Samsung Electronics Co., Ltd. Samsung Galaxy S4,
Samsung Electronics Co., Ltd.Samsung Galaxy Devices withQualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.104/30/14Prepared for:Samsung Electronics Co., Ltd.416 Maetan-3dong, Yeongtong-gu, Suwon-si, Gyeonggi-do, 443-742 KoreaPrepared By:www.gossamersec.com
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security Target1.Version 1.1 04/30/14SECURITY TARGET INTRODUCTION .31.1SECURITY TARGET REFERENCE .31.2TOE REFERENCE .41.3TOE OVERVIEW .41.4TOE DESCRIPTION .41.4.1TOE Architecture .51.4.2TOE Documentation .72.CONFORMANCE CLAIMS .82.13.CONFORMANCE RATIONALE .8SECURITY OBJECTIVES .93.1SECURITY OBJECTIVES FOR THE ENVIRONMENT.94.EXTENDED COMPONENTS DEFINITION . 105.SECURITY REQUIREMENTS . 125.1TOE SECURITY FUNCTIONAL REQUIREMENTS . 125.1.1Cryptographic support (FCS) . 135.1.2User data protection (FDP) . 185.1.3Identification and authentication (FIA) . 185.1.4Security management (FMT) . 205.1.5Protection of the TSF (FPT) . 225.1.6TOE access (FTA) . 245.1.7Trusted path/channels (FTP) . 245.2TOE SECURITY ASSURANCE REQUIREMENTS. 255.2.1Development (ADV) . 255.2.2Guidance documents (AGD) . 255.2.3Life-cycle support (ALC) . 265.2.4Tests (ATE) . 275.2.5Vulnerability assessment (AVA) . 276.TOE SUMMARY SPECIFICATION . 296.16.26.36.46.56.66.7CRYPTOGRAPHIC SUPPORT . 29USER DATA PROTECTION . 33IDENTIFICATION AND AUTHENTICATION . 34SECURITY MANAGEMENT . 35PROTECTION OF THE TSF . 37TOE ACCESS. 39TRUSTED PATH/CHANNELS . 40LIST OF TABLESTable 1 TOE Security Functional Components . 13Table 2 EAL 1 augmented with ALC TSU EXT.1 Assurance Components . 25Table 3 OpenSSL Cryptographic Algorithms . 31Table 4 Samsung Kernel Cryptographic Algorithms . 31Table 5 Power-up Cryptographic Algorithm Known Answer Tests . 38Page 2 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/141. Security Target IntroductionThis section identifies the Security Target (ST) and Target of Evaluation (TOE) identification, ST conventions, STconformance claims, and the ST organization. The TOE consists of the Samsung Galaxy Devices with QualcommSnapdragon Processors provided by Samsung Electronics Co., Ltd. The TOE is being evaluated as a Mobile Device.The Security Target contains the following additional sections: Conformance Claims (Section 2) Security Objectives (Section 3) Extended Components Definition (Section 4) Security Requirements (Section 5) TOE Summary Specification (Section 6)ConventionsThe following conventions have been applied in this document: Security Functional Requirements – Part 2 of the CC defines the approved set of operations that may beapplied to functional requirements: iteration, assignment, selection, and refinement.oIteration: allows a component to be used more than once with varying operations. In the ST,iteration is indicated by a letter placed at the end of the component. For example FDP ACC.1aand FDP ACC.1b indicate that the ST includes two iterations of the FDP ACC.1 requirement, aand b.oAssignment: allows the specification of an identified parameter. Assignments are indicated usingbold and are surrounded by brackets (e.g., [assignment]). Note that an assignment within aselection would be identified in italics and with embedded bold brackets (e.g., [[selectedassignment]]).oSelection: allows the specification of one or more elements from a list. Selections are indicatedusing bold italics and are surrounded by brackets (e.g., [selection]).oRefinement: allows the addition of details. Refinements are indicated using bold, for additions,and strike-through, for deletions (e.g., “ all objects ” or “ some big things ”). The MDFPP uses an additional convention – the ‘case’ – which defines parts of an SFR that apply onlywhen corresponding selections are made or some other identified conditions exist. Only the applicablecases are identified in this ST and they are identified