A Secure Personal-Data Trading System Based On Blockchain .
A Secure Personal-Data Trading SystemBased on Blockchain, Trust, and ReputationGustavo F. Camilo, Gabriel Antonio F. Rebello,Lucas Airam C. de Souza, Otto Carlos M. B. DuarteGrupo de Teleinformática e Automação (GTA) - COPPEUniversidade Federal do Rio de Janeiro (UFRJ)Abstract—Every citizen has the right to privacy and, therefore,the right to control their personal information, deciding towhom, when, and where their information is available. Thispaper proposes a secure, agile, and effective system for adistributed, automatic, and transparent data trading betweendomains using blockchain, smart contracts, trust, and reputation.We develop and implement a prototype of a trust and reputationsystem based on real-life interactions. The results show that theproposed system provides security and privacy in a quick anddistributed way, performing hundreds of transactions per second,and effectively punishing malicious behavior.I. I NTRODUCTIONPersonal-data access control is becoming a major concernas devices increasingly delegate the storage of sensitive datato cloud-based centralized authorities [1]. The centralizedauthorities, such as governments and companies, may thenaccess, control, and share personal user data with third parties.For the owner of the data, using centralized data-storagesolutions implies losing control of personal data, paying highfees, signing terms that often compromise privacy, and still besubject to data leaks. Besides, even if the centralized authoritybehaves honestly, malicious users often compromise cloudbased services through internal attacks and denial of service(DoS) attacks. A more efficient way to ensure security andprivacy while preserving the owner’s control over the data isto use blockchain technology, which provides a distributed andauditable solution for storing personal data.In a previous article [2], we proposed a blockchain-basedsystem to commercialize data in a safe, automatic, and distributed way. The system uses the integrity and auditabilityproperties of the blockchain to store each users’ access permissions to private and sensitive data.Despite maintaining the record immutability of assets transfer, the blockchain does not guarantee the delivery of datastored off-chain nor their quality. Malicious sellers can takeadvantage of this vulnerability to advertise false data or failto deliver data acquired by honest buyers. Thus, the systemis unable to prevent malicious behavior by sellers, causingdamages to buyers who take legitimate actions. A trust andreputation system (TRS) allows the identification of maliciousbehaviors, in addition to presenting an insight into the qualityof the data from buyers’ evaluations. A reputation systemintegrated with the blockchain can provide assessments of datasellers’ reputation as well as the quality of the data advertisedin a transparent and distributed manner. In this way, buyers canquickly check the reputation of an advertisement and decidewhether or not to acquire the data.This paper proposes a secure data marketplace system basedon blockchain, reputation, and trust. The main contributionsare as follows: The creation of a data marketplace environment inan automatic and distributed way between domains, inwhich data owners and buyers can advertise and acquiredata through the blockchain. The proposed marketplacescheme is automatic through smart contracts. A reputation and trust system that considers the historyof interactions and the participants’ opinions to build aseller’s reputation. An efficient data trading model for advertising and purchasing based on transactions in the blockchain. Thetransactions include the assessment of the seller and thequality of the advertised data. Development of the transaction and trust/reputation models. Performance evaluation results of a developed prototype show that the proposed system is effective inpunishing the malicious behavior of a seller.II. R ELATED W ORKSeveral works investigate the use of trust and reputation toprovide secutiy in computer networks. Velloso et al. proposea trust model based on human interactions to establish trustamong nodes in a ad hoc network [3]. Kamvar et al. proposethe Eigentrust algorithm that assigns a global trust value toeach peer in a peer-to-peer (P2P) file-sharing system [4].The algorithm is based on the past file uploads of each peerand uses indirect trust to calculate the global trust view ofthe system. Sun et al. presents defense mechanisms againstattacks on trust and reputations in a mobile ad hoc network(MANET) [5], [6].The blockchain technology can provide auditability andtraceability in trustless environments [7], [8], [9]. We considerthe concepts of the cited works and adapt them to a create atrust and reputation system that considers the properties ofblockchains and distrubuted trustless environments.Other works apply trust and reputation to blockchain.Oliveira et al. propose a blockchain reputation-based consensus (BRBC) [10]. Dennis and Owen propose a file transfer
