Lockbox Secure Technology - CAP’TRONIC
The World Leader in High Performance Signal Processing SolutionsLockbox Secure Technologyon Blackfin ProcessorsR.SALVETAT
Agenda Generalsecurity overview Lockbox overview: DigitalSignature (ECDSA) in Blackfin Lockbox programming interface Modifying VisualDSP linker files (LDF) for Lockbox Developing practical Lockbox applications using overlays. Hands-on Qsecurity example&A Course Viewprerequisites:BOLD Lockbox Module on web st.html#ADEV021) Basic understanding of security concepts and overlays is recommendedbut not required2
Lockbox Secure Technology BenefitsConfidentialityCryptographic encryption/decryption supports situations that require theability to prevent unauthorized users from seeing and using designatedfiles and streams.Lockbox’s secure processing environment (Secure Mode) and securememory support confidentiality.IntegrityDevelopers can use a digital signature authentication process to ensurethat the message or the content of the storage media has not beenaltered in any way. Integrity can be verified using Lockbox’s authenticationof digital signatures.Authenticity/Origin verificationLockbox secure technology allows for verification of a code image againstits embedded digital signature, and provides for a process to identifyentities and data origins.3
Confidentiality – Symmetric Ciphers (AES, ret key4SensitiveDataSecret key
Integrity – Hash (SHA-1, SHA-256, SHA-512)100100101100100101Compute Hash at time A5Compute Hash at time B
Authenticity – Digital Signatures (RSA, ECDSA)Sign a document using aprivate key that is unique toyou (your hand writing)6Your signature is verified using apublic key that is known to anyone(your reference signature)
The World Leader in High Performance Signal Processing SolutionsLockbox Overview
Lockbox Introduction Lockboxenables security by providing a privileged (secure) modeof operation in which only trusted code is allowed to execute. Lockbox performs digital signature authenticationFor an application to establish trust and to reach the privileged mode ofoperation, it has to undergo a digital signature authentication as specifiedin ANSI X9.62 (ECDSA). The digital signature authentication process is carried out by firmwarestored in on-chip ROM. Lockbox The secure processing environment supports execution of sensitive codeand can safeguard the execution of an encryption/decryption algorithm aswell as the decrypted ‘message’ when stored in protected on-chipmemory. Security8DOES NOT perform encryption or decryptionfeatures are completely optional
Security Feature HighlightsOTP memory for storage of customer programmable cipher keys, uniquechip ID or a customer ID OTP write protection to protect programmed OTP memory locations fromfuture tampering Private/Secret OTP memory region accessible only in Secure Mode Store private key(s) for decryption of data or other validationProtection of L1 and on-chip L2 regions of memory with access controlledwhen in Secure Mode. These memory areas are configurable in size and can protect sensitive data fromany DMA access.A secure mode of operation to perform sensitive decryption or execution ofcode “Secured switches” to disable all avenues of attack in support of a securedenvironment Disable DMA access to L1 and on-chip L2 memoryDisable ADI JTAG emulation from ICE portDivert hardware reset to NMIA suitable mode (including on chip ROM) to perform code authentication9
Blackfin enhancements for securityList of new hardware features One Time Programmable memory (64Kx1 bits) Public OTP memory (4 KBytes) Private (secret) OTP memory (4 KBytes) Open Mode (Unsecured) Default power up mode of the ProcessorSecure Entry Mode Ensures integrity of authentication processSecure Mode Secure environment to execute sensitive code and protect data in on-chip memoryHardware Monitor Used to store the authentication software (Secure Entry Service Routine, crypto)Secure State Machine Can be used to prevent cloning of products (bind software -in a flash memory- to a singleProcessor)Secure ROM Used to keep secrets only accessible in Secure Mode (example: secret keys for a cipher)Unique Chip ID (stored in Public OTP memory) Used to keep a trusted Public Key for proper authenticationFirmware execution is monitored for unexpected branchesSystem switches (SECURE SYSSWT) 10Controls secure environment and prevents attacks using JTAG, reset pin or DMAmemory accesses