using bold text. Other sections of the ST – Other sections of the ST use bolding to highlight text of special interest, such ascaptions.1.1 Security Target ReferenceST Title – Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetST Version – Version 1.1ST Date – 04/30/14Page 3 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/141.2 TOE ReferenceTOE Identification – Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm SnapdragonProcessors including the Galaxy S4, Galaxy Note 3, and the Galaxy NotePRO Tablet. The evaluated versions of themobile devices are as follows. Android version: 4.4.2Kernel version: 3.4.0Build number: KOT49HSecurity software version: MDF v1.0 Release 3 & VPN v1.4 Release 2TOE Developer – Samsung Electronics Co., Ltd.Evaluation Sponsor – Samsung Electronics Co., Ltd.1.3 TOE OverviewThe Target of Evaluation (TOE) are the Samsung Galaxy Devices with Qualcomm Snapdragon Processors includingthe Galaxy S4, Galaxy Note 3, and the Galaxy NotePRO Tablet.1.4 TOE DescriptionThe TOE is a mobile operating system based on Android 4.4 with modifications made to increase the level ofsecurity provided to end users and enterprises. The TOE is intended to be used as part of an enterprise messagingsolution providing mobile staff with enterprise connectivity.The TOE includes a Common Criteria mode (or “CC mode”) that an administrator can through use of an MDM.The TOE must be configured as follows in order for an administrator to transition the TOE to CC mode. Require a screen lock password (swipe, PIN, pattern, or facial recognition screen locks are not allowed). The maximum password failure retry policy should be less than or equal to ten. Device encryption must be enabled. SDCard encryption must be enabled.When CC mode has been enabled, the TOE behaves as follows. The TOE sets the system wide Android CC mode property to “Enabled”. The TOE performs FIPS 140-2 power-on self-tests. The TOE performs self-tests for key management. The TOE performs secure boot integrity checking of the kernel and key system executables. The TOE prevents loading of custom firmware/kernels and requires all updates occur through FOTA(Samsung’s Firmware Over The Air firmware update method) The TOE uses FIPS 140-2 approved cryptographic ciphers when joining and communicating with wirelessnetworks. The TOE utilizes FIPS 140-2 approved cryptographic ciphers for TLS. The TOE ensures FOTA updates utilize 2048-bit PKCS #1 RSA-PSS formatted signatures (with SHA-512hashing).There are three different models of the TOE, the Galaxy S4, Galaxy Note 3, and the Galaxy NotePRO tablet. Thesemodels differ in physical form factor and in addition, Samsung offers each model in differing hardware variants:1. Samsung manufactures the Galaxy S4 hardware in a GSM or CDMA cellular radio variant and offers eachvariant with 16GB, 32GB, or 64GB of internal Flash storage.2. Samsung manufactures the Galaxy Note 3 hardware in a single configuration with 32GB of internal Flashstorage and a cellular radio capable of operating on both GSM and CDMA networks.Page 4 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security Target3.Version 1.1 04/30/14Samsung manufactures the Galaxy NotePRO with an LTE cellular radio and offers it with either 32GB or64GB of internal Flash storage.Finally, the Galaxy NotePRO was evaluated without a SIM chip, and thus it does not have any LTE/cellularcapabilities in its evaluated configuration.1.4.1 TOE ArchitectureThe TOE combines with a Mobile Device Management solution that enables the enterprise to watch, control andadminister all deployed mobile devices, across multiple mobile service providers. This partnership provides a securemobile environment that can be managed and controlled by the environment and reduce the risks that can beintroduced through a Bring-Your-Own-Device (BYOD) model.Data on the TOE is protected through