Image MASSter Solo 4 Forensic - Homeland Security
Image MASSter Solo 4 ForensicTest Results for Digital Data Acquisition ToolNovember 18, 2013
This report was prepared for the Department of Homeland Security Science and Technology Directorate CyberSecurity Division by the Office of Law Enforcement Standards of the National Institute of Standards and Technology.For additional information about the Cyber Security Division and ongoing projects, please visithttp://www.dhs.gov/cyber-research.
November 2013Test Results for Digital Data Acquisition Tool:Image MASSter Solo-4 Forensic
ContentsIntroduction . 1How to Read This Report . 11 Results Summary . 22 Test Case Selection . 23 Results by Test Case-Variation. 34 Testing Environment. 44.1 Execution Environment . 54.2 Support Software . 54.3 Test Drive Creation. 54.3.1 Source Drive . 54.3.2 Media Drive . 54.3.3 Destination Drive . 54.4 Test Drive Analysis. 64.5 Note on Test Drives . 65 Test Results. 65.1 DA-01 . 85.2 DA-02 . 85.3 DA-04 . 85.4 DA-06 . 95.5 DA-07 . 95.6 DA-08 . 95.7 DA-09 . 95.8 DA-10 . 105.9 DA-12 . 105.10 DA-14 . 105.11 DA-14 Anomalies . 105.12 DA-17 . 105.13 DA-19 . 115.14 DA-24 . 115.15 DA-25 . 116 Summary of Administrative Data . 11ii
IntroductionThe Computer Forensics Tool Testing (CFTT) program is a joint project of theDepartment of Homeland Security (DHS), the National Institute of Justice (NIJ), and theNational Institute of Standards and Technology Law Enforcement Standards Office(OLES) and Information Technology Laboratory (ITL). CFTT is supported by otherorganizations, including the Federal Bureau of Investigation, the U.S. Department ofDefense Cyber Crime Center, U.S. Internal Revenue Service Criminal InvestigationDivision Electronic Crimes Program, and the U.S. Department of Homeland Security’sBureau of Immigration and Customs Enforcement, U.S. Customs and Border Protectionand U.S. Secret Service. The objective of the CFTT program is to provide measurableassurance to practitioners, researchers, and other applicable users that the tools used incomputer forensics investigations provide accurate results. Accomplishing this requiresthe development of specifications and test methods for computer forensics tools andsubsequent testing of specific tools against those specifications.Test results provide the information necessary for developers to improve tools, users tomake informed choices, and the legal community and others to understand the tools’capabilities. The CFTT approach to testing computer forensics tools is based on wellrecognized methodologies for conformance and quality testing. Interested parties in thecomputer forensics community can review and comment on the specifications and testmethods posted on the CFTT Web site (http://www.cftt.nist.gov/).This document reports the results from testing Image MASSter Solo-4 Forensic againstthe Digital Data Acquisition Tool Assertions and Test Plan Version 1.0, available at theCFTT Web site (http://www.cftt.nist.gov/DA-ATP-pc-01.pdf).Test results from other tools can be found on NIJ’s computer forensics tool testing Webpage, ctronic-crime/cftt.htm or at theDepartment of Homeland Security Web page, https://www.cyberfetch.org/public.How to Read This ReportThis report is divided into six sections. The first section identifies any significantanomalies observed in the test runs. This section is sufficient for most readers to assessthe suitability of the tool for the intended use. The remaining sections of the reportdescribe test case selection, results by test case, the test environment and test details.Section 2 gives justification for the selection of test cases from the set of possible casesdefined in the test plan for Digital Data Acquisition tools. The test cases are selected, ingeneral, based on features offered by the tool. Section 3 lists each test case run and theoverall result. Section 4 lists hardware and software used to run the test cases with linksto additional information about the items used. Section 5 presents for each test case theexpected result data used to measure the success of the test and the actual data reportedby the tool. Section 6 presents administrative data for each test case run. To download azip file containing the raw log files for the Image MASSter Solo-4 Forensic test runs, s-v3.html.