Secure State MachineSecure State Machine Modes of operation OpenMode (Unsecured)Default mode of processor upon power up/reset/boot All secured system switches are deactivated. OTP memory secrets are protected from access. The chip is open, all features are available with no restrictions. SecureEntry Mode (Authentication)Firmware is executing out of internal memory to authenticate a loadedcode image All secured system switches are activated. SecureModeOnce authentication process results in success, device is in Secure Mode Mode of operation to perform sensitive decryption or execution of code OTP memory secrets are accessible. Secured system switches are accessible to user (authenticated) code 11
Secure State MachineOPEN MODEAUTHENTICATION FAILURESECURE ENTRY MODESECURE MODE12POWER-UPORRESET
Using Security FeaturesTo make use of Blackfin's Secure Lockbox Technology, it isnecessary to do the following: 1.2.3.4.13Generate a key pairProgram the public key in Blackfin's OTP memory(Personalization)Sign the application that will run in secure mode using theprivate keyRequest Authentication
Generate a Key Pair AnECC key pair consists of a Public key and a Private key ThePublic Key is stored on the Blackfin itself and is used forverifying (authenticating) digital signatures on the Blackfin The Private Key is retained by the developer and kept confidentialand is used for digitally signing messages off chip. Developersare responsible for key management, i.e.,generating keys and programming the public key onto theprocessor as well as maintaining the confidentiality of theirprivate key.14
Public Key Programming (Personalization) PublicECC key must be programmed into specified areawithin public OTP memory in order to perform Authenticationand transition Secure State Machine through state flow. OTPpages 0x10, 0x11 and 0x12 hold the customer public key Developers are responsible for key management, i.e., generatingkeys and programming the public key onto the processor as wellas maintaining the confidentiality of their private key. OTPcan be programmed via JTAG or via loading andexecuting code on the Blackfin. Support for OTP programming by Device Programmervendors such as BP Microsystems and DataIO is currentlyunder development15
EZ-Kit Security Examples Autility is distributed with the VisualDSP 5.0 EZ-Kitexample code to sign the application that will run in securemode with publicly disclosed private key. WARNING:Please be aware that the digital signature utilityprovided is for demonstration purposes only. It is notsufficiently secure for practical purposes. Please do not usethe provided digital signature utility to generate digitalsignatures for application in your product. BF54xand BF52x EZ-Kits will ship from ADI with a public keypre-programmed in OTP and a published private key for usewith example code and to facilitate support of customerdevelopment16
Initiating Authentication Twoconditions must be met to initiate Authentication and start theSecure Entry Service Routine (SESR) (i.e. authentication firmware),First, the beginning address of the authentication firmware must beloaded into the NMI (EVT2) location of the event vector table. Second, the NMI interrupt must be triggered. For sequential operation,“raise 2;” is executed. Since“raise 2;” is only allowed in supervisor mode, the steps tostart authentication could be concealed in a system call. Thesystem call can also set up the environment necessary to start theauthentication. Specifically, it would set up the arguments and saveor move the contents in L1 or L2 memory. Since the authentication firmware assumes a specific memoryconfiguration before it begins, the system call also has theresponsibility to temporarily move any data out of L1 or L2 regionsused by the authentication firmware.17
iv.OTP4KBDDRSDRAM
shCoreL1DataSRAM64KBCCLKDomain19L3 32KBSecureEntry& BootROMPub.OTP4KBPriv.OTP4KBSDRAM
Lockbox programming interface SESRAPI ArgumentStructure Message/Signature Structure Error Return Codes Memory20Configuration
