SSL Everywhere Sales Playbook
SSL Everywhere Sales Playbook
SSL Everywhere Sales Play PrerequisitesThis playbook assumes a basic understanding ofBIG-IP LTM technologies, SSL Everywhere referencearchitecture, use cases, and value, based on existingtraining materials.BIG-IP LTM educationWeb based training and product information Product Training F5 University Partner Central: Local Traffic Manager Manuals and Release Notes on f5.comSSL Everywhere Reference ArchitectureSolution information f5.com SSL Everywhere Partner Central: SSL Everywhere RA F5 Networks, Inc.2
Topics To Drive SSL Everywhere WinsTOPICMake More Money Selling SSL Everywhere!SSL Market And Customer ChallengesIdentify SSL Everywhere OpportunitiesSelling SSL Everywhere - OffloadSelling SSL Everywhere - InterceptWinning With SSLLicensing OptionsNote: You should be trained already in BIG-IP LTM F5 Networks, Inc3
Make More Money Selling SSL Everywhere!Make More Money Selling SSL Everywhere!Engage withCustomersExpand AccountFootprintGrow DealSizeSecurity and privacy arecompetitive differentiatorsand therefore a topicbusiness agenda itemEnsure F5 as a criticalcomponent of all SSLarchitectures and leverageF5’s SSL leadershipSSL has become a criticalcomponent of all networkprojects due to thechallenges of encryption F5 Networks, Inc4
The New Perimeter Is An App PerimeterApps Are The Gateway to Data!TRADITIONALF5APPSSLSSLAppSSLTRADITIONAL NETWORK PERIMETERPER-APP / PER-USER PERIMETERSSL-visible Location-independent Session-based Continuous trustverification Strategic control points App availability IT’S TIME TO RETHINK SECURITY ARCHITECTURES F5 Networks, Inc5
F5 Architecture For The New PerimeterFull Proxy defense against advanced security threats Chain Security Services SSL inspection Access & app protection Partner ecosystem Execute Protection Performance & scalability Hybrid delivery Per-app defense F5 Networks, IncInspection ZoneUser SideEvaluateContextChainServicesDeployment ModesRiskReputation BehaviorLocation User/Device12ExecuteProtections Evaluate Context User, device, location, etc. Behavior Threat risk vs. app LSTRONG AUTHWEB APP FIREWALLURL FILTERINGApp Side3RouterClone / MirrorICAP / ProxyL2 BridgeNGFWIDSDATA LOSSPREVENTIONAPTSCANNINGWEB APPFIREWALLPACKET /FORENSICSANTIVIRUSIPSA FOUNDATION FOR MORE COMPREHENSIVE SECURITY6
F5 Security Messaging HierarchyF5 Corporate Messaging &Security Architecture MessagingF5 App AccessF5 App ProtectionSales PlaysSSLEVERYWHERE F5 Networks, IncDDOSPROTECTIONAPP PROTECTIONAPPACCESSWEB FRAUDPROTECTION7
Understanding the SSL Market andCustomer Challenges
SSL Market and Customer ChallengesKey Takeaways For Market And Customer Challenge1 SSL market is projected to double this yearGrowth driven by data breaches, compliance, and2privacy3 SSL growth creates challenges for our customers andopportunity for F5 F5 Networks, Inc9
SSL Market and Customer ChallengesF5 Leads ADC & The SSL Market Is GrowingSSL Traffic Projected To Double This YearThere is a steady increase in encryption strategyMarket Growth and Revenue TrendsTAM in 2015 for ADC (includes SSL Offload) stands at 2BTAM in 2015 for SSL Intercept is estimated at 500M SSL traffic is projected to reach 64% by 2016,up from 29% in 2015 F5’s ADC Market Share 52% in 2014, Gartner Gartner recognized F5 as a Leader in 2015 GartnerMagic Quadrant for Application Delivery Controllers SSL Cert Market will grow 21% (CAGR) F5 Networks, Inc.Amount of Encrypted Traffic29%64%SSL IN 2015PROJECTEDSSL IN 2016Source: 1 Sandvine, Global Internet Phenomena Spotlight: Encrypted Internet Traffic 2. Ponemon, 2015 Global Encryption & Key Management Trends Study 3. IT Market Research Report10
