SSLVPN - Cisco
SSL VPNSSL VPN provides support in the Cisco IOS software for remote user access to enterprise networks fromanywhere on the Internet. Remote access is provided through a Secure Socket Layer (SSL)-enabled SSL VPNgateway. The SSL VPN gateway allows remote users to establish a secure VPN tunnel. The XE SSL VPNSupport feature provides a comprehensive solution that allows easy access to a broad range of web resourcesand web-enabled applications using native HTTP over SSL (HTTPS) browser support through the full-tunnelclient support. Prerequisites for SSL VPN, on page 1 Restrictions for SSL VPN, on page 2 Information About SSL VPN, on page 2 How to Configure SSL VPN, on page 4 Configuration Examples for SSL VPN, on page 18 Additional References for SSL VPN, on page 20 Feature Information for SSL VPN, on page 20Prerequisites for SSL VPNTo securely access resources on a private network behind an SSL VPN gateway, the remote user of an SSLVPN service must have the following: An account (login name and password). Support for full tunnel mode using Cisco AnyConnect Client. Operating system support. For more information, see the “AnyConnect Secure Mobility Client 3.1Computer OSs Supported” section in the Supported VPN Platforms, Cisco ASA 5500 Series document. Administrative privileges to install Cisco AnyConnect client.NoteThis feature is supported on the Cisco CSR 1000V Series Cloud Services Router only.SSL VPN1
SSL VPNRestrictions for SSL VPNRestrictions for SSL VPN ACL’s do not support DENY statements. Using Cisco AnyConnect VPN, if you create tunnels at a high bring up rate, a failure may occur. Whencreating a large number of VPN SSL sessions (for example, 1000) use a bring up rate of 15 TPS or lower.If you use a higher TPS rate, a failure may occur. SSLVPN PD is supported only with AnyConnect client version 3.x. On Cisco CSR 1000v versions 16.8.1b, 16.9.1 and 16.9.2, AnyConnect does not work when you run theplatform sslvpn use-pd command. The system displays the "connection attempt has failed" error. As aworkaround, after running this comand, perform write and reload. When you run the command again, itis executed.Information About SSL VPNSSL VPN OverviewCisco IOS SSL VPN is a router-based solution offering Secure Sockets Layer (SSL) VPN remote-accessconnectivity integrated with industry-leading security and routing features on a converged data, voice, andwireless platform. The security is transparent to the end user and easy to administer. With Cisco IOS SSLVPN, end users gain access securely from home or any Internet-enabled location such as wireless hotspots.Cisco IOS SSL VPN also enables companies to extend corporate network access to offshore partners andconsultants, keeping corporate data protected all the while. Cisco IOS SSL VPN in conjunction with thedynamically downloaded Cisco AnyConnect VPN Client provides remote users with full network access tovirtually any corporate application.SSL VPN delivers the following three modes of SSL VPN access, of which only tunnel mode is supportedin Cisco IOS XE software: Clientless—Clientless mode provides secure access to private web resources and will provide access toweb content. This mode is useful for accessing most content that you would expect to access in a webbrowser, such as Internet access, databases, and online tools that employ a web interface. Thin Client (port-forwarding Java applet)—Thin client mode extends the capability of the cryptographicfunctions of the web browser to enable remote access to TCP-based applications such as Post OfficeProtocol version 3 (POP3), Simple Mail Transfer Protocol (SMTP), Internet Message Access protocol(IMAP), Telnet, and Secure Shell (SSH). Tunnel Mode—Full tunnel client mode offers extensive application support through its dynamicallydownloaded Cisco AnyConnect VPN Client (next-generation SSL VPN Client) for SSL VPN. Full tunnelclient mode delivers a lightweight, centrally configured and easy-to-support SSL VPN tunneling clientthat provides network layer access to virtually any application.NoteSSL VPN will not work if ip http secure-server is enabled.SSL VPN2
SSL VPNModes of Remote AccessModes of Remote AccessTunnel ModeIn a typical clientless remote access scenario, remote users establish an SSL tunnel to move data to and fromthe internal networks at the application layer (for example, web and e-mail). In tunnel mode, remote usersuse an SSL tunnel to move data at the network (IP) layer. Therefore, tunnel mode supports most IP-basedapplications. Tunnel mode supports many popular corporate applications (for example, Microsoft Outlook,Microsoft Exchange, Lotus Notes E-mail, and Telnet).SSL VPN support provided by full tunnel mode is as follows: Works like “clientless” IPsec VPN Tunnel client loaded through Java or ActiveX Application agnostic—supports all IP-based applications Scalable Local administrative permissions required for installationFull tunnel client