SESR Argument StructureThe following security firmware arguments are the argumentsaccepted by the secure entry service routine:/* SESR argument structure. Expected to reside at 0xFF900018*/typedef struct SESR args {unsigned short usFlags;unsigned short usIRQMask;unsigned longulMessageSize;unsigned longulSFEntryPoint;unsigned longulMessagePtr;unsigned longunsigned long} tSESR args;21ulReserved1;ulReserved2;/*/*/*/*/*security firmware flags */interrupt mask */message length in bytes */entry point of secure function */pointer to the buffer containingthe digital signature and message/* reserved *//* reserved */*/
Flags Argument (Detail)The usFlags argument is made up of the following bitfields:/* SESR flags argument ine22SESR FLAGS STAY AT NMISESR FLAGS DROP BELOW NMISESR FLAGS NO SF DMASESR FLAGS DMA SF TO RUN DESTSESR FLAGS USE ADI PUB KEYSESR FLAGS USE CUST PUB KEY0x00000x00010x00000x00020x00000x0100
Message/Signature StructureThe structure of the message:23 ------------------------------ Code to receive control from the security firmware (SESR) ------------------------------ Code or Data . ------------------------------
Memory Configuration for AuthenticationL1 Instr.Romsecfw entry:check if args are validget public key from OTPcall SHA1call ECDSAif(pass)move SF fromL1D to L1Cjump to SFif(fail)return with error code0xFF8000000xFF9000000xFF800030Message(Code and optionaldata content to beauthenticated,a.k.a. SF)SHA10xFF901F000xFEB00000Message(Code and optionaldata content to beauthenticated,a.k.a. SF)Data Content for SF(Optional)0xFF8040000xFEB10000Unprotected UserDataUnused AreaUnprotected UserDataUnused/ProtectedRead Only0xFF80800024Argument buffersforSF and SESRECC Data buffersand variables.(Reserved)Data variables andbuffers used byauthentication codeData Content for SF(Optional)ECDSAOTP ErrorCorrectionDigital SignatureL1 Data Bank A0xFF908000L1 Data BankB0xFEB20000L2 (BF54x Only)
Internal MemoryL1 Instr.Rom / BootRomsecfw entry:check if args are validget public key from OTPcall sha1call ecdsaif(pass)move SF fromL1D to L1Cjump to SFif(fail)return with error code0xFF800000Developer’s decryption algorithm will go hereDigital Signature0xFF900000Argument buffers forSF and SESRMessageDecrypt signature and(Code and optionalECC Data buffers andstore HASH into here.variables.data content to be(Reserved)authenticated,a.k.a. SF)Data variables andbuffers used byauthentication codeSHA1Data Content for SF(Optional)ECDSAOTP ErrorCorrection0xFF804000Data Content for SF(Optional)0xFF904000Unprotected UserDataUnused AreaUnprotected UserDataUnused/ProtectedRead OnlyL1 Instr. Bank AMessage(Code and optionaldata content to beauthenticated,a.k.a. SF)StartupCode0xFF80800025L1 Data Bank A0xFF908000L1 Data Bank BL2 (BF54x Only)
Memory Configuration for Authentication The message can either be placed within the protected area of L1A or L2 The digital signature is a pair of 163 bit integers. Each integer is padded to thenearest 32-bit word (resulting in 192 bits). Thus, the total size of the digital signatureis 384 bits.If the message is placed in L1A data memory, it must immediately follow the digitalsignature.Alternatively, the message can be placed anywhere in the secured region of L2memory.When the Secure State Machine enters into Secure Entry Mode (authentication),certain portions of memory are protected from DMA accesses. If the message (i.e. code) is put into L1A for authentication, it must be DMA’d to either L1 codespace or L2, where it can execute. If the message is placed into L2 for authentication, it canremain in L2 and be executed directly from L2These include 32KB of L1A and 8KB of L1B data memoryL1 instruction memory (32KB)Half of on-chip L2 memory (64KB on processors with L2).This means that the message/code that needs to be authenticated is 32KB less 48 bytes for thedigital signature, if placed in L1A data memory and 64KB less 48 bytes if placed in L2 memory.The arguments for both the SESR and the SF are stored in L1B data memorybeginning at top (0xff900000).8KB of L1B data memory is reserved for the firmware for scratch working space 26All memory above 0xff901f00 in L1B is reserved for authentication.
