16 0 Cisco IE RS Ver 4 / 5 - WordPress
Version 52/w/:phttithwdweeir!vatlisemiBrsodaan iPTraining and certificationCisco CCNA routing switching, Cisco CCNP routingswitching, Cisco CCNP RSCisco CCNP study flashcards, Cisco CCNP flashcardsEasy to understand CCNP / CCIE study flashcardsEffective CCNP trainingEffective CCIE trainingCisco Web learningOnline trainingRouting protocols, design, troubleshooting, howtoAs I was going through the entire CCIE training material and had found that I tend to forget some of the many details I had studied month earlier and had to comeConfiguration guidewith a solution on how to remember all the nibbly details and keep the learned fresh. This file contains over 1600 designs, config snippets, explanations ofSimple to understanduptechnologyComplex technology commandmade easy output, and handy debug commands to keep in mind. Based on the “APP Free study cards” I have created the ANKI version, so people can go throughGood training resourcethe flashcards on their mobile phones etc while commuting to work and back again, utilizing that time as study time. I am still working on my CCIE number,CCNA study materialtherefore this document is subject to change without notice, I keep adding things I think one could easily forget etc or is just generally good to know. Keep an eyeCCNP study materialon the “revision number” on the top left to see if I had made any changes since you last visited the file. If my “APP Free” card deck had a great impact on your CCIECCIE study materialtrail, please feel free to let me know and post me your CCIE number!Train & StudyHave fun studying!ExamRe-certify CCNPRe-certify CCIERe-certify CCNACCDP contentCCIE contentCCNP contentCCNA contentCCIE certificationCCNP certificationFor all the folks who rather use the “APP Free” study flashcards on a mobile device, please download the ANKI version of the cardsCCNA certificationCisco learningFound here:Cisco CCIE lernkartenCisco CCIE visio flashcardshttp://www.flashcardguy.chCisco CCNP visio flashcardsCisco CCNA visio flashcardsCisco CCIE ANKI flashcards There are two versions, one with all the 1600 cards in one deck, and another ZIP version where I have separated each technology intoCisco CCNP ANKI flashcardsa separate ANKI file which might be easier, better to use initially.Cisco CCNA ANKI flashcardsCisco quality flashcardsCisco CCIE quality flashcardsANKI for mobile devices found here: http://ankisrs.net/Cisco CCNP quality flashcardsCisco CCNA quality flashcardsPlease use ankisrs support / forums if you are facing problems running ANKI on your mobile devices. ThanksCisco Service Provider flashcardsIphone CCIE study flashcardsAndroid ANKI CCIE study flashcardsCCIE study guideTopic:My CCIE storyCCIE written preparationSwitch/BridgeCisco Notecards CCNP / CCIECCNP flash cardsDMVPNCCIE flash cardsIP routingHands on cisco trainingRIPStudy guidesEIGRPCCIE study planRedistributionCisco TSHOOT 642-813 preparationCisco SWITCH 642-832 preparationOSPFcolored, cut them in rows, pre-fold them in rows, glue them together, cut the single cards from the row.Cisco ROUTE 642-902 preparationBGPMark the question side with a highlighter/marker to make it easier for you to sort.Cisco CCIE study summaryMulticastCCIE mobile appIPv6CCNP mobile appSecurityANKI CCIE APPor simply use the PDF to search for a command etc. Lets say you forgot how to do OSPF authentication, then go to the first page of OSPF,ANKI CCNP APPVPN/MPLSCTRL-F, “authentication” and hopefully you will find something within minutes that can help you.CCNP AnkidroidSystemCCIE AnkidroidServicesTCP / IP trainingQoSCCIE study approachFrame-RelayCCIE study planCCNP study planStudy approachCCNA study planrachsal.fwwch.ydgu1600 Cisco CCIE RS ver 4 / 5/ CCNP RS study flashcardsANKI version for mobile devices:“APP Free”, the classic way:Instructions “APP Free” study flashcardsPrint them A3Page:26810152122334150576674798596102