SSL Market and Customer ChallengesSSL Is Growing Due To Data Breaches, Compliance, And Privacy64% SAYCOMPLIANCE ISMOSTIMPORTANTDRIVER FORSSLPonemon Institute 1000 Price Tagfor a stolen cert in theunderground market1Ponemon Institute34% growth inkeys and certificatesover the past 2 yearsPonemon Institute57% Europeans are worried their data isnot safe SymantecOnly 3 in 10OrganizationsDetected the Breachon Their Own (Source: Mandiant M-Trends 2015)205 Daysthreats were presentbefore detection(Mandiant M-Trends 2015)58%of Security Teams needbetter security toprotect keys and certificates26% of SSL applications usenon-standard portsPalo Alto NetworksPonemon Institute F5 Networks, Inc.11
SSL Market and Customer ChallengesSSL Growth Creates Challenges For Our Customers AndOpportunity For F5The Complexity of SSL Growth Compliance is complex and costly Increased frequency of SSL attacks isstressing IT operations Maintaining consistent SSL policy ischallenging Enabling SSL on next-gen securityproducts kills performance F5 Networks, Inc 1M Cost of single cyberattack can be wellabove 1,000,00050%Received a C Gradeor lower on theirSSL assessment81%Performance losswhen enabling SSL onNGFWs1Source: 1 NSS Labs, SSL Performance Problems; 2 Ponemon, Cost of Failed Trust Report3. SSL Pulse12
Identifying SSL Opportunities
Identify SSL Everywhere Opportunities4 Key Steps to Identifying an SSL Opportunities1 Identify customers with sensitive data2 Identify your target persona3 Ask qualifying questions4 Determine which SSL deployment is right for yourcustomer F5 Networks, Inc14
Step 1: Identify Customers With Sensitive DataExample PCILatest PCI regulations requiremodern encryptionby June 2016Find Out MoreAll PCI merchants willreview SSL in ation (PII)Credit Cards (cardholder data),Bank account numbers, financial informationand credit-related data, SSNPCI, SOX, FDICDisclosure lawsRetailCardholder dataCredit Cards (cardholder dataPCI, DisclosurelawsHealthcare*Protected HealthInformation (PHI)information about health status, provision ofhealth care, or payment for health care thatcan be linked to a specific individual.HIPPA, HITECHGovernmentMilitary andgovernment dataData specific to government programs,particularly those related to militarydepartments.Highly regulated* highest increase in encryption deployments64% SAY COMPLIANCE IS MOST IMPORTANT DRIVER FOR SSL F5 Networks, Inc.15
Identify SSL Everywhere OpportunitiesStep 2: Within Each Org., Identify Target PersonasEXECUTIVE LEADERConcerned with the cost,necessity and ROI;adapting traditionalbusiness, technology,commerce, andmarketing practices to adigital world. Managing organizationallosses due to databreaches and attacks Maintaining compliance Data centerconsolidationSECURITY/ NETWORKVP, DIR., ARCH.Defines andImplements networkinfrastructure Deploys, maintains,and reports onsecurity controls Investigates securityincidents Collaborate with othersto identify and defineeffective controlsAPPLICATION OWNERCOMPLIANCE MGRDeploys and manages theapp service & roadmap andensure the success ofbusiness/appMaintain PCI regulatorycompliance Ensures services that meetkey customer needs & keycompliance standards Assess app health andensures availability,performance and security Drives efforts to patchvulnerabilities Maintains awarenessof compliance risks; Ensures compliance Reports on theeffectiveness of WAFsolutionsBUSINESS UNIT LEADERS GAINING INFLUENCE OVER THEIR COMPANY’S ENCRYPTION STRATEGY. F5 Networks, Inc.16
Identify SSL Everywhere OpportunitiesStep 3: Ask Target Persona These QuestionsSSL Offload Tell me how you are preparing for more stringent SSL regulatory compliance requirements. How have you responded to the latest SSL vulnerabilities? What are your processes for key protection and management?SSL Intercept What’s your plan to address the performance and latency impact associated with decrypting and reencrypting at multiple points in the security service chain? How are your handling increases in inbound and outbound encrypted traffic? Does your outbound content filtering solution scale with the increase in encrypted traffic? F5 Networks, Inc.17
