These Materials Are 2021 John Wiley & Sons, Inc. Any . - IoT For All
These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
IoT ConnectivitySecurityPelion Special Editionby Lawrence C. MillerThese materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
IoT Connectivity Security For Dummies ,Pelion Special EditionPublished byJohn Wiley & Sons, Inc.111 River St.Hoboken, NJ 07030-5774www.wiley.comCopyright 2021 by John Wiley & Sons, Inc., Hoboken, New JerseyNo part of this publication may be reproduced, stored in a retrieval system or transmittedin any form or by any means, electronic, mechanical, photocopying, recording, scanningor otherwise, except as permitted under Sections 107 or 108 of the 1976 United StatesCopyright Act, without the prior written permission of the Publisher. Requests to thePublisher for permission should be addressed to the Permissions Department, John Wiley& Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748-6011, fax (201) 748-6008, oronline at http://www.wiley.com/go/permissions.Trademarks: Wiley, For Dummies, the Dummies Man logo, Dummies.com, and relatedtrade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. and/or itsaffiliates in the United States and other countries, and may not be used without writtenpermission. Pelion and the Pelion logo are trademarks or registered trademarks of ArmLimited. All other trademarks are the property of their respective owners. John Wiley &Sons, Inc., is not associated with any product or vendor mentioned in this book.LIMIT OF LIABILITY/DISCLAIMER OF WARRANTY: THE PUBLISHER AND THE AUTHOR MAKE NOREPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE ACCURACY OR COMPLETENESS OF THECONTENTS OF THIS WORK AND SPECIFICALLY DISCLAIM ALL WARRANTIES, INCLUDING WITHOUTLIMITATION WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE. NO WARRANTY MAY BE CREATEDOR EXTENDED BY SALES OR PROMOTIONAL MATERIALS. THE ADVICE AND STRATEGIES CONTAINEDHEREIN MAY NOT BE SUITABLE FOR EVERY SITUATION. THIS WORK IS SOLD WITH THE UNDERSTANDINGTHAT THE PUBLISHER IS NOT ENGAGED IN RENDERING LEGAL, ACCOUNTING, OR OTHER PROFESSIONALSERVICES. IF PROFESSIONAL ASSISTANCE IS REQUIRED, THE SERVICES OF A COMPETENT PROFESSIONALPERSON SHOULD BE SOUGHT. NEITHER THE PUBLISHER NOR THE AUTHOR SHALL BE LIABLE FORDAMAGES ARISING HEREFROM. THE FACT THAT AN ORGANIZATION OR WEBSITE IS REFERRED TO INTHIS WORK AS A CITATION AND/OR A POTENTIAL SOURCE OF FURTHER INFORMATION DOES NOT MEANTHAT THE AUTHOR OR THE PUBLISHER ENDORSES THE INFORMATION THE ORGANIZATION OR WEBSITEMAY PROVIDE OR RECOMMENDATIONS IT MAY MAKE. FURTHER, READERS SHOULD BE AWARE THATINTERNET WEBSITES LISTED IN THIS WORK MAY HAVE CHANGED OR DISAPPEARED BETWEEN WHENTHIS WORK WAS WRITTEN AND WHEN IT IS READ.For general information on our other products and services, or how to create a custom ForDummies book for your business or organization, please contact our Business DevelopmentDepartment in the U.S. at 877-409-4177, contact info@dummies.biz, or visit www.wiley.com/go/custompub. For information about licensing the For Dummies brand for products orservices, contact BrandedRights&Licenses@Wiley.com.ISBN 978-1-119-60687-1 (pbk); ISBN 978-1-119-60690-1 (ebk)Manufactured in the United States of America10 9 8 7 6 5 4 3 2 1Publisher’s AcknowledgmentsWe’re proud of this book and of the people who worked on it. Some of thepeople who helped bring this book to market include the following:Project Manager: Martin V. MinnerSenior Managing Editor:Rev MengleAcquisitions Editor: Ashley CoffeyBusiness DevelopmentRepresentative: Karen HattanProduction Editor:Mohammed Zafar AliThese materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
IntroductionAny time a device is connected to the Internet, it’sat risk of being breached. Today, billions ofdevices are being connected to the Internet. As aresult, the attack surface has grown, making it exponentially larger, more complex, and more challenging tosecure. But like any other breach today, a successfulInternet of Things (IoT) breach requires network connectivity. Thus, the key to securing IoT devices is tosecure IoT connectivity.About This BookIoT Connectivity Security For Dummies consists of sixchapters that explore IoT connectivity vulnerabilities(Chapter 1), device integrity (Chapter 2), how to protectdata in transit (Chapter 3), IoT security management(Chapter 4), the secure connectivity ecosystem (Chapter 5),and keys to securing IoT connectivity (Chapter 6).This book focuses on cellular IoT security rather thanWi-Fi and other protocols that are commonly used forIoT connectivity.1These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
