DISASTER 101 - Zerto
Why You NeedDisaster RecoveryMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryREQUEST A DEMODISASTERRECOVERY101Everything You Always Wanted toKnow—But Were Afraid to Ask
Why You NeedDisaster RecoveryMeasuring DowntimeComparing Technologies1WHY YOU NEEDDISASTER RECOVERYDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster RecoveryDISASTERRECOVERY 101Measuring DowntimeComparing TechnologiesDisaster Recovery at ScaleConfused about RTOs and RPOs? Fuzzyabout failover and failback? Wonderingabout the advantages of continuous dataprotection over snapshots? This eBookwill help you learn about disaster recovery(DR) from the ground up so you can makeinformed decisions and implement aneffective DR strategy. We’ll show you howthat DR strategy can be one key part inbuilding a resilient IT infrastructure—thebackbone of successful digital businessesand always-on customer experiences.Why Do You Need DR?No one is immune to disruptions, malicious attacks, and unrecoverable data91%91%91% have experienced a tech-relatedbusiness disruption in the past 2 years91% have experienced some type ofbusiness disruption (variety of factors)84%56%84% have experienced a maliciousattack in the past 12 months (that theyknow about)56% have experienced unrecoverabledata within the last 3 years (up from49% last year)Total Cost of OwnershipThe Future of Disaster RecoveryREQUEST A DEMOSource: IDC State of IT Resilience ReportNEXT
Why You NeedDisaster RecoveryTHE COST OFDOWNTIMEMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipModern businesses cannot afford to losedata. Customers & stakeholders, bothinternal and external, expect seamless24/7 access to their data and applications.Whatever the cause—natural disaster,human error, or cyberattack—downtimeand data loss are costly and can beextremely risky to the life of a business.Every enterprise, no matter the industry,needs a cutting-edge disaster recoverystrategy to ensure uptime, minimizedata loss, and maximize productivity nomatter what kind of disruption or outagecomes along.Disruptions cost a business even whenit’s not tier 1 or critical applications thathave an outage. And it’s important to keepin mind that the cost of downtime is notonly impacted by revenue-generating VMs,or those directly involved in creating orprocessing sales. Consider indirect impactas well: Brand damage, either for the IT divisionor the business as a whole Loss of productivity; for example, whenemail, file servers, or the CRM goes down Time spent during and after an incidenton analysis, communication, or reporting 250,000/hrAverage cost of downtime perhour across all industries andorganizational sizes 2,000,000/yrThe collective cost of 8 hoursof downtime per year to anorganizationThe Future of Disaster RecoveryREQUEST A DEMOSource: IDC State of IT Resilience ReportNEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryIT’S ABOUTMORE THANJUST DISASTERSA rock-solid disaster recovery strategy isnot limited to traditional disasters either.Organizations regularly contend withthe need for operational recovery too.Operational recovery deals with the dayto-day realities of accidental deletions,overwritten files, or corrupted folders.Straddling the line between operationalrecovery and disaster recovery are thepotentially crippling effects of viruses,worms, and malware of all types. Notably,ransomware has become a particularlythorny problem for enterprises. Accordingto Cybersecurity Ventures, the global costof ransomware is predicted to reach 11.5billion in 2019. This malicious softwaregains access to files, often via unsecuredRDP, then encrypts the data and generatesa pair of private-public keys. The hackerholds the private key, and without itthe data is impossible to decrypt untilthe ransom is paid (usually in Bitcoin).Sometimes, even after a company pays theransom, the attackers never provide thedecryption key leaving victims without theirmoney or their files.Recent advancements in encryptiontechnologies, coupled with the ease withwhich hackers can conceal their identities,has resulted in an increased adoption ofransomware strategies.What Would DowntimeCost You?Try our Downtime Calculatoror contact Zerto for an in-depthconsultation.Calculatenow CALCULATE NOWREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing Technologies2MEASURINGDOWNTIMEDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipINTRODUCINGRTO & RPORecovery Point Objective (RPO) is the lastpoint in time IT systems and applicationscan be recovered to. It indicates theamount of data that will be lost, measuredin elapsed time. The cost of ONE HOUR of lost data formost enterprises