Enterprise Mobility Suite Enterprise - Pearsoncmg
About the AuthorsManage all the mobile devices your workforce relies onCenter, Devices & EnterpriseLearn how to use Microsoft’s breakthrough Enterprise MobilityClient - CSI Enterprise MobilitySuite to help securely manage all your BYOD and company-Team. Jeff Gilbert is Seniorowned mobile devices: Windows, iOS, and Android. Two of theSolutions Content Developer forleading mobile device management experts at Microsoft showenterprise client managementyou how to systematically help protect employee privacy andtechnologies at Microsoft.Yuri Diogenes is Senior ContentDeveloper for the Microsoft DataEnterprise Mobility SuiteManaging BYOD andCompany-Owned DevicesManaging BYOD and Company-Owned DevicesEnterprise Mobility Suitecorporate assets without compromising productivity. You’llfind best practices, step-by-step guidance, and real-worldscenarios for every stage of planning, design, deployment,EnterpriseMobility SuiteManaging BYOD andCompany-Owned Devicesand administration.Empower your mobile users while improving securityand controlling costs Master proven best practices for centrally managingsmartphones and tabletsAlso look forYuri DiogenesJeff Gilbert Plan mobile strategies that encompass users, devices,apps, and data Overcome BYOD’s unique challenges, constraints, andcompliance issues Provide common “hybrid” user identities and a seamlessexperience across all resources: on-premises, datacenter,and cloud Help safeguard both corporate and personal informationDeploying Windows Devicesand Enterprise AppsBrian SvidergolDiogenesGilbert Simplify and improve device enrollment, monitoring, andtroubleshootingExam Ref 70-695:ISBN: 978-0-7356-98093microsoft.com/mspressISBN 978-0-7356-9840-65 2 4 9 9U.S.A.Canada 24.99 28.99[Recommended]9780735 6984069780735698406 EMS BYOD cover.indd 1Mobile ComputingCelebrating 30 years!Foreword by Brad AndersonMicrosoft Corporate VP, Enterprise Client & Mobility2/25/2015 7:50:10 AM
Enterprise Mobility Suite:Managing BYOD andCompany-Owned DevicesYuri DiogenesJeff Gilbert
PUBLISHED BYMicrosoft PressA Division of Microsoft CorporationOne Microsoft WayRedmond, Washington 98052-6399Copyright 2015 by Microsoft CorporationAll rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or byany means without the written permission of the publisher.Library of Congress Control Number: 2014955635ISBN: 978-0-7356-9840-6Printed and bound in the United States of America.First PrintingMicrosoft Press books are available through booksellers and distributors worldwide. If you need support relatedto this book, email Microsoft Press Book Support at mspinput@microsoft.com. Please tell us what you think ofthis book at soft and the trademarks listed at roperty/Trademarks/EN-US.aspx are trademarks of the Microsoft group of companies. All other marks are property of their respectiveowners.The example companies, organizations, products, domain names, email addresses, logos, people, places, andevents depicted herein are fictitious. No association with any real company, organization, product, domain name,email address, logo, person, place, or event is intended or should be inferred.This book expresses the author’s views and opinions. The information contained in this book is provided withoutany express, statutory, or implied warranties. Neither the authors, Microsoft Corporation, nor its resellers, ordistributors will be held liable for any damages caused or alleged to be caused either directly or indirectly bythis book.Acquisitions Editor: Karen SzallDevelopmental Editor: Karen SzallEditorial Production: Box Twelve CommunicationsTechnical Reviewer: Randall Galloway; Technical Review services provided by Content Master, a memberof CM Group, Ltd.Copyeditor: Box Twelve CommunicationsIndexer Box Twelve CommunicationsCover: Twist Creative Seattle
Contents at a glanceIntroductionxiiiCHAPTER 1Enabling a mobile workforce1CHAPTER 2Introducing the Enterprise Mobility Suite17CHAPTER 3Hybrid identity27CHAPTER 4Implementing hybrid identity49CHAPTER 5Device management75CHAPTER 6Implementing device management95CHAPTER 7Data access and protection127CHAPTER 8Implementing data protection149CHAPTER 9Monitoring BYOD and company-owned devices169CHAPTER 10Troubleshooting Enterprise Mobility Suite187Index205
This page intentionally left blank
