Penetration Testing And Network Defense Pearsoncmg Com-PDF Free Download
Assessment, Penetration Testing, Vulnerability Assessment, and Which Option is Ideal to Practice? Types of Penetration Testing: Types of Pen Testing, Black Box Penetration Testing. White Box Penetration Testing, Grey Box Penetration Testing, Areas of Penetration Testing. Penetration Testing Tools, Limitations of Penetration Testing, Conclusion.
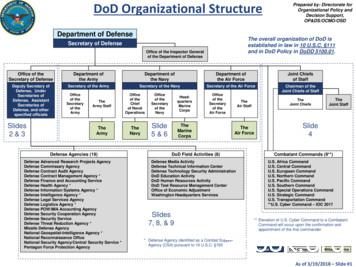
Defense Advanced Research Projects Agency. Defense Commissary Agency. Defense Contract Audit Agency. Defense Contract Management Agency * Defense Finance and Accounting Service. Defense Health Agency * Defense Information Systems Agency * Defense Intelligence Agency * Defense Legal Services Agency. Defense Logistics Agency * Defense POW/MIA .
Penetration testing also helps an organization determine how susceptible or resilient to attack it really is. The process of penetration testing involves a great deal of time and dedication to ensure a positive outcome for both the penetration tester and the organization being evaluated. Comparing penetration testing to other real-world types .
Open Web Application Security Project (OWASP) National Institute of Standards and Technology (NIST) Penetration Testing Execution Standard (PTES) What is PTES? PTES, penetration testing execution standard, as the name implies is an assessment methodology for penetration testing. It covers everything related to a penetration test.
2.1 Extent of Testing 2.0 Test Scope and Method Example Institute engaged PurpleSec to provide the following penetration testing services: Network-level, technical penetration testing against hosts in the internal networks. Network -level, technical penetration testing against internet facing hosts.
network-layer penetration test and application-layer penetration tests. There was a short informational supplement released in 2008 by the PCI Council on penetration testing, but its guidance was very general and still left much room for interpreting what a penetration test rea
The in-place penetration test using the laser particle counter is a measurement of the penetration of the total filtration system. This test incorporates the aerosol penetration from both the HEPAfilter and leaks in the filter housing or gaskets. In separate filter penetration and leak tests, the total penetration of the filtration
Penetration Testing 12/7/2010 Penetration Testing 1 What Is a Penetration Testing? Testing the security
2020 Pen Testing Report www.coresecurity.com 11 In-House Penetration Testing Efforts Figure 10: In-house penetration testing While some businesses exclusively enlist the services of a third-party penetration testing team, it is now quite common to build an in-house team, with 42% of respondents working at organizations that have one
Definitive Guide to PENETRATION TESTING. Chapter 1 Getting To Know Penetration Testing A. What is Penetration Testing? . Nmap was traditionally developed as a host discovery and port scanner in order to "map" out the a network. But can now also be used for host fingerprinting, service detection, and vulnerability .
penetration test services, and for assessors who help scope penetration tests and review final test reports. . Application-layer testing: Testing that typically includes websites, web applications, thick clients, or other applications. . The differences between penetration testing and vulnerability scanning, as required by PCI DSS, still causes
Penetration Testing Services Part 1 – Introduction and overview About this Guide This Procurement Guide (the Guide) provides practical advice on the purchase and management of penetration testing services, helping you to conduct effective, value-for-money penetration testing. It is designed to enable your organisation to plan for a
Penetration Testing Report Independent / 3rd party Web Application Vulnerability & Security Assessment / Penetration Testing / Audit (come with report) . independent security assessment and/or penetration testing services on their End Client systems to help identify any potential risks, as well as to suggest appropriate security measures to .
SOW - GoodBuy- Penetration Testing 22-23 56000 Page 6 MYA prepares standard templates used to provide a Penetration Testing Executive Management Report, and a detailed Transformation blueprint to guide in the development of a mitigation plan as part of the primary deliverable package set. Penetration Testing Executive Management Report
A quality penetration test provider will understand how a penetration test will help you meet your compliance requirements. A simple test of the vendor can quickly help you ferret out companies who do not understand your specific compliance needs. PCI DSS If you are required by the PCI DSS to perform penetration testing, ask the penetration test
SEC561 Immersive Hands-On Hacking Techniques SEC573 Python for Penetration Testers- GPYC SEC575 Mobile Device Security and Ethical Hacking - GMOB SEC617 Wireless Ethical Hacking, Penetration Testing, and Defences - GAWN Penetration Testing an Etical Hacing SEC642 Advanced Web App Penetration Testing and Ethical Hacking
A rigorous Penetration Testing program that, unlike contemporary Penetration Testing courses, teaches you how to perform an effective Penetration test across filtered . you do, your challenge is to use PowerShell and any other means to execute Silver and Gold Ticket and Kerberoasting. The machines will be configured with defenses in place .
Research, Development, Test and Evaluation, Defense-Wide Defense Advanced Research Projects Agency Volume 1 Missile Defense Agency Volume 2 . Defense Contract Management Agency Volume 5 Defense Threat Reduction Agency Volume 5 The Joint Staff Volume 5 Defense Information Systems Agency Volume 5 Defense Technical Information Center Volume 5 .
appropriate understanding or skill to perform penetration testing in-house, this document can be used in their services procurement processes to create RFP documents and evaluate the responses from potential firms offering penetration-testing services. This document breaks the process of penetration testing into logical tasks. These
Solid customer base utilizing the proposed solution, including cities similar in size and service . External Network Vulnerability Assessment and Penetration Testing Internal Network Vulnerability Assessment and Penetration Testing Network Analysis Threat Prevention/Detection Web Application Penetration Testing .
