Show N Show O - Cisco
show n – show o show nac-policy, on page 2 show nameif, on page 4 show nat, on page 6 show nat divert-table, on page 9 show nat pool, on page 11 show nat proxy-arp, on page 15 show ntp associations, on page 17 show ntp status, on page 21 show nve, on page 23 show object, on page 26 show object-group, on page 27 show ospf, on page 30 show ospf border-routers, on page 32 show ospf database, on page 33 show ospf events, on page 37 show ospf flood-list, on page 39 show ospf interface, on page 41 show ospf neighbor, on page 43 show ospf nsf, on page 45 show ospf request-list, on page 46 show ospf retransmission-list, on page 47 show ospf rib, on page 49 show ospf statistics, on page 50 show ospf summary-address, on page 52 show ospf traffic, on page 53 show ospf virtual-links, on page 55show n – show o1
show n – show oshow nac-policyshow nac-policyTo show the NAC policy usage statistics and the assignment of NAC policies to group policies, use the shownac-policy command in privileged EXEC mode.show nac-policy [ nac-policy-name ]Syntax Descriptionnac-policy-name (Optional) Name of the NAC policy for which to display usage statistics.Command DefaultIf you do not specify a name, the CLI lists all NAC policy names along with their respective statistics.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity XECCommand History Yes—— YesRelease Modification8.0(2)Examples YesSystemThis command was added.The following example shows the data for the NAC policies named framework1 and framework2:ciscoasa(config)# show nac-policynac-policy framework1 nac-frameworkapplied session count 0applied group-policy count 2group-policy list:GroupPolicy2GroupPolicy1nac-policy framework2 nac-framework is not in use.The first line of each NAC policy indicates its name and type (nac-framework). The CLI shows thetext “is not in use” next to the policy type if the policy is not assigned to any group policies. Otherwise,the CLI displays the usage data for the group policy. Table 10-1 explains the fields in the shownac-policy command.Table 1: show nac-policy Command FieldsFieldDescriptionapplied session countCumulative number of VPN sessions to which this ASA applied the NAC policy.applied group-policy count Cumulative number of group polices to which this ASA applied the NAC policy.show n – show o2
show n – show oshow nac-policyRelated CommandsFieldDescriptiongroup-policy listList of group policies to which this NAC policy is assigned. In this case, theusage of a group policy does not determine whether it appears in this list; if theNAC policy is assigned to a group policy in the running configuration, then thegroup policy appears in this list.clear nac-policyResets the NAC policy usage statistics.show vpn-session.dbDisplays information about VPN sessions, including NAC results.show vpn-session summary.db Displays the number IPSec, Cisco WebVPN, and NAC sessions.show n – show o3
show n – show oshow nameifshow nameifTo view the interface name set using the nameif command, use the show nameif command in privilegedEXEC mode.show nameif [ physical interface [ .subinterface ] mapped name zone ]Syntax DescriptionCommand Defaultmapped name(Optional) In multiple context mode, identifies the mapped name if it was assignedusing the allocate-interface command.physical interface(Optional) Identifies the interface ID, such as gigabit ethernet0/1 . See the interfacecommand for accepted values.subinterface(Optional) Identifies an integer between 1 and 4294967293 designating a logicalsubinterface.zone(Optional) Shows the zone names.If you do not specify an interface, the ASA shows all interface names.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity XECCommand History Yes Yes Yes YesSystem—Release Modification7.0(1)This command was added.9.3(2)The zone keyword was added.Usage GuidelinesIn multiple context mode, if you mapped the interface ID in the allocate-interface command, you can onlyspecify the mapped name in a context. The output for this command shows only the mapped name in theInterface column.ExamplesThe following is sample output from the show nameif command:ciscoasa# show 1GigabitEthernet0/2show n – show o4Nameoutsideinsidetest2Security010050