Trunk vlan allowed 25,99Switchport mode dot1q-tunnelL2protocol-tunnel [cdp, vtp, stp .]Switch / BridgeShow interface fa0/x pruningVlan100802.1q Tunneling00n1alVot1wdsholneunq-tPort Vlans pruned for lack of request by neighborFa0/16 7-8,10,22,58,67,146show interface fa0/x pruningPort Vlan traffic requested of neighborFa0/16 1,5,7-10,22,43,58,67,79,146show interface trunkShow interface fa0/x trunk - offers easier outputVlan 100 is the Metro TagSwtichport mode trunkSwtichport trunk allowed vlan 25,29MTU 1504 /Reload!Vlans not specified in the listwill NOT be pruned, vlans withinthe list could be pruned:What is a important pre-requisitfor Dot1Q Tunnel setups ?Set the MTU to 1504 and reloadthe switch.VTP Prune-EligibleListinterface FastEthernet0/Xswitchport trunk pruning vlan 2-6, 8-10Show spanning-tree uplinkfast2-6, 8-10 are prune-eligible!Vlan 7 will never be pruned!MTU 1504 /Reload!Access vlan 30Access vlan 20Access vlan 10Trvla unkn 1 All0,2 ow0,3 ed0Po2EtherChannel over802.1q TunnelingPo2Switchport trunkallewed vlan 60,99Access vlan 30Access vlan 20Access vlan 10Global command over-rules the interfacecommand:Spanning-tree global vs InterfacecommandsPo2Spanning-tree vlan 1 – x port-prio 16debug spanning-treebackbonefastInterface Fa0/xSpanning-tree port-priority 16interface FastEthernet0/[X,Y,Z]switchport access vlan [10,20,30]switchport mode dot1q-tunnell2protocol-tunnel cdpl2protocol-tunnel stpl2protocol-tunnel point-to-point [Pagp,Lacp]Interface Fa0/xBridge-group 1Bridge-group 1Bridge-group 2Switchport mode dynamic autoLAN 1LAN 3Switchport mode dynamic desirableSpanning-tree vlan x-y forward-delay [seconds]SwitchportstypesSwitchport mode trunkChange Spanning-tree listening /learning timersSwitchport mode accessswitchport mode dot1q-tunnelDefault is 15, command impacts LISTENING andLEARNINGThere is no separate command for the two states,only one for both.LAN 2LAN 3LAN 4no switchportswitchport mode dynamic desirableswitchport mode dynamic desirableBridge 1 protocol ieeeint fa0/xbridge-group XLAN 2switchport mode private-vlan promiscuousLAN 4LAN 1switchport mode private-vlan hostswitchport mode dynamic desirableBridge-group 2int ser0/xbridge-group XLAN2Serialswitchport mode dynamic desirableBridging over Frame-Relay -non multicastswitchport mode dynamic desirableswitchport mode dynamic desirableSwitchport trunk encapsulation dot1qswitchport mode dynamic autoswitchport mode dynamic desirableswitchport mode dynamic desirableswitchport mode dynamic desirableSwitchport trunk encapsulation dot1qLAN1switchport mode dynamic autoswitchport mode dynamic desirableHow to identify STP portfast portsin the debug outputPort fast enabled ports will have a log entrysuch as:Debug spanning-tree eventsJUMP TO FORWARDING FROM BLOCKINGswitchport trunk encapsulation dot1qswitchport mode trunkswitchport trunk encapsulation dot1qswitchport mode trunkswitchport trunk encapsulation dot1qswitchport mode trunkHelp me create more flashcards:Bridging over Frame-Relay with multicastWhat types of bridging over Framerelay are there?Bridging over Frame-Relay via SubInterfacesRemote Transparent bridging with Circuit-groups(MFR like)switchport trunk encapsulation dot1qswitchport mode trunkSimply press this button and send me yourcredit cards regards!Ranging 5 bucks to unlimited!Debug spanning-tree eventsswitchport mode dynamic desirableSwitchport trunk encapsulation islswitchport mode dynamic desirableswitchport mode dynamic desirableSwitchport trunk encapsulation islswitchport mode dynamic desirableswitchport trunk encapsulation islswitchport mode trunkswitchport trunk encapsulation islswitchport mode trunkswitchport trunk encapsulation islswitchport mode trunkswitchport trunk encapsulation islswitchport mode trunkHandy set of Spanning tree debugcommands:Debug spanning-tree backbone fastDebug spanning-tree pvst Thanks for appreciating my effortsColinhttp://www.flashcardguy.ch