TABLE IATTACKS AND COUNTERMEASURES PROPOSED FOR THE REPUTATION SYSTEMAttacksBad-mouthing attackOn-off attackSybil attackNewcomer attackConflicting-behavior attackDescriptionMalicious users publish false reports about a targetuser to affect the reputation of the target. This attack is mostpowerful when there is collusion between malicious nodes.A malicious user changes his/her behavior from legitimateto malicious and vice versa to damage the network withoutbeing identified.An attacker generates multiple false identities to increasehis/her influence in the system. An attacker can use theseidentities to perform a bad-mouthing attack on a target user.An attacker generates new identities repeatedly and pretendsto be a new user, to continue acting maliciously withoutbeing punished.An attacker can behave differently according to eachneighbor, creating conflicting recommendations fromwell-behaving nodes.reputation system in which the blockchain publicly storesusers’ recommendations [11]. The authors, however, do notoffer a solution to the on-off attack and do not implement andevaluate their proposal. Malik et al. propose a framework tomanage participants’ trust in a blockchain that records transfers in a supply chain [12]. Buyers, government authorities,and sensors attest to the quality of the product by issuingevaluations through transactions in the blockchain. A smartcontract calculates a trader’s reputation using a weighted sumof the entities’ ratings. The authors limit their proposal to thecase of a supply chain and disregard the product price whencalculating reputation. Furthermore, the proposal is susceptibleto on-off attacks, in which a user changes his/her behavior between legitimate and malicious, damaging the network withoutbeing detected.Putra et al. propose a trust and reputation managementsystem for blockchain-based systems to control the accessto IoT devices [13]. The system uses smart contracts toassess the trust and reputation of each node, detecting andeliminating malicious nodes from the network. The authors usereputation as an attribute to control access to a device, defininga minimum reputation that a participant must have to guaranteeaccess to data. The proposal, however, is susceptible to onoff attacks and does not reward the data owners. Moreover,the commercialization of data by the owners is a desirableproperty.Unlike the above mentioned articles, this paper proposesa trust and reputation system based on blockchain that iseffective in punishing malicious behavior and adapted toblockchain-based data marketplace. The complete marketplacesystem is secure, agile, and automatic, rewarding the sellerswho sell their private data and punishing malicious sellers.III. ATTACKER M ODELAttacks on the system of trust and reputation representan attempt by a malicious node to increase its reputation ordamage legitimate nodes reputation. We consider five attacks:(i) bad-mouthing attack; (ii) on-off attack; (iii) Sybil attack;(iv) newcomer attack; and (v) conflicting-behavior attack.Table I presents each attack and the proposed countermeasures.CountermeasuresTo use a dissatisfaction flag by a seller dissatisfied withan evaluation. The system logs requests and detectsmalicious nodes.To use an adaptive forgetting factor in reputation calculation.To use a permissioned blockchain and enforcing regulationsto sellers on a per-organization basis.To use a permissioned blockchain and enforcing regulationsto sellers on a per-organization basis.All users’ feedbacks are publicly verifiable as transactionsin the blockchain.We consider that a blockchain attacker aims to prevent aparticipant from adding a legitimate transaction or block tothe blockchain. The fault-tolerance property of the consensusprotocol requires that the attacker control the majority oforganizations to effectively affect the consensus protocol, mitigating this type of attack. The immutability and distributionproperty of the blockchain structure allow transaction andblock issuers to check if their proposal was correctly added tothe blockchain.Attacks on sellers or buyers try to obtain private and sensibleadvertised data or to impersonate the target. We consider thatall advertised data in the blockchain is encrypted, i.e., if theattacker gains access to the data, he/she must acquire thekey that decrypts it to obtain personal information about theseller. An attacker may try to impersonate the target to deceiveother participants. This attack, however, is not effective oncethe system requires that all issuers sign their transactions.Furthermore, the blockchain logs every attempt to modify itsstructure using a stolen pair of keys, allowing the victim toprevent further damage by replacing his/her stolen pair of keys.Our proposal considers network attacks as an attackertrying to isolate a participant to prevent him/her from issuingtransactions. We mitigate this type of attack by establishingredundant paths between the participants of the blockchainnetwork.IV. T HE P ROPOSED T RUST AND R EPUTATION S YSTEMWe define trust and reputation as distinct concepts in adistributed system1 . Trust is a buyer’s subjective view of aseller based on their previous interactions. Therefore, eachbuyer independently calculates and updates his/her trust in aseller. Conversely, reputation represents a global view of thesystem concerning a specific seller and consists of aggregatingindividual trusts of all buyers in the system.The main idea of our trust model is to simulate real-lifesocial interactions, in which trust gradually increases withpositive experiences and decreases significantly whenever anegative experience occurs. For seller trust, we also consider1 Asin Velloso et al. [3], in Malik et al. [12], and Putra et al. [13].