show n – show oshow nameifSee the following output for the show nameif zone command:ciscoasa# show nameif thernet0/2outsideManagement0/0lanRelated faceAssigns interfaces and subinterfaces to a security context.interfaceConfigures an interface and enters interface configuration mode.nameifSets the interface name.show interface ip briefShows the interface IP address and status.show n – show o5
show n – show oshow natshow natTo display statistics of NAT policies, use the show nat command in privileged EXEC mode.show nat [ interface name ][ ip addr [ mask ] { object object-group } name ][ translated [interface name ]{ ip addr [ mask ] { object object-group } name }] [ detail ]Syntax Descriptiondetail(Optional) Includes more verbose expansion of the object fields.interface name(Optional) Specifies the source interface.ip addr [ mask ](Optional) Specifies an IP address and subnet mask.object name(Optional) Specifies a network object or service object.object-group name (Optional) Specifies a network object grouptranslatedCommand Default(Optional) Specifies the translated parameters.No default behavior or values.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity XECCommand History Yes Yes Yes YesSystem—Release Modification8.3(1)This command was added.9.0(1)Support for IPv6 traffic, as well as translations between IPv4 and IPv6 were added.Usage GuidelinesUse the show nat command to show runtime representation of the NAT policy. Use the detail optionalkeyword to expand the object and view the object values. Use the additional selector fields to limit the shownat command output.ExamplesThe following is sample output from the show nat command:ciscoasa# show natManual NAT Policies (Section 1)1 (any) to (any) source dynamic S S' destination static D' Dtranslate hits 0, untranslate hits 0show n – show o6
show n – show oshow natAuto NAT Policies (Section 2)1 (inside) to (outside) source dynamic A 2.2.2.2translate hits 0, untranslate hits 0Manual NAT Policies (Section 3)1 (any) to (any) source dynamic C C' destination static B' B service R R'translate hits 0, untranslate hits 0ciscoasa# show nat detailManual NAT Policies (Section 1)1 (any) to (any) source dynamic S S' destination static D' Dtranslate hits 0, untranslate hits 0Source - Real: 1.1.1.2/32, Mapped: 2.2.2.3/32Destination - Real: 10.10.10.0/24, Mapped: 20.20.20.0/24Auto NAT Policies (Section 2)1 (inside) to (outside) source dynamic A 2.2.2.2translate hits 0, untranslate hits 0Source - Real: 1.1.1.1/32, Mapped: 2.2.2.2/32Manual NAT Policies (Section 3)1 (any) to (any) source dynamic C C' destination static B' B service R R'translate hits 0, untranslate hits 0Source - Real: 11.11.11.10-11.11.11.11, Mapped: 192.168.10.10/32Destination - Real: 192.168.1.0/24, Mapped: 10.75.1.0/24Service - Real: tcp source eq 10 destination eq ftp-data , Mapped: tcp source eq100 destination eq 200The following is sample output from the show nat detail command between IPv6 and IPv4:ciscoasa# show nat detail1 (in) to (outside) source dynamic inside nw outside map destination static inside map anytranslate hits 0, untranslate hits 0Source - Origin: 2001::/96, Translated: 192.168.102.200-192.168.102.210Destination - Origin: 2001::/96, Translated: 0.0.0.0/0Starting with version 9.16, Section 0 shows the system-defined NAT rules, which are needed for thesystem to function properly. These show rules for internal interfaces, such as nlp int tap. Theserules take priority over all other rules. You cannot add or change rules in Section 0.ciscoasa(config)# show nat detailManual NAT Policies Implicit (Section 0)1 (nlp int tap) to (inside) source dynamic nlp client 0 0.0.0.0 17proto53 intf3 interfacedestination static nlp client 0 ipv4 2 nlp client 0 ipv4 2 service nlp client 0 17svc53 1nlp client 0 17svc53 1translate hits 0, untranslate hits 0Source - Origin: 169.254.1.2/32, Translated: 10.99.11.7/24Destination - Origin: 0.0.0.0/0, Translated: 0.0.0.0/0Service - Origin: udp destination eq domain , Translated: udp destination eq domain2 (nlp int tap) to (inside) source dynamic nlp client 0 intf3 interfacetranslate hits 0, untranslate hits 0Source - Origin: 169.254.1.2/32, Translated: 10.99.11.7/243 (nlp int tap) to (inside) source dynamic nlp client 0 ipv6 :: 17proto53 intf3 interfaceipv6 destination static nlp client 0 ipv6 4 nlp client 0 ipv6 4 servicenlp client 0 17svc53 3 nlp client 0 17svc53 3translate hits 0, untranslate hits 0Source - Origin: fd00:0:0:1::2/128, Translated:Destination - Origin: ::/0, Translated: ::/0Service - Origin: udp destination eq domain , Translated: udp destination eq domainshow n – show o7