Switch / BridgeInt fa0/xUdld port aggressiveUDLD well-known MAC 0100.0ccc.ccccDevice ID Originator Port Timeout Echo ValueNormal Mode:UDLD port modesUndetermind – continues to operate/does not prevent loopsIP Phone Trust andCoS ExtendStorm control setupAgressive Mode: 8 UDLD frames / secondNo response for 1 second - Port is errordisabledInterface bandwith 10 %Reset all UDLD error disabled ports via:SW1(config-if)#storm-control action [trap, shutdown]UDLD RESETspanning-tree mst configurationname MST1revision 1instance 1 vlan 1-100instance 2 vlan 101-200instance 3 vlan 201-4094Spanning-tree MST configDefault interface fa0/xMonitor session [X] source [vlan x, int y]Monitor session [X] destination fa0/x ingress vlan [YY]MonitorsourceMonitor destinationSwitchport access vlan 123Smartport MacrosSPAN sessionsspanning-tree mst 1 priority 0spanning-tree mst 2 priority 4096spanning-tree mst 2 priority 8192Ingress vlan [XX]SnifferSending TCP resets toFW sourced from vlan123Interface fa0/xmacro apply MACRO-NAMEspanning-tree mode mstSW1:showvlanremVlan [500]remote-spanSpanning-tree MST port priorityand costshow parser macroSending TCP FIN to IDS/IPSShow spanning-tree mst X detailote-spanStandard / existing macros can be verified by:monitor session [X] source interface [fa0/x]monitor session [X] destination vlan [500]Interface fa0/xSpanning-tree mst X cost [COST]SW2:RSPAN sessions:Interface fa0/xSpanning-tree mst X priority [16]Vlan [500]remote-spanShow parser macroVlan 500Applying dynamic macrosSW2SW3SW1destinationAnd applied with dynamic parameters:Interface fa0/10Macro apply cisco-desktop access vlan 10SW3:Vlan [500]remote-spanmacro name MACRO-NAMEswitchport mode accessswitchport access vlan 146spanning-tree bpdufilter enable@sourcemonitor session [X] source vlan [500]monitor session [X] destination fa0/x ingress vlan [YY]Config applied to SW1:Rootsw1sw3Spanning-tree port priority and itsinfluence?sw2Port 2Prio 16Port 1Prio 32Int Port-Channel 22switchport backup interface Fa0/16switchport backup interface Fa0/16 preemption mode forcedswitchport backup interface Fa0/16 preemption delay 20Flex LinksPo22Span session show outputXsw4SW1Fa16Alternative to spanning-treeFa13,14BACKUPinterfaceFa19If port-chan 22 goes down,place Fa16 into FWDimmediately.Delay re-using Po22 for20 seconds once it comesback up.Fa16Fa19Spanning-tree port-priorityinfluences only the direct attachedSW4, but is configured on SW3!SW2SW3ckup alldebug baPrimary link is UP/UPRootshow interfaces po1 switchport backupsw1Help me create more flashcards:sw2Spanning-tree port cost and itsinfluence?XPort 2Port cost 16Flex LinksRSPAN session show output:Port 1Port cost 32Show outputssw4Primary link is DOWNshow interfaces po1 switchport backupSpanning-tree port cost affects SW4 andalso other switches possible downstream switches to use port 2SW1:IP routingInt fa1IPv4 is routed while IPv6packets are bridgedSwitchport access vlan 20Simply press this button and send me yourcredit cards regards!Ranging 5 bucks to unlimited!bridge 1 protocol vlan-bridgeInt fa2Switchport protectedFa1Int fa0/4bridge-group [1]Switchport access vlan 20Protected Ports setup:Int fa3Switchport protectedFa2XFa4Fa3Switchport access vlan 20Int fa4What are the three differentconfiguration methods for Voiceports?Fallback BridgingInt fa0/6bridge-group rdguy.chIPv6 ort access vlan 20Fa2 and Fa3 can’t communicate even being in the same VlanIP addr106.0.0.6/24show bridge [1] groupIPv4:RIPv2IP addr104.0.0.4/24Thanks for appreciating my effortsIPv6 addr2001::4/64Colin