Test Results for Digital Data Acquisition ToolTool Tested:Software Version:Firmware Version:Imager MASSter Solo-4 Forensicv4.10.29.0 x32v1.33.0.0 x32Supplier:Intelligent Computer Solutions, IncAddress:10030 Remmet Ave.Chatsworth, CA 91311Tel:Email:WWW:(888) 1 Results SummaryThe Imager MASSter Solo-4 Forensic system is a portable data acquisition device. Theunit provides native interface support for SAS, SATA and USB drives in addition tosupporting PATA. The tool acquired the test media completely and accurately. Thefollowing restore anomaly was observed. In test case DA-10-encrypt the tool’s “Encrypt Destination Files” setting was usedto acquire a source drive to an encrypted image file. In DA-14-encrypt, the imagefile created in DA-10-encrypt was restored to a drive. When the restored drivewas compared to the source, only 1,571,229 sectors out of 156,301,488 sectorsmatched. The vendor plans to address this issue in a future software release andrecommends not using the “Encrypt Destination Files” setting until it is corrected.For more test result details see section 5.2 Test Case SelectionTest cases used to test disk imaging tools are defined in Digital Data Acquisition ToolAssertions and Test Plan Version 1.0. To test a tool, test cases are selected from the TestPlan document based on the features offered by the tool. Not all test cases or testassertions are appropriate for all tools. There is a core set of base cases (e.g., DA-06 andDA-07) that are executed for every tool tested. Tool features guide the selection ofadditional test cases. If a given tool implements some feature then the test cases linked tothe implemented features are run. Table 1 lists the supported features of Imager MASSterSolo-4 Forensic and the linked test cases selected for execution. Table 2 lists the featuresnot available in Imager MASSter Solo-4 Forensic and the test cases not executed.November 2013Page 2 of 12Image MASSter Solo-4
Table 1. Selected Test CasesSupported Optional FeatureCreate a clone during acquisitionCreate an unaligned clone from a digital sourceCreate a truncated clone from a physical deviceBase CasesCreate an image of a drive with hidden sectorsRead error during acquisitionCreate an image file in more than one formatInsufficient space for image fileCreate a clone from an image fileFill excess sectors on a clone deviceFill excess sectors on a clone acquisitionDetect a corrupted (or changed) image fileCases selected for execution01020406 & 070809101214171924 & 25Table 2. Omitted Test CasesUnsupported Optional FeatureCreate cylinder aligned clonesDevice I/O error generator availableDestination Device SwitchingCreate a clone from a subset of a n image fileFill excess sectors on a clone deviceConvert an image file from one format to anotherCases omitted (not executed)03, 15, 21 & 2305, 11 & 18131620, 21, 22 & 2326Some test cases have different forms to accommodate parameters within test assertions.These variations cover the acquisition interface to the source media, type of digital objectacquired, image file format, and the way that sectors are hidden on a drive.The following source interfaces were tested: USB, ATA28, ATA48, SATA28, SATA48,and SAS. These are noted as variations on test cases DA-01, DA-06, DA-08 and DA-14.The following digital source types were tested: compact flash (CF) and thumb drive(Thumb). These digital source types are noted as variations on test cases DA-02, DA–07and DA-14.The following image file types are supported by the tool: E01, E01 compressed andencrypted. These were tested as alternate image file formats and are noted as variationson test case DA-10.3 Results by Test Case-VariationThe following table lists the test outcome by test case-variation. For a completeexplanation of the test case results, see Section 5. To download a zip file containing theraw log files for the Solo-4 Forensic test runs, see http://www.cftt.nist.gov/TBD.November 2013Page 3 of 12Image MASSter Solo-4
Test Case ResultsCaseResults01-sasExpected Results01-sata28Expected Results01-sata48Expected Results01-usbExpected Results02-cfExpected Results02-thumbExpected Results04Expected Results06-sasExpected Results06-sata28Expected Results06-sata48Expected Results06-usbExpected Results07-cfExpected Results07-thumbExpected Results08-ata28Expected Results08-ata48Expected Results08-dcoExpected Results09-abortExpected Results09-skipbloc Expected Results09-skipsec Expected Results10-encrypt Expected Results10-E01Expected Results10-compExpected Results12Expected Results14-sata28Expected Results14-sata48Expected Results14-cfExpected Results14-encrypt Not Expected14-sasExpected Results14-thumbExpected Results14-usbExpected Results17Expected Results19Expected Results24Expected Results25Expected Results4 Testing EnvironmentThe tests were run in the NIST CFTT lab. This section describes the selected testexecution environment, using the support software, and notes on other test hardware.November 2013Page 4 of 12Image MASSter Solo-4
4.1 Execution EnvironmentImage MASSter Solo-4 Forensic is a custom hardware device. The tests were run on theImage MASSter Solo-4 Forensic unit running software version v4.10.29.0 x32 andfirmware version v1.33.0.0 x32.4.2 Support SoftwareA package of programs to support test analysis, FS-TST Release 2.0, was used. Thesoftware can be obtained from: 4.3 Test Drive CreationThere are three ways that a hard drive may be used in a tool test case: as a source drivethat is imaged by the tool, as a media drive that contains image files created by the toolunder test, or as a destination drive on which the tool under test creates a clone of thesource drive. In addition to the operating system drive formatting tools, some tools(diskwipe and diskhash) from the FS-TST package are used to setup test drives.4.3.1 Source DriveThe setup of most source drives follows the same general procedure, but there are severalsteps that may be varied depending on the needs of the test case.1. The drive is filled with known data by the diskwipe program from FS-TST. Thediskwipe program writes the sector