UNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT
UNIVERSAL DATAINTEGRITY SYSTEMASSESSMENTTEMPLATE IN THEBIOPHARMACEUTICALINDUSTRYUniversal data integrity system assessment template 1
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEAuthorsBristol-Myers SquibbRandy BuggeAmgenJoe SantanaShireJeet SarkarAlexionChristopher WhiteBioPhorum Operations GroupSteve AtkinsonContributorsThis document was developed through a collaboration under the auspices of BioPhorum IT Group.The contributing members were:AlexionChristopher WhiteMichael SchofieldAmgenJoe SantanaBiogenMike StrozBristol-Myers SquibbAidan DesmondClaudia YamamotoJennifer McCartyRandy BuggeRekha AlaguchellappanEli LillyAmy SchmidAnita MorrisonNick MillerGSKFred BaluyotIpsenAudrey GodimusMerck KGaA, Darmstadt, GermanyHufrish SirohiJennifer BaughmanRegeneronDeclan McDonnellRocheHorst FroedeJavier HernandezShireDavid LakeJeet SarkarUniversal data integrity system assessment template 2
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEContents1.0Background and context.42.0Introduction.43.0Purpose and scope.44.0Instructions for template use.55.0Intended use.66.0Roles.67.0Data input/ouput.78.0Data changes/entry.89.0Security roles. 1010.0Data backup. 1211.0Critical data fields and audit trail challenges. 1412.0Electronic signatures. 1613.0Summary. 18Universal data integrity system assessment template 3
BioPhorum Operations Group Ltd1.0UNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEBackground and contextThis document has been developed in response to the needto ensure compliance with the regulatory guidance for dataintegrity. Data with integrity is data that is created such thatit is: attributable, legible, contemporaneous, original andaccurate (ALCOA), and once established is maintained in amanner that ensures it is complete, consistent, enduring andavailable throughout its lifecycle.This template was developed through the joint efforts ofindividuals from a number of biopharmaceutical companiescombining their knowledge and best practice into a commonuniversal system assessment template.It should be read in conjunction with the Data integrity for ITin the biopharmaceutical industry paper, which was developedin parallel with this template to provide an industry responseto the regulatory guidelines highlighting the risks and thecontrols and best practices required to manage those risks.The template was developed to assess the health ofcomputerized systems and their electronic records from adata integrity perspective.2.0IntroductionThis template is intended to be used to evaluate potentialrisks to a computerized system and its electronic recordsthroughout the system’s lifecycle and may be conductedduring requirements gathering as a part of the initialvalidation, during assessment of system changes, duringperiodic reviews and/or at the time of decommissioning.This assessment template is an example that should befully developed in conjunction with a standard operatingprocedure (SOP) to manage consistent implementationand use.To ensure accurate evaluation of the system, it is expectedthat data flow maps and system architectural drawings aremade available for the evaluation.Since this is an example template it is not an exhaustivelist of questions and should be augmented to meet eachcompany’s specific needs. Additional what-if scenarioanalysis tools may provide a more in-depth assessment.The what-if scenario analysis should be driven by the dataflow diagrams to ensure an end-to-end evaluation of theintegrity of the data.3.03.0Purpose and scopeThe purpose of this document is to provide a templatefor assessing a system for data integrity regulatorycompliance.The assessment process is applicable to GxP (GMP, GDP,GLP, GCP, GPvP) computerized systems, which create,modify, maintain, archive, retrieve and/or transmit anyelectronic records(s).System description, and pertinent in-scope and out-ofscope parts of the computerized system (e.g. sub- systems,sites) with justification for exclusions should be recorded.The major version(s) of the software and operating systemtogether with a list of direct and indirect impacted systemsshould also be included in the scope of the assessment.Universal data integrity system assessment template 4
BioPhorum Operations Group Ltd4.04.0UNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEInstructions for template useAs a minimum, the business process owner, system owner/technical unit, quality assurance and data integrity subjectmatter expert (SME) should perform a data integrityassessment of a particular system or family of systemsutilizing this template. System and sub-systems, dataflow diagrams, applicable procedures, system interfaces,including third-party software and spreadsheets should belisted and described.This template should be used to assess the health of asystem currently in use or that may shortly be implemented.This assessment should be incorporated in the complianceand validation process followed by the company.System overview information, together with the intendeduse of the system and the review team roles, needs to becompleted. The template is subsequently broken into anumber of sections, each with a series of questionsrelating to: data input/output data changes/entry security roles data backup critical data fields and audit trail challenges electronic signatures.This template provides a starting point for the systemassessment and should be amended to reflect companyspecific requirements. Procedural controls should beestablished and documented around