Identify SSL OpportunitiesStep 4: Determine Which SSL Deployment Is RightWould you like toinspect inbound SSLtraffic or outboundSSL traffic?INSHOWCASE THE SSLOFFLOADDEPLOYMENTSee Slide 29 F5 Networks, IncOUTTIP:Both optionsbuilt onBIG-IP LTMSHOWCASE THE SSLINTERCEPTDEPLOYMENTSee Slide 3418
Identify SSL Everywhere OpportunitiesStep 4: Based On Answers Prescribe DeploymentLISTEN FOR THESE KEY WORDSInbound Outbound Consolidation Visibility into encrypted traffic SSL performance Deploying new security products (NGFW, IPS, DLP, etc.) SSL grade (SSL Labs) Advanced security threats Compliance (PCI, FIPS) Security architectureOffload and TransformationSSL Intercept (Air-Gap)Use BIG-IP to enforce encryption policy to applications andfor in-line SSL VisibilityUse SSL Intercept for visibility into SSL traffic with 3 rd partysecurity devices like NGFW, NG-IPS, DLP, and APT threatsSSL Visibility:Firewall, IPS, WAF F5 Networks, IncRegulatedAppsWeakerStandardAppsClearFastAppsSSL InterceptCorporate NetworkAir-GapUserStrongerAir-GapStrongSSL OFFLOAD ANDTRANSFORMATIONOutboundInbound Internet19
Selling SSL Offload
Selling SSL OffloadKey Selling Steps1 Cover key functionality and value2 Highlight differentiation and VE crypto offload3 Handle objections F5 Networks, Inc21
Selling SSL OffloadStep 1: Cover Key Functionality In Your ConversationSSL OFFLOAD: ENFORCE CONSISTENT SSL POLICY WITHOUT COMPROMISING ON DATAPROTECTION, KEY PROTECTION, OR VISIBILITYCipher DiversityThe mostcompleterange ofenterpriseclass featuresPerformance― Industry leading SSL scale and performance― Improve end user performance with HTTP 2.0 and SPDYKeyProtection HSMs protect keys and certs throughout physical, virtual, and cloud environments Open APIs to automate management digital certificate and encryption keysiRules F5 Networks, Inc. Deeper protection with broader array of encryption options Enforce consistent SSL policy based on industry best practices Stop the latest SSL attacks with programmability Control your applications from connections and traffic22
Step 2: Highlight Industry Leading SSL Scale andPerformance300,000BIG-IP 12250v240K SSL TPS40G Bulk TputVIPRION 4800240K SSL TPS160G Bulk TputBIG-IP 12250VIPRION 4800L7 Requests Per Second (Inf-Inf)250,000VIPRION 2400176K SSL TPS144G Bulk Tput200,000150,000VIPRION 2200BIG-IP 10200v-SSL 88K SSL TPS72G Bulk Tput75K SSL TPSBIG-IP 7200v-SSL 33G Bulk Tput60K SSL TPS19G Bulk Tput100,00050,000BIG-IP 10G VE3.4K SSL TPS4G Bulk TputBIG-IP 2200s4K SSL TPS4G Bulk TputBIG-IP 4200v9K SSL TPS8G Bulk TputVIPRION 4480120K L7 RPS80G Bulk TputBIG-IP 5250v21K SSL TPS12G Bulk Tput0BIG-IP Virtual Edition BIG-IP 2000 Series F5 Networks, IncBIG-IP 4000 SeriesBIG-IP 5000 SeriesBIG-IP 7000 SeriesBIG-IP 10000 SeriesVIPRION 2200VIPRION 4480VIPRION 240023
Step 2: Highlight Data Protection F5 Networks, Inc.24
Step 2: Highlight Comprehensive SSL Lifecycle ManagementSecure VaultInternal HSMNetwork HSMSoftware based encryptedstorage system for securingcryptographic keys with thehighest performancePhysical hardware designed togenerate, store, and protectkeys with high performanceIntegration with leading networkbased hardware for use with allappliances, chassis, and VirtualEditionsCloud HSMIntegration for highassurance encryptionservices fit for the cloud.Enterprise Key andCertificate ManagementOpen APIs to automate management forthe digital certificate and encryption keytechnologies used by today’s enterprises F5 Networks, Inc25
