Network Security Basics Elsevier-PDF Free Download
Sep 30, 2021 · Elsevier (35% discount w/ free shipping) – See textbook-specific links below. No promo code required. Contact Elsevier for any concerns via the Elsevier Support Center. F. A. Davis (25% discount w/free shipping) – Use the following link: www.fadavis.com and en
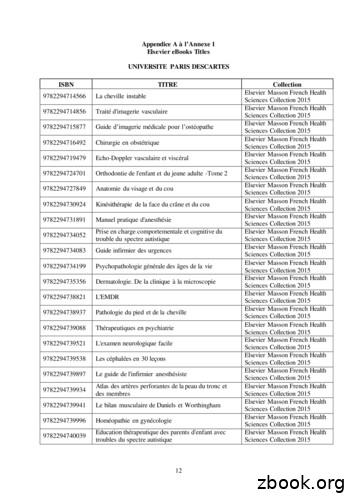
9782294745027 Anatomie de l'appareil locomoteur-Tome 1 Elsevier Masson French Health Sciences Collection 2015 9782294745294 Méga Guide STAGES IFSI Elsevier Masson French Health Sciences Collection 2015 9782294745621 Complications de la chirurgie du rachis Elsevier Masson French Health Sciences Collection 2015 9782294745867 Le burn-out à l'hôpital Elsevier Masson French Health Sciences .
The Elsevier Foundation is a corporate not-for-profit 501(c) (3), funded by Elsevier, a global information analytics business specialized in science and health. Since 2006, the Elsevier Foundation provides over 1 million USD a year in grants to knowledge-centered institutions around the world, which address the UN Sustainable Development
The Human Body in Health and Illness Hardcopy 2018 Herrlihy Elsevier strong 6th /strong Ed. 978-0323498449 NUR120 Geriatric Nursing Basic Geriatric Nursing Hardcopy 2020 Williams Elsevier 7th Ed. 978-0323554558 NUR120 Geriatric Nursing Simulation Learning System for LPN/LVN Electronic 2012 Elsevier Elsevier 11th Ed. 978-1455700110 NUR125
Mar 31, 2020 · Since January 2020 Elsevier has created a COVID-19 resource centre with free information in English and Mandarin on the novel coronavirus COVID-19. The COVID-19 resource centre is hosted on Elsevier Connect, the company's public news and information website. Elsevier
t22 mahon textbook of diagnostic microbiology latest elsevier 123 murray medical microbiolosy latest elsevier 124 nagoba medical microbiology and parasitology: prep manual for undergraduates latest elsevier t25 parija textbook of microbiology and immunology latest elsevier t26 patwardhan neeta handbook of practical examination in microbiology
security in application, transport, network, link layers Network Security 8-3 Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Message integrity 8.4 Securing e-mail 8.5 Securing TCP connections: SSL 8.6 Network layer security: IPsec 8.7 Securing wireless LANs 8.8 Operational security
Python Basics.ipynb* Python Basics.toc* Python Basics.log* Python Basics_files/ Python Basics.out* Python_Basics_fig1.pdf* Python Basics.pdf* Python_Basics_fig1.png* Python Basics.synctex.gz* Python_Basics_figs.graffle/ If you are reading the present document in pdf format, you should consider downloading the notebook version so you can follow .