show n – show oshow natRelated CommandsCommandDescriptionclear nat countersClears NAT policy counters.natIdentifies addresses on one interface that are translated to mapped addresses on anotherinterface.show n – show o8
show n – show oshow nat divert-tableshow nat divert-tableTo display statistics of NAT divert table, use the show nat divert-table command in privileged EXEC mode.show nat divert-table [ ipv6 ][ interface name ]Syntax DescriptionCommand Defaultipv6(Optional) Shows IPv6 entries in the divert table.interfacename(Optional) Limits output to the specified source interface.No default behavior or values.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity XECCommand History Yes Yes Yes YesSystem—Release Modification8.4(2)This command was added.Usage GuidelinesUse the show nat divert-table command to show runtime representation of the NAT divert table. Use theipv6 optional keyword to view the IPv6 entries in the divert table. Use the interface optional keyword to viewthe NAT divert table for the specific source interface.ExamplesThe following is sample output from the show nat divert-table command:ciscoasa# show nat divert-tableDivert Tableid 0xad1521b8, domain twice-nat section 1 ignore notype none, hits 0, flags 0x9, protocol 0src ip/id 0.0.0.0, mask 0.0.0.0, port 0-0dst ip/id 10.86.119.255, mask 255.255.255.255, port 0-0input ifc outside, output ifc NP Identity Ifcid 0xad1523a8, domain twice-nat section 1 ignore notype none, hits 0, flags 0x9, protocol 0src ip/id 0.0.0.0, mask 0.0.0.0, port 0-0dst ip/id 10.86.116.0, mask 255.255.255.255, port 0-0input ifc outside, output ifc NP Identity Ifcid 0xad1865c0, domain twice-nat section 1 ignore notype none, hits 0, flags 0x9, protocol 0src ip/id 0.0.0.0, mask 0.0.0.0, port 0-0dst ip/id 192.168.255.255, mask 255.255.255.255, port 0-0show n – show o9
show n – show oshow nat divert-tableinput ifc amallio-wizard, output ifc NP Identity Ifcid 0xad1867b0, domain twice-nat section 1 ignore notype none, hits 0, flags 0x9, protocol 0src ip/id 0.0.0.0, mask 0.0.0.0, port 0-0dst ip/id 192.168.0.0, mask 255.255.255.255, port 0-0input ifc amallio-wizard, output ifc NP Identity Ifcid 0xad257bf8, domain twice-nat section 1 ignore notype none, hits 0, flags 0x9, protocol 0src ip/id 0.0.0.0, mask 0.0.0.0, port 0-0dst ip/id 172.27.48.255, mask 255.255.255.255, port 0-0input ifc folink, output ifc NP Identity Ifcid 0xad257db8, domain twice-nat section 1 ignore notype none, hits 0, flags 0x9, protocol 0src ip/id 0.0.0.0, mask 0.0.0.0, port 0-0dst ip/id 172.27.48.0, mask 255.255.255.255, port 0-0input ifc folink, output ifc NP Identity IfcThe following is sample output from the show nat divert ipv6 command:ciscoasa# show nat divert ipv6Divert Tableid 0xcb9ea518, domain divert-routetype static, hits 0, flags 0x21, protocol 0src ip/id 2001::/ffff:ffff:ffff:ffff:ffff:ffff::, port 0-0dst ip/id 2001::/ffff:ffff:ffff:ffff:ffff:ffff::, port 0-0input ifc in, output ifc outsideid 0xcf24d4b8, domain divert-routetype static, hits 0, flags 0x20, protocol 0src ip/id ::/::, port 0-0dst ip/id 2222::/ffff:ffff:ffff:ffff:ffff:ffff::, port 0-0input ifc in, output ifc mgmtRelated CommandsCommandDescriptionclear natcountersClears NAT policy counters.natIdentifies addresses on one interface that are translated to mapped addresses on anotherinterface.show natDisplays runtime representation of the NAT policies.show n – show o10