mode offers extensive application support through its dynamically downloaded CiscoAnyConnect VPN Client (next-generation SSL VPN Client) for SSL VPN. Full tunnel client mode deliversa lightweight, centrally configured and easy-to-support SSL VPN tunneling client that provides network layeraccess to virtually any application. The advantage of SSL VPN comes from its accessibility from almost anyInternet-connected system without needing to install additional desktop software. Cisco SSL AnyConnectVPN allows remote users to access enterprise networks on the Internet through an SSL VPN gateway. Duringthe establishment of the SSL VPN with the gateway, the Cisco AnyConnect VPN Client is downloaded andinstalled on the remote user equipment (laptop, mobile, PDA, etc. ), and the tunnel connection is establishedwhen the remote user logs into the SSL VPN gateway. The tunnel connection is determined by the grouppolicy configuration. By default, the Cisco AnyConnect VPN Client is removed from the client PC after theconnection is closed. However, you have the option to keep the Cisco AnyConnect VPN Client installed onthe client equipment.Cisco SSL AnyConnect VPN easy access to services within the company’s network and simplifies the VPNconfiguration on the SSL VPN gateway, reducing the overhead for system administrators.SSL VPN CLI ConstructsSSL ProposalSSL proposal specifies the cipher suites that are supported. Each cipher suite defines a key exchange algorithm,a bulk encryption algorithm, a MAC algorithm. One of the cipher suites configured would be chosen fromthe client's proposal during SSL negotiation. If the intersection between the client proposed suites and configuredsuites is a null set, the negotiation terminates. Ciphers are currently selected based on the client's priority.The SSL proposal is used in SSL handshake protocol for negotiating encryption and decryption. The defaultSSL proposal is used with SSL policy in the absence of any user-defined proposal. The default proposal hasciphers in the order as show below:protection rsa-aes256-sha1 rsa-aes128-sha1 rsa-3des-ede-sha1 rsa-3des-ede-sha1SSL VPN3
SSL VPNSSL PolicySSL PolicySSL policy defines the cipher suites to be supported and the trust point to be used during SSL negotiation.SSL policy is a container of all the parameters used in the SSL negotiation. The policy selection would bedone by matching the session parameters against the parameters configured under the policy. There is nodefault policy. Every policy is associated with a proposal and a trustpoint.SSL ProfileThe SSL VPN profile defines authentication and accounting lists. Profile selection depends on policy andURL values. Profile may, optionally, be associated with a default authorization policy.The following rules apply: The policy and URL must be unique for an SSL VPN profile. At least one authorization method must be specified to bring up the session. The three authorization types namely user, group and cached may coexist. There is no default authorization. The order of precedence for authorization is user authorization, cache authorization, and groupauthorization. If group authorization override is configured the order of precedence is group authorization,user authorization, and cache authorization.SSL Authorization PolicyThe SSL authorization policy is a container of authorization parameters that are pushed to the remote clientand are applied either locally on the virtual-access interface or globally on the device. The authorization policyis referred from the SSL VPN profile.SSL VPN MIBThe SSL VPN MIB represents the Cisco implementation-specific attributes of a Cisco entity that implementsSSL VPN. The MIB provides operational information in Cisco’s SSL VPN implementation by managing theSSLVPN, trap control, and notification groups. For example, the SSL VPN MIB provides the number ofactive SSL tunnels on the device.How to Configure SSL VPNConfiguring SSL ProposalSUMMARY STEPS1.2.3.4.5.SSL VPN4enableconfigure terminalcrypto ssl proposal proposal-nameprotectionend
SSL VPNConfiguring SSL Proposal6. show crypto ssl proposal [proposal name]DETAILED STEPSStep 1Command or ActionPurposeenableEnables privileged EXEC mode.Example: Enter your password if prompted.Device enableStep 2configure terminalEnters global configuration mode.Example:Device# configure terminalStep 3crypto ssl proposal proposal-nameExample:Defines an SSL proposal name, and enters crypto SSLproposal configuration mode.Device(config)# crypto ssl proposal proposal1Step 4protectionSpecifies one or more cipher suites that are as follows:Example: )# protectionrsa-3des-ede-sha1 rsa-aes128-sha1 rsa-aes128-sha1 rsa-aes256-sha1 rsa-rc4128-md5Step 5Exits SSL proposal configuration mode and returns toprivileged EXEC # endStep 6show crypto ssl proposal [proposal name](Optional) Displays the SSL proposal.Example:Device# show crypto ssl proposalWhat to do nextAfter configuring the SSL proposal, configure the SSL policy. For more information, see the “ConfiguringSSL Policy” section.NoteSSL VPN will not work if ip http secure-server is enabled.SSL VPN5