its use.System overviewSystem name:System ID:System description:Assessment date(s):Software components and versions:Hardware components:Location of review (i.e. site or global):Vendor name:Workflow diagrams/network flow diagrams:System interfaces:Installation location/site (specify if local or global system):Date of initial deployment:Is the system governed by a change control procedure for implementationand changes?Is the current version of the software still formally supported by thevendor?Is the system considered an open or closed system?Has a risk assessment taken place and controls identified to mitigate risk?Vendor management:Has a vendor assessment been completed?Is a vendor maintenance agreement in place?Has the vendor been audited (initially and periodically)?Is the current version of the software supported by the vendor?Are all system and service vendor(s) on the approved vendor list?Is the system a cloud service? If so, indicate if IaaS, SaaS or PaaS:Is the application hosted on the premises or by the vendor?Universal data integrity system assessment template 5
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATESystem overviewDoes the data from this system reside on a company or a vendor server?Validation:Has the system been validated for intended use?Were all significant test failures resolved prior to release of the system?Did the validation address the system’s electronic records and/orsignature functionality?Did the validation testing include accuracy, reliability, integrity,availability, and/or authenticity of the electronic record and associatedelectronic signatures including audit trails?Does the system validation documentation include controls to ensuredata integrity (data security, access roles/permissions, sequence ofoperations, enabling of relevant audit trail)?Is the process for generating copies of electronic records validated anddocumented in a procedure?Are all peripheral devices validated?Does the system validation documentation include devices or tokens thatbear or generate ID or password information and have they been tested?Have mobile devices been validated?Is the system subject to a periodic review process to ensure it ismaintained in a validated state?Are the system’s electronic records the primary/source record? Is itdocumented?5.05.0Intended useDescribe the intended use of the computerized system/instrument. Include references to requirement/design specificationdocuments as applicable.List and describe sub-systems, data flow diagrams, applicable procedures, system interfaces, including third-party softwareand spreadsheets. Include reference to documents as applicable.6.06.0RolesIt is recommended that the data integrity evaluation is conducted by a diverse team comprising members from the business,IT and quality, with experience of the targeted system. In some organizations there is a formal steward for the data integrityprogram who should be present in the evaluation if the role is different from the quality or IT roles.Below are the recommended roles in the evaluation. Keep a record of the staff involved in the creation and content of thedata integrity assessment (DIA):RoleStaff nameSignatureBusiness process ownerSystem owner (IT)Technical subject matter expert(s), as required, if different from the IT roleBusiness subject matter expert(s), as requiredQuality assuranceData integrity subject matter expert(s), if applicableUniversal data integrity system assessment template 6
BioPhorum Operations Group Ltd7.07.0UNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEData input/ouputDescribe how data (electronic/hardcopy) and results are reviewed/approved and by whom. Describe the data andassociated metadata being reviewed/approved and give details of the applicable SOP.Describe if electronic copies are used as true copies of paper or electronic records and the verification procedure to ensurethe copies preserve the content and meaning of the original data, which includes associated metadata and the static ordynamic nature of the original records.Assessment questionResponseControls*Action required**Recommendation/ TrackingCAPA***1. H ave data files been moved ortransferred without qualificationor verification/review?2. A re data files maintained in theiroriginal format in the sourcelocation?3. I s there a process to manage themovement of complete copies (truecopies) of original data to otherlocations for use by other systems?4. I s there a process to define theuse of transferable media, USBmemory drives or external harddrives?5. I s data saved in a database residingin a network location or within asystem's architecture?6. I s data saved in local folderswithout application or networkcontrols?7. H ave any changes to the controlledelectronic document/recordsbeen formally authorized with theapproval from the records ownerand quality assurance?8. A re the changes in line withstandard company documentationand/or system change controlprocedural controls?9. W hen transcribed raw data isrequired has it been referencedand the original retained as partof the system's documentationpackage?10. H as metadata been reviewedwith each record and before finalapproval of the record?11. I s retained metadata sufficientto support investigation andreconstruction of the entire datahistory?Table key:* What are the technical or procedural controls required to manage and reduce the identified risk?** Action required. Include owner of the action and completion date*** Corrective and preventative actionUniversal data integrity system assessment template 7