Foolish AssumptionsIn this book, I assume you work for an enterprise that isconsidering an IoT deployment and that you have at leasta basic understanding of IoT and some of the potentialchallenges to security, but that you’d like to learn moreabout IoT connectivity security.Icons Used in This BookThroughout this book, I occasionally use icons to call outimportant information. Here’s what to expect.This icon points out information you shouldcommit to your nonvolatile memory, yourgray matter, or your noggin.If you seek to attain the seventh level ofNERD-vana, perk up! This icon explains thejargon beneath the jargon.Beyond the BookIf you find yourself at the end of this book thinking, “Gosh,this was an amazing book — where can I learn more?”just go to m/.2These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
IN THIS CHAPTER»» Identifying physical securitythreats»» Keeping IoT software secure»» Securing the end-to-endconnection lifecycleChapter1Recognizing IoTConnectivityVulnerabilitiesIn this chapter, you explore Internet of Things (IoT)connectivity vulnerabilities associated with communication, physical security, the connection lifecycle, andthe software components of IoT devices, and why it’simportant to identify vulnerabilities early in your IoTproject to avoid deployment delays due to potential security issues.3These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
CommunicationCellular networks including 3G, 4G, and 5G are ubiquitous for long-range mobile communications and are thusideally suited for IoT device communications.Cellular networks provide distinct security advantagesover other IoT network options, such as Wi-Fi. However,because IoT devices typically transmit data beyond thenetwork to the Internet, security cannot be assumed.Vulnerable cellular network components include:»» Signaling System No. 7 (SS7) nodes: Developedas a set of telephony protocols in 1975, SS7 nowprovides connection for roaming between cellularnetworks. Although newer technologies are beingadopted, many roaming and older networks stillrely on SS7. Vulnerabilities enable routing paths tobe manipulated, transmissions to be intercepted,and locations to be tracked in real time.»» Baseband processors: The CPU, memory, networkinterface and media processor in mobile and IoTdevices are referred to as the baseband processor.Vulnerabilities in the hardware, firmware, andsoftware of these devices can be exploited.Securing SS7 nodes and base station vulnerabilities is thepurview of telcos and mobile network operators (MNOs).IoT device manufacturers developing and deploying IoTsolutions should instead focus on securing connectivityin their IoT devices.4These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
PhysicalAttackers often use physical properties of the systemon-chip (SoC), such as timing or voltage, to extractinformation or induce bad behavior. If the base layer ofsilicon fails, allowing data to leak out or to be easilyaccessed, the entire system security becomes at risk.An intruder may attempt to tamper with an IoT device totake control of the device, alter its functionality or behavior, steal data collected by the device, or use the device topivot to other networks. The intruder often attempts totamper with the device’s communications components,such as the subscriber identity module (SIM).Hardware hacks are much harder to perpetrate than software hacks. Moreover, a software attack can directlyreach thousands of IoT devices, whereas a hardwareattack is generally more limited.SoftwareEven the most robust security schemes and cryptographicarchitectures are susceptible to physical attacks, and thistype of attack is gaining traction as new automated toolsmake it easier to perform. The risk with a physical attackis the scalability factor: Extracting information from onedevice, such as keys or source code, allows an attacker toconduct a large-scale software attack.5These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
As with computer software, vulnerabilities are inevitablydiscovered in IoT device software and must be patchedand updated in a reliable, timely, and effective manner.A challenge with IoT devices is that they cannot be easilyupgraded to mitigate issues. Although there have beenspectacular breaches against IoT devices, such as Mirai,Chalubo, Torii, and Demonbot, many other software vulnerabilities are susceptible to traditional breaches, suchas buffer overflows that exploit memory flaws.Though the computing industry must respond to newvulnerabilities, software must also address traditionalissues such as default user identifiers and passwords.Connection LifecycleSecurity of IoT devices is too often an afterthought. Vulnerabilities must be addressed throughout the devicelifecycle. This includes secure deployment, ongoing orcontinuous monitoring, over-the-air (OTA) updates,remote management, deprovisioning, and human accessto the connectivity management platform.To achieve end-to-end security throughout the connection lifecycle, security must be a primary design consideration in IoT devices — as fundamental as any otherparameter. There should be a strong focus on tightmechanisms for device authentication and integrity, aswell as minimizing the potential attack surface.6These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
