CISCO NETWORKING
CISCO NETWORKINGESSENTIALS
CISCO NETWORKINGESSENTIALSTroy Mc Millan
Acquisitions Editor: Agatha KimDevelopment Editor: Kelly TalbotTechnical Editor: Leslie HerronProduction Editor: Eric CharbonneauCopy Editor: Sharon WilkeyEditorial Manager: Pete GaughanProduction Manager: Tim TateVice President and Executive Group Publisher: Richard SwadleyVice President and Publisher: Neil EddeBook Designer: Happenstance Type-O-RamaCompositor: Craig W. Johnson, Happenstance Type-O-RamaProofreader: Nancy BellIndexer: Ted LauxProject Coordinator, Cover: Katherine CrockerCover Designer: Ryan SneedCover Image: Wayne Johnson/iStockPhotoCopyright 2012 by John Wiley & Sons, Inc., Indianapolis, IndianaPublished by John Wiley & Sons, Inc. Indianapolis, IndianaPublished simultaneously in CanadaISBN: 978-1-118-09759-5ISBN: 978-1-118-20383-5 (ebk)ISBN: 978-1-118-20385-9 (ebk)ISBN: 978-1-118-20384-2 (ebk)No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by anymeans, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, orauthorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 RosewoodDrive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should beaddressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 7486011, fax (201) 748-6008, or online at http://www.wiley.com/go/permissions.Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties withrespect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, includingwithout limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales orpromotional materials. The advice and strategies contained herein may not be suitable for every situation. This workis sold with the understanding that the publisher is not engaged in rendering legal, accounting, or other professionalservices. If professional assistance is required, the services of a competent professional person should be sought.Neither the publisher nor the author shall be liable for damages arising herefrom. The fact that an organization orWeb site is referred to in this work as a citation and/or a potential source of further information does not mean thatthe author or the publisher endorses the information the organization or Web site may provide or recommendationsit may make. Further, readers should be aware that Internet Web sites listed in this work may have changed or disappeared between when this work was written and when it is read.For general information on our other products and services or to obtain technical support, please contact our CustomerCare Department within the U.S. at (877) 762-2974, outside the U.S. at (317) 572-3993 or fax (317) 572-4002.Wiley also publishes its books in a variety of electronic formats and by print-on-demand. Not all content that is available in standard print versions of this book may appear or be packaged in all book formats. If you have purchased aversion of this book that did not include media that is referenced by or accompanies a standard print version, you mayrequest this media by visiting http://booksupport.wiley.com. For more information about Wiley products, visitus at www.wiley.com.Library of Congress Control Number: 2011939636TRADEMARKS: Wiley, the Wiley logo, and the Sybex logo are trademarks or registered trademarks of John Wiley &Sons, Inc. and/or its affiliates, in the United States and other countries, and may not be used without written permission. All other trademarks are the property of their respective owners. John Wiley & Sons, Inc. is not associated withany product or vendor mentioned in this book.10 9 8 7 6 5 4 3 2 1
Dear Reader,Thank you for choosing Cisco Networking Essentials. This book is part of afamily of premium-quality Sybex books, all of which are written by outstandingauthors who combine practical experience with a gift for teaching.Sybex was founded in 1976. More than 30 years later, we’re still committed toproducing consistently exceptional books. With each of our titles, we’re workinghard to set a new standard for the industry. From the paper we print on, to theauthors we work with, our goal is to bring you the best books available.I hope you see all that reflected in these pages. I’d be very interested to hearyour comments and get your feedback on how we’re doing. Feel free to let meknow what you think about this or any other Sybex book by sending me an emailat nedde@wiley.com. If you think you’ve found a technical error in this book,please visit http://sybex.custhelp.com. Customer feedback is critical to ourefforts at Sybex.Best regards,Neil EddeVice President and PublisherSybex, an Imprint of Wiley
To my dear wife, Heike, who has supported me throughall the late nights working and missed weekends and whohas endured my ill temper throughout this process.She is living proof there are angels among us.