R4:interface FastEthernet0/1ip address 104.0.0.4 255.255.255.0ipv6 address 2001::4/64R4#SW1#Ip routingFallback Bridginginterface Vlan104ip address 104.0.0.10 255.255.255.0bridge-group 1PPPBi-directionalCHAP Authenticationinterface FastEthernet0/6No switchportIp address 106.0.0.10 255.255.255.0bridge-group 1interface FastEthernet0/1ip address 106.0.0.6 255.255.255.0ipv6 address 2001::6/64Host ACommunity 2000Host BCommunity 1000Private VLANsGateway RouterPromiscous PortDesignppp authentication chapppp chap hostname USER-R5PPP AAAAuthenticationR5R5auaga ths R4instPPPinterface Serial 0/1encapsulation pppppp authentication chap(Auth via Radius, if not available fallback to local database)R5#(Radius)username USER-R5 pass ciscoHost CCommunity 2000R5uthsR4 a instagaDebug ppp negotiationsR4PPPRadiusSwitch / BridgeTACACS R4#( User admin password 0 cisco ! Don’t get locket out )aaa new-modelaaa authentication login CONSOLE noneaaa authentication ppp PPP-AUTH-LIST group GRP-RADIUS local!aaa group server radius GRP-RADIUSserver-private 155.1.146.100 key CISCO!interface Serial 0/1/0ppp authentication pap chap PPP-AUTH-LIST!line console 0login authentication CONSOLEppp chap hostname USER-R4TrunkVlan 100R4Radiusinterface Serial 0/1encapsulation pppAPCH thauIPv6 trafficIs bridgedbetween arouted portand SVI vlanWhile IPv4traffic isroutedbridge 1 protocol vlan-bridgeR5uthsR4 a instagausername USER-R4 pass ciscoR5R5auaga ths R4instTACACS PPPHost DCommunity 1000Useful PPP debug commandsHost ECommunity 3000Debug ppp authenticationDebug ppp packetDebug ppp errorPrimary Vlan 100Community1000Community2000isolated 3000Host BHost AHost EHost DHost CPPP AAAAuthentication(TACACS )( debug aaa authentication )R5#( User admin password 0 cisco ! Don’t get locket out )aaa new-modelaaa authentication login CONSOLE noneaaa authentication ppp default group tacacs local!tacacs-server host 155.1.146.200 key CISCO!line console 0login authentication CONSOLE(Auth via TACACS , if not available fallback to local database)1”h as e“cfg p-vlancheck n privatelavwshovlan 1000private-vlan communityvlan 3000private-vlan isolatedPrivate VLANsconfigvlan 100private-vlan primaryprivate-vlan association 1000,2000,3000( Associate Prim / Sec aslast part in cfg phase 1)interface FastEthernet0/1switchport private-vlan mapping 100 add 1000,2000,3000switchport mode private-vlan promiscuousGatewayinterface FastEthernet0/3switchport private-vlan host-association 100 1000switchport mode private-vlan hostCommunity 1000interface FastEthernet0/5switchport private-vlan host-association 100 2000switchport mode private-vlan hostCommunity 2000interface FastEthernet0/13switchport trunk encapsulation dot1qswitchport mode trunkMR MT UU1 /492!“Config phase 1"vtp domain CCIEvtp mode transparentHow do you filter out Vlan IDs outof SPAN sessions for Trunks ?monitor session 2 destination interface fa0/1R4 Client:PPPoEClient / Server( SPAN session will only SPAN traffic within Vlan 5-10 )ip dhcp pool POOL-PPPoEnetwork 155.1.35.0 255.255.255.0interface FastEthernet 0/1no shutdowninterface FastEthernet0/1.35encapsulation dot1Q 35pppoe enable group PPPOEbba-group pppoe PPPOEvirtual-template 1sessions per-mac throttle 10 60 300debug pppoe packetsWhats the purpose ofPrivate VLANsvlan dot1q tag nativeShow commandscheck after configuring “phase 1”In dot1q tunneling ?enables tagging of native VLAN frames on all IEEE 802.1Qtrunk ports in dot1q tunnels.show vlan dot1q tag nativedebug pppoe eventsPPPoEDebugs / Show CMDs- Service-provider network mis-direction issueR5#clear pppoe allSession on Client is UPmonitor session [1] destination interface Fa0/xencapsulation replicateR5R4 will have to authenticate towards R5 (sending credentials)debug ppp negotiationshow pppoe sessionR4#interface Serial 0/1encapsulation pppppp pap sent-username