can easily hit six figures,which is one reason organizations of allsizes are reconsidering whether nightlybackups (with an RPO of 24 hours) arestill sufficient in today’s demandingbusiness environments Due to the RPO’s importance on dataloss, it is recommended to agree on anacceptable, achievable RPO on a perapplication basis.The Future of Disaster Recovery Always aim for the lowest RPO possible,then configure alerts to warn if you are indanger of the actual RPO exceeding yourdefined SLA. Ensure that your solutionenables the prioritization of individualapplications should the bandwidth forreplication become constrained.Recovery Time Objective (RTO) is thetime that it takes to recover data andapplications, meaning, how long will itbe until business operations are back tonormal after an outage or interruption. The cost of downtime associated withwaiting for applications and data to berecovered (RTO) can result in significantloss in revenue and productivity.DAILYBACKUPSRPO 24 HoursUP TO 273,972.60 *SNAPSHOT-BASEDREPLICATIONRPO HoursUP TO 45,662.10 *CONTINUOUSREPLICATIONRPO SecondsUP TO 7,610.35 *REQUEST A DEMO*Example: Organization with a turnover of 100MNEXT
Why You NeedDisaster RecoveryPROVE YOURDR WORKSMeasuring DowntimeIn order to benchmark your RTOand tweak your DR plan to minimizedowntime, testing is a must. By testingyour plan with a DR technology thatallows for no downtime in productionor break in the replication, you canperform a test during working hours.This ensure you are able to fullyrecover, and you can run through therecovery operation multiple times toget your RTO as low as possible.Recovery Report for Virtual Protection GroupProduction 3Report was generated on 09/14/2019 12:02:29Recovery Operation DetailsComparing TechnologiesInitiated bySystemRecovery operationFailover TestPoint-in-time09/14/2019 11:46:17Recovery operation Start Time09/14/201915:46:30Recovery operation End Time09/14/201916:01:07RTO00:07:43Recovery operation resultPassed by userUser NotesStop Test for VPG Production 3Virtual Protection Group Recovery SettingsDisaster Recovery at ScaleTotal Cost of OwnershipProtected SiteProductionRecovery SiteCulpeper ProdDefault recovery hostProd 1Default recovery datastoreDSXtremCP6Journal datastoreDRJOURNAL01Default test recovery networkZerto TestNetDefault recovery folderDRDetailed Recovery Steps#Step Description1.Fail-over test VM ‘c3putdmo2212d1’End TimeExecuti11:46:4200:00:09Create Recovery VM ‘c3putdmo2212db1’- testing nfigure IP for VM ‘c3putdmo2212db1’- testing 1:46:4211:46:5000:00:08Create Recovery VM ‘c3putdcts1’’- testing ure IP for VM ‘c3putdcts1’ testing 1:46:4211:46:5000:00:0716.1REQUEST A DEMOStart11:46:321.1.16.The Future of Disaster RecoveryResultSuccess16.219.Fail-over test VM ‘c3putdcts1’Fail-over test VM ‘c3pitdga2122ap1’19.1Create Recovery VM ‘c3pitdga2122ap1- testing nfigure IP for VM ‘c3pitdga2122ap1’- testing over test CM 0725.Fail-over test VMs’ ‘c3putdmo2212db1’ volumesSuccess11:47:1911:48:0600:00:4625.1Create scratch volume for VM 2425.2Detach volume VMs’ ‘c3putdmo2212db1-0:1:’ fromSuccess11:47:4711:47:5600:00:0827.1Attach volume VMs’ ‘c3putdmo2212db1-0:1:’ toSuccess11:47:5411:48:0200:00:08This is an actual successful failover test from a healthcare organization using Zerto Virtual Replication. The testwas completed during a regular work day, with zero productionimpact.This failover test covers the organization’s tier one healthcareapplications, consisting of 23 VMs with 8.3 TB of data, and tookless than 15 min, with no downtime.Note: Some data points in this report have been redacted toprotect customer confidentiality.NEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing Technologies3COMPARINGTECHNOLOGIESDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster Recovery5 REPLICATIONTYPESMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipArray-Based ReplicationSometimes called storage-basedreplication, these solutions are deployedinside the storage array and replicatethe entire LUN, regardless of its utilizedcapacity. They are designed for physicalrather than virtual infrastructuresand, as such, eliminate the benefits ofvirtualization.There are two types of replication that canbe deployed.RPO 0RPO 1hrSynchronousAsynchronous12Ensures all data is written to the source andtarget storage simultaneously, waiting foracknowledgment from both arrays beforecompleting the operation. This relies onmatching storage arrays and close geographicproximity between sites to achieve low fiberchannel latencies and minimize performanceimpact. With the rise of all-flash arrays (AFA),latency of the connection between arraysbecomes a