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEComplementary assessment: what-if analysis should be driven by the data process map to ensure an end-to-end evaluationof the integrity of the data.Perform additional what-if scenarios to address peculiarities of the targeted system:What-if scenarioEffect(Risk)8.0Controls to reduce and detect riskTechnical8.0ProceduralAction required (Y/N)/Tracking (i.e. CAPA#)Data changes/entryDescribe who can alter specifications, process parameters, or manufacturing or testing methods, and by what means(electronic or manual).Note: Permissions to change settings or data should be limited to authorized personnel only.TTTTTAssessment questionResponseControls*Action required**Recommendation/Tracking CAPA***1. T esting confirms users' ability to delete data has beenremoved?2. D oes the system enforce contemporaneous dataentry?3. D oes the system use automated operational checksto determine if results are within a predefinedspecification?4. I f an invalid entry is entered, is it automaticallycaptured within the audit trail?5. D oes the system require documentation of a reasonfor change or deletion of GxP data?Universal data integrity system assessment template 8
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEAssessment questionResponseControls*Action required**Recommendation/Tracking CAPA***6. H as manual data entry only been completed byauthorized individuals and has the system recordeddetails of the entry, the individual making the entryand the time of the entry?7. H as all manual data entry been performed in avalidated specified format controlled by the softwareand have invalid data formats been rejected by thesystem?8. A re all manual data entries verified, either by a secondoperator or by computerized means?9. H ave changes to manual data entries been capturedin the audit trail and reviewed by an appropriatelyauthorized and independent person?10. H as automated data capture occurred throughvalidated interfaces between validated dataacquisition and recording systems?11. H as automatically captured data been savedinto memory in a format that is not vulnerable tomanipulation, loss or change?12. H as the system software incorporated validatedchecks to ensure the completeness of data andmetadata acquired through automated data capture?13. D oes the system enforce chronological data entry ifrequired by the business process?14. A re spreadsheet or manual calculations used outsideof the system?15. H ave methods/recipes of the change verificationprocess been formally documented?16. A re current system configuration parameterscaptured in an approved document?17. I s there a process in place to ensure records are notdeleted?18. A re there procedures in place to ensure data ismodified through change controls and/or changemanagement?19. A re processes in place to prevent the creation,modification or deletion of GxP data in temporarymemory without an audit trail?20. A re there processes that ensure data recorded intemporary memory is committed to durable media(e.g. saved to the database or hard drive) at the timeof the activity?Describe the what-if scenarios for data creation/modification/deletion as follows: scenarios in which data can be created/modified should be reviewed and evaluated to determine if a what-ifscenario is required scenarios in which data can be deleted require a what-if scenario.Universal data integrity system assessment template 9
BioPhorum Operations Group LtdWhat-if scenarioUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEEffect(Risk)9.0Controls to reduce and detect riskTechnical9.0ProceduralAction required (Y/N)/Tracking (i.e. CAPA#)Security rolesDescribe the initial data and associated metadata set-up of the instrument/system (e.g. metadata, master data, attributes,data dictionary, processes and calculations), document the system roles, and identify who can make updates, when updatescan be made and the impact of the changes (e.g. the users with authorized security level in the system have the permissionto set up the data collection and optical bench parameters for each experiment).Identify the roles in use in the computerized system, the controls around assignment of the roles and the abilities ofeach role.Follow the questionnaire below for additional assessment questions:Assessment questionResponseControls*Action required**Recommendation/Tracking CAPA***1. Does the company have a policy/procedure definingcontrols on password strength and password sharing?2. A re SOPs in place defining administration of the systemby the administrator?3. C an you detail the usage of non-standard accounts andhow they are used and controlled?4. I s the number of system administrators commensuratewith the total number of users?5. D o any end-users have access to administer the system? Ifso, is there a documented justification?Universal data integrity system assessment template 10