USER-1 pass ciscoUni-directionalPAP AuthenticationR5Serverinterface Virtual-Template 1encapsulation pppip address 155.1.35.1 255.255.255.0ppp authentication chap PPPOE-LISTshow vlan private-vlanPPPinterface Dialer1ip address dhcpencapsulation pppdialer pool 1ppp chap hostname USER-1ppp chap password CISCO!interface FastEthernet0/1no ip addressno shutdownpppoe enablepppoe-client dial-pool-number 1between switchesR4PPPoEaaa authentication ppp PPPOE-LIST localusername USER-1 password CISCOmonitor session 2 source interface fa0/2 rxmonitor session 2 filter vlan 5-10R4ClientHelp me create more flashcards:Transit to PPPoe SRV has just been disruptedHow can one SPAN CDP, STP andother control protocols to thedestination port ?PPPoe Client status views:username USER-1 pass ciscoTransit disrupted, attempting connection to SRVinterface Serial 0/1encapsulation pppSimply press this button and send me yourcredit cards regards!ppp authentication papClock rate [64000]R4#Connection from PPPoe SRV to Client establishedusername USER-R4 pass ciscoPPPHow to configure dot1Q tunnel ona routers subInterfaceR45 ausnd o R tose ls t R5R4 tia cten peed ex kcr not bac lin)les(cadoUni-directionalCHAP Authenticationinterface Serial 0/1encapsulation pppppp authentication chap callinppp chap hostname USER-R5R5#username USER-R5 pass ciscoPPPoE Server’s status views:Interface Fa0/1.41Connection from PPPoe SRV to Client was lost due toproblem on transit from client to serverencapsulation dot1Q 99 second-dot1q 200,300Thanks for appreciating my effortsthinterface Serial 0/1encapsulation pppppp authentication chaphttp://www.flashcardguy.chInterface Fa0/1MTU 1504Ranging 5 bucks to unlimited!Colin
Switch / BridgeShow int trunkShow etherchannel summaryIF “spanning-tree extend system-id” is NOT ENABLED:Advanced LACP / PAGPtroublehsooting commands:Rack1SW1#show pagp ? 1-48 Channel group numbercounters Traffic informationinternal Internal informationneighbor Neighbor informationspanning-tree extend system-idone MAC address per VLAN to make the bridge ID uniquefor each VLAN, using a lot of MAC addresses- (chassis with only 64 MAC addresses!)extended system ID enabled:explainedRack1SW1#show lacp ? 1-48 Channel group numbercounters Traffic informationinternal Internal informationneighbor Neighbor informationsys-id LACP System IDOne MAC address used in all STP Vlans. In order touniquely identify the root the VLAN-ID value is added tothe STP priority value, with the same MAC address in allVLANs.STP Root- MST domain domain name and revision numberRX part breaks(unidirectional)( 64 instances max )- MST domain configuration can be distributed via VTPVersion 3 instance. (Instead of error prone manual config)What does:conf tdefine interface-range VPORTS FastEthernet 0/7-8And MSTUsed for macro’sDo?- only the vtp primary server, is allowed to update otherdevices- Two instances in VTP version 3, VLAN and MSTinstanceVTP Version 3- Instances can be on the same or separate switches.- If there is more than one primary server a warningmessage will indicate conflicting devices.facts:VTP Version 3With routed interfaces and- VTPVer 2 compatible to Version 3, where as Ver 1 is not.Default VLAN-IDs:- VTP 2 device will never update a Version 3 device.