show n – show oshow nat poolshow nat poolTo display statistics of NAT pool usage, use the show nat pool command in privileged EXEC mode.show nat pool [ interface if name [ ip address ] ip address ][ detail ]show nat pool cluster [ summary interface if name [ ip address ] ip address ]Syntax Descriptioncluster [ summary ] (Optional) When ASA clustering is enabled, shows the current assignment of a PATaddress to the owner unit and backup unit.(9.15 ) Include the summary keyword to see the distribution of port blocks amongthe units in the cluster.Command Defaultinterface if nameLimit the display to pools for the named interface. You can optionally include theip keyword to futher limit the view.ip addressLimit the display to the specified IP address from the PAT pool.detailShow information related to the usage and distribution of port blocks within a cluster.This keyword appears only if the unit is a cluster member. You cannot use it withthe cluster keyword.This command has no default settings.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity XECCommand History Yes Yes Yes YesSystem—Release Modification8.3(1)This command was added.8.4(3)The output was modified to show the destination address for extended PAT. The PAT range wasalso modified depending on the use of the flat and include-reserve keywords.9.0(1)Support for IPv6 traffic and the cluster keyword to show the current assignment of a PAT addressto the owner unit and backup unit were added.9.15(1) The following keywords were added: interface , ip , detail , summary .show n – show o11
show n – show oshow nat poolUsage GuidelinesA NAT pool is created for each mapped protocol/IP address/port range. (Pre-9.15) The port ranges are 1-511,512-1023, and 1024-65535 by default. If you use the flat keyword for a PAT pool in the nat command,you will see fewer, larger ranges.(9.15 ) Starting with 9.15, the port range is flat by default, and you can optionally include the reserved ports,1-1023, in the pool. For clustered systems, the PAT pool is distributed among the cluster members in blocksof 512 ports.Each NAT pool exists for at least 10 minutes after the last usage. The 10 minute hold-down timer is canceledif you clear the translations with clear xlate .ExamplesThe following is sample output for the NAT pools created by a dynamic PAT rule shown by theshow running-config object network command.ciscoasa(config)# show running-config object networkobject network myhosthost 10.10.10.10nat (pppoe2,inside) dynamic 10.76.11.25ciscoasa# shownat poolTCP inside, address 10.76.11.25, range 1-511, allocated 0TCP inside, address 10.76.11.25, range 512-1023, allocated 0TCP inside, address 10.76.11.25, range 1024-65535, allocated 1(Pre-9.15) The following is sample output from the show nat pool command showing use of thePAT pool flat option. Without the include-reserve keyword, two ranges are shown; the lowerrange is used when a source port below 1024 is mapped to the same port.ciscoasa# shownat poolICMP PAT pool dynamic-pat, address 172.16.2.200, range 1-65535, allocated 2TCP PAT pool dynamic-pat, address 172.16.2.200, range 1-1024, allocated 0TCP PAT pool dynamic-pat, address 172.16.2.200, range 1024-65535, allocated 2UDP PAT pool dynamic-pat, address 172.16.2.200, range 1-1024, allocated 0UDP PAT pool dynamic-pat, address 172.16.2.200, range 1024-65535, allocated 2(Pre-9.15) The following is sample output from the show nat pool command showing use of thePAT pool flat include-reserve options.ciscoasa# shownat poolICMP PAT pool dynamic-pat, address 172.16.2.200, range 1-65535, allocated 2TCP PAT pool dynamic-pat, address 172.16.2.200, range 1-65535, allocated 2UDP PAT pool dynamic-pat, address 172.16.2.200, range 1-65535, allocated 2(Pre-9.15) The following is sample output from the show nat pool command showing use of thePAT pool extended flat include-reserve options. The important items are the parentheticaladdresses. These are the destination addresses used to extend PAT.ICMP PAT pool dynamic-pat, address 172.16.2.200, range 1-65535, allocated 0ICMP PAT pool dynamic-pat, address 172.16.2.200(172.16.2.99), range 1-65535, allocated 2TCP PAT pool dynamic-pat, address 172.16.2.200(172.16.2.100), range 1-65535, allocated 1UDP PAT pool dynamic-pat, address 172.16.2.200(172.16.2.100), range 1-65535, allocated 1TCP PAT pool dynamic-pat, address 172.16.2.200, range 1-65535, allocated 0ICMP PAT pool dynamic-pat, address 172.16.2.200(172.16.2.100), range 1-65535, allocated 1TCP PAT pool dynamic-pat, address 172.16.2.200(172.16.2.99), range 1-65535, allocated 2UDP PAT pool dynamic-pat, address 172.16.2.200, range 1-65535, allocated 0show n – show o12