IN THIS CHAPTER»» Authenticating devices andconnections»» Establishing the “new perimeter”»» Providing authentication andauthorization servicesChapter2Securing DeviceIdentityIn this chapter, you learn about the importance ofsecure identity management for the devices in yourInternet of Things (IoT) deployment.Ensuring Device and SIMAuthenticityEnsuring the authenticity of devices connected to yourIoT platform and the subscriber identity modules (SIMs)7These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
in those devices is crucial to maintaining the confidentiality, integrity, and availability of your IoT ecosystem.Digital certificates, unique device credentials, and virtualprivate network (VPN) connections can help the enterprise verify the authenticity of IoT devices to the centralized management point.Embedded SIMs (eSIMs), discussed in Chapter 4, can helpto significantly reduce the risk of removal or replacementof the SIM card in a device, helping to further ensure theauthenticity of devices connecting to your platform. AneSIM, which is directly soldered within the device, ismuch harder for an attacker to locate, remove, or replace,than removable form factors, thereby improving IoTsecurity with a hardware-integrated solution.Verifying IdentityWith the proliferation of cloud computing and mobilecomputing, traditional network perimeters have becomelargely indistinct. Identity has become the foundation forcontrolling how and if a device connects to the network,and which services can be accessed by a subscriber. Verifying an IoT device is crucial to the security of the ecosystem within which it operates as well as the authenticityof the data it is gathering and passing back across theecosystem.8These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
A device can be verified with its International MobileEquipment Identity (IMEI), which uniquely identifies thedevice and is essentially a make, model, and serial number for the device. The IoT SIM Applet For Secure Endto-End Communication (SAFE) is a recommendation ofthe Global System for Mobile Communications (GSMA) toleverage the advanced security and cryptographic features in a SIM to function as the hardware Root of Trustin an IoT device. Although IoT SAFE does not identify thedevice, it allows you to verify the trustworthiness of thedevice.Enabling more secure network access pairing requires acombination of subscription identification coupled withhardware identification. An entity on the network, knownas an Equipment Identity Register (EIR), matches theIMEI of a device with the International Mobile SubscriberIdentity (IMSI). The EIR is typically a component of thecellular network and is closely integrated into the Operations Support System (OSS) and Business Support System(BSS) that has close insight into both device and subscriber IDs, as well as integration with a central blacklisting service. However, use of this capability has to becarefully approached because blocking or flagging subscriber access as suspicious, in cases where the IMEIdoesn’t marry up with the subscriber ID, can haveramifications.9These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
Authenticating andAuthorizing AccessThe Third Generation Partnership Project (3GPP), that is,the world umbrella standardization body for cellularconnectivity, includes a complete mechanism by whichsession keys are derived from the network authenticationprocess. This process protects radio communicationsfrom the device to the first network equipment that itconnects to — the Evolved Node B (eNodeB) on a 4G network or Next Generation Node B (gNodeB) on a 5Gnetwork.Centrally managing the ongoing authentication andauthorization of devices at scale can be a major challengein enterprise IoT deployments. A secure connectivitymanagement platform (CMP), discussed in Chapter 4,can provide authentication and authorization services,including generating and validating access credentials;issuing, validating, and revoking security certificates;exchanging security keys; and establishing a secure virtual private network (VPN) from enterprise environments to IoT connections.10These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