- After reload a primary server will take the secondaryserver roleSWITCH# show spanning-tree mst configuration% Switch is not in mst modeName [MST]Revision 1 Instances configured 3Instance Vlans mapped-------- ---------0 2-400,406-4000,4006-4094-------- ---------config changes of MST only allowed on VTP 3 primaryserver.SWITCH# show vlan internal usageVLAN Usage---- ------------------- SNIP 1018 FastEthernet1/24VlanID 1018 for Fa1/24 !VTP Version 3modesservice password-encryptionvtp password --------------------------------- vtp mode server- vtp mode client- vtp mode transparent- vtp OFFvtp password / service password-encryptionSW1# show vtp passwordVTP Password: CF94C2FF1CDCEB8DC795CEB21E305F10If you have a lab on which the Lines keep miss-behaving,Clear all lines instead of individually:RXTXRXTXRXTXRoutingUsed for routingVlanDisables routing and sets the switch to be a layer 2 switchDisable vtp per port (VTP off)Extended-matchReformats routing memory space to allow 144-bit layer 3TCAM support needed for WCCP and/or multple VRFinstancesVTP Version 3Cisco 3750 Stack Master is thevtp primary-serverVQP Client Status:--------------------- THE CURRENT STACK MASTER FAILS!With the following command, the newly assigned StackMaster will send a VTP Version 3 take-over message after5 minutes down time of the previous Stack Master.Announcing the new Stack Masters MAC address asprimary-serverCatalyst VMPS config:VMPS VQP Version: 1Reconfirm Interval: 60 minServer Retry Count: 3VMPS domain server:vmps reconfirm 30vmps retry 5vmps server 1.1.1.1 primaryvmps server 2.2.2.2Reconfirmation status:---------------------VMPS Action: No Dynamic Portstack-mac persistent timer 5 Show commands:show vtp counters(can discover configs from different primary servers)show vlan internal usage (Vlan ID 1000-1018 issue)Help me create more flashcards:Simply press this button and send me yourcredit cards regards!Ranging 5 bucks to unlimited!show vtp devices conflictsshow vtp interfaceR3#line-clear%HA EM-6-LOG: CLEAR-LINES: All lines clearedint fa0/xswitchport mode accessswitchport access vlan dynamicshow vtp status enhancedVTP Version 3event manager applet CLEAR-LINESevent none sync yesaction 1.0 cli command "clear line 65"action 1.1 cli command "clear line 66"action 1.2 cli command "clear line 67"action 1.3 cli command "clear line 68"action 1.4 cli command "clear line 69"action 1.5 cli command "clear line 70"action 1.6 cli command "clear line 71"action 1.7 cli command "clear line 72"action 1.8 cli command "clear line 73"action 1.9 cli command "clear line 74"action 2.0 cli command "clear line 75"action 2.1 cli command "clear line 76"action 2.2 cli command "clear line 77"action 2.3 cli command "clear line 78"action 2.4 cli command "clear line 79"action 2.5 syslog msg "All lines cleared"SW1#show vmpsvlan.dat is encryptedshow vtp devices featurealias exec line-clear event manager run CLEAR-LINESshow sdm preferThe Stack Master announces its own MAC Address asvtp version 3 primary-server.vtp password CISCO hiddenAndRXTXRXconf tsdm prefer [Access Routing Vlan Extended-match]Within vlan.dat password is still in clear text.vtp password X hiddenHome Lab tip:Per interface:Spanning-tree guard loopDisplay of the password is encrypted, vlan.dat IS CLEAR TEXTDifference betweenTXGlobal:Spanning-tree loopguard defaultint fa0/24no vtpSW1# show vtp passwordVTP Encrypted Password: 02270A5F19030E32SWITCH# show vtp passwordVTP Encrypted Password: 02270A5F19030E32TXTXRXSDM Prefer on Catalystservice password-encryptionVTP Version 3RXRXTXdefault allocation policy the switch starts to allocatebeginning at 1018! In order to use Vlan 1018, defaultinterface fa1/24, shutdown the port, force a VTP revisionnumber change, by changing vlan 1018's name to floodthe change from an Internal Vlan to a regular vlan to otherswitches.vtp primary-server mst [force]Configuration:TXRXAccessUsed for QoS classification and securityvtp domain DOMAIN-Xvtp primary-server vlan [force]RXRXSTP Root(mainly used on fiber links, can bereproduced with bpdufilter onethernet) - requiredvtp version 3VTP Version 3TXMainlyint fa1/24no switchportip address 1.2.3.4 255.255.255.0- Reserved VlanIDs 1000-1017, (show vlan intern usage)spanning-tree extend system-idRX- MST config changes only allowed on primary server.VTP Version 3define interface-rangeTXSpanning-tree loopguardTXVTP