bottleneck. Synchronous replicationalso runs the risk of quickly propagating malwareand thus dramatically extending recovery times.Uses storage snapshots to take a point-in-timecopy of the data that has changed and sends itto the recovery site. The frequency is typicallyset on a schedule of hours, depending on thenumber and frequency of snapshots that thestorage and application can withstand.The Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster Recovery5 REPLICATIONTYPES (CONT’D)Measuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryRPO 1hrRPO 1hrRPO secsVM Snapshotbased 3Guest-basedHypervisorbased 5Uses VM-level snapshots to take a point-in-timecopy of the data that has changed and sends itto the recovery site. The snapshots are created inthe hypervisor and incur performance impact. Itis not recommended to create, remove or leaveVM-level snapshots running on production VMsduring working hours.Otherwise known as agent- or OS-basedreplication, these are software components thatmust be installed on each physical and virtualserver. Although more portable than array-basedsolutions, the requirement to install modules onevery server limits scalability and is limited toonly certain operating systems.When VM-level snapshots are being used the onlytype of supported replication is asynchronous.The frequency of replication is typicallyscheduled to occur every few hours due to theperformance impact of this type of technology.Guest-based replication typically only supportasynchronous replication. As it runs on theoperating system of the production systemsitself, it can impact the performance of thesesystems.4With these solutions, all writes are captured,cloned, and sent to the recovery site at thehypervisor layer, making it more efficient,accurate, and responsive than prior methods.Hypervisor-based replication uses continuousdata protection (CDP) and is constantlyreplicating only the changed data to therecovery site within seconds— it’s always on.This technology thus combines the best of bothsynchronous and asynchronous replication. Itdoes not need to be scheduled, does not usesnapshots, and writes to the source storagewithout having to wait for acknowledgment fromthe target storage.LEARN MOREREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMeasuring DowntimePERIODIC VERSUSCONTINUOUSBACKUPSnapshotsComparing TechnologiesDisaster Recovery at ScaleWhen using any kind of snapshot (whetherVM-level or storage-level technology), thereplication occurs on a schedule. Thisresults in the potential for more data loss incase of a disaster.This periodic approach also impacts thegranularity in recovery as checkpoints willonly be generated every few hours.Total Cost of Ownership4 hoursCORRUPTION3:43PM24 tSnapshotIf we take the above example of a data corruption at 15:43, then a VM-level 24-hour snapshot-based replication solution means you are going to potentially have nearly 16 hours of data loss, as you would have to restore a replicated snapshot from last night. The same examplewith storage-level snapshots would result in data loss of nearly 4 hours.The Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryContinuous DataProtectionContinuous data protection (CDP) utilizeschanged block tracking at the hypervisorlayer to constantly replicate data as it iswritten to storage. Because CDP replicatesonly changed information, rather than animage of the entire host or array, thereis no impact to the performance of thereplicated VM.Hypervisor-based CDP also utilizesjournal technology to keep a log of all thechanges occurring in a specified journaltimeframe, allowing point-in-time recoveryin increments of just seconds for the lengthof the journal.Easy Recovery toAny Point In TimeCHECKPOINT3:40PM4 hoursCORRUPTION3:43PM24 tSnapshotBecause CDP is always on and alwaysreplicating the most recently changed data,it offers considerably lower RPOs thansnapshot-based solutions. This results insignificantly less data loss to the businessand consequently, a far lower cost ofimpact.REQUEST A DEMONEXT