The World Leader in High Performance Signal Processing SolutionsLockbox Programming
Message Placement for BF52x ProcessorsAuthentication LocationRun LocationulMessagePtrSignatureSF EntryPointRest ofMessageL1 Data Bank A28ulMessagePtr 0x30SF EntryPointRest ofMessageL1 Code
Message Placement for BF54x ProcessorsAuthentication LocationRun LocationulMessagePtrSignatureSF EntryPointRest ofMessageL1 Data Bank A or L229ulMessagePtr 0x30SF EntryPointRest ofMessageL1 Code or L2
Message Placement – Deep ThoughtsHow do I deal with the message? During authentication, the message will be in on-chip datamemory In secure mode, the message will be in on-chip code memory(and possibly data memory as well) The message may not be a critical function that you want toreside in internal memory in the first placeThe answer is overlays30
Life Story of an Overlay – 1Source File XLDF FileSource File Y31xy.ovlWe specify overlay generation in the LDF: Take section xx from source file x Take section yy from source file y Call the output xy.ovl
Message Placement – Source Filesection("overlay live 1") void secure function(void){/* Enable JTAG */*pSECURE SYSSWT ( *pSECURE SYSSWT & ENABLE JTAG );ssync();log authentication results();led blink();return;}32
Message Placement – LDF File#define MEM MESSAGE OVL RUN MEM L1 CODE#define MEM MESSAGE OVL LIVE MEM L1 DATA Amessage overlays {ALIGN(4)OVERLAY INPUT {INPUT SECTION ALIGN(4)ALGORITHM(ALL FIT)OVERLAY OUTPUT( COMMAND LINE OUTPUT DIRECTORY\secure function.ovl )INPUT SECTIONS( "secure function.doj"(overlay live 1) )} MEM MESSAGE OVL LIVE} MEM MESSAGE OVL RUN33
Digital Signature Placement Inthe source file:section("L1 data a ds") u32digital signature in L1 data a[DS LEN WORDS]; Inthe LDF file:digital signature{FORCE CONTIGUITYINPUT SECTION ALIGN(4)INPUT SECTIONS( OBJECTS(L1 data a ds) )} MEM L1 DATA A34
Security Firmware Arguments & ScratchBuffer Requirements Thesecurity firmware expects its arguments to residetowards the beginning of L1 data bank B. (0xFF900018) It also expects to have free access to a scratch buffer of size0x1F00 immediately following the argument buffersL1 data bank B35FF900000- - - -FF900018- - - -FF900030- - - -FF901F30- - - - ------------------------------ ------------------------------ Security Firmware Arguments (24 bytes) ------------------------------ Scratch Buffer for Use by the Security Firmware (7936 bytes) ------------------------------
Security Firmware Arguments Placement Inthe source file:tSESR args security firmware args in L1 data b; Inthe LDF file:RESOLVE( security firmware args in L1 data b, 0xFF900018)36
Dealing with the Scratch Buffer Requirement –Overlay Style In the source file:section("overlay live 3") u8security firmware scratch in L1 data b[SCRATCH BUFFER SIZE - 4]; In the LDF file:scratch overlays {ALIGN(4)OVERLAY INPUT {INPUT SECTION ALIGN(4)ALGORITHM(ALL FIT)OVERLAY OUTPUT( COMMAND LINE OUTPUT DIRECTORY\secure scratch.ovl )INPUT SECTIONS( "secure function.doj"(overlay live 3) )} MEM SCRATCH OVL LIVE} MEM SCRATCH OVL RUN37
Life Story of an Overlay – 2 Linker adds a unique 4Byte overlay ID to thebeginning of each overlay Linker replaces all references to functions in anoverlay with a custom code (interceptor)OverlayManagerOverlay 1InterceptorOverlay 2Overlay “Run" Space(ex: internal memory)38Overlay "Live" Space(ex: external memory)
Interceptor (PLIT) – 1PLIT {[--SP] RETS;[--SP] (R7:0,P5:0);R0.L lo(PLIT SYMBOL OVERLAYID); // pass overlay ID to overlay managerR0.H hi(PLIT SYMBOL OVERLAYID);sp -12;CALL ( OverlayManager);sp 12;R0.L lo(PLIT SYMBOL OVERLAYID); // are we dealing w/a secure overlay?R0.H hi(PLIT SYMBOL OVERLAYID);R1 2;cc R0 R1;if !cc jump non secure overlay PLIT SYMBOL OVERLAYID;secure overlay PLIT SYMBOL OVERLAYID: non secure overlay PLIT SYMBOL OVERLAYID: }39