SSL VPNConfiguring SSL PolicyConfiguring SSL PolicySUMMARY STEPS1.2.3.4.5.6.7.8.9.10.enableconfigure terminalcrypto ssl policy policy-nameip address local ip-address [vrf vrf-name] [port port-number] [standby redundancy-name]ip interface local interface-name [vrf vrf-name] [port port-number] [standby redundancy-name]pki trustpoint trustpoint-name signssl proposal proposal-nameno shutendshow crypto ssl policy [policy-name]DETAILED STEPSStep 1Command or ActionPurposeenableEnables privileged EXEC mode.Example: Enter your password if prompted.Device enableStep 2configure terminalEnters global configuration mode.Example:Device# configure terminalStep 3crypto ssl policy policy-nameExample:Defines an SSL policy name and enters SSL policyconfiguration mode.Device(config)# crypto ssl policy policy1Step 4ip address local ip-address [vrf vrf-name] [portport-number] [standby redundancy-name]Specifies the local IP address to start the TCP listener.NoteExample:Either this command or the ip interface localcommand is mandatory.Device(config-crypto-ssl-policy)# ip address local10.0.0.1 port 446Step 5ip interface local interface-name [vrf vrf-name] [portport-number] [standby redundancy-name]Example:Specifies the local interface to start the TCP listener.NoteEither this command or the ip address localcommand is mandatory.Device(config-crypto-ssl-policy)# ip interfacelocal FastEthernet redundancy1Step 6pki trustpoint trustpoint-name signExample:SSL VPN6(Optional) Specifies the trustpoint to be used to send servercertificate during an SSL handshake.
SSL VPNConfiguring an SSL ProfileCommand or ActionPurposeDevice(config-crypto-ssl-policy)# pki trustpoint Notetp1 signStep 7ssl proposal proposal-nameExample:Step 8If this command is not specified, a defaultself-signed trustpoint is used. If there is nodefault self-signed trustpoint, the system createsa default self-signed certificate.(Optional) Specifies the cipher suites to be selected duringan SSL handshake.If a proposal is not specified, the defaultproposal is used.Device(config-crypto-ssl-policy)# ssl proposalpr1Noteno shutStarts the TCP listener based on the icy)# no shutStep 9Exits SSL policy configuration mode and returns toprivileged EXEC mode.endExample:Device(config-crypto-ssl-policy)# endStep 10show crypto ssl policy [policy-name](Optional) Displays the SSL policies.Example:Device# show crypto ssl policyWhat to do nextAfter configuring the SSL policy, configure the SSL profile to match the policy. For more information, seethe “Configuring SSL Profile” section.Configuring an SSL ProfileSUMMARY STEPS1.2.3.4.5.6.7.8.9.10.11.12.enableconfigure terminalcrypto ssl profile profile-nameaaa accounting user-pass list list-nameaaa authentication user-pass list list-nameaaa authorization group [override] user-pass list aaa-listname aaa-usernameaaa authorization user user-pass {cached list aaa-listname aaa-username}match policy policy-namematch url url-nameno shutendshow crypto ssl profile [profile-name]SSL VPN7
SSL VPNConfiguring an SSL ProfileDETAILED STEPSStep 1Command or ActionPurposeenableEnables privileged EXEC mode.Example: Enter your password if prompted.Device enableStep 2configure terminalEnters global configuration mode.Example:Device# configure terminalStep 3crypto ssl profile profile-nameExample:Defines an SSL profile and enters SSL profileconfiguration mode.Device(config)# crypto ssl profile profile1Step 4aaa accounting user-pass list list-nameExample:Specifies authentication, authorization, and accounting(AAA) accounting method list.Device(config-crypto-ssl-profile)# aaa accountinguser-pass list list1Step 5aaa authentication user-pass list list-nameSpecifies the AAA authentication method list.Example:Device(config-crypto-ssl-profile)# aaaauthentication user-pass list list2Step 6aaa authorization group [override] user-pass listaaa-listname aaa-usernameSpecifies the AAA method list and username for groupauthorization.Example: group—Specifies group authorization.Device(config-crypto-ssl-profile)# aaaauthorization group override user-pass list list1user1 override—(Optional) Specifies that attributes fromgroup authorization should take precedence whilemerging attributes. By default, user attributes takeprecedence. user-pass—Specifies the user-password basedauthorization. aaa-listname—AAA method list name. aaa-username—Username that must be used in theAAA authorization request. Refers to SSLauthorization policy name defined on the device.Step 7aaa authorization user user-pass {cached listaaa-listname aaa-username}Example: user—Specifies user authorization.Device(config-crypto-ssl-profile)# aaaauthorization user user-pass list list1 user1 user-pass— Specifies the user-password basedauthorization.SSL VPN8Specifies the AAA method list and username for userauthorization.