A c k n ow l e d g m e n t sI want to thank the entire editing and production staff that has helped tomake this book as good as it can possibly be. That includes Kelly Talbot, mydevelopment editor, who gave me great advice beyond simply grammar andstyle. I took full advantage of all his years of experience as an editor. He was theconductor of this orchestra and ensured that everything was where it was supposed to be, when it was supposed to be.I also would like to thank the technical editor, Leslie Herron, who saved mefrom myself a number of times. It is so comforting to know that someone withdeep technical knowledge is looking over your shoulder. That also goes for EricCharbonneau, who caught things that all of us missed, and the other membersof the team, Pete Gaughan, Connor O’Brien, and Jenni Housh.A special thanks goes to Jeff Kellum for recommending me for this book andto Agatha Kim, the acquisition editor, for selecting me for this book and helpingto guide me through the entire process.
AbouttheAuthorTroy McMillan is a trainer and writer from Atlanta, Georgia. He began his ITcareer with IBM in 1999 supporting point-of-sale systems. After achieving his MCSE,he became a network administrator in the Atlanta office of a global manufacturer ofelectric motors. In 2000, he took his first job as a trainer, teaching MCSE classesto career changers at a local IT school in Atlanta.In 2001, Troy started delivering corporate training for New Horizons inAtlanta. His concentration was in Microsoft, CompTIA, and Cisco classes.In 2002, Troy started his own training company while continuing with NewHorizons on a contract basis and also teaching at various colleges and technicalschools in the Atlanta area.In 2003, Troy began traveling the United States and Canada, teaching Cisco,wireless (CWNA program), and Microsoft classes for training organizations suchas Global Knowledge, New Horizons, PPI, and Knowlogy.In 2005, Troy accepted a position with Kaplan IT Certification Preparation,creating practice tests and study guides for the Self-Test and Transcenderbrands. His work includes Microsoft, but he is the principal Cisco writer.Troy’s first book, Change Your Career: Computer Network Security as YourNew Profession, was released in 2007. This guide provides resources and helpfulhints for career changers considering this field.Troy began contributing to and providing technical edits for Sybex books in2009. He contributed to Todd Lammle’s CCNA Wireless Study Guide: IUWNEExam 640-721 and CompTIA Network Study Guide: Exam: N10-005, provided technical edits and contributions to Todd’s CCNA Cisco Certified NetworkAssociate Review Guide: Exam 640-802, and was technical editor for DarrilGibson’s Windows 7 Desktop Support and Administration: Real World Skills forMCITP Certification and Beyond (Exams 70-685 and 70-686). He is currentlyproviding technical editing on Toby Skandier’s Network Administrator StreetSmarts: A Real World Guide to CompTIA Network Skills.In 2010, Troy coauthored VCP VMware Certified Professional on vSphere 4Review Guide with Brian Perry, Chris Huss, and Jeantet Fields. He also createdand edited textbooks for Penn Foster on Apple computers, basic troubleshooting, and mobile devices. Troy created classroom instruction materials for manyof the Sybex titles already listed as well as for MCTS: Windows Server 2008 R2Complete Study Guide (Exams 70-640, 70-642 and 70-643) by William Panek.
Prior to his career in IT, Troy was a professional musician. From 1968 to 1986,he recorded and performed with many of his own bands and as a backup musician for acts including Vassar Clements and Delbert McClinton. He worked fora number of years as a session musician and songwriter in Nashville as well. In1983, he returned to school, earning a BBA in management from Georgia StateUniversity in 1986. He operated his own businesses after graduation as well asworking several years in retail management. He began a self-study in IT in the1990s, leading to his first IT job at IBM.Troy lives with his wife, Heike, and a house full of dogs, cats, birds, and fish inAtlanta, Georgia. He enjoys running, music, and sports of all kinds, especiallyNASCAR.