Why You NeedDisaster RecoveryTHE ROLE OFCDP IN BACKUPMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipBackup typically uses snapshot-basedtechnology to protect virtual environments.Because the data that is backed up is readdirectly from production systems, backupsare almost always run at night to avoid“VM stun,” or any kind of application lag orslowdown.When an environment is protected by CDP,you can recover data from seconds ago onproduction grade systems within only a fewminutes. Besides that, the recovery site canalso be used as a source for longer termbackups. This completely eliminates theconcept of backup windows.SNAPSHOTSVSCDPStoring multiple snapshots on replica VMs incursa significant VM performance penalty if youattempt to power on the replica VM.With journal-based protection, the journal isonly used until you commit to the point-in-timeselected, without the performance impact ofmany snapshots.Using snapshots on replicated VMs allows noway of controlling the total space used forsnapshots, or the ability to store the data changeon a separate datastore. This makes it unscalablein terms of being able to set SLAs and definemaximum limits on the data space used by thesnapshots.With journal-based protection, you can place thejournal on any datastore and place maximum sizelimits and warnings; so as not to fill the datastore,which could otherwise break replication andrecovery.With snapshot-based replication, there is oftensignificant overhead on the storage arrays forreplication reserves; which can be 20-30% onboth source and target storage in many cases.With journaling technology, no extra space isused in the source storage as no snapshots arecreated. Only 7-10% of the target storage istypically used for the changed data, freeing upsignificant amounts of disk space.DOWNLOAD THE WHITE PAPERThe Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing Technologies4DISASTER RECOVERYAT SCALEDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryBUILT-INAUTOMATION &ORCHESTRATIONThe top hypervisor-based replicationsolutions include replication, recoveryautomation, and orchestration all-in-one.The VMs that form each application arerecovered together in consistency groupsfrom the same point-in-time. Boot-orderingis then applied to ensure that the VMs comeonline in the correct order, and re-IP orMAC addressing can be utilized if needed toensure there is no break in communication.This ensures an RTO of just minutes withno manual operations required since theapplication is automatically recovered in aworking and consistent state.No-impact failover testing also enablesthis automated process to be testedduring working hours in minutes, withno shutdown in production or break inreplication. Reports can be generated toshow the testing outcomes and provethe recovery capability. This enablesorganizations to increase the frequencyof DR testing, mitigate risk, and satisfycompliance initiatives.ANALYTICSOrchestration & Continuous Data ProtectionREQUEST A DEMONEXT
Why You NeedDisaster RecoveryAPIs ANDSCRIPTINGMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipAlthough you’ll want to avoid solutions thatare overly dependent on scripting—whichwill inhibit efficient scaling, even withprofessional services—it’s inevitable thatenterprise-scale deployments will needopen, REST APIs. The platforms that havean API-first approach (potentially usingsomething like Swagger or Postman) willallow a business virtually unlimited ways ofintegrating systems together for effective,automated DR.VISIT ZERTO ON GITHUBThe Future of Disaster RecoveryREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMULTI-SITEMANAGEMENTMeasuring DowntimeComparing TechnologiesDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster RecoveryAs a business grows, typically so does itsneed to run multiple datacenters, andthey’re often geographically diverse andpotentially using disparate hardware& vendors. A modern DR strategy mustaccount for all the various sites and cloudsbeing utilized, no matter where they’relocated, what hypervisor they’re on, or howbig the environments.Part of effective management will includerole-based access control (RBAC), butit’s also important to have a single paneof glass that provides a window intoeverything the organization is running.A multi-site management platform canshow IT teams at a glance what the stateof their protection coverage is, as well ashighlight any critical issues that need to beaddressed. Dynamic analytics, especially ifit includes forecasting or modeling, can beespecially useful in seeing exactly how yourinfrastructure is performing (e.g. in terms ofstorage or bandwidth consumed) as well asplan for future growth.On-PremisZerto CSPAzureAWSIBM CloudREQUEST A DEMONEXT
Why You NeedDisaster RecoveryMeasuring DowntimeComparing Technologies5TOTAL COST OFOWNERSHIPDisaster Recovery at ScaleTotal Cost of OwnershipThe Future of Disaster R
Disaster Recovery at Scale Why You Need Disaster Recovery Total Cost of Ownership The Future of Disaster Recovery REQUEST A DEMO Recovery Point Objective (RPO) is the last point in time IT systems and applications can be recovered to. It indicates the amount of data that will be lost, measured in elapsed time. The cost of ONE HOUR of lost .