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEAssessment questionResponseControls*Action required**Recommendation/Tracking CAPA***6. Do any system administrators have end-user access? If so, isthere a documented justification?7. Has the generic system administration password beenchanged/disabled? If so, how often? What controls are thereon the management and use of generic passwords? Aregeneric password activities defined in a procedure and arethe activities reviewed?8. Does the system allow a user to administer the systemunder a proxy generic role, thereby obscuring the audit trail?9. Is the system configured to ensure that passwords arerevised on a regular basis? How often are they changed?10. C an the system disable users after a defined numberof continuous invalid login attempts? If so, what is thisnumber?11. A re invalid login attempts captured in a system audit trail?12. D oes the system allow the administrator to reset and issuetemporary passwords for disabled users?13. D oes the system force the users to change the temporarypassword provided by the administrator?14. I s application timeout activated on the system? If so, howlong until timeout?15. D oes the system provide the ability to deactivate andreactivate a user without losing their history of activities?16. A re training requirements defined for the differentsecurity roles?17. I s a process in place to ensure training required for systemaccess is assigned and completed before granting access tothe system and is it verified on an ongoing basis?18. I s there a list for user and system roles for the overallsystem?19. I s there evidence of the user roles being tested?20. D oes the system have any generic user names defined(excludes system-controlled service accounts)? If so howmany?21. C an the system generate a list of all users who have accessto the system and their user roles?22. F or all e-signatures: are the user ID, date, time and reasonpresent?23. H ave appropriate levels of access been defined, set upand verified? Is there clear segregation of duties that aredocumented and enforced by the software?24. A re users unable to alter the time/date stamp for thesystem?25. D oes the vendor/developer have active access to thecomputerized system?26. W ere vendor (default) passwords changed uponinstallation?27. I s there a procedure for user access reviews and are theyperformed on a defined basis?28. I s there a procedure that defines user provisioning for thesystem?Universal data integrity system assessment template 11
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEExplore what other what-if scenarios could be applicable to the system being assessed:What-if scenarioEffect(Risk)Controls to reduce and detect riskTechnicalProceduralAction required (Y/N)/Tracking (i.e. CAPA#)10.0 10.0 Data backupDescribe where and how results (electronic/hardcopy) are stored: is the data and associated metadata stored to the workstation automatically? is the data and associated metadata stored on a file server? If so, how is this performed and how often? is the data documented or saved at the time of performance? are true copies of dynamic electronic records made and maintained in the format of the original records or in acompatible format?Assessment questionResponseControls*Action required**Recommendation/Tracking CAPA***1. Has periodic review of backed-up data been completed incompliance with site procedures?2. W hat is the strategy for executing a complete backup ofraw data and metadata (including audit trail) directly to aserver by a method that preserves content and meaning?3. W hat is the backup interval to an alternative andpermanent media? How often is data restored andverified for completeness and accuracy?4. H ow long is backup data retained?Universal data integrity system assessment template 12
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEAssessment questionResponseControls*Action required**Recommendation/Tracking CAPA***5. Which processes control system administration,monitoring, security and access to backed-up data?6. W hich processes are in place to confirm the readability,integrity and accuracy of backed-up data?7. W hich processes are in place to check the ability torestore backup data periodically and prior to systemchanges?8. I s archived data checked for security, accessibility,readability and integrity to ensure content and meaningis preserved?9. I f records are retrieved is there documentation to ensurethat the set of records provided is accurate, complete andreflects the source set of records?10. A re documented disaster recovery exercises performed?Explore what other what-if scenarios could applicable to the system being assessed:What-if scenario(Risk)EffectControls to reduce and detect riskTechnicalProceduralAction required (Y/N)/Tracking (i.e. CAPA#)Universal data integrity system assessment template 13
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATE11.0 11.0 Critical data fields and audit trail challengesComplete the tables below to define critical data fields, associated metadata and critical configuration settings. Verifywhether the audit trail is enabled to capture changes/deletions/and reason for the modification of these events and data inthe system by one of the following methods: review existing testing create a test script per procedure and execute/document the results.When the fields that require an audit trail have been identified, verify and/or update the relevant quality systemdocument(s) to identify the critical fields and critical configuration items.Note: Changes to the system are to be made using an approved change control system as described in the applicable systemprocedures.Note: During the periodic review, the audit trail for the critical data fields identified in this section will be reviewed.Critical data fieldAudit trail enabledAudit trail works as expected?