Contentsat aGl anceIntroductionxxiCHAPTER 1Networks1CHAPTER 2The OSI Model19CHAPTER 3TCP/IP37CHAPTER 4Protocols63CHAPTER 5Physical and Logical Topologies89CHAPTER 6Numbering Systems105CHAPTER 7Classful IP Addressing125CHAPTER 8Classless IP Addressing147CHAPTER 9Media169C H A P T E R 10Network Devices193C H A P T E R 11LAN Operations215C H A P T E R 12Managing the Cisco IOS243C H A P T E R 13Configuring Routers271C H A P T E R 14Configuring Switches299C H A P T E R 15Configuring Static Routing317C H A P T E R 16Configuring Dynamic Routing331APPENDIXAnswers to Review Questions349Index359
ContentsC hapter 1IntroductionxxiNet work s1Describing Network Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1Defining the Benefits of Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2Identifying the Requirements for a Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5Classifying Networks by Function . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8Understanding LANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8Understanding WANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9Defining Network Architectures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11Understanding Peer-to-Peer Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11Understanding Client-Server Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17C hapter 2T he OSI M odelUsing Reference Models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Benefits of Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Exploring Reference Model Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Introducing the Layers of the OSI Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Application Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Presentation Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Session Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Transport Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Network Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Data-Link Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Physical Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the OSI Encapsulation Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Identifying the Process on the Source Device . . . . . . . . . . . . . . . . . . . . . . . . . . . .Identifying the Process on the Destination Device . . . . . . . . . . . . . . . . . . . . . . . .The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19192021222323252629303232333435
xivContentsC hapter 3TC P/ I P37Understanding the TCP/IP Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Exploring the Four Layers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Comparing the OSI and TCP/IP Models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the TCP/IP Encapsulation Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Data and PDUs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Contents of Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Contents of Segments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Contents of Packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Contents of Frames . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Conversion to Bits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Functions at the Transport Layer . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding TCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding UDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Functions at the Internet Layer . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining Logical Addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Performing Routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Accomplishing Packet Forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Functions of ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Illustrating the ARP Broadcast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Logic of MAC-to-IP-Address Conversion . . . . . . . . . . . . . . . . . . .The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .C hapter 4P 63Understanding the Function of Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining Routed Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining Routing Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Exploring Application Layer Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing FTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing TFTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing SMTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Exploring Transport Layer Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Reviewing TCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Reviewing UDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .636464656567676970727276
ContentsxvExploring Internet Layer Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing IP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing ICMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing IGMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Exploring Network Access Layer Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining Network Access Layer Protocols on the LAN . . . . . . . . . . . . . . . . . . . .Defining Network Access Layer Protocols on the WAN . . . . . . . . . . . . . . . . . . . .The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .C hapter 5Physic al and Logic al Topologies77777980828384858689Designing the Physical Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89Implementing a Bus Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90Implementing a Ring Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91Implementing a Star Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92Implementing a Mesh Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94Implementing a Hybrid Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95Implementing a Point-to-Point Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96Implementing a Point-to-Multipoint Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . 98Designing the Logical Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99Understanding the Token Ring Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99Understanding the FDDI Ring Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100Understanding the Star Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102C hapter 6N u mbe ring Syste ms10 5Exploring Binary Numbering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105Understanding the Base-2 Numbering System . . . . . . . . . . . . . . . . . . . . . . . . . . 106Understanding the Relationship between Binary and Computers . . . . . . . . . . . 108Exploring Hexadecimal Numbering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110Understanding the Base-16 Numbering System . . . . . . . . . . . . . . . . . . . . . . . . . 110Identifying MAC Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113Applying Conversions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114Decimal-to-Binary Conversion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114Hex-to-Decimal Conversion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117Binary-to-Hex Conversion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