SSL VPNConfiguring the SSL Authorization PolicyCommand or ActionPurpose cached—Specifies that the attributes received duringEAP authentication or obtained from the AAApreshared key must be cached. aaa-listname—AAA method list name. aaa-username—Specifies the username that must beused in the AAA authorization request.Step 8match policy policy-nameExample:Uses match statements to select an SSL profile for a peerbased on the SSL policy name.Device(config-crypto-ssl-profile)# match addresspolicy policy1Step 9match url url-nameExample:Uses match statements to select an SSL profile for a peerbased on the URL.Device(config-crypto-ssl-profile)# match urlwww.abc.comStep 10Specifies the profile cannot be shut until the policyspecified in the match policy command is in use.no shutExample:Device(config-crypto-ssl-profile)# no shutStep 11Exits SSL profile configuration mode and returns toprivileged EXEC mode.endExample:Device(config-crypto-ssl-profile)# endStep 12show crypto ssl profile [profile-name](Optional) Displays the SSL profile.Example:Device# show crypto ssl profileConfiguring the SSL Authorization PolicyPerform this task to configure the SSL authorization policy.SUMMARY STEPS1.2.3.4.5.6.7.enableconfigure terminalcrypto ssl authorization policy policy-namebanner banner-textclient profile profile-namedef-domain domain-nameDo one of the following: dns primary-server [secondary-server] ipv6 dns primary-server [secondary-server]SSL VPN9
SSL VPNConfiguring the SSL Authorization al {client server} intervalhomepage homepage-textinclude-local-lanipv6 prefix prefixkeepalive secondsmodule module-namemsie-proxy exception exception-namemsie-proxy option {auto bypass none}msie-proxy server {ip-address dns-name}mtu bytesnetmask maskDo one of the following: pool name ipv6 pool name20.21.rekey time secondsDo one of the following: route set access-list acl-name ipv6 route set access-list l-disconnectsplit-dns stringtimeout {disconnect seconds idle seconds session seconds}wins primary-server [secondary-server]endshow crypto ssl authorization policy [policy-name]DETAILED STEPSStep 1Command or ActionPurposeenableEnables privileged EXEC mode.Example: Enter your password if prompted.Device enableStep 2configure terminalEnters global configuration mode.Example:Device# configure terminalStep 3crypto ssl authorization policy policy-nameExample:Specifies the SSL authorization policy and enters SSLauthorization policy configuration mode.Device(config)# crypto ssl authorization policypolicy1Step 4banner banner-textExample:SSL VPN10Specifies the banner. The banner is displayed on successfultunnel set up.