Interceptor (PLIT) – 2secure overlay PLIT SYMBOL OVERLAYID:// Load the firmware address into the NMI handler:P0.H (0xFFE02008 16);P0.L (0xFFE02008 & 0xFFFF);P1.H (0xEF001000 16);P1.L (0xEF001000 & 0xFFFF);[P0] P1;ssync;// restore state(R7:0,P5:0) [SP ];RETS [SP ];// Invoke SESRraise 2;// The stack is preserved accross SESRSP -4;P0 [SP ]; // re-read RETSjump (P0);40
Interceptor (PLIT) – 3non secure overlay PLIT SYMBOL OVERLAYID:// restore state(R7:0,P5:0) [SP ];RETS [SP ];P0.L lo(PLIT SYMBOL ADDRESS);P0.H hi(PLIT SYMBOL ADDRESS);// "call" to resolved symbolJUMP (P0);41
Overlay Manager – 1/* Element type for a data overlay linked list */typedef struct data overlay pointer struct {s32dataOvlIndex[DATA OVL INDEX SIZE];struct data overlay pointer struct*next;} t data ovl ptr struct;/* overlay table layout */typedef struct overlay struct {u32 liveAddress;u32 liveSize;u32 runAddress;u32 runSize;u32 flags;secure overlay */t data ovl ptr struct * dataOverlays;} t overlay struct;42/*/*/*/*/*RAM-based live addresses */live size */run address */run size */flag to indicate whether or not weare processing a/* pointer to a linked list ofrelated data overlays */
Overlay Manager – 2void OverlayManager(s32 requestID){requestIndex requestID - 1; // zero-based indexif ( DATA OVERLAY ! overlay table[requestIndex].flags ) {/* Bring in any associated data overlays */}/* For secure overlays, the overlay manager doesn't DMA the codeintorun space because the security firmware does it. */if ( SECURE OVERLAY overlay table[requestIndex].flags )return;/* Check is overlay is already loaded */if (residentID requestID)return;}/* DMA in the overlay code */ 43
Overlay Manager – 3 Ifthe overlay is a secure overlay, the overlay manager doesnot need to perform the DMA because the firmware code willmove the message from its authentication location to its runlocation. If the overlay is a secure overlay, the SESR (firmware) willrequire some scratch space. One way to implement this is toassociate a data overlay with the secure overlay. Every timethe overlay manager encounters a secure overlay, it checks tosee if any data in the scratch space needs to be saved beforeit loads in the secure overlay.44
Signing a Messagecmdcmdcmdcmdcmd/C echo Delete previous state/C del Debug\secure function.bin 1 nul 2 &1/C del Debug\secure function signature.txt 1 nul 2 &1/C echo Extract the overlay section/C (VDSP)\elfpatch.exe -get ov message overlays 1 -o Debug\secure function.binDebug\secure function.ovl(overlay1.elf)cmd /C echo sign the contents of the overlay sectioncmd /C cd .\Bin &&ecsign.exe .\ADSP-BF527 EZ-KIT Lite\elliptic curve parameters 527.ecs.\ADSP-BF527 EZ-KIT Lite\private key 527.ecs.\ADSP-BF527 EZ-KIT Lite\random number 527.ecs.\ADSP-BF527 EZ-KIT Lite\Debug\secure function.bin &&cd .\ADSP-BF527 EZ-Kit Litecmd /C echo Place the digital signature in the digital signature sectioncmd /C (VDSP)\elfpatch.exe -replace digital signature -bits Debug\secure function.bf-text Debug\lockbox 527.dxe45
The World Leader in High Performance Signal Processing SolutionsInstructor led demo
The World Leader in High Performance Signal Processing SolutionsResources & References
Resources & References http://www.rsasecurity.com/rsalabs/ http://www.certicom.com/index.php http://csrc.nist.gov/ l http://www.keylength.com/index.php http://www.schneier.com/index.html http://www.kilopass.com/e15/ Textbook 48references:Applied Cryptography: Protocols, Algorithms, and Source Code in C, SecondEdition, by Bruce Schneier, Wiley; 2 edition (October 19, 1995), ISBN: 0471128457Security Engineering: A Guide to Building Dependable Distributed Systems, byRoss Anderson, Wiley (January 22, 2001), ISBN: 0471389226Handbook of Applied Cryptography, by A. Menezes, P. van Oorschot, and S.Vanstone, CRC Press, 1996. For further information, seewww.cacr.math.uwaterloo.ca/hac