Step 2: Highlight VE Crypto OffloadUserF5 Networks provides the industry’s firstSSL Crypto Offload for hybrid deployments Offload SSL processing from your Virtual Editionto the BIG-IP hardware platforms Achieve the maximum SSL performance of yourvirtual license Free up Virtual Edition CPU utilization for otherapplication servicesSSL Crypto OffloadAll Application ServicesExcept SSLSSL Acceleration SSL Crypto OffloadSSL Traffic Onlyfor OffloadBIG-IP 12250vF5 HardwareMultipleBIG-IP Virtual EditionsHigh PerformanceHigh Capacity SSLApplications F5 Networks, Inc26
Step 2: Highlight VE Crypto OffloadCapacityVE Stand-AloneSSLCryptoOffload F5 Networks, IncSSL PerformancevCPU Utilization1,500100%TPS1,500TPS34%66%MoreHybrid deployments cando more L4-7 ApplicationService workloads thanstand-alone VEs27
Selling SSL OffloadStep 3: Handle ObjectionsOBJECTIONRESPONSEThe biggest challenge in planningand executing a data encryptionIt’s cost effective control to deploy SSL without Scale or Performance issues. Save time andstrategy is discovering wheremoney by transition to encrypt-by-defaultsensitive data resides in theorganization.F5 offers both static and dynamic bypass list. URL filtering provides dynamic bypass. WeI don’t want to see my usersrecommend discussions with your legal department sooner than later to remove and projectprivate data like online bankingbarriers in the future. (quote Gartner)F5 helps consolidate multiple services, while simplify integration with multi vendor solutions.I want something simpleAllowing you to focus on universal policy enforcement rather than multiple SSL stacks. Thisgives you the ability provide a comprehensive defense in depth strategy. F5 Networks, Inc.28
Selling SSL Intercept
Selling SSL InterceptKey Selling Steps1 Cover key functionality and value2 Highlight differentiation3 Handle objections F5 Networks, Inc30
Selling SSL InterceptStep 1: Cover Key Functionality In Your ConversationSSL INTERCEPT: ADVANCED THREAT PROTECTION WITH F5SSL VisibilityAdvancedProtectionThe mostcompleterange ofenterpriseclass featuresSecureArchitectureURL Bypass F5 Networks, Inc. Inspect SSL traffic for hidden threats like malware across third party vendors Chain security services with full proxy for visibility and policy enforcement― Industry leading SSL scale and performance with hardware acceleration Integration with FireEye and other third party solutions to provide defense in-depth Firewall segmentation and key protection and an integral part of the design Flexible 1 or 2 box architecture for simplified troubleshooting and operations Bypass URL categories such as banking to protect user privacy Dynamically and static options available for individual requirements31
Step 2: As Defenses Evolve, Attackers Adapt and InnovateSSL the New Threat VectorSpotlight on the Game Changers Year over year growth in SSL traffic is notstopping New SSL protocols and ciphers can breaksecurity products 80% performance degradation with SSL onNGFWsStealthy Techniques Attackers continued to use novel techniques todeploy and hide web-based malware Shells planted on servers use SSL encryptionto evade network monitoring Because the victims had not configured theirnetwork architectures to permit security toolsto inspect SSL traffic, the attacker’s actionswent undetected F5 Networks, Inc“We expect this trend to continue, especially as moreorganizations adopt SSL encryption for all Internet-facingweb services.”Mandiant 2015 M-Trends Report32
Step 2: Highlight the challenges of today’s networkNew SSL protocols canbreak infastructureGrowing SSL stressesperformance New ciphers address highprofile vulnerabilities Multiple decrypt and encryptpoints adds overheadSSL Compatibility breaks manysecurity products SSL impacts performance by80% on NGFWs F5 supports the broadestrange of SSL protocols F5 offers industry leading SSLscale and performance F5 Networks, Inc33
