Advanced Threat Solution - Cisco
Advanced Threat Solutiontentokrát více o koncovém zařízeníListopad 2018Jiří Tesařjitesar@cisco.comCSE Security, CCIE #14558, SFCE #124266, CEH
Security Strategy Overview
Digital Disruption Drives the Hacker EconomyAttack SurfaceThreat ActorsAttack Sophistication Creating an ever-evolving, dynamic threat landscape
RansomwareDDoSMalvertisingAdvanced Persistent ThreatsDrive by DownloadsData ManipulationSpyware/MalwarePhishingMonetary TheftWiper AttacksBotnetsRogue SoftwareMan in the MiddleData DestructionData/IP TheftUnpatched SoftwareTrojans
Technology
We developed Cisco Talos: the largest nongovernment threat intelligence organization on theplanet250 full-time threatresearchers and datascientistsAnalyzing 1.5 millionunique malwaresamples dailyBlocking 20 billionthreats daily. More than20x any other vendor.We see more so you can block more and respond faster to threats.
More threats blockeddaily than anyone elseProofpoint1MZscalerFortinet800K972M20BCheck Point700KTrend Micro250MSymantec4MPalo Alto1M
See it once, protect everywhereNGIPSNGFWISECloudlockUmbrellaAMPThreat GridMerakiNetwork ISR/ASRStealthwatchBest news yet: Cisco Talos is free for customers
Fo rc i n g t h e B a d G u ys to I n n o vateSpreading security news,updates, and otherinformation to the publicThreatSource Newslettercs.co/TalosUpdateSocial Media PostsFacebook: TalosGroupatCiscoTwitter: @talossecurityWhite papers, articles, & other informationtalosintelligence.comTalos Blogblog.talosintelligence.comInstructional Videoscs.co/talostube
AMP for Endpoints
Monitor DetectRecordingIdentify athreat’spoint of originSee what it isdoingSee where it's beenTrack it’s rate ofprogression andhow it spreadSurgically targetand remediate
AMP for Endpoints Protection LatticeshorterTime To Detectionlonger
In MemoryExploit Prevention§Make the memory unpredictable bychanging its structure§Make the app aware of legitimate memorystructure§Any code accessing the old structure ismalware§Currently protects 32-bit apps on 32/64-bitOS! (64bit app protection coming in AMPfor Windows 6.2.x, check release notes)§No Audit mode & CVE agnostic e.exe e keng.exeMalicious CodeInjection HittingTrusted Codea ert!
In MemoryExploit Prevention: In Field FindingsCCleaner0-day FlashExPrev Beta Test leads tobackdoor discovery inCCleaner software from Avast0-day Remote Code Executionvulnerability prevented, preventsexfiltration and remote adminIcedID TrojanMinimalist (evolutionary) codeinjection technique preventedby ExPrev technologyCCleaner: istributes-malware.html0-day Flash: 3-goes-wild.htmlIcedID: Talos Analysis: banking-trojan.html
In MemorySystem Process Protection§Protects Windows system processesfrom being compromised throughmemory injection attacks§Evaluates desired process/threadaccess, truncates potentially dangerousaccess§Protects against Mimikatz dumpingcredentials from lsass.exe memory Session Manager Subsystem (smss.exe)Client/Server Runtime Subsystem (csrss.exe)Local Security Authority Subsystem (lsass.exe)Windows Logon Application (winlogon.exe)Windows Start-up Application (wininit.exe)Talos Analysis: evolution-continues-netting-over.html
Malicious Activity Protection§Detects abnormal behavior of arunning program, initially focused onran RL, etc.) observables?AMPUmbrellaSMA Have we seen these observables? Which end-points reached out to the URL? Etc.
Encrypted Traffic?