Cryptography Made Easy AnIllustrated Guide to Cryptographic o-hashes.html DigitalSignature /isc/dsg-tutorial.html Whatis a Digital Signature?http://www.youdzone.com/signature.html crypto/crypto-dict.html Wikipedia,the free encyclopediahttp://www.wikipedia.org/49
Glossary Asymmetric algorithm - A cryptographic algorithm which uses two different keys for encryption and Authentication - Verifying a code image against its embedded digital signature. Process for identifying Authentication Control Code - Firmware code stored in ROM to control Secure State Machine and decryption.either entities or data originshardware modes during the process of AuthenticationChip ID - Unique identification number per chip (stored in public OTP memory)Ciphertext - Encrypted messageCleartext - Unencrypted message (synonomous with ”plaintext”)Confidentiality - Cryptographic means to ensure privacy or secrecy of information from unauthorizedparties (so that only after authorized access, data can be read). Typically, confidentiality is ensured usingdata encryption via symmetric algorithms.Digest - Secure digital fingerprint, created by a one-way hashing functionDigital Certificate - A piece of information digitally signed by a trusted third party, or certificate authority(CA), that establishes a user’s credentials and identity. Typically consists of customer’s public key andcustomer ID signed by a certification authorityDigital Signature - A digitally signed hash result of the message. Any digest encrypted with a customer’sprivate keyElliptic Curve Cryptography [ECC] - A class of cryptosystems that are based on the difficulty of findingpoints on an elliptic curve over a field with special properties. Most often, the strength of ECC is providedby the discrete logarithm problem; however, the factoring problem can also be used.Integrity - Cryptographic means to ensure that the message or the content of the storage media has notbeen altered in any way. Integrity is verified using authentication.Key management - Refers to the distribution, authentication, and handling of keysNon-repudiation - Preventing an entity from denying previous commitments or actions50
Glossary Open Mode - Default operating mode of the processor in which nothing is restricted except for access toPrivate OTP memory.OTP - One Time Programmable memory. Customer-programmable via code executing on processorPlaintext - Unencrypted messagePrivate Key - Private (secret) part of asymmetric key used to create digital signaturesPrivate OTP - Customer-programmable OTP memory area for private (secret) key and sensitiveinformation storage. Accessible only in Secure Mode.Public Key - Public part of asymmetric key used to verify digital signaturesPublic OTP - Customer-programmable OTP memory area for public key and information storage.Accessible in all operating Modes including Open Mode, Secure Entry Mode and Secure Mode.Secret Key - Any symmetric secret key (e.g., download key, key encryption key (KEK))Secure Entry Mode - Secure operating mode in which firmware controls the authentication processSecure Mode - Secure operating mode allowing execution of authenticated code, decryption of sensitiveinformation, authenticated code access chip secrets in private OTP memory area, etc.Secure RAM - Configurable part of internal system RAM accessible only in Secure ModeSecurity Framework - Application code executed in RAM to pass parameters to Authentication ControlCode and invoke an Authentication RequestSymmetric Key algorithm - A cryptographic algorithm in which only one key is used to both encrypt anddecrypt data.References:Cryptography Dictionary ml)Wikipedia (http://www.wikipedia.org/)51