address to each sector in both C/H/S and LBAformat. The remainder of the sector bytes is set to a constant fill value unique foreach drive. The fill value is noted in the diskwipe tool log file.2. The drive may be formatted with partitions as required for the test case.3. An operating system may optionally be installed.4. A set of reference hashes is created by the FS-TST diskhash tool. These includeboth SHA1 and MD5 hashes. In addition to full drive hashes, hashes of eachpartition may also be computed.5. If the drive is intended for hidden area tests (DA-08), an HPA, a DCO or bothmay be created. The diskhash tool is then used to calculate reference hashes ofjust the visible sectors of the drive.The source drives for DA-09 are created such that there is a consistent set of faultysectors on the drive. Each of these source drives is initialized with diskwipe and thentheir faulty sectors are activated. For each of these source drives, a duplicate drive, withno faulty sectors, serves as a reference drive for comparison.4.3.2 Media DriveTo setup a media drive, the drive is formatted with one of the supported file systems. Amedia drive may be used in several test cases.4.3.3 Destination DriveTo setup a destination drive, the drive is filled with known data by the diskwipe programfrom FS-TST. Partitions may be created if the test case involves restoring from the imageof a logical acquire.November 2013Page 5 of 12Image MASSter Solo-4
4.4 Test Drive AnalysisFor test cases that create a clone of a physical device, e.g., DA-01, DA-04, etc., thedestination drive is compared to the source drive with the diskcmp program from the FS TST package; for test cases that create a clone of a logical device, i.e., a partition, e.g.,DA-02, DA-20, etc., the destination partition is compared to the source partition with thepartcmp program. For a destination created from an image file, e.g., DA-14, thedestination is compared, using either diskcmp (for physical device clones) or partcmp(for partition clones), to the source that was acquired to create the image file. Bothdiskcmp and partcmp note differences between the source and destination. If thedestination is larger than the source then the excess destination sectors are scanned andcategorized as either undisturbed (still containing the fill pattern written by diskwipe),zero filled or changed to something else.For test case DA-09, imaging a drive with known faulty sectors, the program diskcmp isused to compare a clone of the faulty sector drive to a reference drive. The referencedrive is a copy of the faulty sector drive with readable sectors where the faulty sectordrive has faulty sectors.For test cases such as DA-06 and DA-07 any acquisition hash computed by the tool undertest is compared to a corresponding reference hash of the source to check that the sourceis completely and accurately acquired.4.5 Note on Test DrivesThe testing uses several test drives from a variety of vendors. The drives are identified byan external label that consists of a two digit hexadecimal value and an optional tag, e.g.,25-SATA. The combination of hex value and tag serves as a unique identifier for eachdrive. The two digit hex value is used by the FS-TST diskwipe program as a sector fillvalue. The FS-TST compare tools, diskcmp and partcmp, count sectors that are filledwith the source and destination fill values on a destination that is larger than the originalsource.5 Test ResultsThis section presents the expected results for each test case along with the actual resultsproduced by the tool. To download a zip file containing the raw log files for the ImageMASSter Solo-4 test runs, see http://www.cftt.nist.gov/CFTT-Test-Run-Raw-Files v3.html.Test case DA-01 measures the tool’s ability to acquire a physical device source using aspecified access interface and to create a complete and accurate clone of the source to adestination drive. The test is repeated for each access interface supported by the tool. Theexpected result is measured by checking that all source sectors match correspondingdestination sectors in a sector-by-sector comparison.Test case DA-02 measures the tool’s ability to acquire a digital source (DS) to a clone ofthe same type. Some examples of digital sources are flash media, thumb drives, and hardNovember 2013Page 6 of 12Image MASSter Solo-4
drive partitions. The test is repeated for each digital source supported by the tool. Theexpected result is for all source sectors to match corresponding destination sectors in asector-by-sector comparison.Test case DA-04 measures the tool’s ability to acquire a physical device to a smallerphysical device. The expected result is for the tool to (1) copy source sectors to thedestination until there is no free space left on the destination and (2) the tool notifies theuser that the entire source has not been copied to the destination.Test case DA-06 measures the tool’s ability to create a complete and accurate image overa specified access interface (AI). The test is repeated for each access interface supportedby the tool. The expected result is for a hash value reported by the tool to match areference hash value for the imaged source.Test case DA-07 measures the tool’s ability to create a complete and accurate image froma specified digital source (DS). Some examples of digital sources are flash media, thumbdrives, and hard drive partitions. The test is repeated for each digital source supported bythe tool. The expected result is for a hash value reported by the tool to match a referencehash value for the imaged source.Test case DA-08 measures the tool’s ability to acquire a physical drive with hiddensectors to an image file. The expected result is for a hash value reported by the tool tomatch a reference hash value for the imaged so
The Imager MASSter Solo-4 Forensic system is a portable data acquisition device. The unit provides native interface support for SAS, SATA and USB drives in addition to supporting PATA. The tool acquired the test media completely and accurately. The following restore anomaly was observed.