that recent interactions are more relevant than past interactionsto allow for possible changes in a seller’s behavior. The modeluses an adaptive ageing function, In , to implement the gradualforgetfulness of past interactions, given byIn nXβ (n i) δi ,(1)i 1where 0 β 1 is the forgetting factor, n is the total numberof interactions that occurred and δi is the value associated witheach interaction. If the i-th interaction is positive, δi δ 0.Otherwise, δi δ 0. By ensuring δ δ , negativeinteractions weigh more than positive interactions and we areable to simulate real-life trust.Unlike previous works that use fixed forgetting factors [12],[13], our work adopts a forgetting factor that adapts accordingto the probability that the seller will act honestly [5]. Wemodel the probability that a seller will be honest with a betadistribution of prior probability 12 , which corresponds to thedefault probability assumed by the system that an unknownseller will be honest. For each new interaction, the modelupdates the beta distribution via Bayesian inference and usesthe expected value, E[p], expressed byE[p] δ 1 βδ δ 2(2)to estimate the likelihood that the seller will be honest atthat time. The main advantage of using an adaptive forgettingfactor is mitigating on-off attacks, in which a malicious sellerbehaves well just enough to regain his/her reputation andbehave maliciously once again. With the adaptive forgettingfactor, if the probability that the seller is honest is high,i.e. E[p] 1, the system takes longer to forget the seller’spast, rewarding him for his/her good deeds. If the seller actsmaliciously, i.e. E[p] 0, the system quickly forgets his/herpast actions and the weight of his/her recent malicious actionson reputation is larger.After calculating In , we model the trust growth of a buyeri in a seller j, sij , using the Gompertz function. The functionsij is given bysij a exp( b exp( cIn )),(3)where a, b, and c are constants that represent the asymptote,the displacement parameter along the x-axis, and the trustgrowth rate, respectively. We choose the Gompertz functionbecause it increases gradually, simulating real-life trust [13],and we can easily shape it by adjusting its parameters.A. Seller ReputationOur seller reputation model aggregates the local values oftrust, taking inspiration from the Eigentrust algorithm [4]. TheEigentrust algorithm is one of the most cited and used trust algorithms for peer-to-peer (P2P) systems because it provides anefficient way to build reputation in distributed environments.The original proposal of the Eigentrust algorithm defines thenormalized local trust, cij , of a peer i in a known peer j asmax(sij , 0)cij P,j max(sij , 0)(4)where sij sat(i, j) unsat(i, j) is the difference betweensatisfactory and unsatisfactory interactions amongst the involved peers. Normalization transforms trust values into aprobability distribution that prevents a malicious peer fromissuing arbitrarily high trust values to other malicious peers.The algorithm then proposes that the natural way for a peeri to discover the reputation of an unknown peer k is to askhis/her acquaintances about their opinions on k. The opinionsof acquaintances receives weights proportional to the trust thatthe peer i has in each acquaintance. The trust, tik , the peer iplaces in peer k based on the opinions of his/her acquaintancesis expressed bytik Xcij cjk ci1 c1k ci2 c2k . cin cnk .(5)jOur proposed model replaces, without loss of generality, theoriginal sij equation with the Gompertz function proposed inEq. 3. The peers i and j that ask for opinions are equivalentto buyers who want to interact with a seller k. Generalizingthe Eq. 5 in the matrix notation for every buyer i, the trustvalue is t ik C T .c ik , where . c1nc1kt1k c2k t2k . c2n , c , t . . ik . ik . . cnncnktnk(6)The trust of buyer i in seller k, however, is a limited view basedon his/her own experience and that of his/her acquaintances.To get a broader view, buyer i can ask acquaintances of his/heracquaintances, given byc11 c21C .cn1c12c22.cn2t ik (C T )2 .c ik .(7)By repeating the process over and over, the buyer obtains acomplete view of the network after a sufficient number of niterations. Therefore, the final trust is expressed byt ik (C T )n .c ik .(8)We highlight that c ik , C, and t ik correspond, respectively,to the initial state, the probability matrix and the current stateof a stationary Markov chain. Hence, if n is large enough andif the matrix C is irreducible and aperiodic, the current statet ik of all buyers i will converge to the stationary state, r ik r1kr2k.rnk T,(9)regardless of the initial trust c ik each peer places in seller k.As r1k r2k . rnk , we can then conclude that anyelement of r ik represents the reputation Repk of a seller inthe system as a whole. Thus, we define a global reputationvector T r Rep1 Rep2 . Repn ,(10)