Encrypted Traffichttps inspection on gateways (resign, known keys) NGFW WSALeverage Endpoint Visibility AMP4E NVM AnyConnectBehavior analysis of encrypted traffic ETA Stealthwatch
Telemetry sources thatinstrument the digitalbusiness.Catalyst9000Collect and store atscale.StealthwatchEnterpriseAnalyze and automate.Security OutcomesStealthwatchCustom ceMalwareDetection
ETA dataInitial Data PacketSequence of packetlengths and timesGlobal Risk MapC2 MessageData ExfiltrationSelf-Signed CertificateMake the most ofunencrypted fields 2018 Cisco and/or its affiliates. All rights reserved.Identify the content type throughthe size and timing of packetsKnow who’s who of theInternet’s dark sideGlobalSales Training
Cryptographic Compliance 2018 Cisco and/or its affiliates. All rights reserved.GlobalSales Training
Identifying maliciousencrypted trafficGoogle Search Page itiate Command and ControlServerPacket lengths, arrival times anddurations tend to be inherently differentfor malware than benign trafficsrcdstExfiltration and Keyloggingsrc 2018 Cisco and/or its affiliates. All rights reserved.dstdstGlobalSales Training
ETA Data Features, TLS 1.2client keyexchangeApplication Informationchangecipherspecapp dataencryptedhandshakemessageclienthelloapp dataserverhellocertificateServer ncryptedhandshakemessageapp dataencryptedalertserverhellodoneBehavioral Information 2018 Cisco and/or its affiliates. All rights reserved.GlobalSales Training
ETA Data Features, TLS 1.3app dataApplication Informationapp dataclienthelloserverhelloapp dataapp dataapp dataapp dataapp dataapp dataServer InformationBehavioral Information 2018 Cisco and/or its affiliates. All rights reserved.GlobalSales Training
ETA Topologyv Showcased in NOC & ThreatWallv Monitored Public WiFi, Show floor networksv 25,000 Attendeesv 185 Million Flows Analyzedv 88% HTTPS vs 12% HTTPv 40K fps from Wireless UsersThreats Detectedv 400 Detections using ETAv Ransomware detectedv C&C and Data Exfiltrationv Multiple Critical, High- and Medium-risk Detectionsv Numerous Malware Instances including Cryptomining & Botnet activitiesv Several Applications using TLS 1.0
Security that works losStealthwatchEnterprise 2018 Cisco and/or its affiliates. All rights aldomainlookupsUmbrellaInvestigateUser, device andapplication infoISEPxGridTrustSecAnyConnectNVMGlobalSales Training
Stealthwatch Endpoint Visibility SolutionManagementConsolenvzFlowAttributing a flow to: Process name Process hash Process account Parent process name Parent process hash Parent process account 2017 Cisco and/or its affiliates. All rights reserved.EndpointConcentratorAnyConnect withNetwork Visibility ModuleFlowCollectorISEThreat FeedLicenseCognitiveAnalytics
Integrated Security
Latest Announcements in the Cisco Security TechnicalAlliances Ecosystem See 9/19 announcement: How Alliances Strengthen Your CybersecurityDefenses Introducing pxGrid 2.0 – evolving the bedrock of our policy ecosystem ISE & IoT – bringing IoT into mainstream network access policy New integrations and partners from network to endpoint to cloud ISEFirepowerAMP for EndpointsCisco Cloud Security Threat Grid Cisco Security ConnectorAppendix – Details on New Ecosystem Partners and Integrations
CSTA September Announcement Summary57 new integrations from network to endpoint to cloud CISCO ISEpxGrid Integrations forIOT, Orchestration,Deception, Endpoint,VulnerabilityManagementCISCO FirepowerThreat Intelligence Director forNGFW Enrichment, Firepowerintegrations
CSTA September Announcement Summary57 new integrations from network to endpoint to cloud CISCO AMP for EndpointsIntegrations provide analysts withdetailed information and actions onendpoint eventsCISCO Cloud SecurityThreat Intelligence on MaliciousDomains and Threat ResponseEnforcement & CASBCISCO Threat GridMalware Intelligence Sharing andIncident Response Integration
Simplifying WSA Policies with SGTsWho: DoctorWhat: LaptopWhere: OfficeISEDoctorsInternetEnterpriseBackboneWho: DoctorWhat: iPadWhere: OfficeBYODWho: GuestWhat: iPadWhere: OfficeGuestW wwWebSecurityAppliancePoliciesOrderGroupProtocols andUser AgentsURLFiltering(global policy)Block: 1Monitor: 78Doctors BYOD(global policy)Block: 1Monitor: 78Guests(global policy)Global PoliciesNo blocked items1Doctors23ApplicationsBlock: 10Monitor:367ObjectsAnti-Malware and Reputation(global policy)(global policy)Block: 10Monitor:367(global policy)(global policy)Block: 1Monitor: 78Block: 10Monitor:367(global policy)(global policy)Monitor: 79Monitor:367No Blocked ItemsWeb Reputation: EnabledAnti-Malware Scanning: Enabled
ISE as a source of Context Cisco ISE SMC 2018 Společnost Cisco a její pobočky.Maintain historical session tableCorrelate NetFlow to usernameBuild User-centric reportsLive Sessions Table of ISEDevice/User AuthenticationDevice ProfilingNAD detailsLive Authentication Eventsshown in SMC
PxGRIDFTD Policies Based on ISE Context and Sec GroupsNGIPS/ASA Firepower 2018 Společnost Cisco a její pobočky.
