Building Trustworthy Systems With Cisco Secure Development .
Building Trustworthy Systems withCisco Secure Development LifecycleJanuary 2016
Foundation of TrustProcessTechnologyPolicySecure ProcessTrustworthy Systems TechnologySecure StandardsLifecycle/Security BaselineCommon Modules and HardwareInformation Assurance (IA)PerformGAPAnalysisRegister andValidateUpdate ThirdRequirementsand ResiliencyParty SoftwareDetectSecurityDefectsVisibility and ControlISO 27034Identify andAddressSecurityPrevent ThreatsSecurityAttacksSecure CommunicationsFIPS/USGv6Platform IntegrityTCGCSDLPreventionDetectionRecovery
Cisco Secure Development LifecyclePerformGAPAnalysisRegister andUpdate ThirdParty SoftwareValidateRequirementsand cksIdentify andAddressSecurityThreatsEnsures consistent productsecurity through proventechniques and technologies,reducing the number and severityof vulnerabilities in softwareConforms with the guidelinesof ISO 27034
Product Security Baseline (PSB)Gap AnalysisPSB ArchitectureAdministrative Access SecurityLogging and AuditingApplication SecurityOperational ProcessAuthentication and AuthorizationBoot and System IntegrityPrivacy and Data SecuritySession ManagementCryptographic SupportThreat Surface ReductionDevelopment ProcessTraffic and Protocol ProtectionHosted Services HardeningVulnerability ManagementWeb Security
Third Party SoftwareFundamentalsMinimize exposure by Perform gap analysis Establish maintenance plan Verify no backdoors Address all known vulnerabilities before FCSManages third party security alerts Register components with in a centralized database Contract support for critical security fixesPlanned response to security issues Follow established maintenance plan
Secure DesignThreat ModelingFocus on how a feature can be attacked andhow best to mitigate the attack
Secure Coding Boot Time Integritywith Run Time Defenses ASLR X-Space OSC “Safe” libraries Input validation Best Practices Guidelines for each OS Signed Images
Static Analysis Security Checkers find key vulnerability types Buffer overflow Tainted input Integer overflow Maximizes efficacy and reduce false positives
Vulnerability TestingCheck Protocol RobustnessDuplicate Hacker AttacksCSDL Security TestingNetwork Device TestingCodenomiconProtocol RobustnessTest Suites for 50 Protocols, including:DNS, H.323, IKEv2,IPv4, IPv6, HTTP, SIP,SNMP, SSH, TLS andmany moreOpen Source“Hacker” Tools20 Open Sourcesecurity tools,including: Amap, Curl,Dsniff, Hydra, Naptha,Nessus, Nikto, Nmap,Xprobe and many moreApplication TestingIBM Rational AppScanFamily of applicationattack and test tools,including: risk analysis,security standardcompliance testing,vulnerability scan andmany more
ISO 27034 & CSDLISO 27034 ISO 27034 is the standard for “Information Technology – SecurityTechniques – Application Security” Addresses Security Lifecycle for development and deployment Aligns with existing international, national, and industry standards Section 1 is adopted, sections 2-6 (implementation details) still indraftCSDL conforms with the guidelines of ISO 27034 Following CSDL is part of Cisco’s ISO compliance In 2013, Cisco used ISO/IEC 27034-1, as a baseline to evaluateCSDL. “All current mandatory application security related policies, standards, andprocedures along with their supporting people, processes, and tools meet orexceed the guidance in ISO/IEC 27034-1 as published in 2011.”With Cisco’s CSDL processes, policies and technologies applied throughout the design and development phases,customers have a strong secured focused foundations on which to build their secured infrastructures.10
Security is Everyone’s JobAccelerating to A Security Aware CultureEstablished ngLearning11
Cisco Security and Trust Spectrum“Cradle to Grave”CloudEnterprise SecurityPrivacy and Data ProtectionSecurity and Trust Built InDesignEngineeringManufacturingDelivery /DeploymentOngoingOperation
Thank you.
ISO 27034 is the standard for “Information Technology –Security Techniques –Application Security” Addresses Security Lifecycle for development and deployment Aligns with existing international, national, and industry standards Section 1 is adopted, sections 2-6 (implementation details) still in draft CSDL conforms with the guidelines of ISO 27034 Following CSDL is .
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unified Computing System (Cisco UCS), Cisco UCS B-Series Blade Servers, Cisco UCS C-Series Rack Servers, Cisco UCS S-Series Storage Servers, Cisco UCS Manager, Cisco UCS
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
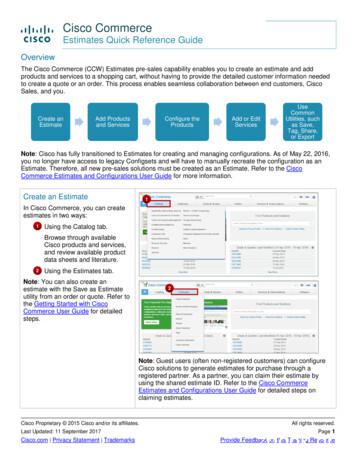
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base