SSL VPNConfiguring the SSL Authorization PolicyCommand or # banner Thisis SSL VPN tunnel. NOTE: DO NOT dial emergencyresponse numbers (e.g. 911,112) fromsoftware telephony clients. Your exact locationand the appropriate emergency response agency maynot be easily identified.Step 5client profile profile-nameExample:Specifies the client profile. The profile must already bespecified using the crypto ssl profile command.Device(config-crypto-ssl-auth-policy)# clientprofile profile1Step 6def-domain domain-nameExample:Specifies the default domain. This parameter specifies thedefault domain that the client can use.Device(config-crypto-ssl-auth-policy)# def-domainexample.comStep 7Do one of the following: dns primary-server [secondary-server] ipv6 dns primary-server -auth-policy)# dns198.51.100.1 198.51.100.100Specifies an IPv4-or IPv6-based address for the primaryand secondary Domain Name Service (DNS) servers. primary-server—IP address of the primary DNSserver. secondary-server—(Optional) IP address of thesecondary DNS y)# ipv6 dns2001:DB8:1::1 2001:DB8:2::2Step 8dpd-interval {client server} cy)#dpd-interval client 1000Configures Dead Peer Detection (DPD).globally for theclient or server. client—DPD for the client mode. The default valueis 300 (five minutes). server—DPD for the server mode. The default valueis 300. interval—Interval, in seconds. The range is from 5to 3600.Step 9homepage homepage-textSpecifies the SSL VPN home page URL.Example:Device(config-crypto-ssl-auth-policy)# homepagehttp://www.abc.comStep 10include-local-lanExample:Permits the remote user to access resources on a local LAN,such as a network ude-local-lanStep 11ipv6 prefix prefixDefines the IPv6 prefix for IPv6 addresses.SSL VPN11
SSL VPNConfiguring the SSL Authorization PolicyCommand or ActionExample:Purpose prefix—Prefix length. The range is from 1 to 128.Device(config-crypto-ssl-auth-policy)# ipv6 prefix64Step 12keepalive secondsExample:Enables setting the minimum, maximum, and defaultvalues for keepalive, in seconds.Device(config-crypto-ssl-auth-policy)# keepalive500Step 13module olicy)# module ginaEnables the server gateway to download the appropriatemodule for VPN to connect to a specific group. dart—Downloads the AnyConnect Diagnostic andReporting Tool (DART) module. gina—Downloads the Start Before Logon (SBL)module.Step 14msie-proxy exception exception-nameExample:The DNS name or the IP address specified in theexception-name argument that must not be sent via theproxy.Device(config-crypto-ssl-auth-policy)# msie-proxyexception 198.51.100.2Step 15msie-proxy option {auto bypass # msie-proxyoption bypassSpecifies the proxy settings for the Microsoft InternetExplorer browser. The proxy settings are required tospecify an internal proxy server and to route the browsertraffic through the proxy server when connecting to thecorporate network. auto—Browser is configured to auto detect proxyserver settings. bypass—Local addresses bypass the proxy server. none—Browser is configured to not use the proxyserver.Step 16msie-proxy server {ip-address dns-name}Example:The IP address or the DNS name, optionally followed bythe port number, of the proxy server.Device(config-crypto-ssl-auth-policy)# msie-proxy Noteserver 198.51.100.2Step 17mtu bytesExample:SSL VPN12This command is required if the msie-proxyoption bypass command is specified.(Optional) Enables setting the minimum, maximum, anddefault MTU value.