the implementation of Samsung On-Device Encryption (ODE) which utilizesa FIPS 140-2 certified cryptographic module to encrypt device and SD card storage. This functionality is combinedwith a number of on-device policies including local wipe, remote wipe, password complexity, automatic lock andprivileged access to security configurations to prevent unauthorized access to the device and stored data.The Samsung Enterprise Software Development Kit (SDK) builds on top of the existing Android security model byexpanding the current set of security configuration of options to more than 390 configurable policies and includingadditional security functionality such as application whitelisting and blacklisting.1.4.1.1 Physical BoundariesThe TOE is a multi-user operating system based on Android (4.4) that incorporates the Samsung Enterprise SDK.The TOE does not include the user applications that run on top of the operating system, but does include controlsthat limit application behavior. The method of use for the TOE is as a mobile messaging device for use within anenterprise environment where the configuration of the device is managed through a compliant device managementsolution.The TOE communicates and interacts with 802.11-2012 Access Points to establish network connectivity, and thethrough that connectivity interacts with MDM servers that allow administrative control of the TOE.1.4.1.2 Logical BoundariesThis section summarizes the security functions provided by the Samsung Galaxy Devices with QualcommSnapdragon Processors: Cryptographic support User data protection Identification and authentication Security management Protection of the TSF TOE access Trusted path/channels1.4.1.2.1 Cryptographic supportThe TOE includes a cryptographic module with FIPS 140-2 certified algorithms for a wide range of cryptographicfunctions including: asymmetric key generation and establishment, symmetric key generation,encryption/decryption, cryptographic hashing and keyed-hash message authentication. These functions aresupported with suitable random bit generation, key derivation, salt generation, initialization vector generation,Page 5 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/14secure key storage, and key and protected data destruction. These primitive cryptographic functions are used toimplement security protocols such as TLS and HTTPS and also to encrypt the media (including the generation andprotection of data, right, and key encryption keys) used by the TOE. Many if these cryptographic functions are alsoaccessible as services to applications running on the TOE.1.4.1.2.2 User data protectionThe TOE is designed to control access to system services by hosted applications, including protection of the TrustAnchor Database. Additionally, the TOE is design to protect user and other sensitive data using encryption so thateven if a device is physically lost, the data remains protected.1.4.1.2.3 Identification and authenticationThe TOE supports a number of features related to identification and authentication. From a user perspective, exceptfor making phone calls to an emergency number, a password (i.e., Password Authentication Factor) must becorrectly entered to unlock the TOE. Also, even when the TOE is unlocked the password must be re-entered tochange the password. Passwords are obscured when entered so they cannot be read from the TOE's display and thefrequency of entering passwords is limited and when a configured number of failures occurs, the TOE will be wipedto protect its contents. Passwords can be constructed using upper and lower cases characters, numbers, and specialcharacters and passwords up to 16 characters are supported.The TOE can also serve as an 802.1X supplicant and can use X509v3 and validate certificates for EAP-TLS andTLS, exchanges.1.4.1.2.4 Security managementThe TOE provides all the interfaces