(Change/Del ete/Reason)Sample name(includes thesample ID andsample point)Does the system/instrument ops SOPinclude a review of the audit trail?Is the configuration setting capturedin a controlled document?YesYesYesYesNoNoNoNoSOPAssessment questionResponseControls*Action required**Recommendation/Tracking CAPA***1. D oes the system generate electronic records that areavailable for review in both human readable and electronicform that accurately and completely reflects the sourcedata, including audit trails?2. Has audit trail functionality, availability and accessibilitybeen tested? Are audit trails available for all GMPelectronic records?3. H as a periodic review been completed in compliance withsite procedures?4. D oes the system audit trail track and store configurationchanges (i.e. actions of system administrator, changes torules for system operation)?5. D oes the system generate audit trails for creation,modification and deactivation of user and administratoraccess accounts?6. D oes the system record the date, time (hr/min), time zoneand any create, modify or delete actions performed by aspecifically attributable user in the audit trail?7. D oes the system retain the previously recordedinformation in the audit trail when a record is modifiedor deleted?Universal data integrity system assessment template 14
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEAssessment questionResponseControls*Action required**Recommendation/Tracking CAPA***8. D oes the system prohibit users and administrators frommodifying the audit trail and, if yes, has the capabilitybeing validated?9. Are end-users prohibited from turning off the audit trail?Has this been tested?10. D oes the source of date/time from the audit trail comefrom a server or protected workstation that cannot bealtered by end-users? Is the source defined?11. I s daylight saving time changeover automatic?12. H as the critical data of the business process beendefined for the business process?13. H as the data audit trail for critical data been reviewed(and documented) according to procedures?14. H ave individuals who collect/enter/review data andaudit trails been appropriately trained to use thesystem?15. H as the system audit trail been reviewed anddocumented according to procedures?16. A re training requirements defined for the differentsecurity roles?17. H as the system enabled a computer-generated audittrail of data that displays the name or User ID of theperson making the change, the date and time of thechange, the reason for the change, and are the ‘before’and ‘after’ values viewable?18. I t is possible to print out a legible and meaningful recordof the data generated by the computerized system(including metadata)?19. I f a change is made to a record is it possible to print outa record of the change indicating when and how theoriginal data was changed?20. D oes the audit trail detect when a system administratordisables or deletes entries from the audit trail?21. I s the audit trail retained for the same period of time asthe electronic record?Universal data integrity system assessment template 15
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEExplore what other what-if scenarios could be applicable to the system being assessed:What-if scenarioEffect(Risk)Controls to reduce and detect riskTechnicalProceduralAction required (Y/N)/Tracking (i.e. CAPA#)12.0 12.0 Electronic signaturesDetermine if GxP electronic signatures are utilized in the system. Describe how the electronic signatures are controlled andvalidated.Assessment questionResponseControls*Action required**Recommendation/Tracking CAPA***1. Does the system have electronic signature requirementsrelated to health authority regulation?2. Are electronic signatures permanently linked to anelectronic record?3. Does system validation include testing that the electronicsignature cannot be edited, deleted, copied or transferredto a different record (including copies of the electronicrecord)?4. Does system design prevent electronic signatures beingreused or reassigned?5. Are the GxP electronic signatures used in the systemunique to an individual?6. Are group ID/passwords for electronic signaturesprevented?7. Does the system require two distinct electronic signaturecomponents: a public and unique ID and a privatepassword?8. Are two individual specific electronic signaturecomponents required for the initial signing and at leastone component for subsequent signings within a singlecontinuous period of system/application access?9. Are two individual specific electronic signaturecomponents required if signatures are not performedwithin a single continuous period of system/applicationaccess?Universal data integrity system assessment template 16
BioPhorum Operations Group LtdUNIVERSAL DATA INTEGRITY SYSTEM ASSESSMENT TEMPLATEAssessment questionResponseControls*Action required**Recommendation/Tracking CAPA***10. Does the system validation testing include:a) d isplay of the electronically signed electronic recordin a format that is a clear human readable text,including the date and time when the electronicsignature was executed? b) capture of the meaning of the signature?11. Does validation documentation include changes tosigned electronic records with evidence that the linkaget
analysis tools may provide a more in-depth assessment. The what-if scenario analysis should be driven by the data flow diagrams to ensure an end-to-end evaluation of the integrity of the data. 3.0 3.0 Purpose and scope The purpose of this document is to provide a template for ass
Integrity ONE* 41x51x15.5cm Integrity DUE XL* 43.5x67x21cm Integrity TOP* 37x51x15.5cm Integrity Q* 41x51x17.5cm Integrity, the Silestone kitchen sink Seamless Integration More than 90% Quartz and 100% Innovation Integrity ONE In one single piece ONE is the model which embodies Integrity's concept. A single kitchen sink in one piece.