SSL VPNConfiguring the SSL Authorization PolicyStep 18Command or # mtu 1000Notenetmask maskSpecifies the netmask of the subnet from which the IPaddress is assigned to the y)# netmask255.255.255.0Step 19Do one of the following: pool name ipv6 pool nameExample:Device(config-crypto-ssl-auth-policy)# pool abcThe value specified in this command overridesthe default MTU specified in Cisco AnyConnectSecure client configuration. If not specified, thevalue specified Cisco AnyConnect Secure clientconfiguration is the MTU value. If thecalculated MTU is less than the MTU specifiedin this command, this command is ignored. mask—Subnet mask address.Defines a local IPv4 or IPv6 address pool for assigning IPaddresses to the remote access client. name—Name of the local IP address pool.NoteThe local IP address pool must already bedefined using the ip local pool cy)# ipv6 poolipv6poolStep 20rekey time secondsExample:Specifies the rekey interval, in seconds. The default valueis 3600.Device(config-crypto-ssl-auth-policy)# rekey time1110Step 21Do one of the following: route set access-list acl-name ipv6 route set access-list access-list-nameEstablishes IPv4 or IPv6 routes via the access list that mustbe secured through tunnels. acl-name—Access list # route setaccess-list acl1Example:Device(config-crypto-ssl-auth-policy)# ipv6 routeset access-list acl1Step 22smartcard-removal-disconnectExample:Enables smartcard removal disconnect and specifies thatthe client should terminate the session when the smart cardis tcard-removal-disconnectStep 23split-dns stringExample:Allows you to specify up to ten split domain names, whichthe client should use for private networks.Device(config-crypto-ssl-auth-policy)# split-dnsexample.com example.netSSL VPN13
SSL VPNVerifying SSL VPN ConfigurationsStep 24Command or ActionPurposetimeout {disconnect seconds idle seconds sessionseconds}Specifies the timeout, in cy)# timeoutdisconnect 10000 disconnect seconds—Specifies the retry duration, inseconds, for Cisco AnyConnect client to reconnectto the server gateway. The default value is 0. idle seconds—Specifies the idle timeout, in seconds.The default value is 1800 (30 minutes). session seconds—Specifies the session timeout, inseconds. The default value is 43200 (12 hours).Step 25wins primary-server -auth-policy)# wins203.0.113.1 203.0.113.115Specifies the internal Windows Internet Naming Service(WINS) server addresses. primary-server—IP address of the primary WINSserver. secondary-server—(Optional) IP address of thesecondary WINS server.Step 26Exits SSL authorization policy configuration mode andreturns to privileged EXEC cy)# endStep 27show crypto ssl authorization policy [policy-name](Optional) Displays the SSL authorization y)# show cryptossl authorization policyVerifying SSL VPN ConfigurationsThis section describes how to use show commands to verify the SSL VPN configurations:SUMMARY STEPS1.2.3.4.5.6.7.8.SSL VPN14enableshow crypto ssl proposal [name]show crypto ssl policy [name]show crypto ssl profile [name]show crypto ssl authorization policy [name]show crypto ssl session {user user-name profile profile-name}show crypto ssl stats [profile profile-name] [tunnel] [detail]clear crypto ssl session {profile profile-name user user-name}
SSL VPNVerifying SSL VPN ConfigurationsDETAILED STEPSStep 1enableExample:Device enableEnables privileged EXEC mode. Enter your password if prompted.Step 2show crypto ssl proposal [name]Example:Device# show crypto ssl proposalSSL Proposal: sslpropProtection: 3DES-SHA1Displays the SSL proposal.Step 3show crypto ssl policy [name]Example:Device# show crypto ssl policySSL Policy: sslpolicyStatus: ACTIVEProposal: sslpropIP Address : 10.78.106.23Port: 443fvrf: 0Trust Point: TP-self-signed-1183786860Redundancy : noneDisplays the SSL policies.Step 4show crypto ssl profile [name]Example:Device# show crypto ssl profileSSL Profile: sslprofileStatus: ACTIVEMatch Criteria:URL: nonePolicy:sslpolicyAAA accounting List: localAAA authentication List :noneAAA authorization cached :trueAAA authorization user List:defaultAAA authorization user name: sslauthAAA authorization group List:noneAAA authorization group name: noneAuthentication Mode: user credentialsInterface: SSLVPN-VIF1Status: ENABLEDisplays the SSL profile.SSL VPN15