Parma Magica: Add 5 x Parma Magica Ability Takes 2 minutes to cast, lasts until sunset or sunrise. Penetration Bonus: Penetration Ability x (1 Arcane Connection Penetration Bonus Penetration Total: Casting Total Penetration Bonus – Spell Level
Certified Network Defense (CND) Outline . Module 01: Computer Network and Defense Fundamentals Network Fundamentals Computer Network Types of Network Major Network Topologies Network Components Network Interface Card
penetration tests regularly with a competent cybersecurity company. This whitepaper will first cover why organizations need to conduct penetration tests regularly that captures all the necessary objectives of an organization. Second, this paper will cover the questions you should ask when hiring a cybersecurity company for penetration testing.
penetration tester and a senior technical trainer teaching Cisco and Microsoft products. In addition, Newman spe-cializes in practicing and training certified ethical hacking and penetration testing. In his pursuit of increased knowledge, he has become certified in the following:
Part One of the Testing Framework describes the Why, What, Where and When of testing the security of web applications and Part Two goes into technical details about how to look for specific issues using source code inspection and a penetration testing (for example exactly how to find SQL Injection flaws in code and through penetration testing).
the basics of hacking and penetration testing : ethical hacking and penetration testing made easy / Patrick engebretson. p. cm. - (syngress basics series) includes bibliographical references and index. isBn 978-1-59749-655-1 (alk. paper) 1. computer security. 2. computer hackers. 3. computer software-testing. 4. computer crimes .
hands-on penetration testing experience and is a globally accepted hacking and penetration testing class available that covers the testing of modern infrastructures, operating systems and application environments while teaching the students how to document and write a penetration testing report.
sia-Pacific Defense Outlook: Key Numbers4 A 6 Defense Investments: The Economic Context 6 Strategic Profiles: Investors, Balancers and Economizers . Asia-Pacific Defense Outlook 2016 Asia-Pacific Defense Outlook 2016. 3. Asia-Pacific Defense Outlook: . two-thirds of the region's economic product and nearly 75 percent of the 2015 regional .
DEPARTMENT OF DEFENSE Defense Acquisition Regulations System 48 CFR Parts 204, 212, 213, and 252 [Docket DARS-2019-0063] RIN 0750-AJ84 Defense Federal Acquisition Regulation Supplement: Covered Defense Telecommunications Equipment or Services (DFARS Case 2018-D022) AGENCY: Defense Acquisition Regulati
French Defense - Minor Variations French Defense - Advance Variation French Defense - Tarrasch Variation: 3.Nd2 French Defense - Various 3.Nc3 Variations French Defense - Winawer Variation: 3.Nc3 Bb4 Caro-Kann Defense - Main Lines: 3.Nc3 dxe4 4.Nxe4 Caro-Kann Defense - Panov Attack
30:18 Defense — Fraud in the Inducement 30:19 Defense — Undue Influence 30:20 Defense — Duress 30:21 Defense — Minority 30:22 Defense — Mental Incapacity 30:23 Defense — Impossibility of Performance 30:24 Defense — Inducing a Breach by Words or Conduct
Penetration Testing a.k.a. Pentesting, Ethical Hacking, Red Teaming Method for evaluating the security of an information system or network by simulating attacks from malicious outsiders or insiders Exploit vulnerabilities and dig much deeper Penetration Testing is: Authorized Adversary based Ethical (for defensive purposes)
conducting Penetration Testing and analyzing and reporting on the findings. A Penetration Test is a proactive and authorized exercise to break through the security of an IT system. The main objective of a Penetration Test is to identify exploitable security weaknesses in an information system.
Penetration testers encounter many di erent systems during assessments. Penetration testers encounter systems using Docker more and more often, because of the popularity of Docker in recent years. This research discusses Docker from a security perspective and looks at how a penetration test
network penetration test. All testing performed is based on the NIST SP 800-115 Technical Guide to Information Security Testing and Assessment, OWASP Testing Guide (v4), and customized testing frameworks. Phases of penetration testing activities include the following: Planning - Customer goals are gathered and rules of engagement obtained.
Types of Attacks 3.15 Automating Internal Network Penetration Test Effort 3.16 Post Exploitation activities . . 4.6 Testing for XSS Vulnerabilities 4.7 Testing for Parameter Tampering 4.8 Testing for Weak Cryptography Vulnerabilities 4.9 Testing for Security Misconfiguration
Ethical hacking and penetration testing guide / Rafay Baloch. pages cm Includes bibliographical references and index. ISBN 978-1-4822-3161-8 (paperback) 1. Penetration testing (Computer security) I. Title. QA76.9.A25B356 2014 005.8--d
RFP for Vulnerability Assessment and Penetration Testing REQUEST FOR PROPOSAL For Vulnerability Assessment And Penetration Testing Reference Number: VAPT 02042015 MTVIEW Dated: 04/13/2015 RSU 3 Regional School Unit 3 84 School Street Unity, Maine 04988 Tel: 207 948 6136 Fax: 207 948 6173
OECM Vulnerability Assessment and Penetration Testing Services RFP #2021-381 Page 1 of 54 . VULNERABILITY ASSESSMENT AND PENETRATION TESTING SERVICES REQUEST FOR PROPOSALS NUMBER #2021-381 . OECM shall not be obligated in any manner to any Proponent whatsoever until a written Master Agreement has been duly executed with a Supplier.
The basics of hacking and penetration testing : ethical hacking and penetration testing made easy / Patrick Engebretson. e Second edition. pages cm Includes bibliographical references and index. ISBN 978--12-411644-3 1. Penetration testing (Computer security) 2. Computer hackers. 3. Computer softwareeTesting. 4. Computer crimesePrevention. I .