ContentsIntroductionChapter 1xiiiEnabling a mobile workforce1The shift towards mobility. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1The challenges of enabling enterprise mobility . . . . . . . . . . . . . . . . . . . . . . . 2What about BYOD?. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4Understanding the challenges of BYOD5Understanding the Microsoft Device Strategy Framework7Designing a strategy to enable a mobile workforce. . . . . . . . . . . . . . . . . . . . 9UsersChapter 29Devices10Apps12Data13Threat mitigation14Introducing the Enterprise Mobility Suite17Understanding the EMS solution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17Establishing a hybrid identity18Managing mobile devices20Protecting data21EMS activation process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23Embracing a mobile workforce scenario. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24What do you think of this book? We want to hear from you!Microsoft is interested in hearing your feedback so we can continually improve ourbooks and learning resources for you. To participate in a brief online survey, please visit:microsoft.com/learning/booksurveyv
Chapter 3Hybrid identity27Cloud identity with Azure AD Premium. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27Azure AD Premium advanced security reports and alerts28Azure Multi-Factor Authentication30User self-service from the Azure Access Panel32Understanding directory integration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35Source of authority36Directory synchronization36Active Directory Federation Services38Directory integration scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39Directory sync40Directory sync with password sync40Directory sync with SSO40Multiforest directory sync with SSO41Directory synchronization tools. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41Chapter 4Azure Active Directory Synchronization Tool41Azure Active Directory Synchronization Services43Azure AD Connect45Implementing hybrid identity49Scenario description. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49Implementation goals49Solution diagram50Planning and designing the solution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51Microsoft Azure planning and design considerations51On-premises planning and design considerations53Single Sign-On components and considerations54Implementing the hybrid identity solution . . . . . . . . . . . . . . . . . . . . . . . . . . 60viContentsPrepare the Azure AD service for directory integration60Prepare the on-premises environment for directory integration61Enable Single Sign-On64Customize branding70
Chapter 5Device management75Preparing for device enrollment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76Mobile Device Management authority76Device management prerequisites78Device enrollment profiles80The Company Portal80Customizing the Company Portal81Custom company terms and conditions83Deploying policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83Configuration policies84Compliance policies88Conditional access policies88Exchange ActiveSync policies90Policy conflicts90Managing inventory. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91Computer inventory91Mobile device inventory91Performing full and selective wipes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92Chapter 6Selective device wipes93Full device wipes93Implementing device management95Scenario description. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95Implementation goals96Solution diagram96Planning and designing the solution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97Microsoft Intune service configuration considerations97Policies100Mobile Device Management enrollment considerations102Implementing device management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105Prepare the Microsoft Intune service for device enrollment105Satisfy external device enrollment dependencies112Contentsvii
Enrolling devices. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114Chapter 7Enrolling iOS devices114Enrolling Android devices117Enrolling Windows devices120Data access and protection127Leveraging on-premises resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127Windows Server Dynamic Access Control128Web Application Proxy130Protecting data at rest at the user device locationusing work folders131Azure RMS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135Chapter 8How Azure RMS works137Choosing the right deployment topology141Azure RMS connector143Monitoring access to resources145Implementing data protection149Scenario description. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149Implementation goals149Solution diagram149Planning and designing the solution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151Leveraging Azure RMS151Preparing the environment151Implementing the solution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153viiiContentsConfiguring Azure RMS templates153Azure RMS connector159