xviContentsC hapter 7Classful IP Addressing125Describing the Function of IP Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Identification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Segmentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Identifying IP Address Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining IP Address Classes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Identifying Network and Host Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing Private IP Addresses and NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Utilizing Diagnostic Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Executing the ipconfig Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Executing the ping Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Executing the arp Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Executing the traceroute Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Cisco DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Introducing IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .IPv6 Address Format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .IPv6 Address Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Special IPv6 Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .C hapter 8C lassless I P Add 41142142143144144147Understanding the Limitations of Classful Networking . . . . . . . . . . . . . . . . . . . . .Exhaustion of the Class B Network Address Space . . . . . . . . . . . . . . . . . . . . . . .Unmanageable Routing Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Exhaustion of the 32-Bit IPv4 Address Space . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Benefits of Subnetting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Identifying Sources of Network Congestion . . . . . . . . . . . . . . . . . . . . . . . . . . . .Deploying Subnetting as a Segmentation Tool . . . . . . . . . . . . . . . . . . . . . . . . . .Describing the Components of CIDR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Introducing Classless Subnetting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding VLSM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Summarization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .147148148149149150151152152161166166
ContentsC hapter 9Me diaxvii169Selecting the Proper Media Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169Bandwidth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170Convenience . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174Cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174Understanding Cabling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175Describing Cable Behavior and Characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . 175Describing Physical Implementations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176Choosing the Correct Wiring Standard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180Describing Wireless Standards . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184Identifying Standards Bodies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185Understanding 802.11 Amendments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185Understanding Wireless LAN Components and Terminology . . . . . . . . . . . . . . . 187Describing CSMA/CA Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189The Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190C hapter 10Net work Devices193Describing Device Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Repeaters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Hubs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Bridges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Routers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Wireless Access Points and Wireless Routers . . . . . . . . . . . . . . .Understanding Device Placement Principles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining Broadcast Domains . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining Collision Domains . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Cisco Three-Layer Model . . . . . . . . . . . . . . . . . . . . . . . . . . .Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .C hapter 11L A N Ope rstanding the Routing Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing Routing Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Population Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Administrative Distance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Using Routing Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .215216219221223
xviiiContentsDescribing the Switching Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Reviewing MAC and IP Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Reviewing Contention Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing MAC Address Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Frame Forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing End-to-End Communications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Local LAN Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Remote Communication Process . . . . . . . . . . . . . . . . . . . . .Essentials and Beyond . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .C hapter 12M anaging the C isco I OS243Describing Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining the Contents of RAM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining the Contents of NVRAM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining the Contents of Flash . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Defining the Contents of ROM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Describing IOS Navigation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Connecting to the Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Accessing User, Privileged, and Global Configuration Modes . . . . . . . . . . . . . . .Understanding and Managing the Boot Process . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding the Boot Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Managing the IOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Understanding Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .Managing the Configuration Register . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .The Essentials an
Exam 640-721 and CompTIA Network Study Guide: Exam: N10-005, pro-vided technical edits and contributions to Todd’s CCNA Cisco Certified Network Associate Review Guide: Exam 640-802, and was technical editor for Darril Gibson’s Windows 7
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
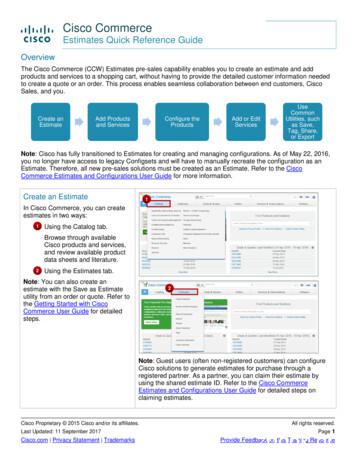
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unified Computing System (Cisco UCS), Cisco UCS B-Series Blade Servers, Cisco UCS C-Series Rack Servers, Cisco UCS S-Series Storage Servers, Cisco UCS Manager, Cisco UCS
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base