Selling SSL InterceptStep 3: Handle ObjectionsOBJECTIONI don’t want to see my usersprivate data like online bankingI want something simpleI heard you are more expensivethan both Blue Coat and A10 F5 Networks, Inc.RESPONSEF5 offers both static and dynamic bypass list. URL Filtering provides dynamic bypass. Werecommend discussions with your legal department sooner than later to remove and projectbarriers in the future.F5 helps consolidate multiple services, while simplify integration with multi vendor solutions.Allowing you to focus on universal policy enforcement rather than multiple SSL stacks. Thisgives you the ability provide a comprehensive defense in depth strategy.Blue Coat charges 15K for their 250 mbps. It can’t help with scale, uptime, or defense.F5’s 2000 starts at 17K can do all of those.A10’s SSL Insight (Outbound) requires 2 boxes doubling the cost of the solution and doesn’tdecrypt beyond port 443.34
Winning With SSL Everywhere
Sales WinCustomer StoryWhat was customer trying to do?Initially: Scale FireEye sensor deployment beyond 4 Gbps Avoid outages from sensor failuresEventually: Added SSL decryption for outbound traffic with URL filtering toexclude certain traffic from decryption (PHI, Financial, etc.)Who was the audience? Network architects Security architectsWhat did we sell? 1.68M P&I 185K FYB Dedicated B2250 blades per data center SSL forward Proxy and URL Filtering licenseWhat won the deal? Trust and experience with the F5 account teamSuccessful proof of conceptExpanding the discussion beyond simple FireEye sensor LBEducating the customer on global privacy requirementsThe ability to pivot with the customer’s changing requirementsWho were we competing against? Cisco? We were able to prove that they had no solutionNew or existing F5 customer? Existing F5 customer expanding deployment F5 Networks, Inc36
Case Study:Blue Cross Blue Shield ofKansas CityBCBS needed to protect personal healthcare data while ensuring HA,performance and security of its site, which holds key healthcare planinformation for providers, brokers, and employers.“Before, SSL traffic was being terminated onthe server itself. That led to performanceproblems, especially as our traffic numbersbegan to increase. [By offloading SSL from theservers to the BIG-IP LTM device.] It lowers ouradministration and maintenance of our servers,and saves a considerable amount of time andmoney.”Chad O’NealWeb Technical EngineerCustomer Overview:Health benefits provider, servingmore than 880,000 members ingreater Kansas City, Missouri, KansasVertical:Location:BIG-IP LTM, Link Controller, and ASM Benefits: Met HIPAA security requirements Reduced page load times from 30 seconds to less than a second ISP redundancy removed serious network vulnerability by eliminating single pointof failure Consolidation onto LTM saves money in the long run by reduced admin duties andmaintenance costsCase -blueshield-cs.pdfInsuranceKansas City, MO F5 Networks, Inc37
Licensing Options
SSL LicensingInternal HSM/FIPS ModelsVIPRION Chassis - SSL LicensesBIP-IP 10200v FIPSF5-BIG-LTM-10200V-F 119,995BIG-IP 7200v FIPSF5-BIG-LTM-7200V-F 94,995BIG-IP 5200V FIPSF5-BIG-LTM-5200V-F 76,995SSL License Upgrade for 4800Chassis (Max TPS)F5-ADD-VPR-SSL8 69,995SSL License Upgrade for 44X0/2400Chassis (Max TPS)F5-ADD-VPR-SSL4 34,995SSL License Upgrade for 2200Chassis (Max TPS)F5-ADD-VPR-SSL2SSL Forward Proxy LicenseF5-ADD-VPR-SSL-FWD 34,995 9,995BIG-IP Appliance - SSL LicensesSSL Forward ProxyLicenseF5-ADD-BIG-SSL-FWD 4,995Network HardwareSecurity ModuleF5-ADD-BIG-EXT-HSM 4,995 F5 Networks, Inc.39