Chapter 9Monitoring BYOD and company-owned devices169Continuous monitoring and incident response. . . . . . . . . . . . . . . . . . . . . . 169Creating an incident response plan170Leveraging EMS to monitor resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171Azure AD monitoring capabilities172Microsoft Intune monitoring capabilities175Microsoft Azure RMS monitoring capabilities179Leveraging EMS to respond to a security incident. . . . . . . . . . . . . . . . . . . 180Scenario181Chapter 10 Troubleshooting Enterprise Mobility Suite187Troubleshooting methodology. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .187Knowing where to find information190Using troubleshooting tools190Troubleshooting EMS cloud services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191Troubleshooting Azure AD Premium191Troubleshooting Microsoft Intune194Troubleshooting Azure Rights Management Services199Index205What do you think of this book? We want to hear from you!Microsoft is interested in hearing your feedback so we can continually improve ourbooks and learning resources for you. To participate in a brief online survey, please visit:microsoft.com/learning/booksurveyContentsix
This page intentionally left blank
ForewordOf all the books you’ll read about the Enterprise Mobility Suite, this one isprobably the first. In my opinion, it is also the most comprehensive to date.Enterprise Mobility Management—the thing that EMS so brilliantly supportsand empowers—is one of today’s defining trends, and it is the core area of focusfor some of the most brilliant software architects and developers in the techindustry. The reason is obvious: No other technological development will have agreater impact on the way we live and work than our current device ubiquity.From an IT perspective, the number of devices your users want to use, thevolume of data they access, and protecting those corporate assets (and the endusers themselves) are just a handful of the incredibly serious issues you must faceevery day. This reality is what makes EMS so exciting; it represents the intersectionof great software architects with the IT teams working on the front lines of organizations all over the world. With this cloud-based technology, and by leveragingthings like Machine Learning from the cloud, the feedback loop is faster than ever.Now you can enable your users in ways you never have been able to in the past.In this book you’ll see—in practical terms and examples—how to make thesedevices and the people using them dramatically more productive, more connected, and more secure. From the back end of your infrastructure (Microsoft Intune,Azure Active Directory Premium, Azure AD RMS) to the apps your end users interact with every day (Office 365), EMS is an incredibly sophisticated set of tools thatdramatically simplify many previously intractable technical challenges.The Enterprise Mobility Suite is where I believe a cloud-first, mobile-firstperspective really takes shape. The speed of business, the constant movement ofworkers and data, and the need to keep innovating are all delivered with the entirely service-based solutions offered by the EMS. It’s powerful, reliable, and offersyou the cross-platform functionality that’s required to help you successfully andoptimistically bridge your organization’s past and future.Jeff and Yuri have spent an exhaustive amount of time with every corner ofthe Enterprise Mobility Suite, and this book will prepare you to use it to solve theunique challenges your organization is facing today—and to plan ahead for yourorganization’s long-term success.BradBrad Anderson, Microsoft Corporate VP, Enterprise Client & Mobility,@InTheCloudMSFTxi
This page intentionally left blank