show n – show oshow nat pool(9.15 ) The following example shows the distribution of port blocks (showing the port range), andtheir usage, in a cluster, including the unit that owns the block and the backup unit for the block.ciscoasa# show nat pool clusterIP outside a:src map a 174.0.1.20[1536 – 2047], owner A, backup B[8192 – 8703], owner A, backup B[4089 – 4600], owner B, backup A[11243 – 11754], owner B, backupIP outside a:src map a 174.0.1.21[1536 – 2047], owner A, backup B[8192 – 8703], owner A, backup B[4089 – 4600], owner B, backup A[11243 – 11754], owner B, backupIP outside b:src map b 174.0.1.22[6656 - 7167], owner A, backup B[13312 - 13823], owner A, backup[20480 - 20991], owner B, backup[58368 - 58879], owner B, backupIP outside b:src map b 174.0.1.23[46592 - 47103], owner A, backup[52224 - 52735], owner A, backup[62976 - 63487], owner B, backupAABAABBA(9.15 ) The following example shows a summary of pool assignments in a cluster.ciscoasa# show nat pool cluster summaryport-blocks count display order: total,IP outside a:src map a, 174.0.1.20 (128IP outside a:src map a, 174.0.1.21 (128IP outside b:src map b, 174.0.1.22 (128unit-A, unit-B, unit-C, unit-D- 32/32/32/32)- 36/32/32/28)- 31/32/32/33)(9.15 ) The following example shows detailed PAT pool usage for the pools in a cluster.ciscoasa# show nat pool detailTCP PAT pool outside a, address 174.0.1.1range 1536-2047, allocated 56range 8192-8703, allocated 16UDP PAT pool outside a, address 174.0.1.1range 1536-2047, allocated 12range 8192-8703, allocated 25TCP PAT pool outside b, address 174.0.2.1range 47104-47615, allocated 39range 62464-62975, allocated 9UDP PAT pool outside b, address 174.0.2.1range 47104-47615, allocated 35range 62464-62975, allocated 27(9.15 ) The following example shows how to limit the view to a specific interface on a specificdevice.ciscoasa# show nat pool interface outside b ip utside b,outside b,outside b,outside 174.0.2.1,174.0.2.1,rangerangerangerange1-511, allocated 0512-1023, allocated 121024-65535, allocated 481-511, allocated 6show n – show o13
show n – show oshow nat poolUDP PAT pool outside b, address 174.0.2.1, range 512-1023, allocated 8UDP PAT pool outside b, address 174.0.2.1, range 1024-65535, allocated 62Related CommandsCommand DescriptionnatIdentifies addresses on one interface that are translated to mapped addresses on another interface.show nat Displays NAT policy statistics.show n – show o14
show n – show oshow nat proxy-arpshow nat proxy-arpTo display the NAT proxy ARP table, use the show nat proxy-arp command in privileged EXEC mode.show nat proxy-arp [ ipv6 ] [ interface name ]Syntax DescriptionCommand Defaultipv6(Optional) Shows IPv6 entries in the proxy ARP table.interfacename(Optional) Limits output to the specified source interface.No default behavior or values.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity XECCommand History Yes Yes Yes YesSystem—Release Modification8.4(2)This command was added.Usage GuidelinesUse the show nat proxy-arp command to show runtime representation of the NAT proxy ARP table. Usethe ipv6 optional keyword to view the IPv6 entries in the proxy ARP table. Use the interface optional keywordto view the NAT proxy ARP table for the specific source interface.ExamplesThe following is sample output from the show nat proxy-arp command:ciscoasa# show nat proxy-arpNat Proxy-arp Tableid 0x00007f5558bbbfc0, ip/id 10.10.1.134, mask 255.255.255.255 ifc test2config:(inside) to (test2) source dynamic inside v6 outside v4 pat destinationstatic inside v6 nat anyid 0x00007f5558bbbfc0, ip/id 10.10.1.135, mask 255.255.255.255 ifc test2config:(inside) to (test2) source dynamic inside v6 outside v4 pat destinationstatic inside v6 nat anyid 0x00007f55595ad2c0, ip/id 10.86.118.2, mask 255.255.255.255 ifc insideconfig:(inside) to (test2) source dynamic inside v6 interface dnsid 0x00007f5559424e80, ip/id 10.100.10.1, mask 255.255.255.255 ifc NP Identity Ifcconfig:(any) to (any) source dynamic src network pat-pool mapped-pat-poolid 0x00007f5559424e80, ip/id 10.100.10.2, mask 255.255.255.255 ifc NP Identity Ifcconfig:(any) to (any) source dynamic src network pat-pool mapped-pat-poolid 0x00007f5544785700, ip/id 10.7.17.2, mask 255.255.255.254 ifc NP Identity Ifcshow n – show o15
