Monitoring Cisco Standalone C-Series Servers Using SNMP .
Monitoring Cisco Standalone C-Series Servers usingSNMP and iReasoning MIB BrowserSeptember 2013Jeff Foster (TME)Cisco SystemsSection #1: Cisco Standalone C-Series SNMP Monitoring OverviewSection #2: Configuring SNMP on Standalone C-Series ServersSection #3: Cisco Standalone C-Series MIB OverviewSection #4: Setting up iReasoning MIB --------------------Section #1: Cisco Standalone C-Series Monitoring Overview:Cisco Standalone C-Series servers support many communication channels including SNMP.Using SNMP communication we are able to get/read the information from the C-SeriesIntegrated Management Controlled (IMC) – the system baseboard management controller.Additionally, the Cisco IMC can be configured to generate SNMP notifications (traps/informs) asevents occur.Cisco IMC generates SNMP notifications as either traps or informs. Traps are less reliable thaninforms because the SNMP manager does not send any acknowledgment when it receives atrap, and the initiating system cannot determine if the trap was received. An SNMP managerthat receives an inform request acknowledges the message with an SNMP response PDU(Protocol Data Unit). If the IMC does not receive the PDU, it can send the inform request again.As part of this SNMP implementation, the Cisco IMC supports all three versions of SNMP i.e.SNMPv1, SNMPv2c and SNMPv3. Both SNMPv3 and SNMPv2c use a community-based formof security. We can perform SNMP get, get next, getbulk and SNMP walk on these systems.Note: SNMP v3 requires that the IMC is running v1.5 or later firmware.To perform any SNMP operation(s), we need to configure SNMP on the target systems. (DefaultSNMP is disabled on the IMC). Directions for enabling SNMP are available in Section #2.This Document Contains Cisco Public Information
Section #2: Configuring SNMP on Standalone C-Series ServersSNMP Configuration Steps through GUI (WebUI):Perform the following steps in order to configure the C-Series SNMP services:1. Open the system WebUI:2. Select Admin tab and Communication Services page.3. Select the SNMP tab in the main window:4. Enable SNMP admin state. (Default SNMP is disabled)5. Configure the SNMP Access/Trap community strings and select community access level fromthe drop-down box. After providing necessary inputs save the changes to be effective.Configure SNMP Users (SNMPv3):SNMPv3 supports user authentication and can be configured for up to 15 users on the Admin Communication Services SNMP Page.This Document Contains Cisco Public Information
1. Select the user to be configured and then the ‘Add’’ button2. Provide Name and Security Level along with passwords (as appropriate).Note: Available Security Levels include “no auth, no priv”, “auth, no priv” and “auth/priv”Configure Trap Destinations:The Cisco IMC also supports configuration of up to 15 trap destinations. Trap destinations canbe configured from the on the Admin Communication Services SNMP Page.1. Select the Trap Destinations tab (located on the right side of the task pane)2. Select a trap destination (SIM Server) line and then the ‘Add’ button3. Provide necessary configuration details including: (Save Changes when complete)A. EnableB. SNMP VersionC. Trap TypeD. User (SNMPv3)E. Destination IP4. Repeat as necessary and ensure that traps are being sent to the SIM Server IP.5. To verify connectivity in later stages of the configuration, this configuration window allows youto send test traps.This Document Contains Cisco Public Information