IntroductionThis book provides you with an introduction to the Enterprise MobilitySuite (EMS). In it, you are put in the driver’s seat through scenario-basedcontent covering each of the independent technologies that make up EMS:Microsoft Azure AD Premium, Azure Rights Management Services (RMS), andMicrosoft Intune. Throughout the chapters, we guide you through the processof implementing EMS to support Mobile Device Management (MDM) of bothcompany-owned devices and personally-owned devices in your enterpriseenvironment.The scenarios described in this book are truly end-to-end. Starting withenabling hybrid identity, you will quickly learn how to secure corporate dataaccess, protect your employees’ personal information, manage iOS, Android, andWindows devices, and, finally, how to monitor and perform basic troubleshootingof all EMS components.The target audience for this book is comprised of enterprise IT Pros whoare either charged with implementing EMS for their organizations or just wantto learn more about the technologies that are included in EMS. While it is notpossible to cover every aspect and nuance of the technologies included in EMS ina single book, we have attempted to include the content we believe will provideyou with the solid foundation you will need as you begin your own EMS implementation journey.AcknowledgmentsThe authors would like to thank Karen Szall and the entire Microsoft Press teamfor their support in this project, Brad Anderson for writing the foreword of thisbook, and all of our Microsoft colleagues who contributed by reviewing this book:Ben Hawken, Simon May, Robert Mazzoli, Sonia Wadhwa, Eddie Bowers, KeithBrintzenhofe, Marsha Shoemaker, Taylor Thomson, Ken Hoff, Gil Lapid Shafriri,Debbie Furtado, and Stacey Ellingson. We would also like to thank the MicrosoftMVPs who reviewed this book: Kent Agerlund, Kenny Buntinx, Peter Daalmans,John Marcum, Torsten Meringer, Stefan Schörling, and Steve Thompson.Yuri Diogenes I would also like to thank my wife and daughters for their endless support and understanding; my great God for giving me strength and keepguiding my path; my friend and co-author Jeff Gilbert (without you this projectwould not have been possible—thanks); my great friends and former co-authorsxiii
Tom Shinder and Jim Harrison (you both keep inspiring me to write); my formermanagers Kathy Watanabe and Jason Whitmarsh for their support when I joinedthe team; and last, but not least, my parents for working hard to give me an education, which is the foundation that I use every day to keep moving forward in mycareer.Jeff Gilbert I would also like to thank my wife and kids for their support inalways lending a sympathetic ear to my excited technical ramblings—which I’msure sounded like a foreign language to them. This book could not have beenpossible without the help of Yuri Diogenes, my co-author and the one who inspired me to join him on this journey. I’d also like to thank all those whom I workwith at Microsoft and my friends in the systems management IT community whohave always supported me and given focus to the work I do every day.Free ebooks from Microsoft PressFrom technical overviews to in-depth information on special topics, the freeebooks from Microsoft Press cover a wide range of topics. These ebooks areavailable in PDF, EPUB, and Mobi for Kindle formats, ready for you to download at:http://aka.ms/mspressfreeCheck back often to see what is new!Microsoft Virtual AcademyBuild your knowledge of Microsoft technologies with free expert-led online training from Microsoft Virtual Academy (MVA). MVA offers a comprehensive libraryof videos, live events, and more to help you learn the latest technologies andprepare for certification exams. You’ll find what you need here:http://www.microsoftvirtualacademy.comErrata, updates, & book supportWe’ve made every effort to ensure the accuracy of this book and its companioncontent. You can access updates to this book—in the form of a list of submittederrata and their related corrections—at:http://aka.ms/EMSdevice/errataxiv
If you discover an error that is not already listed, please submit it to us at thesame page.If you need additional support, email Microsoft Press Book Support atmspinput@microsoft.com.Please note that product support for Microsoft software and hardware is notoffered through the previous addresses. For help with Microsoft software orhardware, go to http://support.microsoft.com.We want to hear from youAt Microsoft Press, your satisfaction is our top priority, and your feedback ourmost valuable asset. Please tell us what you think of this book at:http://aka.ms/tellpressThe survey is short, and we read every one of your comments and ideas.Thanks in advance for your input!Stay in touchLet’s keep the conversation going! We’re on Twitter: http://twitter.com/MicrosoftPress.xv
This page intentionally left blank