IN THIS CHAPTER»» Securing end-to-end IoTcommunications»» Protecting the confidentialityand integrity of data in transit»» Ensuring a robust, highlyavailable connectivitymanagement platformChapter3Protecting Datain TransitIn this chapter, you learn about secure connectivityrequirements, how to protect the confidentiality andintegrity of data in transit, and what to look for in aconnectivity management platform to ensure a highlyavailable Internet of Things (IoT) solution.11These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
Ensuring Secure End-to-EndConnectivityThe IoT introduces new challenges associated with secureend-to-end connectivity. For example, IoT devices connected to each other can be different from one another interms of characteristics and communication technologies,making it harder to establish secure sessions and securecommunications. IoT devices often connect to theirreciprocal management server or ecosystem over cellularnetworks including 3G, 4G, and 5G, and other neweremerging technologies such as Low-Power Wireless Area(LWPA) Networks.As with most IoT technologies used, cellular technologiesalso have vulnerabilities and new vulnerabilities willinevitably be discovered across the full range of IoT connectivity options. Network operators implement securityin their cellular networks in the following ways:»» Including fraud detection as a component of themobile network to track and trace unwantedbehaviors and miscreant activity, thereby adding totheir overall security»» Uniquely identifying endpoint devices on thenetwork using an international mobile equipmentidentity (IMEI)12These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
»» Using network and country codes to identifydifferent networks»» Encrypting network traffic, providing privatenetworks (including virtual private networks), andcreating dedicated networks»» Ensuring high availability by using licensedspectrum, implementing standard networktechnologies, and building resilient networktopologiesEnterprises (as deployers or consumers of the IoT ecosystem and data), device manufacturers, and networkoperators must ensure that secure end-to-end connectivity is a fundamental part of their IoT designs. Thisincludes ensuring only authenticated and authorizeddevices can connect to the IoT platform and that the platform, in turn, can only communicate with properlyauthenticated and authorized endpoints. This is particularly important because IoT devices may connect to multiple public and private clouds, as well as edge clouds anddifferent provider networks in the IoT ecosystem.End-to-end communications can be secured via a VPNwith robust key management capabilities and/or by separating IoT traffic from the public Internet over a dedicated network. Whether communicating over a VPN ordedicated network, Transport Layer Security (TLS)/Datagram TLS (DTLS) should be used to secure end-to-endtraffic. Enterprises and device manufacturers must also13These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
ensure that their devices can be supported from a remotemanagement platform with robust capabilities. Forexample, reliably installing security patches and protocolupdates over the air for devices already deployed in thefield.To establish a data connection with a network operator, amobile device must be configured with an access pointname (APN). The APN maps to a specific configurationset that can include functions that can ensure a secureentry point between the cellular network and anothernetwork, such as a private corporate network. For generalusers, the APN is usually configured to be open to generalInternet access, but it still protects a device from unsolicited requests from the Internet towards a device. Thenetwork operator may use the APN to determine the typeof data connection that should be created. For example,the APN may be used to define what security methods touse for the connection.Some network providers can create “privateAPNs” that allow authentication to be controlled on a per-SIM level and updateddynamically.Encrypting Data in TransitData transmitted and received by IoT devices must beencrypted to protect its confidentiality and integrity.Although certain IoT applications may not generate or14These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