Flexible options to meet you where you are goingPLATFORMSA broad selection ofhardware andsoftware platformswhich can be blendedto meet your needs. F5 Networks, IncLICENSINGFlexible options acrossperpetual licensing,subscription modelsand on-demandconsumption.SERVICESA variety of F5 servicesand support options tohelp you succeedacross the applicationlifecycle.40
PLATFORMSA Broad Selection of PlatformsF5 Platforms25M200M1Gbps3Gbps5Gbps10GbpsVIPRION 2200VIPRION 2400FIPS 140-22000 series*4000 series5000 Series7000 Series10000 Series12000 SeriesVirtualPhysicalF5 softwareF5 hardwareProvide flexible deployment options for virtualenvironments and the cloud with Virtual EditionHigh-performance with specialized anddedicated hardwareVirtual Edition is best for:Physical Hardware is best for: Accelerated deploymentMaximizing data center efficiencyPrivate and public cloud deploymentsApplication or tenant-based podsKeeping security close to the appLab, test, and QA deployments F5 Networks, Inc Fastest performanceHighest scaleSSL offload, compression, and DoS mitigationAn all F5 solution: integrated HW SWEdge and front door servicesPurpose-built isolation for application deliveryworkloads*Note: 2000 Series appliances is not offered with Better or Best bundlesVIPRION 4480VIPRION 4800HybridPhysical virtual hybrid ADC infrastructureUltimate flexibility and performanceHybrid is best for: Transitioning from physical tovirtual and private data center tocloud Cloud bursting Splitting large workloads Tiered levels of service41
LICENSINGChoose How to Consume F5 SoftwareCloud options tailored to customer needs for greater flexibility and choiceVolume of F5-backed AppsCloud Licensing Program(CLP)Bring Your Own License(BYOL)Volume Licensing Subscription(VLS)On-demand Utility pricing withhighest flexibility; pay-as-you-go orannual subscription.Perpetual VE License whichSubscription discounts for 100 customer owns and can move across applications; 1 or 3-year terms, up toprivate and public clouds.78% discount. Includes premiumsupport services.Public cloudPublic, private, and hybridPublic, private and hybridBest for deployment flexibility; ondemand consumptionBest for few production workloads orexisting licensesBest for large scale workloadproduction; F5 for every app.OPEXCAPEXOPEXvia F5 or channel partnerPrice/License F5 Networks, Inc 42
LICENSINGFind an F5 Ready Public Cloud ProviderVerified by F5 for greater cloud confidenceF5-verifiedBIG-IP products verified byF5 for compatibility in F5Ready clouds.Global-reachingFlexibleF5-verified providers spanAmericas, EMEA, and APAC forbroad reach and selection.Variety of purchase options:BYOL, on-demand Utility billing,Volume Licensing Subscription.Note: F5 adds new partners on a regular cadence, check f5.com/f5ready for the most up-to-date list F5 Networks, Inc43
SERVICESDrive Greater ROI with Global ServicesThroughout the Solution Lifecycle F5 Networks, IncOptimizeArchitectMaximize performance, health, security Proactive Assessments andIntegration iHealth / AskF5 / DevCentral CertificationDesign for best-practices deployments Solution Definition Workshops Design and AssessmentsMaintainImplementEnsure continued availability Upgrades and Expert Services World-class Support Premium Plus and EnhancedServicesDeploy quickly and optimally Installations and Migrations Web and Onsite Training44
SERVICESGlobal Services Optimized for your InitiativesEnd-to-end Services and Support options to meet your customer’s needsTraditional ADCArchitectDesign for best practicesImplementQuick and optimalSecurityCloudSolution Definition WorkshopDeployment & Migration ServicesTraining and CertificationMaintainBacked by F5 SupportMaintenance AgreementsPremium Plus SupportOptimizeMaximize performance, health,security F5 Networks, IncCustomization & ScriptingiHealth Diagnostics & Self-help Tools45