Chapter 1Enabling a mobile workforceThe catchy phrase “work from anywhere” has evolved throughout the years andnowadays working from anywhere is the standard for many industries. However, asconsumers started to use their own gadgets more and more to perform work-relatedtasks, “working anywhere and from any device” has become the new vision for manyenterprises in a mobile-first, cloud-first world. This chapter explains why it is importantfor companies to develop an effective strategy for embracing a mobile workforce andalso explains how the paradigm shift caused by the Bring Your Own Device (BYOD) trendimpacts the overall strategy to securely adopt a mobile workforce.The shift towards mobilityWhen companies started to understand the value of cloud computing—particularlyas it related to how they could leverage its resources to be more agile and to reducecosts—they also discovered that users were already consuming cloud resources on theirown devices. Cloud-based apps are intended to run on all types of portable devices.Also, cloud-based apps are usually programmed to run on several major operating systems, a strategy that drives rapid adoption from consumers. In this new era of EnterpriseIT—also referred to by Gartner1 as the “Third Era of Enterprise IT”—enterprise users notonly demand agility, they demand a substantial increase in productivity.While you might think that this concept is new, the fact is that this mobility phenomenon has been growing for at least the past seven years. A 2008 IDC study sponsoredby Microsoft and performed by International Data Corporation (IDC) called MobilitySolutions in Enterprise-Sized Businesses: Quantifying the Return on Investment2 revealedthat the Return of Investment (ROI) with the use of mobility technologies pays off. So thequestion becomes, “What strategy should be implemented to support a mobile workforce and remain competitive in the marketplace?”A 2014 survey3 published by IDG Enterprise Consumerization of IT in the Enterprise(CITE) suggests that the consumerization of IT maximizes the capabilities of mobility and1For more information about the Third Era of Enterprise IT, visit http://www.gartner.com/newsroom/id/2649419.2You can read the entire report at http://aka.ms/MobileROI.3You can read the entire survey at 4.1
empowers users. This survey documents several key findings. The following two key findingsspecifically address the trends for IT and mobile workforces; these key findings are the corefoundation of this book: The proliferation of user-owned devices requires companies to adjust their policies andinvest in Mobile Device Management (MDM) capabilities in order to maintain controlover the devices while ensuring users can remain productive.Security is a key element to consider throughout the lifecycle of mobile devices.These findings reinforce the fact that while CEOs are willing to enable users to be moreproductive by using their own mobile devices, the IT department must remain in control ofthose devices to ensure the company’s data is protected.The challenges of enabling enterprise mobilityTo address the challenges that comes with enabling mobility in your company, you mustunderstand the four elements of an enterprise mobility strategy (see Figure 1-1): Users Devices Apps DataUsersDevicesAppsDataFIGURE 1-1 The four elements of an enterprise mobility strategyWhen you embrace a mobile workforce, you not only must consider the user and thedevice he wants to use, you must consider how the apps that will be consumed will beaffected by being on a mobile device. Even more importantly, you need to consider howto ensure that the company data remains secure. To effectively manage security of mobiledevices, you should be sure to incorporate security into each of the four elements referencedin Figure 1-1. Focusing on each of the elements will help you to better address each challengein a scenario-based approach. You want to ensure that your overall strategy is compliant withyour business requirements while meeting the user’s expectation about how she will performat work using the device or devices of her choice.2Chapter 1Enabling a mobile workforce
Now that you know the elements, Figure 1-2 expands on the elements shown in Figure 1-1and shows the three core scenarios that you will use throughout the entire book:1. Enable users to choose their devices.2. Unify the management of applications and devices3. Protect corporate data.By using this approach, you will be able to understand the challenges that must beaddressed by your company before you embrace mobility.Users(1) Enableusers tochoose theirdevices.Devices(2) Unify themanagement ofapplications anddevices.AppsData(3) Protectcorporate data.FIGURE 1-2 The three categories of challengesAs shown in Figure 1-2, the three core scenarios are bound to one or more of the elementsshown in Figure 1-1. The following list explains the issues that must be