process particularly sensitive data, intruders may be ableto glean information from the aggregation of this datathat helps perpetrate a breach against a target. For example, a power meter may provide an intruder with enoughdata to determine if someone is at home or not, or whenthey are likely to be home, based on their power consumption patterns.Additionally, ensuring the encryption of data in transitassures its integrity and validity upon arrival. This can bedata gathered by the device (for example, environmentaldata or electrical power usage) or software updates andsecurity patches destined for the device, ensuring malicious code is not installed and the device is notcompromised.Data in transit should be encrypted using the most current version of the Transport Layer Security (TLS)protocol.Transport Layer Security (TLS) is commonly,though incorrectly, referred to as SecureSockets Layer (SSL) encryption. All versionsof SSL have now been deprecated andreplaced by TLS.Data in transit should also be encrypted from end toend — from the device, across the communications service provider (CSP) networks, to the data center and system where the data is ultimately hosted for use.15These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
The 3rd Generation Partnership Project (3GPP) standardsdefine the mechanisms for authentication and confidentiality between the device and the base station, as well asthe interfaces from the base station back to the networkoperators’ infrastructure core and the Internet gateways.Authentication occurs with credentials held in the HomeSubscriber Server (HSS)/Home Location Register (HLR),which sits in the heart of the core network. Numeroussecurity methods and controls are used to ensure theentirety of the mobile network infrastructure is a privatenetwork and protected against external attacks. In comparison, a web browser session may be encrypted usingTransport Layer Security (TLS), whereas an IoT devicedoesn’t have any end-to-end session encryption unlessit is set up explicitly.In addition to the 3GPP security standardsand the network operators’ security deployments, ensuring that data is encrypted endto-end provides additional security and protects against any momentary degradation orbreaches in security at any point.IoT Subscriber Identity Module (SIM) Applet for SecureEnd-to-End Communication (SAFE) is a Global Systemfor Mobile Communications Association (GSMA) recommendation that leverages the SIM to protect the device’scredentials, just like the network credentials themselves.IoT SAFE advocates using the SIM as the hardware Rootof Trust in an IoT device to establish “end-to-end,16These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
chip-to-chip security.” It uses the SIM as a mini “cryptosafe” to establish a Datagram TLS (DTLS) session with anapplication server or cloud and mutually authenticate thedevice and server/cloud.Providing ResilienceYour IoT connectivity management platform also needsto provide resilience to maximize uptime and ensure thatcritical devices can reliably and securely reach and interact with your IoT ecosystem. In the event of a failure, youneed to maintain the security of your critical applicationsand devices until they can be returned to their normaloperating state. When considering different connectivitymanagement platforms and partners, look for the following features and capabilities:»» Redundant, geographically dispersed Tier 3(or Tier 4) data centers with 99.982 percent uptime(no more than 1.6 hours of downtime per year)and N 1 fault tolerance providing at least 72-hourpower outage protection»» Multiple partner networks with different transitproviders and Internet providers providing failovercapabilities between diverse links with sufficientcapacity to handle full traffic loads individually17These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
»» Redundant, load balanced Packet Data NetworkGateways (PGWs) capable of handling full trafficloads»» IPSec VPN routing and hot failover for maximumreliability and seamless failover of services betweensites»» Successful completion of an InternationalOrganization for Standardization (ISO) andInternational Electrotechnical Commission(ISO/IEC) 27001 security standards audit18These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
IN THIS CHAPTER»» Managing secure IoT connectivityat scale»» Exploring remote provisioningcapabilities»» Enabling proactive monitoringand alertingChapter4Managing IoTConnectivitySecurityIn this chapter, you learn about connectivity management platforms and how they help enterprises securelymanage their IoT deployments.19These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