Basics 2 7.2 kV Bus 1-Line : Basics 3 4.16 kV Bus 1-Line : Basics 4 600 V 1-Line : Basics 5 480 V MCC 1-Line : Basics 6 7.2 kV 3-Line Diagram : Basics 7 4.16 kV 3-Line Diagram
3 CONTENTS Notation 10 Preface 12 About the Author 18 PART ONE: BACKGROUND 19 Chapter 1 Computer and Network Security Concepts 19 1.1 Computer Security Concepts 21 1.2 The OSI Security Architecture 26 1.3 Security Attacks 27 1.4 Security Services 29 1.5 Security Mechanisms 32 1.6 Fundamental Security Design Principles 34 1.7 Attack Surfaces and Attack Trees 37
Network Security Groups Network Security Groups are used to provide traffic control at the packet level. You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allo
network.edgecount Return the Number of Edges in a Network Object network.edgelabel Plots a label corresponding to an edge in a network plot. network.extraction Extraction and Replacement Operators for Network Objects network.indicators Indicator Functions for Network Properties network.initialize Initialize a Network Class Object
Network security administrators earn a good income. According to Glassdoor, network security administrators earn a national average of almost 70,000 per year. CompTIA Security is the first step in starting your career as a network security administrator or systems security administrator. Professionals who are CompTIA Security certified are
1 8: Network Security 8-1 Chapter 8: Network Security Chapter goals: understand principles of network security: cryptography and its manyuses beyond “confidentiality” authentication message integrity key distribution security in practice: firewalls security in application, transport, netwo
network data security issues (e.g., personal information protection). 49 Operation Security Implement measures to monitor network operations and network security related activities. 21(3) Introduce emergency plans or review exiting plans in order to effectively and timely respond to system loopholes and Network Security Hazards. 25
of network security. 2 What is network security? 2.1 Background x3 will present in some detail how networks and network services can be de-scribed rigorously for studying network security. In the meantime, this section explains a few basic concepts necessary to understand the threats. A member of a network is a software or hardware module .
24. The Developing Human: Clinically Oriented Embryology Moore Elsevier 8th, 2007 2 25. Netter’s Atlas of Human Embryology: Updated Edition Cochard Elsevier 2012 2 26. Textbook of Clinical Embryology Singh Elsevier 2012 4 27. Medical genetics with Student Consult Online Access
9780323354905 Farag Brown's Atlas of Regional Anesthesia eBook available 5 Elsevier 2017 9780323400565 Farag Brown's Regional Anesthesia Review eBook available 1 Elsevier 2017 9780323394970 Fleisher Essence of Anesthesia Practice 4 Elsevier 5/17 9781605475509 Flood Stoelting's Pharmacology and Physiology in Anesthetic Practice 5 Wolters Kluwer 2015
to a lawsuit filed by Elsevier against the site and herself in a New York court (Elsevier Inc. et al v. Sci-Hub et al Case No. 1:15-cv-04282-RWS). Rather than lying low, or focusing on a legal defense, Elbakyan responded to the court case with a highly visible public campaign against the publisher who sued her (Elsevier), and the business practices
Elsevier Foundation provides over 1 million USD a year in grants to knowledge-centered institutions around the world, which address the UN Sustainable Development Goals through tech-enabled innovations in health information, diversity in science and health, research in developing countries. The Elsevier Foundation also offers a comprehensive
Elsevier has established agreements and developed policies to allow authors whose articles appear in journals published by Elsevier,to comply with potential manuscript archiving requirements as specified as conditions of their grant
If you need to publish open access, remember that most Elsevier journals explain their open access options on the journal homepage (see 2.4). Submit your paper to only one journal at a time (see 3.6, on ethics). 2.2 JOURNAL FINDER The Journal Finder tool locates Elsevier journals that most closely match your abstracts. An Elsevier journal will be recommended if it has published .
Optimization of FCC Units (3rd Edition) 2012 Elsevier Fluid Flow for Chemical Engineers (2nd Edition) 1995 Elsevier Fluid Power Dynamics 2000 Elsevier Fluidization; Solids Handling; and Processing - Industrial Applications 1998 William Andrew Publishing/Noyes Food Process Engineering an
1. Fundamentals of Reservoir Engineering by Dake, L P, Elsevier 2. The Practice of Reservoir Engineering, by Dake, L.P., Elsevier 3. Reservoir Engineering Handbook, by Tarek Ahmed, Gulf Professional Publishing,Elsevier 4. Applied Petroleum Reservoir Engineering
1. Fundamentals of Reservoir Engineering by Dake, L P, Elsevier 2. The Practice of Reservoir Engineering by Dake, L.P., Elsevier 3. Reservoir Engineering Handbook by Tarek Ahmed, Gulf Professional Publishing,Elsevier 4. Applied Petroleum Reservoir Engineering
1. Nursing Concepts Online (NCO) is a combination of several Elsevier products, which allows for a more holistic course. NCO contains Elsevier Adaptive Quizzing, Clinical Skills, HESI Patient Reviews, and Case Studies as well as links to Giddens' Concepts for Nursing Practice, and two sets of quizzes. Select versions of NCO also include SimChart.
