Cisco Success Network (CSN) On Cisco Email Security
Cisco Success Network (CSN) on Cisco on CollectedPrerequisitesRequirementsFirewall Related ConfigurationComponents UsedConfigureCSN and CTR dependenciesCSN Configuration using the UICSN Configuration using the CLITroubleshootIntroductionThis document provided the information on the Cisco Success Network feature which would beavailable as part of the AsyncOS 13.5.1 release for the Cisco Email Security Appliance (ESA).Cisco Success Network (CSN) is a user-enabled cloud service. When CSN is enabled, a secureconnection is established between the ESA and the Cisco cloud (Using the CTR Connection), tostream feature status information. Streaming CSN data provides a mechanism to select data ofinterest from the ESA and to transmit it in a structured format to remote management stations.Benefits To inform the customer regarding available unused features that can improve theeffectiveness of the product.To inform the customer regarding additional technical support services and monitoring thatmight be available for the product.To help Cisco improve the product.Information CollectedThese are the list of feature information that is collected as part of this feature once configured onthe ESA device: Device Model (x90, x95, 000v,100v, 300v, 600v)Device Serial Number (UDI)UserAccountID (VLN id number or SLPIID)Software Version
Install DateslVAN (Virtual Account Name in Smart Licensing)Deployment ModeIronPort Anti-SpamGraymail Safe UnsubscribeSophosMcAfeeFile ReputationFile AnalysisData Loss PreventionExternal Threat FeedsIronport Image AnalysisOutbreak filtersCisco IronPort Email Encryption Settings (envelope encryption)PXE encryptionDomain ReputationURL FilteringBlock Page CustomizationMessage TrackingPolicy, Virus and Outbreak QuarantinesSpam QuarantinePrerequisitesRequirementsTo configure this feature, these are some of the requirements which must be fulfilled: CTR (Cisco Threat Response) accountFirewall Related ConfigurationThe Firewall configuration needed to get CSN functional is currently dependent on the CTRcommunication and please refer to this document for more information: Integrating ESA with CTRComponents UsedThe information in this document is based on these software and hardware versions: Email Security Appliance (ESA) AsyncOS Version 13.5.1.x and above.ConfigureYou can configure this feature using both the ESA UI or the CLI. Details on both the steps areshown below.CSN and CTR dependencies
CSN Feature depends on the CTR Feature connectivity for its successful operation and this tableprovides more information on the relationship between these two processes.SSECSNConnect ProcesorsDisableDisabled anuallyEnabledEnabledDownDownUpUpUpDownUpUpCSN Configuration using the UI1) Login into the ESA UI.2) Browse to Network Cloud Service Settings (I will assume that CTR was disabled beforewe started with the upgrade to 13.5.1.x). Before the upgrade, If CTR was enabled, then CSN willalso be enabled by default. If CTR was disabled, then CSN will also be disabled.Note: We will assume CTR was disabled before the upgrade as CTR in a CentralizedDeployment is supposed to be disabled as it is enabled only on the SMA for sending out thereporting information to CTR.3) This is what you would observe as default on the ESA Device: -4) We will now register this ESA by first enabling the CTR Services on the ESA and "Submit" thechanges.
5) It would show this Status on the CTR Page "The Cisco Cloud Service is busy. Navigate back tothis page after some time to check the appliance status." Commit the changes to the device.6) You would then move ahead and get the CTR Token and register the device to CTR:7) You should see this status once the registration is successful:Success — A request to register your appliance with the Cisco Threat Response portal isinitiated. Navigate back to this page after some time to check the appliance status.8) Once you refresh the page, you would see the CTR Registered and CSN Enabled:9) As Discussed, CTR in this scenario needs to be disabled as this ESA is Centralized and youwould still see CSN enabled as expected. In case, this ESA is not managed by SMA (NonCentralized), you can keep the CTR enabled.