show n – show oshow nat proxy-arpconfig:(any) to (any) source static test2 10.3.3.0id 0x00007f554c4ae740, ip/id 10.1.1.1, mask 255.255.255.255 ifc NP Identity IfcRelated CommandsCommandDescriptionclear natcountersClears NAT policy counters.natIdentifies addresses on one interface that are translated to mapped addresses on anotherinterface.show natDisplays runtime representation of the NAT policies.show n – show o16
show n – show oshow ntp associationsshow ntp associationsTo view NTP association information, use the show ntp associations command in user EXEC mode.show ntp associations [ detail ]Syntax Descriptiondetail (Optional) Shows additional details about each association.Command DefaultNo default behavior or values.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity ContextTransparentSingleMultipleContextUser EXECCommand History Yes Yes YesSystem— YesRelease Modification7.0(1)This command was added.Usage GuidelinesSee the “Examples” section for a description of the display output.ExamplesThe following is sample output from the show ntp associations command:ciscoasa show ntpaddress 172.31.32.2 192.168.13.33* 192.168.13.57* master (synced),associationsref clockst when poll reach delay offsetdisp172.31.32.1529 1024 3774.2-8.591.6192.168.1.111369128 3774.13.482.3192.168.1.111332128 3777.911.183.6# master (unsynced), selected, - candidate, configuredTable 10-2 shows each field description.show n – show o17
show n – show oshow ntp associationsTable 2: show ntp associations FieldsFieldDescription(leading characters in display The first characters in a display line can be one or more of the followinglines)characters: * —Synchronized to this peer. # —Almost synchronized to this peer. —Peer selected for possible synchronization. - —Peer is a candidate for selection. —Peer is statically configured, but not synchronized.addressThe address of the NTP peer.ref clockThe address of the reference clock of the peer.stThe stratum of the peer.whenThe time since the last NTP packet was received from the peer.pollThe polling interval (in seconds).reachThe peer reachability (as a bit string, in octal).delayThe round-trip delay to the peer (in milliseconds).offsetThe relative time of the peer clock to the local clock (in milliseconds).dispThe dispersion value.ExamplesThe following is sample output from the show ntp associations detail command:ciscoasa show ntp associations detail172.23.56.249 configured, our master, sane, valid, stratum 4ref ID 172.23.56.225, time c0212639.2ecfc9e0 (20:19:05.182 UTC Fri Febour mode client, peer mode server, our poll intvl 128, peer poll intvlroot delay 38.04 msec, root disp 9.55, reach 177, sync dist 156.021delay 4.47 msec, offset -0.2403 msec, dispersion 125.21precision 2**19, version 3org time c02128a9.731f127b (20:29:29.449 UTC Fri Feb 22 2002)rcv time c02128a9.73c1954b (20:29:29.452 UTC Fri Feb 22 2002)xmt time c02128a9.6b3f729e (20:29:29.418 UTC Fri Feb 22 2002)filtdelay 4.474.584.975.634.795.525.87filtoffset -0.24-0.36-0.370.30-0.170.57-0.74filterror 0.020.991.712.693.664.645.62Table 10-3 shows each field description.show n – show o1822 2002)1280.000.0016000.0
show n – show oshow ntp associationsTable 3: show ntp associations detail FieldsFieldDescriptionIP-address configured The server (peer) IP address.(status) our master—The ASA is synchronized to this peer. selected—Peer is selected for possible synchronization. candidate—Peer is a candidate for selection.(sanity) sane—The peer passes basic sanity checks. insane—The peer fails basic sanity checks.(validity) valid—The peer time is believed to be valid. invalid—The peer time is believed to be invalid. leap add—The peer is signaling that a leap second will be added. leap-sub—The peer is signaling that a leap second will besubtracted.stratumThe stratum of the peer.