Building on a previous discussion of data integrity (2), the first article explores a four-layer data integrity model that demonstrates the scope of a data integrity and data governance program. Next, McDowall discusses how data process mapping is a vital step for identifying data integrity gaps within chroma
May 20, 2008 · Power Integrity in System Design CAE / Design Simulation Skipper Liang 5/20/2008. 2 Agenda Introduction Power Integrity Concept DC Analysis for Power Integrity AC Analysis for Power Integrity Summary Q & A 1. Observe from Frequency Domain 2. Observe from Time Domain. 3 Introduction Power Integrity Concept DC
EMA: Good Manufacturing Guidance to Ensure the Integrity of Data 23 Q&A 10 Aug 2016 PIC/s: Draft Guidance Good Practices For Data Management And Integrity In Regulated GMP/GDP Environments 41 pages July 2016 MHRA: GXP Data Integrity Draft Guidance 14 pages April 2016 FDA: Draft Guidance: Data Integrity
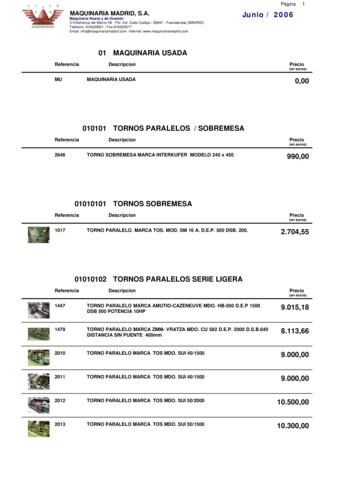
2210 fresadora universal marca fexac up 9.000,00 2296 fresadora universal marca ghe 1.000,00 2314 fresadora universal kondia modelo 2 2.300,00 2315 fresadora universal ghe modelo 2 2.100,00 2364 fresadora universal marca fexac up 2.500,00 2429 fresadora universal. marca mrf. mod. fu 115. 7.000,00 2456 fresadora universal marca correa mod. f1 u .
Gehl to Mini Universal Adapter Plate ASV RC-30 or Terex PT-30 to Mini Universal Adapter Plate Mini Universal Adapter - Bolt or Weld-on. Thomas to Mini Universal Adapter Plate MT-50/52/55 & 463 to Mini Universal Adapter Plate Mini Universal Adapter - Bolt or Weld-on. SS Universal Quick Attach
Integrity. A single sink, in one piece, measuring 41x51x15,5cm., ONE is 1, with its curved outline, the perfect choice for lovers of fluid design and originality. Integrity Integrity DUE L Integrity ONE Integrity DUE S Integrity DUE XL. . Price Groups Silestone .
assessment. In addition, several other educational assessment terms are defined: diagnostic assessment, curriculum-embedded assessment, universal screening assessment, and progress-monitoring assessment. I. FORMATIVE ASSESSMENT . The FAST SCASS definition of formative assessment developed in 2006 is “Formative assessment is a process used