which contains the reputation of all sellers in the system andthat must be stored in the global state of the blockchain.V. I NTEGRATING T RUST AND R EPUTATION INTO THEB LOCKCHAINThe blockchain structure is similar to the one used in Camiloet al. [2] with the definition of three types of transaction fordata trading: i) advertisement transaction; ii) purchase transaction and iii) response transaction. We propose a feedbacktransaction in addition to the three transactions to introduce thetrust and reputation system. Data owners interested in makingtheir data available and commercialized send advertisementtransactions. The owner submits the advertised data to a storage server capable of supporting and processing large amountsof data [14] and issues a signed advertisement transaction. Thesystem requires the issuer to sign the transactions using asymmetric encryption to guarantee the authenticity and integrityof the transaction, preventing attackers from impersonatingthe target. The advertisement transaction must contain a briefdescription of the advertised data type, for example, data frommedical sensors, and the data price. Also, the transaction storesthe advertised data to maintain its integrity.Buyers search for data in the blockchain by querying advertisement transactions. Those interested in acquiring data advertised in the blockchain issue purchase transactions informingthe buyer’s IP address to an SDN controller, which reads thetransaction and grants access. The purchase transaction mustalso include the amount to be paid for the data, which will bededucted from the buyer’s account once the blockchain logsthe transaction. The smart contract associates the purchasetransaction with the corresponding advertisement using thetransaction identifier and checks if the paid amount is higherthan the amount required by the data owner.Data owners issue response transactions automatically afterthe data acquisition from a participant. The response transaction sends the buyer the key that decrypts the data. The keyis encrypted using the buyer’s public key to ensure that thestorage server does not have access to the decrypted data and,then, should not share the decrypted data with third parties.A smart contract executes the transactions before consensusparticipants order them in a block. This process consists of asmart contract that verifies if the paid amount is greater orequal than the data price requested by the owner and if theorganization owns enough tokens to accomplish the purchase.Peers validate transactions that meet the previous requirementsand invalidate those that do not. If the transaction is valid,the contract deduces the corresponding number of tokens paidfrom the buyer’s organization and sends it to the seller’sorganization, which can use these acquired tokens to buy datafrom other organizations.Our proposed system provides trust management in a distributed and autonomous way through smart contracts executed in the blockchain. We propose a feedback transactionT Xf b that relies on the smart contract function responsiblefor calculating a seller’s trust and reputation. The feedbacktransaction contains the corresponding purchase transactionidentifier to ensure that the purchase transaction exists and thatthe buyer needs to sign the evaluation transaction to ensurenon-repudiation. After purchasing data d from a seller s, abuyer b can issue a feedback transaction T Xf b defined asT Xf b [T XIDpur Sigb βb,dr λb,sr Tj ],(11)where T XIDpur is the corresponding purchase transaction, thefield Sigb is the buyer’s signature, the field βb,dr is the buyer’srating for the data d, the field λb,sr is the buyer’s rating forthe seller s, and the field Tj is a text in which the buyer canjustify his/her ratings to the rest of the network. The smartcontract defines “0” as a negative interaction and “1” as apositive interaction in the fields βb,dr and λb,sr .Figure 1 shows the complete data trading process betweentwo domains. If the seller considers the ratings βb,dr and λb,srunfair, he/she may display a dissatisfaction flag [12]. The smartcontract checks if: (i) the seller flags all negative ratings;(ii) the buyer rates all pu
A Secure Personal-Data Trading System Based on Blockchain, Trust, and Reputation . paper proposes a secure, agile, and effective system for a distributed, automatic, and transparent data trading between domains using blockchain, smart contracts, trust, and reputation. . (P2P) file-sharing system [4].
