, Development, Test and Evaluation, Defense-Wide Defense Advanced Research Projects Agency Volume 1 Missile Defense Agency Volume 2 . Defense Contract Management Agency Volume 5 Defense Threat Reduction Agency Volume 5 The Joint Staff Volume 5 Defense Information Systems Agency Volume 5 Defense Technical Information Center Volume 5 .
One characteristic of the BES Cyber Asset is a real-time scoping characteristic. The time horizon that is significant for BES Cyber Systems and BES Cyber Assets subject to the application of these Version 5 CIP Cyber Security Standards is defined as that which is material to real-time operations f
- Cyber Resilience Review - Cyber Infrastructure Survey Tool Cyber Security Advisors Protective Security Advisors 3 . Presenter's Name June 17, 2003 Critical Infrastructure Cyber Community (C3) DHS launched the C3 Program in February 2014 to complement the launch of the NIST . DHS Cyber Resources - Operations Focused .
- Cyber Resilience Review - Cyber Infrastructure Survey Tool Cyber Security Advisors Protective Security Advisors 3 . Presenter's Name June 17, 2003 Critical Infrastructure Cyber Community (C3) DHS launched the C3 Program in February 2014 to complement the launch of the NIST . DHS Cyber Resources - Operations Focused .
Jan 26, 2021 · Appendix J: Secretary of Defense Memorandum of 19 Jun 2020, Actions for Improving Diversity and Inclusion in the Department of Defense . Appendix K: Secretary of Defense Memorandum of 14 Jul 2020, Immediate Actions to Address . On 1 July 2020, the Navy stood up Task Force One Navy (TF1N), l
DOD TRAINING U.S. Cyber Command and Services Should Take Actions to Maintain a Trained Cyber Mission Force What GAO Found U.S. Cyber Command (CYBERCOM) has taken a number of steps—such as . Our report does not address the cybersecurity awareness training that is . 4: The National Mission Teams and Combat Mission Teams have support teams that
Fighters—Royal Navy, U.S. Navy, and Imperial Japanese Navy 14 FIGURE 1-2 Service Ceiling, in Feet, for Selected Fighters—Royal Navy, U.S. Navy, and Imperial Japanese Navy 15 FIGURE B-1 Stall Speed vs. Prototype Year 178 FIGURE B-2 Takeoff Weight vs. Year 179 FIGURE B-3 Roll at 25 Knots WOD vs. Year 180 Tables TABLE 2-1 Characteristics of .
Jul 31, 2020 · 3. Background. The Navy GME office at Navy Medicine Professional Development Center manages Navy GME application processes and Joint Service GME Selection Board (JSGMESB) planning for Navy Medicine. The Navy GME selection board will be held Monday,
E3 —NDSN —Navy Diver Seaman E4 —ND3 —Navy Diver Third Class E5 —ND2 —Navy Diver Second Class E6 —ND1 —Navy Diver First Class E7 —NDC —Chief Navy Diver E8 —NDCS —Senior Chief Navy Diver E9 —NDCM —M
Sep 29, 2021 · CV-67, a conventionally powered carrier, has since retired from the Navy, and all of the Navy’s aircraft carriers today are nuclear powered. Even so, Navy oilers continue to conduct UNREPs with Navy aircraft carriers to provide fuel for the carriers’ embarked air wings. Navy
from your local Navy recruiter. For many people a Navy recruiter is the first Sailor they meet. It’s the recruiter’s job to help you understand what the Navy can do for you. If the Navy is right for you, and you’re right for the Navy, your recruiter will arrange a meeting with a profess
2015-005 Navy Cash Equipment Ownership and Maintenance Responsibilities 2015-006 Recommendations for Spare Navy Cash Card Stocks—Revised 2015-007 Navy Cash System Documentation Now Available on SAILOR 2.1 2016-001 Residual Funds on Navy Cash Cards 2016-002 Treasury Navy Cash / Marine Cash Website Address Change 2016-003 Navy Cash System .
Homeland Defense, Homeland Security, Maritime Homeland Defense, Maritime Homeland Security, Joint, Navy, Command and Control, Northern Command, NORTHCOM, Defense . Prescribed by ANSI Std. 239-18. ii THIS PAGE INTENTIONALLY LEFT BLANK . iii Approved for public release; distribution is unlimited .