Version 3SWITCH# show vtp devicesGathering information from the domain, please wait.VTP Database Conf switch ID Primary Server Revision System Nameshow vtp devicesOutput:------------ ---- -------------- ------ ---------- ---------VLAN No 000c.0012.3456 000c.0012.3456 1001 SWITCHMST No 000c.0012.3456 000c.0012.3456 42 SWITCH(Neighbor with two instances shown, VLAN and MSTinstance)STP rules:Spanning-tree selectionrules1. Lower root BID2. Lower path cost to the root bridge3. lower sending BID4. lower Sending Port-ID (Priority).Port-iDThanks for appreciating my effortsColinhttp://www.flashcardguy.ch
HUBinterface Tunnel1ip address 10.1.1.1 255.255.255.0no ip redirectsip nhrp map 10.1.1.2 192.1.2.2ip nhrp map 10.1.1.3 192.1.3.3ip nhrp map 10.1.1.4 192.1.4.4ip nhrp network-id 111tunnel source Ethernet0/0tunnel mode gre multipointNBMA Range 192.1.1.x.xTunnel Range 10.1.1.xHUB.11.1Tun 13.3NBMA2.2.3.2SpokeSpokeNBMA Range 192.1.1.x.xTunnel Range 10.1.1.xTrace from Spoke 2 to Spoke 3HUB.11.1Tun 1NBMA2.2.3.2SpokeSpokeDMVPN Phase 1Static configR2#traceroute 10.1.1.3 numericType escape sequence to abort.Tracing the route to 10.1.1.3VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.1 13 msec 6 msec 5 msec2 10.1.1.3 3 msec * 2 msecHUB.1tunnel mode gre multipoint3.3NBMA.3.2SpokeSpokeDMVPN Phase 2Static configTrace from Spoke 4 to Spoke 2HUB.1.2Spoke.3SpokeDMVPN Phase 2static configHUB.1Tun 1Spoke2.2.2.2/323.3NBMA2.2.3.2Spoke3.3.3.3/32NBMA Range 200.1.x.xTunnel Range 123.1.1.xDMVPN Phase 1 setupUsing EIGRPDo not use “no ip split-horizon eigrp VPN Phase 1Dynamic config2.2.3.2SpokeSpokeDMVPN Phase 2Dynamic configTrace from Spoke 4 to Spoke 2HUB.1 1. packet1.1Tun 13.3NBMA2.2.2.32nd packetSpokeSpokeDMVPN Phase 2dynamic configclear ip nhrp on the HUB anddiscover that you no longerhave reachability from and toyour spokes!Spokeinterface Tunnel123ip address 123.1.1.2 255.255.255.0ip nhrp map 123.1.1.1 200.1.1.1ip nhrp network-id 111tunnel source Ethernet0/0tunnel destination 200.1.1.1How do you solve this in thelab?NBMA Range 200.1.x.xTunnel Range 123.1.1.xHUB:HUBrouter eigrp 10interface Tunnel123network 123.0.0.0ip address 123.1.1.1 255.255.255.0network 1.1.1.1no ip redirectsip nhrp map 123.1.1.2 200.1.2.2ip nhrp map 123.1.1.3 200.1.3.3Sending aip nhrp map multicast 200.1.2.2via su defaultip nhrp map multicast 200.1.3.3rommarizatio uteip nhrp network-id 111nip summary-address eigrp 10 0.0.0.0 0.0.0.0tunnel source Ethernet0/0tunnel mode gre multipointSpokeinterface Tunnel123ip address 123.1.1.2 255.255.255.0Spoke:ip nhrp map 123.1.1.1 200.1.1.1router eigrp 10ip nhrp network-id 111network 123.0.0.0tunnel source Ethernet0/0network 2.2.2.2tunnel destination 200.1.1.1DMVPN Phase 1 setupUsing RIPSpoke2.2.2.2/32HUB.1Tun 13.3NBMA2.2.2.3int tun 1tunnel source x.x.x.xtunnel mode gre multipointHub:debug nhrp cache:interface Tunnel1ip address 10.1.1.1 255.255.255.0no ip redirectsip nhrp network-id 111tunnel source Ethernet0/0tunnel mode gre multipointe:achb:cuHhrpOngnubdeinterface Tunnel1ip address 10.1.1.4 255.255.255.0no ip redirectsip nhrp map 10.1.1.1 192.1.1.1ip nhrp network-id 111ip nhrp nhs 10.1.1.1tunnel source Ethernet0/0tunnel mode gre multipointSpokeinterface Tunnel1ip address 10.1.1.2 255.255.255.0no ip redirectsip nhrp map 10.1.1.1 192.1.1.1ip nhrp network-id 111ip nhrp nhs 10.1.1.1tunnel source Ethernet0/0Spoke:R2#show ip nhrp10.1.1.1/32 via 10.1.1.1interface Tunnel1Tunnel1 created 00:04:29, never expireip address 10.1.1.4 255.255.255.0Type: static, Flags: usedno ip redirectsNBMA address: 192.1.1.1ip nhrp map 10.1.1.1 192.1.1.110.1.1.4/32 via 10.1.1.4ip nhrp network-id 111Tunnel1 created 00:02:31, expire 01:57:29ip nhrp nhs 10.1.1.1Type: dynamic, Flags: routertunnel source Ethernet0/0NBMA address: 192.1.4.4tunnel mode gre multipointR2#traceroute 