addressed as part ofyour enterprise mobility strategy:1. Enable users to choose their devices Users want to use their own devices to access both their personal data and theirwork-related data/apps.Users want access to these elements from anywhere.While CEOs want to fulfill user requirements in order to enable users to be productive, they also want their IT department to be in control of how users accesscompany data.2. Unify the management of applications and devices Users must have a common identity to access applications and company resourcesfrom any device and from anywhere.IT must be able to manage, deploy, and maintain applications for all types of devices.The challenges of enabling enterprise mobilityChapter 13
IT must be able to manage company-owned devices as well as user-owned devicesfrom a single location. 3. Protect corporate dataCorporate data must be protected at all stages: while data is in the cloud, while datais at the company’s datacenter, while data in the user’s device, and while data is intransit between any (and all) of the aforementioned locations. Corporate data must be isolated and protected from a user’s personal data whilealso securing a user’s privacy. The IT department must be empowered to secure, classify, and protect the company’sdata while also maintaining regulatory compliance. Throughout this book, these challenges will be used as examples for scenarios that explain howEnterprise Mobility Suite (EMS) can assist your company’s efforts to enable a mobile workforce.What about BYOD?Your efforts to embrace a mobile workforce must include an effective strategy for handlingthe BYOD scenario. The BYOD scenario includes more than making your company “mobileready;” it encompasses all the challenges and opportunities as well as the security risks ofvariations on the scenario. These variations will be explored in this chapter. Before you delveinto the specific challenges involved with BYOD, think about why BYOD has become a “buzzword” and why companies should proceed cautiously when adopting BYOD.Real WorldFThe vendor-agnostic approach to BYODor the past two years, I’ve been delivering BYOD presentations that approachthe topic from the architecture perspective and explain how to build a BYODdesign with a vendor-agnostic approach. My first work on this field was released inApril 2014 with the BYOD Design Considerations Guide (available at http://aka.ms/BYODCG ), which features a collection of vendor-agnostic considerations regardingBYOD and how Microsoft technologies can help your company fulfill those requirements. The presentation that I delivered at TechEd North America 2014 was basedon this paper; you can watch it at http://aka.ms/byodtena14 and learn how to use avendor-agnostic approach when developing your BYOD strategy.To help IT professionals to think of BYOD as a problem domain that must havedesign considerations and choices aligned with company requirements, constraints,and vision, I also recorded a series of interviews (http://ala.ms/byodseris) forTechNet Radio. These materials can help you to plan, design and build your solutionto address the BYOD challenges.Yuri DiogenesSenior Content Developer, CSI Enterprise Mobility Team, Microsoft Corporation4Chapter 1Enabling a mobile workforce
A November 2013 study by Gartner suggested that 20 percent of enterprise BYOD programs will fail before 2016. The study indicates programs will fail because of mobile devicemanagement measures that are too restrictive. This study shows that companies are movingtowards the adoption of BYOD, but they are restricting access and thereby not necessarilyrealizing BYOD’s full potential. Managing security is often a delicate balance. If your securitypolicies aren’t strict enough, you’ll put corporate resources at risk. If your security policiesare too strict, you might create an environment that becomes a tremendous challenge forthe IT department to support, thereby adversely impacting your ROI. If your BYOD securityproduces a higher volume of help-desk calls from frustrated users, or, worse yet, if users areunable to perform their work, you might find that your organization needs to roll back toprevious technology. As a result, BYOD becomes an enemy of the company. For this reason,you must ensure that your organization defines an effective BYOD strategy before BYOD isimplemented or deployed.In October 2014, a CheckPoint survey of 700 IT professionals showed mobile securityincidents caused by BYOD had cost each organization more than 250,000 US to remediate 4.These costs are likely to increase