SERVICESFlexible Services OptionsPackaged, Custom & HourlyPackagedCustomHourlyLicense: Fixed PriceLicense: CustomLicense: HourlyScoped to meet popularcustomer solutions.Scoped to meet your specificbusiness and solution needs.Flexible procurement options.Small-scale services for ad-hoccustomization and scriptingFocus: Customer andtechnology trends. Carefullyaligned with F5 pricingbundles GBB and popularcustomer solutions.Focus: Complex or uniquesolutions, or where a customercan leverage our deep skills.Focus: Extended applicationverification, complex monitors,iRules scripting, iControl API, andother automated tasks.F5 UNITY Gold or Platinum PartnersDedicated Professional Services staffbacked by F5 certifications F5 Networks, Inc46
Gartner recognized F5 as a Leader in 2015 Gartner Magic Quadrant for Application Delivery Controllers SSL Cert Market will grow 21% (CAGR) F5 Leads ADC & The SSL Market Is Growing SSL Traffic Projected To Double This Year SSL Market and Customer Challenges There is a steady increase in encryption strategy PRO
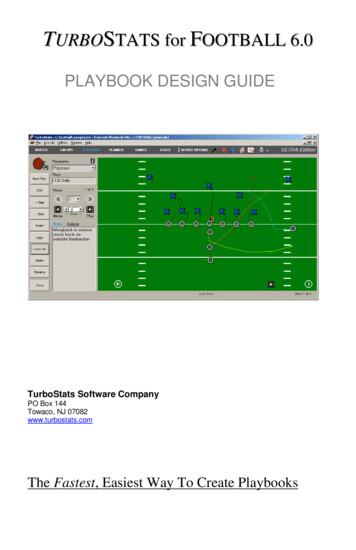
playbook, Offensive Formation playbook, Defensive Formation playbook and Drills click the Database Selector pull down list. Creating a New Playbook File There are two ways to make playbook files. 1. File New Playbook File will start you off with a blank playbook or 2. File Save Playbook
A sales playbook outlines every step of the sales process to ensure sales efficiency and effectiveness. This example playbook gives you an inside look at what a real playbook for a Sales Development Rep (SDR) or Business Development Rep (BDR) should include. Every playbook is custom to fit business and industry needs, so we don't
l DecryptionServices DPI-SSL/TLSClient l ViewingDPI-SSLStatus l DeployingtheDPI-SSL/TLSClient DecryptionServices DPI-SSL/TLSClient TIP:ForinformationaboutDPI-SSL,seeAboutDPI-SSL. SonicOS7DPI-SSLAdministrationGuide ConfiguringtheDPI-SSL/TLSClient 2 8
administrators of Windows Server 2003 & 2008R2 to harden SSL/TLS support. Administrators can manually edit and backup the SSL configuration and set PCI-DSS compliant SSL rules with a click of a button. Link SSL Audit (alpha) - A remote SSL audit tool able scan for SSL/TLS support against remote servers.
Proposed SSL 2015 Salary Midpoints versus SSL 3 and Market Present (SSL 3) SSL 2015 Midpoint SSL 2015 Midpoint/Market Benchmark (%) 11,400 154 12,084 144 12,809 135 13,578 127 . SSL 2015 vs. Market for Nurses (Total Guaranteed Compensation PBB) 17 (254%) (281%) (209%) SSL 2015 vs. Market for Teachers (Total Guaranteed Compensation PBB) 18 .
Go to SETUP - VPN Settings - SSL VPN Server - SSL VPN Policies, create a policy that allow the SSL VPN users to access remote network. Add a SSL VPN policy and follow below parameters on SSL VPN Policy Configuration Page. Policy For: Global Apply Policy to: All Addresses Policy Name: Allow_all_address Begin: 0 End: 65535 Service: All .
Add products to quote, order, or invoice Reopen a lead Close an opportunity Track competitors Manage sales literature Manage org charts for accounts Enforce best practices with playbooks Playbook manager guide Define playbook categories Manage playbook templates Playbook user gui
Tulang hyoid (1) bersama dengan cartilages menyusun rangka dari larinx. Hyoid terletak pada dasar lidah dan melekat pada dasar tl tengkorak (skull) dengan bantuan ligaments. Source: Wesley Norman, PhD, DSc (1999 ), Homepage for the Anatomy Lesson.html . THE STERNUM STERNUM (1) : berbentuk palang terletak di tengah dada. Bersama dgn tulang rusuk (rib) menyusun rongga Thorax. The sternum .