Apr 27, 2001 · Cleveland for inclusion in the Navy WCF financial statements. Navy Working Capital Fund. The Navy WCF finances nine primary activity groups, which provide support to the Navy and other authorized customers. For FY 2000, the Navy WCF reported 25 billion in assets, 6 billion in liabilities,
America’s Navy Reserve is an essential element of the Total Force that is America’s Navy. Wherever the important work of the Navy is being conducted in the world today, whenever the Maritime Strategy that guides those efforts is being executed, Navy Reservists are there. Seamlessl
Space, and Cyber operations. Operational C2 of cyber forces is a significant challenge that impacts the planning and integration of cyber operations at the AOC. The Joint Staff’s Transitional Cyberspace C2 Concept of Operations, released in March 2012, provides a cyber
Cyber Security Cyber security is designed to protect systems, networks and data from cyber crimes. Effective cyber security reduces the risk of a cyber attack and protects organizations from the deliberate exploitation of its assets. Business Continuity Business continuity provides the capability to
Cyber Assets consisted of BES Cyber Assets16 and Protected Cyber Assets17 within a BES Cyber System18 or associated Cyber Assets outside the BES Cyber System (i.e., Electronic Access Control or Monitoring Systems (EACMS) and
impact BES Cyber Systems located at a Control Center. x Medium Impact BES Cyber Systems with External Routable Connectivity t Only applies to medium impact BES Cyber Systems with External Routable Connectivity. This also excludes Cyber Assets in the BES Cyber System that cannot be
.Digimon Story Cyber Sleuth Faq Walkthrough Playstation 4 .Digimon Story Cyber Sleuth Digivolution Guide Levels .Getting Started With A Solid Stable Of Digimon In Digimon .Koromon Evolution Chart Cyber Sleuth .Koromon Evolution Chart Cyber Sleuth .26 True To Life Digimon Cyber Sleuth Farm Guide .All 240
What is Cyber Security? The term cyber security refers to all safeguards and measures implemented to reduce the likelihood of a digital security breach. Cyber security affects all computers and mobile devices across the board - all of which may be targeted by cyber criminals. Cyber security focuses heavily on privacy and
the cyber governance strategies, and establishing the right controls and capabilities to be cyber resilient. KPMG'S CYBER GOVERNANCE AND RESILIENCE APPROACH It is essential that leaders take control of allocating resources to deal with cyber security, actively manage governance and decision making over cyber security, and build an informed and
This Future Cyber Security Landscape paper illustrates this increasing national dependency, threat and vulnerability by providing a view of a possible cyber security future. As a companion paper to the DSTO Cyber S&T Plan: Cyber 2020 Vision, it provides Australian context to strategic investment in cyber
ing. Modern power systems are thus cyber-physical power systems (CPPS). Although the coupling of these two net-works brings some convenience, the power system is more vulnerable to intricate cyber environment, which puts the CPPS at the risk of cyber attacks [1], [2]. In general, external attacks on CPPS can be divided into physical attacks, cyber
cyber attacks. Today, cyber attacks are among the most critical business risks facing corporations. A cyber attack may damage the profit, customer relations, and the reputation of a company. Accordingly, it is crucial to focus on cyber and information security in the board room. 2. Cyber competences in the Board of Directors Board members need .
DHS Cyber Security Programs Cyber Resilience Review (CRR) Evaluate how CIKR providers manage cyber security of significant information services and assets Cyber Infrastructure Survey Tool (C-IST) Identify and document critical cyber security information including system-level configurations and functions, cyber security threats,
With our reliance on ICT and the value of this data come risks to its security, integrity and failure. This cyber risk can either have a natural cause or be man-made, where the latter can emerge from human failure, cyber criminality (e.g. extortion, fraud), cyberwar, and . Ten Key Questions on Cyber Risk and Cyber Risk Insurance 9 Table 1 .
5. Philippine Participation in Countering Global Marine Pollution 27 6. International Conventions 27 7. International Dimensions of the Ecological Issue 28 8. The US Navy: A Case Study 32 III. THE PHILIPPINE NAVY'S PRESENT STRENGTHS/CAPABILITIES 35 A. PHILIPPINE NAVY'S DEFENSE OBJECTIVES AND STRATEGIES 35 1. National Defense Objectives 35 2.
leadership. Build cyber security awareness, actions, and oversight into command daily battle rhythm, and in parallel, develop the technically competent, informed, and proactive supervisors to inculcate cyber readiness down to the deckplates. Navy Cyber Forces (CYBERFOR) N41 manages this document and