Connectivity ManagementPlatform (CMP)Making a reliable, secure connection available is criticalto IoT deployments, which are complex environmentswith potentially hundreds of thousands of connecteddevices. An IoT connectivity management platformenables secure remote connectivity for IoT deploymentsat scale.Without a connectivity management platform (CMP),large IoT deployments cannot be efficiently managed, forexample, in the event of a breach that requires visibilityand control to identify, contain, mitigate, and recover theaffected IoT devices. Other important reasons to manageyour IoT deployments with a CMP include:»» Managing devices across networks and providersat scale is challenging; having a consistent interfaceand integration allows easier device updates.»» No insight into connectivity status means you donot know if your critical assets have gone offlineand whether it’s due to a malfunction, a breach, orsome other issue.»» Lack of statistical data and analytics means youdon’t know if your asset has overconsumed dataand you can’t efficiently identify issues withconnections that aren’t functioning correctly.20These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
The ideal CMP is an interface that should provide enterprises with the ability to:»» Manage the lifecycle of a connection: Activate,deactivate, bar, or unbar a subscriber.»» Monitor subscriber activity and performance,preferably in an automated fashion: How muchdata has been used on a device or account?»» Manage inventory: Order new subscriber identitymodules (SIMs) and embedded SIM (eSIM) profiles,or manage existing stock.»» Manage billing: How much does each connectioncost? What was my bill this month? How much didmy overage cost?»» Allow easy access to devices over a singlenetwork interface: Allow updates for devicesregardless of mobile network.Provisioning andDeprovisioningRemote eSIM provisioning provides the ability to download, enable, disable, and delete network operator profiles for devices over the air.21These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
An eSIM is embedded (that is, directly soldered) within the device at the point ofmanufacture.Remote eSIM provisioning opens the door to a range ofuse cases that cannot be supported by conventional SIMs.For example, it allows a device manufacturer to insert orembed an eSIM at the point of assembly. When the deviceis turned on, provided the correct configuration is inplace, it can connect to a local cellular network, makingthe device ready to use immediately regardless of whereit has been deployed. Instead of holding SIM cards formultiple network operators across the globe and coordinating which card should be inserted into which device,every device can use the same type of physical eSIM andhave the correct profile applied in the field. If the network operator profile on a deployed device needs to bechanged, it can be downloaded to an available memoryslot on the eSIM and enabled over the air. This capabilityis a significant enhancement, especially when comparedto conventional SIM cards, which require a SIM to bephysically swapped for a network change.In short, remote eSIM provisioning allows manufacturersto drastically simplify their supply chain and reduce thehigh cost of inventory, while providing customers withdevices that can be connected out of the box. It also provides the capability to manage connectivity by downloading and enabling the SIM profile for a new operator’ssubscription for an IoT device deployed in an inaccessiblelocation. The CMP must have an awareness of this type of22These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
SIM and SIM profile deployment mechanism as well asintegration with the relevant remote SIM provisioningplatforms.Managing Human AccessHuman access to physical IoT devices introduces the riskof tampering. Often, such tampering involves replacingor removing the SIM card to take control of the device,steal data, or otherwise compromise functionality.Technologies such as eSIMs help to reduce the risk oftampering because the SIM is embedded during the manufacturing process into a sealed enclosure. It is extremelydifficult to tamper with or remove an eSIM without causing significant damage to the device.Access to the connectivity management platform mustalso be controlled, including the permissions assigned toauthorized users for specific systems. The CMP providesvisibility and control of the entire IoT device estate, socontrolling access to this functionality is crucial.Monitoring and AlertingA connectivity management platform also enables realtime monitoring of devices deployed at scale, which helpsenterprises proactively troubleshoot device issues. Alerting capabilities ensure that corrective action can be taken23These materials are 2021 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized useis strictly prohibited.
immediately when a device goes offline or otherwiseexperiences issues.Monitori
IoT Connectivity Security For Dummies consists of six chapters that explore IoT connectivity vulnerabilities (Chapter 1), device integrity (Chapter 2), how to protect data in transit (Chapter 3), IoT security management (Chapter 4), the secure connectivity ecosystem (Chapter 5), and keys to securing IoT connectivity (Chapter 6). .