Verkehrszeichen in Deutschland 05 101 Gefahrstelle 101-10* Flugbetrieb 101-11* Fußgängerüberweg 101-12* Viehtrieb, Tiere 101-15* Steinschlag 101-51* Schnee- oder Eisglätte 101-52* Splitt, Schotter 101-53* Ufer 101-54* Unzureichendes Lichtraumprofil 101-55* Bewegliche Brücke 102 Kreuzung oder Einmündung mit Vorfahrt von rechts 103 Kurve (rechts) 105 Doppelkurve (zunächst rechts)
Strategy for Disaster Reduction. An alignment of the terminology used in disaster risk reduction in Africa with the internationally acceptable concepts is logical. 2.1 Disaster Although the focus of disaster reduction is not on any actual disaster event itself, disaster remains the main focus. Thus our efforts must be geared towards the
namely Disaster and its classification, Disaster risk and Disaster Risk Reduction, Mainstreaming gender for Disaster Risk Reduction. IV. DISASTER AND ITS CLASSIFICATION Disaster is a phenomenon which can identify from the history of human civilization and it can be simply defined as an event
There are three important phases in hospital emergency disaster management plan 1) Pre-disaster phase 2) Disaster Phase 3) Post Disaster Phase Pre-Disaster Phase a) Planning: Most of the assessment and planning is done in the pre-disaster phase, the hospital plans are formulated and then discussed in a suitable forum for approval. b) Preparation
1. Post-Disaster Recovery and Disaster Risk Reduction require support from community participation in improving the quality and objectives of Disaster Management; 2. Community-based Disaster Risk Reduction is a key factor in participatory disaster management, including in post-disaster recovery, as indicated by best practices in Yogyakarta and .
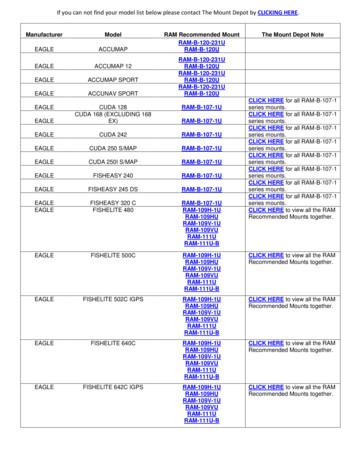
FISHFINDER 340C : RAM-101-G2U RAM-B-101-G2U . RAM-101-G2U most popular. Manufacturer Model RAM Recommended Mount The Mount Depot Note . GARMIN FISHFINDER 400C . RAM-101-G2U RAM-B-101-G2U . RAM-101-G2U most popular. GARMIN FISHFINDER 80 . RAM-101-G2U RAM-B-101-G2U . RAM-101-
UOB Plaza 1 Victoria Theatre and Victoria Concert Hall Jewel @ Buangkok . Floral Spring @ Yishun Golden Carnation Hedges Park One Balmoral 100 100 100 100 100 100 100 100 100 100 100 100 100 100 100 101 101 101 101 101 101 101 101 101. BCA GREEN MARK AWARD FOR BUILDINGS Punggol Parcvista . Mr Russell Cole aruP singaPorE PtE ltd Mr Tay Leng .
Agile methods in SWEP Scrum (mainly) XP Head First Software Development Process The Scrum process follows the agile manifesto is intended for groups of 7 consists of simple rules and is thus easy to learn 15.04.2012 Andreas Schroeder 9