Vulnerability-Aware Cisco SecurityUsing Vulnerability to Drive Threat Response in Firepower & ISEDrives Threat Scores inFirepower MCRapid 7Endpoint Vulnerability ScoresQualys TenableDrives Threat-basedNetwork Policy in ISE
Use Cases – Host Input API Allows the import of Host andVulnerability DataVendor, Product,Version, andMobile DeviceInformationServer Applicationsand VersionsFMCClient Applicationsand Version 2018 Společnost Cisco a její pobočky.VulnerabilityNames and IDs
Qualys – ISE Integration
CTA/AMP – ISE IntegrationDifference: vulnerable (Qualys) vscompromised (CTA/AMP) endpointsQuarantine 2017 Cisco and/or its affiliates. All rights reserved. Cisco Public
What is Threat Centric NAC: ThreatThreat EndPoints based on Incidents and Indicators
Incident Response: Rapid Threat ContainmentCisco AMP, Firepower, Stealthwatch, ISE & CSTA Partners “Rapid Threat Containment” – automatically or manually quarantine devices or spawn investigations Enlist other Cisco infrastructure in the network response – such as dynamic ACLs on switches and ASAor increase IPS inspection levelsCisco AMP, NGFW,Stealthwatch ConsolesUser/DeviceQuarantineISE as unifiedpolicy pointACopxGrid ANC API3rd Party Consoles like IBM, McAfee, Splunk,Tanium, Exabeam, Infoblox, LogRhythm, Rapid 7SGTDynamic ACLs,Increase Inspection
DUO
Duo’s Approach is Easy and Reduces Cost1Instantly integrateswith all apps2Users self-enrollin minutes3Authenticate inseconds
3 Key Points About Duo’sSecurity Policies1. Centrally build policies for all apps2. Web based policy management3. Customize for user groups & apps
Duo’s PlatformDevicesPersonal(Unmanaged) DevicesCorporate(Managed) DevicesIdentityApplications& InfrastructureAll EmployeesCloudPrivileged UsersOn-premiseContractors& urity & AccessRemediation
FlexibleAuthenticationOptions foryour usersPush, soft token, SMS,Phone Call, U2F, Wearables,Biometrics, HW Tokens
Verify End User DevicesAllow only compliant devices to access workapplications1.Mobile (iOS and Android)a. Natively using Duo Mobile app. MDM alternative.b. Integration with MDM platforms.1.Non Mobile (Windows, Mac, Linux, ChromeOS)a. Natively using browser data. No agents.b. Integration with endpoint management platform.
Nov 13, 2018 · TETRA definitions from cloud Internal Updates External Updates Customer premises TETRA Update Server Public Wi-Fi TETRA definition Updates § Offline AV engine for Windows § On-prem server gets updates from AMP Public Cloud § Server FQDN configured per AMP Policy § Can make FQDN availa
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
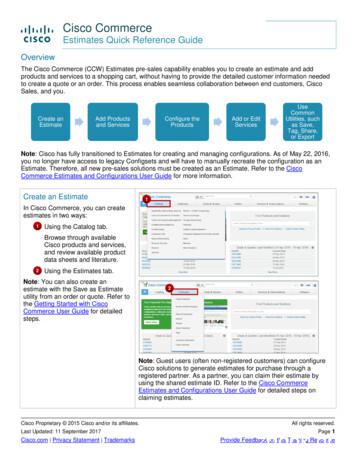
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unified Computing System (Cisco UCS), Cisco UCS B-Series Blade Servers, Cisco UCS C-Series Rack Servers, Cisco UCS S-Series Storage Servers, Cisco UCS Manager, Cisco UCS
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base