necessary to manage the security functions identified throughout this SecurityTarget as well as other functions commonly found in mobile devices. Many of the available functions are availableto users of the TOE while many are restricted to administrators operating through a Mobile Device Managementsolution once the TOE has been enrolled. Once the TOE has been enrolled and then un-enrolled, it removes allMDM policies and disables CC mode.1.4.1.2.5 Protection of the TSFThe TOE implements a number of features designed to protect itself to ensure the reliability and integrity of itssecurity features. It protects particularly sensitive data such as cryptographic keys so that they are not accessible orexportable. It also provides its own timing mechanism to ensure that reliable time information is available (e.g., forlog accountability). It enforces read, write, and execute memory page protections, uses address space layoutrandomization, and stack-based buffer overflow protections to minimize the potential to exploit application flaws. Itis also designed to protect itself from modification by applications as well as to isolate the address spaces ofapplications from one another to protect those applications.The TOE includes functions to perform self-tests and software/firmware integrity checking so that it might detectwhen it is failing or may be corrupt. If any of the self-tests fail, the TOE will not go into an operational mode. It alsoincludes mechanisms (i.e., verification of the digital signature of each new image) so that the TOE itself can beupdated while ensuring that the updates will not introduce malicious or other unexpected changes in the TOE.Digital signature checking also extends to verifying applications prior to their installation.1.4.1.2.6 TOE accessThe TOE can be locked, obscuring its display, by the user or after a configured interval of inactivity. The TOE alsohas the capability to display an advisory message (banner) when users unlock the TOE for use.The TOE is also able to attempt to connect to wireless networks as configured.Page 6 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/141.4.1.2.7 Trusted path/channelsThe TOE supports the use of 802.11-2012, 802.1X, EAP-TLS, and TLS to secure communications channelsbetween itself and other trusted network devices.1.4.2 TOE DocumentationSamsung Android 4.4 on Galaxy Devices Guidance Documentation, version 1.4, April 29, 2014Samsung Android 4.4 on Galaxy Devices User Guidance Documentation, version 1.2, April 29, 2014Page 7 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/142. Conformance ClaimsThis TOE is conformant to the following CC specifications: Common Criteria for Information Technology Security Evaluation Part 2: Security functional components,Version 3.1, Revision 4, September 2012. Part 2 ExtendedCommon Criteria for Information Technology Security Evaluation Part 3: Security assurance components,Version 3.1 Revision 4, September 2012. Part 3 Extended Protection Profile For Mobile Device Fundamentals, Version 1.0, 21 Oct 2013 (MDFPP10) Package Claims: Assurance Level: EAL 1 augmented with ALC TSU EXT.12.1 Conformance RationaleThe ST conforms to the MDFPP10. As explained previously, the security problem definition, security objectives,and security requirements are defined the PP.Page 8 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/143. Security ObjectivesThe Security Problem Definition may be found in the MDFPP10 and this section reproduces only the correspondingSecurity Objectives for operational environment for reader convenience. The MDFPP10 offers additionalinformation about the identified security objectives, but that has not been reproduced here and the MDFPP10 shouldbe consulted if there is interest in that material.In general, the MDFPP10 has defined Security Objectives appropriate for Mobile Device and as such are