(reference peer)unsynced—The peer is not synchronized to any other machine.ref ID—The address of the machine that the peer is synchronized to.timeThe last time stamp the peer received from its master.our mode clientOur mode relative to the peer, which is always client.peer mode serverThe mode of the peer relative to the server.our poll intvlOur poll interval to the peer.peer poll intvlThe peer poll interval to us.root delayThe delay along the path to the root (ultimate stratum 1 time source).root dispThe dispersion of the path to the root.reachThe peer reachability (as a bit string in octal).sync distThe peer synchronization distance.delayThe round-trip delay to the peer.offsetThe offset of the peer clock relative to our clock.dispersionThe dispersion of the peer clock.precisionThe precision of the peer clock (in hertz).show n – show o19
show n – show oshow ntp associationsRelated CommandsFieldDescriptionversionThe NTP version number that the peer is using.org timeThe originate time stamp.rcv timeThe receive time stamp.xmt timeThe transmit time stamp.filtdelayThe round-trip delay (in milliseconds) of each sample.filtoffsetThe clock offset (in milliseconds) of each sample.filterrorThe approximate error of each sample.CommandDescriptionntp authenticateEnables NTP authentication.ntpauthentication-keySets an encrypted authentication key to synchronize with an NTP server.ntp serverIdentifies an NTP server.ntp trusted-keyProvides a key ID for the ASA to use in packets for authentication with an NTPserver.show ntp statusShows the status of the NTP association.show n – show o20
show n – show oshow ntp statusshow ntp statusTo show the status of each NTP association, use the show ntp status command in user EXEC mode.show ntp statusSyntax DescriptionThis command has no arguments or keywords.Command DefaultNo default behavior or values.Command ModesThe following table shows the modes in which you can enter the command:Command Mode Firewall ModeRoutedSecurity ContextTransparentSingleMultipleContextUser EXECCommand History Yes Yes YesSystem— YesRelease Modification7.0(1)This command was added.Usage GuidelinesSee the “Examples” section for a description of the display output.ExamplesThe following is sample output from the show ntp status command:ciscoasa show ntp statusClock is synchronized, stratum 5, reference is 172.23.56.249nominal freq is 99.9984 Hz, actual freq is 100.0266 Hz, precision is 2**6reference time is c02128a9.73c1954b (20:29:29.452 UTC Fri Feb 22 2002)clock offset is -0.2403 msec, root delay is 42.51 msecroot dispersion is 135.01 msec, peer dispersion is 125.21 msecTable 10-4 shows each field description.Table 4: show ntp status FieldsFieldClockDescription synchronized—The ASA is synchronized to an NTP server. unsynchronized—The ASA is not synchronized to an NTPserver.stratumNTP stratum of this system.referenceThe address of the NTP server to which the ASA is synchronized.show n – show o21
show n – show oshow ntp statusFieldDescriptionnominal freqThe nominal frequency of the system hardware clock.actual freqThe measured frequency of the system hardware clock.precisionThe precision of the clock of this system (in hertz).reference time The reference time stamp.clock offsetThe offset of the system clock to the synchronized peer.root delayThe total delay along the path to the root clock.root dispersion The dispersion of the root path.peerdispersionRelated CommandsThe dispersion of the synchronized peer.CommandDescriptionntp authenticateEnables NTP authentication.ntpauthentication-keySets an encrypted authentication key to synchronize with an NTP server.ntp serverIdentifies an NTP server.ntp trusted-keyPr
shownac-policy To show the NAC policy usage statistics and the assignment of NAC policies to group policies, use the show nac-policy command in privileged EXEC mode. show nac-policy [nac-policy-name] SyntaxDescription nac-policy-name (Optional) Name of the NAC policy for which to display usage statistics. CommandDefault If you do not specify a name, the
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
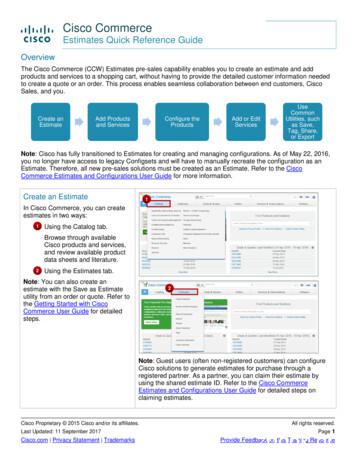
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unified Computing System (Cisco UCS), Cisco UCS B-Series Blade Servers, Cisco UCS C-Series Rack Servers, Cisco UCS S-Series Storage Servers, Cisco UCS Manager, Cisco UCS
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base