10.1.1.3 numericType escape sequence to abort.Tracing the route to 10.1.1.3VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.1 11 msec 1 msec 6 msec2 10.1.1.3 1 msec * 1 msecsrc NBMA: 192.1.4.4src protocol: 10.1.1.4, dst protocol: 10.1.1.1NHRP: Send Registration Reply via Tunnel1 vrf 0, packet size: 112src: 10.1.1.1, dst: 10.1.1.4What are main configurationdifferences betweenDMVPN Phase 12nd traceroute:Static and dynamicR2#traceroute 10.1.1.3 numericType escape sequence to abort.Tracing the route to 10.1.1.3VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.3 1 msec * 2 msecSpoke3.3.3.3/321.1.1.1/321.1What are main configurationdifferences betweenHUB.1Spoke3.3NBMA.22.2.2.2/32DMVPN Phase 2.3Spoke3.3.3.3/32Static and dynamicOn Spokes:int tun xip nhrp registration timeout 1 sec HUBinterface Tunnel123ip address 123.1.1.1255.255.255.0no ip redirectsip nhrp map 123.1.1.2 200.1.2.2ip nhrp map 123.1.1.3 200.1.3.3ip nhrp map multicast 200.1.2.2ip nhrp map multicast 200.1.3.3ip nhrp network-id 111ip rip advertise 2no ip split-horizontunnel source Ethernet0/0tunnel mode gre multipointSpoke:router ripversion 2network 2.0.0.0network 123.0.0.0no auto-summaryHUB:router ripversion 2network 1.0.0.0network 123.0.0.0no auto-summaryDMVPN Phase 1 setupUsing RIPdo not use “no ip split-horizon”HUB.1Tun 1Spokeinterface Tunnel123ip address 123.1.1.2 255.255.255.0ip nhrp map 123.1.1.1 200.1.1.1ip nhrp network-id 111tunnel source Ethernet0/0tunnel destination 200.1.1.12.2Spoke2.2.2.2/323.3NBMA.2.3Spoke:ip nhrp map HUB-TUNNEL-IP HUB-NBMA-IPtunnel destination HUB-NBMA-IPPhase 1 dynamicHub:ip nhrp map SPOKE-TUN-IP SPOKE-NBMA-IPtunnel mode gre multipointPhase 2 staticHub:ip nhrp map SPOKE-TUNNEL-IP SPOKE-NBMA-IPtunnel mode gre multipointSpoke:ip nhrp map HUB-TUNNEL-IP HUB-NBMA-IPip nhrp map SPOKE-x-TUNNEL-IP SPOKE-x-NBMA-IPtunnel mode gre multipointPhase 2 dynamicHub:ip nhrp map SPOKE-TUNNEL-IP SPOKE-NBMA-IPtunnel mode gre multipointSpoke:ip nhrp map HUB-TUNNEL-IP HUB-NBMA-IPip nhrp nhs HUB-TUNNEL-IPtunnel mode gre multipointConfig?1.1.1.1/321.1Phase 1 staticHub:ip nhrp map SPOKE-TUNNEL-IP SPOKE-NBMA-IPtunnel mode gre multipointSpoke:ip nhrp map HUB-TUNNEL-IP HUB-NBMA-IPtunnel destination HUB-NBMA-IPip nhrp nhs HUB-NBMA-IPConfig?Tun 12.2NHRP: Tunnel1: Cache add for target 10.1.1.4/32 next-hop 10.1.1.4192.1.4.4NHRP: Inserted subblock node for cache: Target Inserted subblocknode for cache: Target 10.1.1.4/32nhop 10.1.1.4NHRP: Converted internal dynamic cache entry for 10.1.1.4/32interface Tunnel1 to externalNHRP: Updating our cache with NBMA: 192.1.1.1, NBMA ALT:192.1.1.1NHRP: Setting 'used' flag on cache entry with nhop: 10.1.1.4NHRP: NHRP successfully mapped '10.1.1.4' to NBMA 192.1.4.4NHRP: Tunnel1: Cache update for target 10.1.1.4/32 next-hop 10.1.1.4192.1.4.4NHRP: Updating our cache with NBMA: 192.1.1.1, NBMA ALT:192.1.1.1NHRP: Setting 'used' flag on cache entry with nhop: 10.1.1.4NHRP: NHRP successfully mapped '10.1.1.4' to NBMA 192.1.4.4NHRP: Receive Registration Request via Tunnel1 vrf 0, packet size: 92t:src NBMA: 192.1.4.4ek
Cisco Notecards CCNP / CCIE CCNP flash cards CCIE flash cards Hands on cisco training Study guides CCIE study plan Cisco TSHOOT 642-813 preparation Cisco SWITCH 642-832 preparation Cisco ROUTE 642-902 preparation Cisco CCIE study summary CCIE mobile app CCNP mobile app ANKI CCIE APP ANKI CCNP APP CCNP Ankidroid CCIE Ankidroid TCP / IP training .
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
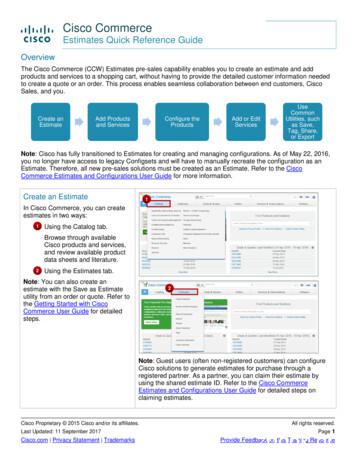
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unified Computing System (Cisco UCS), Cisco UCS B-Series Blade Servers, Cisco UCS C-Series Rack Servers, Cisco UCS S-Series Storage Servers, Cisco UCS Manager, Cisco UCS
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base