applicableto the Samsung Galaxy Devices with Qualcomm Snapdragon Processors TOE.3.1 Security Objectives for the Environment OE.CONFIG TOE administrators will configure the Mobile Device security functions correctly to createthe intended security policy. OE.NOTIFY The Mobile User will immediately notify the administrator if the Mobile Device is lost orstolen. OE.PRECAUTION The Mobile User exercises precautions to reduce the risk of loss or theft of the MobileDevice.Page 9 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/144. Extended Components DefinitionAll of the extended requirements in this ST have been drawn from the MDFPP10. The MDFPP10 defines thefollowing extended SFRs and SARs and since they are not redefined in this ST the MDFPP10 should be consultedfor more information in regard to those CC extensions. FCS CKM EXT.1: Extended: Cryptographic Key Support FCS CKM EXT.2: Extended: Cryptographic Key Random Generation FCS CKM EXT.3: Extended: Cryptographic Key Generation FCS CKM EXT.4: Extended: Key Destruction FCS CKM EXT.5: Extended: TSF Wipe FCS CKM EXT.6: Extended: Salt Generation FCS HTTPS EXT.1: HTTPS Protocol FCS IV EXT.1: Extended: Initialization Vector Generation FCS RBG EXT.1: Extended: Cryptographic Operation (Random Bit Generation FCS SRV EXT.1: Extended: Cryptographic Algorithm Services FCS STG EXT.1: Extended: Cryptographic Key Storage FCS STG EXT.2: Extended: Encrypted Cryptographic Key Storage FCS STG EXT.3: Extended: Integrity of encrypted key storage FCS TLS EXT.1: Extended: EAP TLS Protocol FCS TLS EXT.2: TLS Protocol FDP ACF EXT.1: Extended: Security access control FDP DAR EXT.1: Extended: Data-At-Rest Protection FDP STG EXT.1(1): Extended: User Data Storage FIA AFL EXT.1: Authorization failure handling FIA PAE EXT.1: Extended: PAE Authentication FIA PMG EXT.1: Extended: Password Management FIA TRT EXT.1: Extended: Authentication Throttling FIA UAU EXT.1 : Extended: Authentication for Cryptographic Operation FIA UAU EXT.2: Timing of Authentication FIA UAU EXT.3: Extended: Re-Authentication FIA X509 EXT.1: Extended: Validation of certificates FIA X509 EXT.2: Extended: X509 certificate authentication FIA X509 EXT.3: Extended: Request Validation of certificates FMT SMF EXT.1: Extended: Specification of Remediation Actions FPT AEX EXT.1: Extended: Anti-Exploitation Services (ASLR)Page 10 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security Target FPT AEX EXT.2: Extended: Anti-Exploitation Services (Memory Page Permissions) FPT AEX EXT.3: Extended: Anti-Exploitation Services (Stack Overflow Protection) FPT AEX EXT.4: Extended: Domain Isolation FPT BBD EXT.1: Application Processor Mediation FPT KST EXT.1: Extended: Key Storage FPT KST EXT.2: Extended: No Key Transmission FPT KST EXT.3: Extended: No Plaintext Key Export FPT NOT EXT.1: Extended: Event Notification FPT TST EXT.1: Extended: TSF Cryptographic Functionality Testing FPT TST EXT.2: Extended: TSF Integrity Testing FPT TUD EXT.1: Extended: Trusted Update: TSF version query FPT TUD EXT.2: Extended: Trusted Update Verification FTA SSL EXT.1: Extended: TSF- and User-initiated locked state FTA WSE EXT.1: Extended: Wireless Network Access FTP ITC EXT.1: Extended: Trusted channel Communication ALC TSU EXT.1: Timely Security UpdatesVersion 1.1 04/30/14Page 11 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/145. Security RequirementsThis section defines the Security Functional Requirements (SFRs) and Security Assurance Requirements (SARs)that serve to represent the security functional claims for the Target of Evaluation (TOE) and to scope the evaluationeffort.The SFRs have all been drawn from the MDFPP10. The refinements and operations already performed in theMDFPP10 are not identified (e.g., highlighted) here, rather the requirements have been copied from the MDFPP10and any residual operations have been completed herein. Of