as more organizations adopt BYOD as part of their enterprisemobility strategy—underscoring the importance of understanding the challenges of adoptingBYOD.Understanding the challenges of BYODBefore you can understand the challenges introduced by BYOD, you must first understand yourown business requirements, constraints, regulatory compliance needs, and users’ needs andgoals. Unfortunately, this planning phase is often completely overlooked and gaps are foundwhen the next phase—designing the solution—is underway. The best way to mitigate risk isto be aware of how your own company operates. The assumption here is that your companyalready has a security policy in place. What if that security strategy does not address the security challenges that BYOD introduces to the environment? The same rationale can be applied toyour current management infrastructure. What if the existing management platform does notallow users to bring their own devices or does not provide access to company resources?The industry that your company works in also plays an important role in how BYODshould be adopted. With BYOD, the device contains both the user’s personal data and thecompany-owned data. This results in unique challenges for each industry. For instance, in aschool environment, BYOD can be very helpful; to improving user productivity; however, thechallenges can be very unique, as you will see in this section of the book.MORE INFORead “BYOD Devices - A Deployment Guide for Education” for a bet-ter understanding of the design considera
Enterprise Mobility Management—the thing that EMS so brilliantly supports and empowers—is one of today's defining trends, and it is the core area of focus . (Microsoft Intune, Azure Active Directory Premium, Azure AD RMS) to the apps your end users inter-act with every day (Office 365), EMS is an incredibly sophisticated set of tools that
Aruba 7008 Mobility Controller Aruba 7010 Mobility Controller Aruba 7024 Mobility Controller Aruba 7030 Mobility Controller Aruba 7210 Mobility Controller ArubaOS_72xx_8.1.0.0-1.0.0.0 ArubaOS_72xx_ 8.4.0.0-1.0.6.0 ArubaOS_72xx_8.4.0.0-1.0.5.1 Aruba 7220 Mobility Controller Aruba 7240 Mobility Con
ScanTools Pro 4 dS Performance Suite Plus 6 dS Performance Suite Pro 19 dS Performance Suite Premium 25 dS Neuro Suite Plus 31 dS Neuro Suite Pro 37 dS Neuro Suite Premium 43 dS MSK suite 47 dS Body Suite 51 dS Liver Suite 55 dS Breast Suite 59 dS Cardiac Suite Pro 63
2 Introduction: - Transformational Shifts Reshaping the Future of Mobility New Mobility Business Models Mobility Integration Convergence of Corporate Mobility The City as a Customer Women and the Automotive Industry Focus on Health Wellness and Wellbeing in the Automotive Industry Connected and Automated Mobility Growth in high Speed Rail and Public transport .
01.26.10.0033 Trial double mobility liner Ø 22mm / DMC 1 on demand 01.26.10.0034 Trial double mobility liner Ø 22mm / DMD 01.26.10.0035 Trial double mobility liner Ø 28mm / DMD 01.26.10.0036 Trial double mobility liner Ø 28mm / DME 01.26.10.0037 Trial double mobility liner Ø 28mm / DMF 01.26.10.0038 Trial double mobility liner Ø 28mm / DMG
Source: Gartner, Inc., 2014 Magic Quadrant Report for Enterprise Mobility Management, Terrence Cosgrove, et al, June 3, 2014. Source: : IDC MarketScape: Worldwide Enterprise Mobility Management Software 2014 Vendor Assessment, by Stacy K. Crook, Sept 2014, IDC Doc#251379 Figure 1. Magic Quadrant for Enterprise Mobility Management Suites
Als kosteneffizientes Angebot umfasst die Enterprise Mobility Suite drei Produkte: Azure Active Directory (AD) Premium zur hybriden Identitätsverwaltung, Windows Intune zur Verwaltung von Geräten und Apps sowie zur Anwendungsbereitstellung und Azure Rights Management (RMS) zum Schutz Ihrer Daten. Enterprise Mobility Suite 06/07
Regression Testing Process and Issues Test-suite maintenance Obsolete test cases Test suite Tval Regression test selection Test suite T' Test-suite prioritization Prioritized Test suite T' T est-suite augmentation Test suite Taug T est-suite minimization Redundant test cases Minimized test suite est-case manipulation
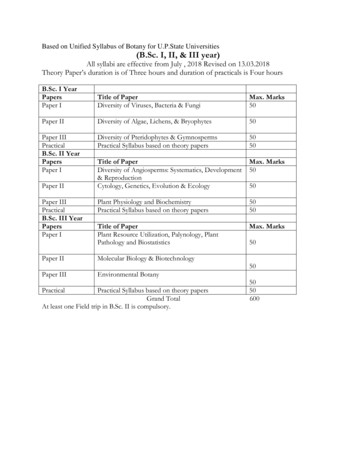
Diversity of Algae, Lichens, & Bryophytes 50 Paper III Diversity of Pteridophytes & Gymnosperms 50 Practical Practical Syllabus based on theory papers 50 B.Sc. II Year Papers Title of Paper Max. Marks Paper I Diversity of Angiosperms: Systematics, Development & Reproduction 50 Paper II Cytology, Genetics, Evolution & Ecology 50 Paper III Plant Physiology and Biochemistry 50 Practical Practical .