This document will explain how to logon to your Trading Platform. All the Trading Interfaces (the Trading Chart and the 3 different Trade Windows) use a Profile to logon to your data feed and the contract you want to trade. Everything you need to use your Trading Platform is accessed from the Menu at the top of the Trading Chart and Trading .
Algo trading TOTAL TRADING ALGORITHMIC TRADING HIGH FREQUENCY TRADING . Algorithmic trading: In simple words an algorithmic trading strategy is a step-by-step instruction for trading actions taken by computers (au
Trading System, Trading Rules and the Trading Plan 42 Example of Trading Rules 43 Chapter 6: Establishing a Trading Schedule 45 U.S. National Exchanges 45 Regional U.S. Exchanges 46 Canada 46 Europe 46 U.K. 47 Japan 47 Chapter 7: Setting up a Trading Journal 49 The Trading Journal-your best friend 50
Algorithmic trading From Wikipedia, the free encyclopedia Jump to: navigation, search In electronic financial markets, algorithmic trading or automated trading, also known as algo trading, black-box trading or robo trading, is the use of computer programs for entering trading orders with the computer algorithm deciding on aspects of the order such as
the place of anatomy in medical education amee education guide, service manual 1988 mercury 70hp, atlas copco fx 6 manual, force 120 hp outboard repair manual, options trading beginners guide to make money with options trading options trading day trading stock trading stock market trading and investing trading volume 1, gerhard richter, your flight
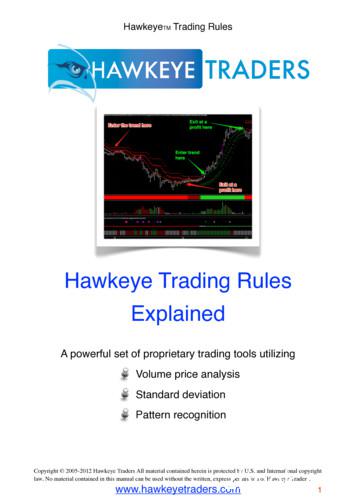
GearboxNDX indicator and trading rules! ! ! ! !43-47 GearchangerNDX indicator and trading rules! ! ! !48-50 Trend and Stops indicator and trading rules!! ! ! !51-54 Volume indicator and trading rules! ! ! ! ! !55-57 Volume Radar indicator and trading rules! ! ! ! !58-60 No Progress ndicator and trading rule
Trading system 7: Donchian style breakout Trading system 8: Breakout with EMA confirmation Trading system 9: Trend following with the TEMA Trading system 10: Bull/Bear fear Trading system 11: Simple RSI with equity curve filter Trading system 12: The range indicator (TRI) Trading system 13: Volatility
Literary Theory and Schools of Criticism Introduction A very basic way of thinking about literary theory is that these ideas act as different lenses critics use to view and talk about art, literature, and even culture. These different lenses allow critics to consider works of art based on certain assumptions within that school of theory. The different lenses also allow critics to focus on .