Permissions may be sought directly from Elsevier's Science & Technology Rights Department in Oxford, UK: phone: ( 44) 1865 843830, fax: ( 44) 1865 853333, e-mail: permissions@elsevier.com.uk. You may also complete your request on-line via the Elsevier
1 Circulation Journal 2.540 J Stage 12 P High 2 European Journal of Radiology 2.687 Elsevier 12 P Moderate 3 American Journal of Cardiology 2.570 Elsevier 12 P Moderate ASED ON PAPER'S RESEAR H OMPLIAN E 1 Journal of Cardiology 2.246 Elsevier 12 P High 2 Cardiology 1.791 Karger 12 P Moderate
ISBN Elsevier North-Holland, Inc., 0-444-1 5255-5 Published in March 1977 by Elsevier/Excerpta Medica/North-Holland, P.O. Box 21 1, Amsterdam and Elsevier North-Holland Inc., 52 Vanderbilt Avenuz, New York, N.Y. 10017. Suggested series entry for library catalogues: Ciba Foundation Symposia.
1. Advances in Building Energy Research, Taylor & Francis online 2. American Journal of Applied Science, Science Publications 3. American Journal of Biochemistry and Biotechnology, Science 4. Annual Review of Energy and the Environment, UC Berkeley 5. Applied Acoustics, Elsevier 6. Applied Energy, Elsevier 7. Applied Ergonomics, Elsevier 8.
Aug 26, 2015 · Modern Network Security Threats Explain network threats, mitigation techniques, and the basics of securing a network 1.1 Securing Networks Explain network security 1.2 Network Threats Describe various types of threats and attacks 1.3 Mitigating Threats Explain tools and procedures to mitigate the effects of
Unit 3 SQL language: basics DBMG 2 SQL language: basics Introduction The SELECT statement: basics Nested queries Set operators Update commands Table management. Databases SQL language: basics Elena Baralisand Tania Cerquitelli 2013 Politecnico
Automotive Basics - Course Description "Automotive Basics includes knowledge of the basic automotive systems and the theory and principles of the components that make up each system and how to service these systems. Automotive Basics includes applicable safety and environmental rules and regulations. In Automotive Basics, students will gain
Any security plan is an attempt to strike the proper balance between the two. As in any other specialty fi eld, security professionals speak a language all their own and understanding the concepts requires that you learn the jargon.
AVG Internet Security 9 ESET Smart Security 4 F-Secure Internet Security 2010 Kaspersky Internet Security 2011 McAfee Internet Security Microsoft Security Essentials Norman Security Suite Panda Internet Security 2011 Sunbelt VIPRE Antivirus Premium 4 Symantec Norton Internet Security 20
HP Security Manager (Security Manager) is a security compliance solution for a fleet of HP products. It enables administrators to create a security policy to reduce network risks and monitor security for a fleet of printers. The key benefits of using Security Manager are the following: Easily and quickly create device security policies.
3 CONTENTS Notation 10 Preface 12 About the Author 18 PART ONE: BACKGROUND 19 Chapter 1 Computer and Network Security Concepts 19 1.1 Computer Security Concepts 21 1.2 The OSI Security Architecture 26 1.3 Security Attacks 27 1.4 Security Services 29 1.5 Security Mechanisms 32 1.6 Fundamental Security Des
computer security Security Management: Risks, Policies, and Ethics First principles of cyber security Introduction to cryptography Data security and privacy OS security Software security Network security Cybersecurity practice Hands-on labs OS and network hardening Cyber Defense Competition 8
The Target of Evaluation (TOE) is RSA Security Analytics (SA), hereafter referred to as Security Analytics, SA or the TOE. 2.1 TOE Overview SA is a collection of appliances that form a security infrastructure for an enterprise network. This architecture provides converged network security monitoring and centralized security information and .
Chapter 8: Network Security Goals: understand principles of network security: cryptography and its many uses beyond “confidentiality” authentication message integrity security in practice: firewalls and intrusion detection systems security in application, transport, network, link laye