User documentation for configuring communication Services in IMC v1.5 is available here:http://www.cisco.com/en/US/docs/unified computing/ucs/c/sw/gui/config/guide/1.5/b Cisco UCS Cseries GUI Configuration Guide.151 chapter 01010.htmlCisco IMC CLI Configuration:Open CLI session for the IMC using proper credentials. And follow the below mentionedcommands to configure SNMP. Inputs used here are to demonstrate only. Provide inputs asper your need/choice.Server# scope snmpServer /snmp # set enabled yesServer /snmp *# commitServer /snmp # set community-str cimcpublicServer /snmp # set community-access FullServer /snmp # set trap-community-str publicServer /snmp *# set sys-contact "User Name username@example.com "Server /snmp *# set sys-location "San Jose, California"Server /snmp *# commitConfigure Trap receiver to receive SNMP traps from Cisco IMC using CLI:Server# scope snmpServer /snmp # Scope trap-destinations 1Server /snmp/trap-destination *# set enabled yesServer /snmp/trap-destination *# set version 2Server /snmp/trap-destination *# set type informServer /snmp/trap-destination *# set user user1Server /snmp/trap-destination *# set v4-addr 192.2.3.4Server /snmp/trap-destination *# commitThis Document Contains Cisco Public Information
Configure SNMPv3 Users using CLI:If you wish to use SNMPv3, you need to create SNMPv3 User in IMC to enable SNMPv3communication.Here is the procedure to created SNMPv3 user in CLI, Below example enables SNMP, createsan SNMPv3 user named snmp-user, specifies the use of MD5 authentication, sets the passwordand privacy password, and commits the transaction:Server# scope snmpServer /snmp # scope v3users 2Server /snmp/v3users # set v3add yesServer /snmp/v3users *# set v3security-name ucsSNMPV3userServer /snmp/v3users *# set v3security-level authprivServer /snmp/v3users *# set v3proto SHAServer /snmp/v3users *# set v3auth-keyPlease enter v3auth-key:ex4mp1ek3yPlease confirm v3auth-key:ex4mp1ek3yServer /snmp/v3users *# set v3priv-proto AESServer /snmp/v3users *# set v3priv-auth-keyPlease enter v3priv-auth-key:!1@2#3 4%5 6&7*8Please confirm v3priv-auth-key:!1@2#3 4%5 6&7*8Server /snmp/v3users *# commitNote:Refer to corresponding Cisco IMC CLI Configuration Guide. The v1.5 documentation isavailable here:http://www.cisco.com/en/US/docs/unified computing/ucs/c/sw/cli/config/guide/1.5/b Cisco UCS Cseries CLI Configuration Guide 151 chapter 01010.html#d45101e722a1635.Section #3: Cisco Standalone C-Series MIB Overview:Cisco UCS MIB files are a set of objects that are private extensions to the IETF standard MIB II. If yourNMS cannot get requested information from a Standalone C-Series server or Cisco UCS, then the MIBthat allows that specific data collection might be missing. Typically, if an NMS cannot retrieve aparticular MIB variable, either the NMS does not recognize that MIB variable, or the agent does notsupport the MIB variable. If the NMS does not recognize a specific MIB variable, you might need to loadthe MIB into the NMS, usually with a MIB compiler. This is the case HP SIM and in Section #5 we willreview the process of using the SIM MIB Compiler to Compile the required Cisco MIBs.Prerequisite MIBS:The MIBs in this section are required for all use cases and need to be loaded before other Cisco MIBs areloaded. You should load the MIBs in the order listed to eliminate most of the load-order issues. SNMPv2-SMI.myThis Document Contains Cisco Public Information
SNMPv2-TC.my SNMP-FRAMEWORK-MIB.my RFC1213-MIB.my IF-MIB.my CISCO-SMI.my CISCO-ST-TC.my ENTITY-MIB.my INET-ADDRESS-MIB CISCO.TC.myBelow are the MIBs required for Monitoring: (Load in the following order) CISCO-UNIFIED-COMPUTING-MIB.my CISCO-UNIFIED-COMPUTING-TC-MIB.my CISCO-UNIFIED-COMPUTING-FAULT-MIB.my CISCO-UNIFIED-COMPUTING-NOTIFS-MIB.myTraps defined in the NOTIFS-MIB:cucsFaultActiveNotif: This notification is generated by a Cisco UCS instance whenever a fault is raised.The OID that corresponds to this SNMP trap is .1.3.6.1.4.1.9.9.719.0.1.cucsFaultClearNotif: This notification is generated by a Cisco UCS instance whenever a fault is cleared.The OID that corresponds to this SNMP trap is .1.3.6.1.4.1.9.9.719.0.2.A complete list of Standalone C-Series MIBs are available for download /ucs-C-supportlist.htmlThe Standalone C-Series MIB Reference Guide is available here: (Complete Detail)http://www.cisco.com/en/US/docs/unified computing/ucs/sw/mib/c-series/b UCS Standalone CSeries MIBRef.pdfSection #4: Setting up iReasoning MIB Browser:iReasoning is an intuitive, easy to use MIB Browser and trap receivers that allows administrators toquery systems and receive traps without a lot of setup work. iReasoning comes in three variants(Personal Edition, Professional Edition and Enterprise Edition) and can be downloaded from theirwebsite here: http://ireasoning.com/mibbrowser.shtmliReasoning allows customers to load their own MIBs, including MIBs downloaded from the Cisco sitelinked above. iReasoning can be used to issue SNMP requests that retrieve data from target systems orit can act as a trap receiver and present data received from initiator systems.This Document Contains Cisco Public Information