L’ARÉ est également le point d’entrée en as de demande simultanée onsommation et prodution. Les coordonnées des ARÉ sont présentées dans le tableau ci-dessous : DR Clients Téléphone Adresse mail Île de France Est particuliers 09 69 32 18 33 are-essonne@enedis.fr professionnels 09 69 32 18 34 Île de France Ouest
August 2, 2021 15 August 2, 2021 16 August 2, 2021 17 August 3, 2021 18 August 4, 2021 19 August 5, 2021 20 August 6, 2021 21 August 9, 2021 22 August 9, 2021 23 August 9, 2021 24 August 10, 2021 25 August 11, 2021 26 August 12, 2021 27 August 13, 2021 28 August 16, 2021 29 August 16, 2021 30 August 16, 2021 31
118 I have broken these verses here in John chapter 1 into four main points and they are, THE WORD IS MADE FLESH – JOHN 1:14 JOHN BORE WITNESS – JOHN 1:15 GRACE AND TRUTH – JOHN 1:16-17 GOD MADE KNOWN – JOHN 1:18 So John is going to finish up his prologue or introduction that covers John 1:1-18, as I
021 BIBLIOGRAFI 1. Rujukan Buku Bahasa Arab Abd al-‘AzÊz, AmÊr (1999), Fiqh al-KitÉb wa al-Sunnah: DirÉsah MustafÉdah TatanÉwulu AbwÉb al-Fiqh ‘alÉ Mukhtalif al-MadhÉhib wa al-‘ArÉ wa Tu’raÌu li Ammah al-QadÊyah fÊ Öaw’i al-IslÉm bi UslËbin MauÌË’iyyin Mu’ÉÎirin. j. 5,
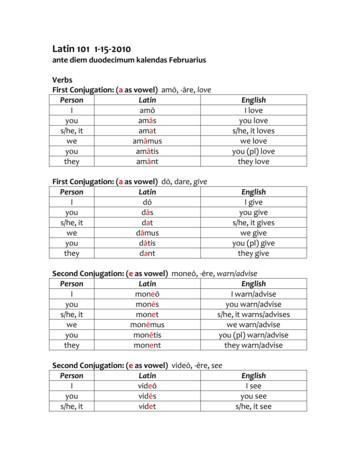
Jan 15, 2010 · Latin 101 1-15-2010 ante diem duodecimum kalendas Februarius Verbs First Conjugation: (a as vowel) amō, -āre, love Person Latin English I amō I love you amās you love s/he, it amat s/he, it loves we amāmus we love you amātis you (pl) love they amānt they love
MANUAL DE INSTRUCCIONES TORNO FTX-2000X660-T02-DCR Pol.Ind.Font del Radium Cl/ Severo Ochoa, 40-42 08403 Granollers (Barcelona)-Spain Tel. 34 93 861 60 76 FTX2000X660-T02-DCR*UPDT.2019 1/90. Mantenga el orden en su campo de trabajo. Mantenga el áre a limpia y bien iluminada .
9. John 1:29 - How did John describe Jesus in this passage? 10. John 1:30-33 - Who did John see descending and remaining on Jesus? 11. John 1:40-42 - Who found his brother and brought him to Jesus? 12. John 1:43-51 - Who did Philip find and tell about Jesus? 13. John 2:1-5
1ST STAGE RESULT 2ND STAGE RESULT PAINTING 9th –20 THOCT, 2021 25 THOCT, 2021 (International Artist Day) 30 OCT –7 NOV, 2021 14TH NOV, 2021 (FINAL RESULTS) WRITING 9th –20TH OCT, 2021 25TH OCT, 2021 (International Artist Day) 30TH OCT –7TH NOV, 2021 14TH NOV, 2021 (FINAL RESULTS) LYRICS, SINGING AND MUSIC 4TH NOV (To be