SSL VPNVerifying SSL VPN ConfigurationsStep 5show crypto ssl authorization policy [name]Example:Device# show crypto ssl authorization policySSL Auth Policy: sslauthV4 Parameter:Address Pool: SVC POOLNetmask: 255.255.255.0Route ACL : split-includeBanner: noneHome Page: noneIdle timeout: 300Disconnect Timeout: 0Session Timeout: 43200Keepalive Interval: 0DPD Interval: 300RekeyInterval: 0Method : noneSplit DNS: noneDefault domain: noneProxy SettingsServer: noneOption: NULLException(s): noneAnyconnect Profile Name :SBL Enabled: NOMAX MTU: 1406Smart CardRemoval Disconnect: NODisplays the SSL authorization policy.Step 6show crypto ssl session {user user-name profile profile-name}Example:Device# show crypto ssl session user LABSession Type: Full TunnelClient User-Agent : AnyConnect Windows 3.0.08057UsernamePublic IPProfileLast-UsedSession TimeoutDPD GW TimeoutAddress PoolRekey TimeLease DurationTunnel IPRx IP PacketsCSTP StartedCSTP DPD-Req sentMsie-ProxyServerMsie-ExceptionClient Ports::::::::::::::::LABNum Connection : 172.163.209.245sslprofilePolicy Group: sslauth00:00:02Created: *00:58:44.219 PDT Thu Jul 25 201343200Idle Timeout: 300300DPD CL Timeout : 300sslvpn-poolMTU Size: 14060Rekey Method:4320050.1.1.2Netmask: 255.255.255.00Tx IP Packets : 12500:01:12Last-Received : 00:00:020Virtual Access : 0NoneMsie-PxyPolicy : Disabled34552Device# show crypto ssl session profile sslprofileSSL profile name: sslprofileClient Login Name Client IP AddressSSL VPN16No of ConnectionsCreatedLast Used
SSL VPNVerifying SSL VPN ConfigurationsLAB72.163.209.2451Error receiving show session info from remote cores00:00:3300:00:00Displays SSL VPN session information.Step 7show crypto ssl stats [profile profile-name] [tunnel] [detail]Example:Device# show crypto ssl statsSSLVPN Global statistics:Active connections:Peak connections:Authentication failures :VPN session timeout:User cleared VPN sessions:Connect succeed:Reconnect succeed:IP Addr Alloc Failed:Route Insertion Failed:IPV6 Addr Alloc Failed:IPV6 Route Insert Failed :IPV6 Hash Insert Failed :IPV6 STC Alloc Failed:in CSTP control:in CSTP data:01211010000000521AAA pending reqsPeak time: 0: 1w6dVPN idle timeoutLogin DeninedConnect failedReconnect failedVA creation failed:::::out CSTP controlout CSTP data: 3: 8Device# show crypto ssl stats tunnel profile prf1SSLVPN Profile name : prf1Tunnel Statistics:Active connections: 0Peak connections: 0Peak timeConnect succeed: 0Connect failedReconnect succeed: 0Reconnect failedDPD timeout: 0Clientin CSTP frames: 0in CSTP controlin CSTP data: 0in CSTP bytesout CSTP frames: 0out CSTP controlout CSTP data: 0out CSTP bytescef in CSTP data frames : 0cef in CSTP data bytescef out CSTP data frames : 0cef out CSTP data bytesServerIn IP pkts: 0In IP bytesOut IP pkts: 0Out IP bytes00000: never: 0: 0::::::000000: 0: 0Displays SSL VPN statistics.Step 8clear crypto ssl session {profile profile-name user user-name}Example:Device# clear crypto ssl session sslprofileClears SSL VPN session.SSL VPN17
SSL VPNConfiguration Examples for SSL VPNConfiguration Examples for SSL VPNExample: Specifying the AnyConnect Image and ProfileThe following example shows how to specify the Cisco AnyConnect image and profile.Device enableDevice# configure terminalDevice(config)# crypto vpn anyconnect equence 1Device(config)# crypto vpn anyconnect profile Employee bootflash:/Employee.xmlDevice(config)# endExample: Configuring SSL ProposalThe following example shows how to configure the SSL proposal.Device enableDevice# configure terminalDevice(config)# crypto ssl prop
Configuring SSLPolicy SUMMARYSTEPS 1. enable 2. configure terminal 3. crypto ssl policy policy-name 4. ip address local ip-address [vrf vrf-name][port port-number][standby redundancy-name] 5. ip interface local interface-name [vrf vrf-name][port port-number][standby redundancy-name] 6. pki trustpoint trustpoint-name sign 7. ssl proposal proposal-name 8. no shut
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
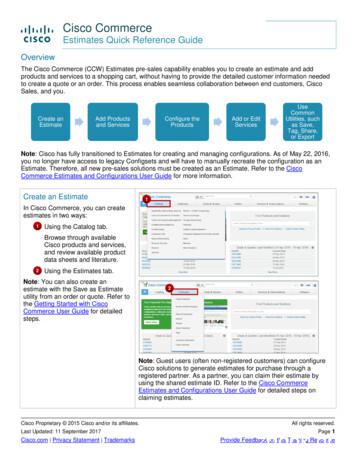
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b
Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unified Computing System (Cisco UCS), Cisco UCS B-Series Blade Servers, Cisco UCS C-Series Rack Servers, Cisco UCS S-Series Storage Servers, Cisco UCS Manager, Cisco UCS
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base