Major features highlighted by iReasoning: Intuitive GUIComplete SNMPv1, v2c and v3 (USM and VACM) supportComplete SNMPv3 USM support, including HMAC-MD5, HMAC-SHA, CBC-DES, CFB128-AES-128, CFB128AES-192, CFB128-AES-256 (128-bit, 192-bit and 256-bit AES) algorithmsRobust and powerful SMIv1/SMIv2 MIB parserIPv6 supportTrap ReceiverTrap SenderLog window to display application log and SNMP packets exchanged between browser and agentsTable view for MIB tablesSNMPv3 USM user management (usmUserTable in SNMP-USER-BASED-SM-MIB)Performance graph tool for monitoring of numerical OID valuesPing and traceroute toolsSNMP Agents ComparisonNetwork discovery toolRuns on Windows, Mac OS X, Linux and other UNIX platformsHow to use iReasoning MIB Browser to communicate with UCSM:iReasoning MIB Browser should be downloaded from the iReasoning website and installed on a systemthat can communicate with target systems that will be monitored. Required MIBs can be downloadedfrom Cisco and loaded into iReasoning using the ‘File Load MIBs’ Window.SNMP should be enabled and configured on the Cisco C-Series systems as outlined in Section #2 of thisdocument using the IP of the system where iReasoning has been installed as the Destination IP in theCisco IMC.How to Browse MIB Tables and Query target system using iReaonsing:Launch MIB Browser Window by using Start - Programs - iReasoning - MIB Browser - MIB Browser1. After launching the application, you need to specify IP address of the C-Series node on which SNMPoperations need to be performed in the address field of iReasoning.2. Click on ‘Advanced ’ Properties Button to configure SNMP parameters of the node – SNMP Readcommunity and version. The port number is always fixed to 161.3. Specify OID in the OID – A Cisco OID follows the following syntax: .1.3.6.1.4.1.9.9.719.x.x.x.Use different operations in the MIB Browser to perform SNMP get, get next and get bulk.If you have provided a valid OID correctly, the MIB Browser will fetch the current value of this OID usingan SNMP Get. A MIB Tree can be walked using ‘Get Next’, ‘Get Bulk’, ‘Get Subtree’ and other optionsprovided in the dropdown box. These options provide a good solution if the OID of the target object youwould like to query is unknown.This Document Contains Cisco Public Information
SNMP walk will fetch all OIDs with their current value in the target system. (Refer the provided picturesbelow)SNMP Get Bulk can be used to collect the data from a specified MIB table and current OID and propertyvalues are returned.This Document Contains Cisco Public Information
iReasoning can also be used as a trap receiver to capture traps that are sent from the Cisco IMC. Tostart the Trap Receiver select ‘Tools Trap Receiver’ and Click the green ‘Start’ button.Traps will be displayed in the main screen with VarBind data populated in the bottom window. See thegraphic above for a reference to a fault received using the iReasoning Trap Receiver.This Document Contains Cisco Public Information
Section #3: Cisco Standalone C-Series MIB Overview: Cisco UCS MIB files are a set of objects that are private extensions to the IETF standard MIB II. If your NMS cannot get requested information from a Standalone C-Series server or Cisco UCS, then the MIB that allows that specific data collection might be missing.
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unified Computing System (Cisco UCS), Cisco UCS B-Series Blade Servers, Cisco UCS C-Series Rack Servers, Cisco UCS S-Series Storage Servers, Cisco UCS Manager, Cisco UCS
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
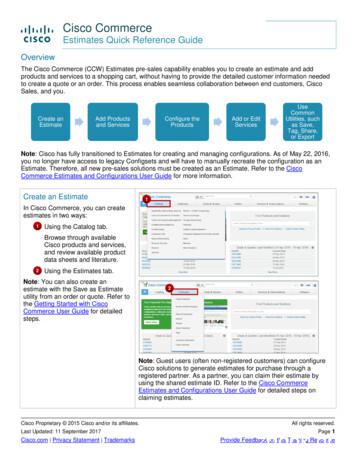
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base