Acronyms AES- Advanced Encryption Standard specified in FIPS 197. ANSI - American National Standards Institute CA - Certification Authority DSA - Digital Signature Algorithm specified in FIPS 186-2. ECDSA - Elliptic Curve Digital Signature Algorithm FIPS - Federal Information Processing Standard. HMAC - Keyed-Hash Message Authentication Code spec’d in FIPS 198. IV - Initialization Vector. MAC - Message Authentication Code NIST - National Institute of Standards and Technology PKI - Public Key Infrastructure PRNG - Pseudorandom Number Generator RNG - Random Number Generator TDES - Triple Data Encryption Standard; Triple DES52
The World Leader in High Performance Signal Processing SolutionsQ&A
Lockbox’s secure processing environment (Secure Mode) and secure memory support confidentiality. . Lockbox secure technology allows for verification of a code image against its embedded digital signature, and provides for a process to identify . Protection of L1 and on-chip L2 regions of memory with access controlled
When you release the shackle, it will completely detach from the lockbox, so hold onto the lockbox to prevent it from falling to the ground. 3. Don't leave your SentriCard on your car's dashboard or any surface that could get hot enough to melt it, and don't bend it excessively. 4. Afte
Retail Lockbox Image Viewer Regions Commercial Banking—A Complete Solution Service Overview Regions Retail Lockbox Imaging Services has developed an enhanced Image Viewer to provide you with improved navigation to store and access images of your remittance checks and documents. The CD / DVD you receive contains a date range of captured
Cap. 1 Fondamenti di informatica e hardware Cap. 2 Il software Cap. 3 La rappresentazione dei dati per le scienze umane Cap. 4 Dalle reti a Internet Cap. 5 Il World Wide Web Parte II - Temi per le scienze umane Cap. 6 La computazione linguistica Cap. 7 Arte e beni culturali nell'era digitale Cap. 8 Biblioteconomia e ricerca delle informazioni .
347-Hubodometer hub cap with oil port. 348-Sentinel oil hub cap. 349-Sentinel grease hub cap. 352-Solid grease hub cap. Part No. Description 340-4009 Standard 6 hole hub cap without oil port. 340-4013 Standard 5 hole hub cap without oil port. 340-4019 Standard 3 hole hub cap without oil
Callan Periodic Table of Investment Returns Returns Ranked in Order of Performance (as of June 30, 2019) Equity Cap Large-9.11% Equity Cap Large-11.89% Equity Cap Large-22.10% Equity Cap Large 28.68% Equity Cap Large 10.88% Equity Cap Large 4.91% Equity Cap Large 15.79% Equity Cap Large
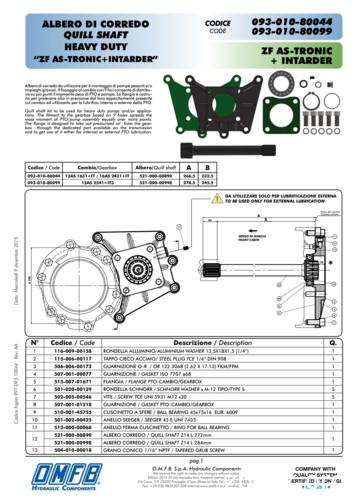
ZF AS-TRONIC INTARDER 093-010-80044 093-010-80099 180 266,5 34 232,5 16 5 2 12 11 10 9 4 3 6 7 8 1 Piano del cambio Gearbox surface SENSO DI MARCIA FRONT CABIN * DA UTILIZZARE SOLO PER LUBRIFICAZIONE ESTERNA TO BE USED ONLY FOR EXTERNAL LUBRICATION 13 B A N Codice / Code Descrizione / Description Q. 1 116-009-00158 RONDELLA ALLUMINIO .
Transmission 6-speed manual 7-speed S tronic 6-speed manual 7-speed S tronic 7-speed S tronic Acceleration (sec) 0-100km/h 5.4 4.8 5.4 4.8 5.3 . Inlays in matt brushed aluminium, illuminated design 5TV Interior Features Aluminium door sill trims with S logo Aluminium look interior elements including air vents, glove box, window switches .
Academic Phrasebank. Setting objectives –student tip “It is important that your chosen research question is clearly focused and well written; answering it must be achievable in the time available to you!” Your research question and the objectives to achieve it. Your research title Your dissertation title is important as it tells your reader what your dissertation is about ! Titles often .