This should be the final state of the configuration. This step should be followed for every ESAas this setting is Machine Level.CSN Configuration using the CLI(Machine esa ) csnconfigYou can enable the Cisco Success Network feature to send your appliance details and featureusage to Cisco.Choose the operation you want to perform:- ENABLE - To enable the Cisco Success Network feature on your appliance.[] enableThe Cisco Success Network feature is currently enabled on your appliance.Changes would need to be committed as part of enabling this using the CLI.TroubleshootTo troubleshoot this feature, there is a PUB (/data/pub/csn logs) Log available that would havethe information on this feature. The sample below is the log at the time when the registration wascompleted on the device:(Machine ESA) (SERVICE) tailCurrently configured logs:Log NameLog -1. APIAPI LogsManual DownloadNone2. ampAMP Engine LogsManual DownloadNone3. amparchiveAMP ArchiveManual DownloadNone4. antispamAnti-Spam LogsManual DownloadNone5. antivirusAnti-Virus LogsManual DownloadNone6. asarchiveAnti-Spam ArchiveManual DownloadNone7. authenticationAuthentication LogsManual DownloadNone8. avarchiveAnti-Virus ArchiveManual DownloadNone9. bouncesBounce LogsManual DownloadNone10. cli logsCLI Audit LogsManual DownloadNone
CSN LogsCTR LogsDLP LogsAdvanced Phishing Protection LogsEncryption LogsIronPort Text Mail LogsSpam Quarantine LogsSpam Quarantine GUI LogsFTP Server LogsGraymail ArchiveGraymail Engine LogsHTTP LogsIP Reputation LogsIronPort Text Mail LogsRemediation LogsReporting LogsReporting Query LogsS3 Client LogsScanning LogsSender Domain Reputation LogsService LogsSmartlicense LogsNTP logsStatus LogsSystem LogsThreat Feeds LogsTracking LogsConsolidated Event LogsUpdater LogsUpgrade LogsURL Reputation Logslog you wish to tail.11. csn logs12. ctr logs13. dlp14. eaas15. encryption16. error logs17. euq logs18. euqgui logs19. ftpd logs20. gmarchive21. graymail22. gui logs23. ipr client24. mail logs25. remediation26. reportd logs27. reportqueryd logs28. s3 client29. scanning30. sdr client31. service logs32. smartlicense33. sntpd logs34. status35. system logs36. threatfeeds37. trackerd logs38. unified-239. updater logs40. upgrade logs41. url rep clientEnter the number of the[] 11Press Ctrl-C to stop.Sun Apr 26 18:16:13 2020Sun Apr 26 18:16:13 2020Sun Apr 26 18:16:13 2020Sun Apr 26 18:16:13 2020Sun Apr 26 18:16:13 2020Sun Apr 26 18:16:16 2020Sun Apr 26 18:16:16 in LogfileVersion: 13.5.1-177 SN: 564D2E7007BA223114B8-786BB6AB7179Time offset from UTC: -18000 secondsSystem is coming up.DAEMON: Watchdog thread startedThe appliance is uploading CSN dataThe appliance has successfully uploaded CSN data
Cisco Success Network (CSN) is a user-enabled cloud service. When CSN is enabled, a secure connection is established between the ESA and the Cisco cloud (Using the CTR Connection), to . Cisco IronPort Email Encryption Settings (envelope encryption)
ČSN ISO 21940-12 . 011449 : Vibrace - Vyvažování rotorů - Část 12: Postupy . (ruší ČSN EN ISO 13850:2016) 211 Kč . 501556 . ČSN EN ISO 16993. 838225 . Tuhá biopaliva - Přepočet výsledků analýz pro různé stavy biopaliv (ruší ČSN EN ISO . 16993:2015) 211 Kč. 501529 . ČSN EN ISO 16994 .
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
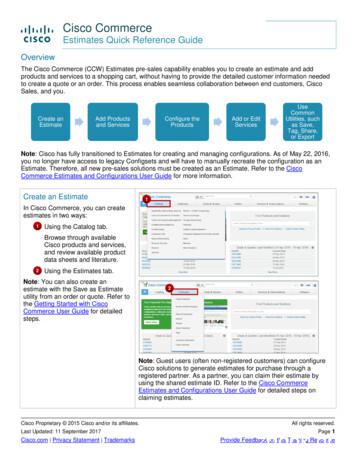
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Ulster Archaeological Society at the Divis and Black Mountain site. 5 Illustration 1: Divis Mountain viewed from the south west 1.2 Aims In order to enhance the archaeological record of this site, the aims of this survey were to produce an accurate plan drawing of the monument and carry out a photographic survey. This information was compiled into a report and submitted to the Environment and .