Forensic Science is the integration of core scientific disciplines. Forensic science involves a variety of careers. 1. Students will recognize the major contributors to the development of Forensic . Worksheets Lab; Activity Project assessments Research activities such as “famous forensic scientists and their contributions” or “careers inFile Size: 444KBPage Count: 21People also search forforensic science for high school textbook pdfdo forensic criminologist investigate the cri forensic criminology bookswhat is a dental hygienisthow to check fingerprint forensic criminologyare dental hygienists and dentist same thing
25 FLUTE SOLO, OBOE SOLO, CLARINET SOLO 26 SAXOPHONE SOLO, BASSOON SOLO, TRUMPET SOLO, TROMBONE SOLO, EUPHONIUM SOLO, TUBA SOLO 1 WIND INSTRUMENT WITH ACCOMPANIMENT, piano unless stated otherwise: 26 PICCOLO with accompaniment 27 FLUTE with accompaniment 28 FLUTE PLAY ALONG 29 OBOE with accompaniment 30 OBOE
Forensic science is the application of science to law. Any science can be applied into a legal situation, but some of the commonest forensic sciences include forensic biology, forensic chemistry, and forensic toxicology. The word forensic in today’s world simply
forensic science discipline (or equivalent). Experience It is essential that the post holder is an experienced forensic scientist in forensic drug analysis, forensic toxicology and preferably in forensic criminalistics, with a minimum of 10 years performing multi-disciplined forensic
Forensic Psychology Chapter ObjeCtives ·orensic Define f psychology. · Review career areas in the forensic sciences. · Distinguish forensic psychology from forensic psychiatry. · Identify and describe the major subareas of forensic psychology. · Review the educational, training, and certification requirements to become a forensic psychologist.
Delivering forensic services (Report 21: 2018-19) 4 . Summary of audit findings . Delivering forensic services . We audited four types of forensic services: fingerprints, deoxyribonucleic acid(DNA), forensic medical examinations and illicit drugs. Three of these services accounted for approximately 92 per cent of all forensic services .
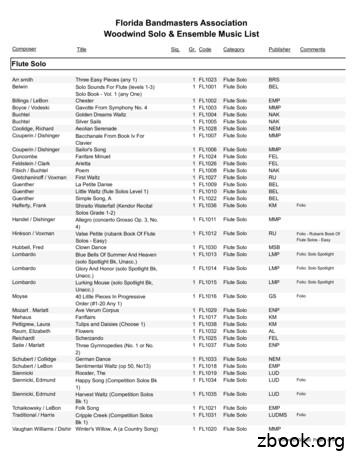
Florida Bandmasters Association Woodwind Solo & Ensemble Music List Composer Title Sig. Gr. Code Category Publisher Comments Flute Solo Arr.smith Three Easy Pieces (any 1) 1 FL1023 Flute Solo BRS Belwin Solo Sounds For Flute (levels 1-3) Solo Book - Vol. 1 (any One) 1 FL1001 Flute Solo BEL Billings / LeBon Chester 1 FL1002 Flute Solo EMP
children are most likely to live in a conflict zone. In 2016, about 2 in 5 children in this region were living within 50km of a conflict event in their country, and children in Syria, Iraq, Yemen and other warzones in the region are at high risk of all six grave violations. Africa is second, with 1 in 5 children affected by conflict. Syria, Afghanistan and Somalia are at the top of our ranking .