particular note, the MDFPP10 made a number ofrefinements and completed some of the SFR operations defined in the Common Criteria (CC) and that PP should beconsulted to identify those changes if necessary.The SARs are also drawn from the MDFPP10 which includes all the SARs for EAL 1 augmented withALC TSU EXT.1. However, the SARs are effectively refined since requirement-specific 'Assurance Activities' aredefined in the MDFPP10 that serve to ensure corresponding evaluations will yield more practical and consistentassurance than the assurance requirements alone. The MDFPP10 should be consulted for the assurance activitydefinitions.5.1 TOE Security Functional RequirementsThe following table identifies the SFRs that are satisfied by the Samsung Galaxy Devices with QualcommSnapdragon Processors TOE.Requirement ClassFCS: Cryptographic supportFDP: User data protectionRequirement ComponentFCS CKM.1(1): Refinement: Cryptographic key generationFCS CKM.1(2): Cryptographic key generationFCS CKM.1(3): Cryptographic key generationFCS CKM.2: Cryptographic key distributionFCS CKM EXT.1: Extended: Cryptographic Key SupportFCS CKM EXT.2: Extended: Cryptographic Key Random GenerationFCS CKM EXT.3: Extended: Cryptographic Key GenerationFCS CKM EXT.4: Extended: Key DestructionFCS CKM EXT.5: Extended: TSF WipeFCS CKM EXT.6: Extended: Salt GenerationFCS COP.1(1): Cryptographic operationFCS COP.1(2): Cryptographic operationFCS COP.1(3): Refinement: Cryptographic operationFCS COP.1(4): Refinement: Cryptographic operationFCS COP.1(5): Refinement: Cryptographic operationFCS HTTPS EXT.1: HTTPS ProtocolFCS IV EXT.1: Extended: Initialization Vector GenerationFCS RBG EXT.1: Extended: Cryptographic Operation (Random BitGeneration)FCS SRV EXT.1: Extended: Cryptographic Algorithm ServicesFCS STG EXT.1: Extended: Cryptographic Key StorageFCS STG EXT.2: Extended: Encrypted Cryptographic Key StorageFCS STG EXT.3: Extended: Integrity of encrypted key storageFCS TLS EXT.1: Extended: EAP TLS ProtocolFCS TLS EXT.2: TLS ProtocolFDP ACF EXT.1: Extended: Security access controlFDP DAR EXT.1: Extended: Data-At-Rest ProtectionPage 12 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetFIA: Identification andauthenticationFMT: Security managementFPT: Protection of the TSFFTA: TOE accessFTP: Trusted path/channelsVersion 1.1 04/30/14FDP STG EXT.1(1): Extended: User Data StorageFIA AFL EXT.1: Authorization failure handlingFIA PAE EXT.1: Extended: PAE AuthenticationFIA PMG EXT.1: Extended: Password ManagementFIA TRT EXT.1: Extended: Authentication ThrottlingFIA UAU.7: Protected authentication feedbackFIA UAU EXT.1 : Extended: Authentication for CryptographicOperationFIA UAU EXT.2: Timing of AuthenticationFIA UAU EXT.3: Extended: Re-AuthenticationFIA X509 EXT.1: Extended: Validation of certificatesFIA X509 EXT.2: Extended: X509 certificate authenticationFIA X509 EXT.3: Extended: Request Validation of certificatesFMT MOF.1(1): Management of security functions behaviorFMT MOF.1(2): Management of security functions behaviorFMT SMF.1: Specification of Management FunctionsFMT SMF EXT.1: Extended: Specification of Remediation ActionsFPT AEX EXT.1: Extended: Anti-Exploitation Services (ASLR)FPT AEX EXT.2: Extended: Anti-Exploitation Services (MemoryPage Permissions)FPT AEX EXT.3: Extended: Anti-Exploitation Services (StackOverflow Protection)FPT AEX EXT.4: Extended: Domain IsolationFPT BBD EXT.1: Application Processor MediationFPT KST EXT.1: Extended: Key StorageFPT KST EXT.2: Extended: No Key TransmissionFPT KST EXT.3: Extended: No Plaintext Key ExportFPT NOT EXT.1: Extended: Event NotificationFPT STM.1: Reliable time stampsFPT TST EXT.1: Extended: TSF Cryptographic Functionality TestingFPT TST EXT.2: Extended: TSF Integrity TestingFPT TUD EXT.1: Extended: Trusted Update: TSF version queryFPT TUD EXT.2: Extended: Trusted Update VerificationFTA SSL EXT.1: Extended: TSF- and User-initiated locked stateFTA TAB.1: Default TOE Access BannersFTA WSE EXT.1: Extended: Wireless Network AccessFTP ITC EXT.1: Extended: Trusted channel CommunicationTable 1 TOE Security Functional Components5.1.1 Cryptographic support (FCS)5.1.1.1 Refinement: Cryptographic key generation (FCS CKM.1(1))FCS CKM.1(1).1The TSF shall generate asymmetric cryptographic keys used for key establishment in accordancewith:- NIST Special Publication 800-56B, 'Recommendation for Pair-Wise Key Establishment SchemesUsing Integer Factorization Cryptography' for RSA-based key establishment schemes and[- NIST Special Publication 800-56A, 'Recommendation for Pair-Wise Key EstablishmentSchemes Using Discrete Logarithm Cryptography' for elliptic curve-based key establishmentPage 13 of 40
Samsung Electronics Co., Ltd. Samsung Galaxy Devices with Qualcomm Snapdragon Processors(MDFPP10) Security TargetVersion 1.1 04/30/14schemes and implementing 'NIST curves' P-256, P-384 and [P-521] (as defined in FIPS PUB186-4, 'Digital Signature Standard')]and specified cryptographic key sizes equivalent to, or greater than, a symmetric key strength of112 bits.5.1.1.2 Cryptographic key generation (FCS CKM.1(2))FCS CKM.1(2).1Th
Samsung Galaxy Devices with Qualcomm Snapdragon Processors including the Galaxy S4, Galaxy Note 3, and the Galaxy NotePRO Tablet. 1.4 TOE Description The TOE is a mobile operating system based on
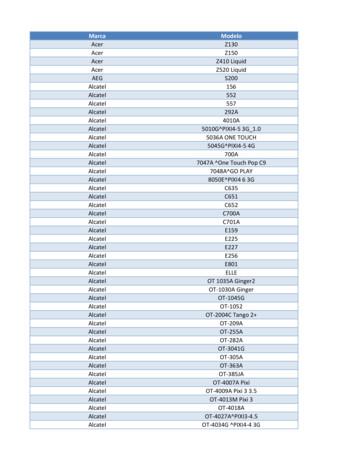
Samsung SGH-D807 Samsung SGH-D900 Samsung SGH-E215L Samsung SGH-E251L Samsung SGH-E256 Samsung SGH-E316 Samsung SGH-E356 Samsung SGH-E376 Samsung SGH-E496 Samsung SGH-E608 Samsung SGH-E630 Samsung SGH-E720 Samsung SGH-E736. Marca Modelo Samsung SGH-E786 Samsung SGH-E906 Samsung SGH-F250L Samsung SGH
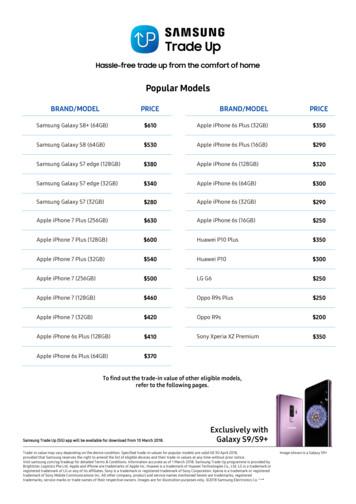
Samsung Galaxy S6 (32GB) 100 Samsung Galaxy S5 60 Samsung Galaxy A9 Pro 250 Samsung Galaxy A8 100 Samsung Galaxy A7 2017 200 Samsung Galaxy A7 2016 130 Samsung Galaxy A7 50 Samsung Galaxy A5 2017 150 Samsung Galaxy A5 2016 100 Samsung Galaxy A5 50 Samsung Galaxy A3 2016 80 Samsung Galaxy
- Samsung Electronics Co., Ltd. ("SEC" or "the Company") was established as Samsung Electronics Industry Co., Ltd. on January 13, 1969, and held an initial public offering on June 11, 1975. - SEC changed its name from Samsung Electronics Industry Co., Ltd. to Samsung Electronics Co., Ltd. following a
Billericay Dental Supply Co. Ltd Birds (Derby) Ltd Blackpool Pleasure Beach (Holdings) Ltd Bloom and Wild Ltd BOC Ltd Boohoo.Com UK Ltd Booker Group Ltd Borax Europe Ltd Borden International Holdings Ltd Bowman Ingredients Ltd BP International Ltd Brake Bros Ltd Brand Addition Ltd Brand-Rex Ltd Brenntag UK Ltd Bridport Ltd Brightstar 20:20 UK Ltd
Samsung Electronics America (SEA), Inc. Address: 85 Challenger Road Ridgefield Park, New Jersey 07660 Phone: 1-800-SAMSUNG (726-7864) Internet Address: samsung.com 2016 Samsung Electronics America, Inc. Samsung, Samsung Galaxy, Multi Window, S Pen, S Health, S Voice, Samsung Pay, and Samsung Milk Music are all
Samsung Electronics Co., Ltd. 129 Samsung-ro, Yeongtong-gu, Suwon-si, Gyeonggi-do 443-742, Korea www.samsung.com 2015-08 About Samsung Electronics Co., Ltd. Samsung Electronics Co., Ltd. inspires the world and shapes the future with transformative ideas and technologies, redefining the worlds of TVs, smartphones, wearable devices,
Samsung Electronics Co., Ltd. Samsung Galaxy Devices on Android 9 (MDFPP31/WLANCEP10/VPNC21) Security Target Version: 0.5 2019/10/16 Prepared for: Samsung Electronics Co., Ltd. 416 Maetan-3dong, Yeongtong-gu, Suwon-si, Gy
Samsung Electronics Co., Ltd. Samsung Galaxy VPN Client on Android 6 (IVPNCPP14) Security Target Version 0.21 2016/12/13 Prepared for: Samsung Electronics Co., Ltd. 416 Maetan-3dong, Yeongtong-gu, Suwon-si, Gyeonggi-do, 443-742 Korea Prepared By: www.gossamersec.com