Cisco Identity Services Engine (ISE) Security Target
Cisco ISEMarch 2017Cisco Identity Services Engine(ISE) Security TargetVersion 0.8March 20171
Cisco ISEMarch 2017Table of Contents1SECURITY TARGET INTRODUCTION . 61.1 ST and TOE Reference . 61.2 Acronyms and Abbreviations . 71.3 Terminology . 71.4 TOE Overview . 81.4.1TOE Product Type . 81.4.2Supported Non-TOE Hardware/ Software/ Firmware . 91.5 TOE DESCRIPTION . 91.6 TOE Evaluated Configuration . 101.7 Physical Scope of the TOE. 121.8 Logical Scope of the TOE . 131.8.1Security Audit . 131.8.2Cryptographic Support . 131.8.3Identification and Authentication . 141.8.4Security Management . 151.8.5Protection of the TSF . 151.8.6TOE Access . 161.8.7Trusted Path/Channels . 161.9 Excluded Functionality . 162CONFORMANCE CLAIMS. 172.1 Common Criteria Conformance Claim . 172.2 Protection Profile Conformance . 172.3 Protection Profile Conformance Claim Rationale . 172.3.1TOE Appropriateness. 172.3.2TOE Security Problem Definition Consistency . 172.3.3Statement of Security Requirements Consistency . 183SECURITY PROBLEM DEFINITION . 193.13.23.34SECURITY OBJECTIVES . 234.14.25Assumptions . 19Threats . 20Organizational Security Policies . 22Security Objectives for the TOE . 23Security Objectives for the Environment . 23SECURITY REQUIREMENTS . 255.1 Conventions. 255.2 TOE Security Functional Requirements . 255.2.1Security Audit (FAU) . 275.2.2Cryptographic Support (FCS) . 315.2.3Identification and Authentication (FIA) . 355.2.4Security Management (FMT) . 375.2.5Protection of the TSF (FPT) . 385.2.6TOE Access (FTA) . 395.2.7Trusted Path/Channel (FTP) . 395.3 TOE SFR Dependencies Rationale . 402
Cisco ISEMarch 20175.4 Security Assurance Requirements . 405.4.1SAR Requirements. 405.4.2Security Assurance Requirements Rationale . 415.5 Assurance Measures . 416TOE SUMMARY SPECIFICATION . 426.17TOE Security Functional Requirement Measures . 42Annex A: Additional Information. 567.1 Key Protection and Zeroization . 568Annex B: References . 573
Cisco ISEMarch 2017List of TablesTABLE 1: ST AND TOE IDENTIFICATION . 6TABLE 2: ACRONYMS. 7TABLE 3: ACRONYMS. 7TABLE 4: IT ENVIRONMENT COMPONENTS . 9TABLE 5: TOE MODELS . 12TABLE 6: CAVP CERTIFICATE REFERENCES . 13TABLE 7: EXCLUDED FUNCTIONALITY . 16TABLE 8: PROTECTION PROFILES . 17TABLE 9: TOE ASSUMPTIONS . 19TABLE 10: THREATS . 20TABLE 11: ORGANIZATIONAL SECURITY POLICIES . 22TABLE 12: SECURITY OBJECTIVES FOR THE ENVIRONMENT . 23TABLE 13: SECURITY FUNCTIONAL REQUIREMENTS . 25TABLE 14: AUDITABLE EVENTS . 27TABLE 15: ASSURANCE MEASURES . 40TABLE 16: ASSURANCE MEASURES . 41TABLE 17: HOW TOE SFRS ARE MET . 42TABLE 18: TOE KEY ZEROIZATION . 56TABLE 19: REFERENCES . 574
Cisco ISEMarch 2017DOCUMENT INTRODUCTIONPrepared By:Cisco Systems, Inc.170 West Tasman Dr.San Jose, CA 95134This document provides the basis for an evaluation of a specific Target of Evaluation (TOE), theCisco Identity Services Engine (ISE) v2.0. This Security Target (ST) defines a set of assumptionsabout the aspects of the environment, a list of threats that the product intends to counter, a set ofsecurity objectives, a set of security requirements, and the IT security functions provided by theTOE which meet the set of requirements. Administrators of the TOE will be referred to asadministrators, Security Administrators, TOE administrators, semi-privileged, privilegedadministrators, and security administrators in this document.5
Cisco ISEMarch 2017SECURITY TARGET INTRODUCTION1The Security Target contains the following sections: Security Target Introduction [Section 1]Conformance Claims [Section 2]Security Problem Definition [Section 3]Security Objectives [Section 4]IT Security Requirements [Section 5]TOE Summary Specification [Section 6]Rationale [Section 7]The structure and content of this ST comply with the requirements specified in the CommonCriteria (CC), Part 1, Annex A, and Part 3, Chapter 4.1.1ST and TOE ReferenceThis section provides information needed to identify and control this ST and its TOE.Table 1: ST and TOE IdentificationST TitleCisco Identity Services Engine (ISE) v2.0 Security TargetST Version0.8Publication DateMarch 2017Vendor and ST AuthorCisco Systems, Inc.TOE ReferenceCisco Identity Services Engine (ISE) v 2.0TOE Models ISE 3400 series: SNS-3415 and SNS-3495;ISE 3500 series: SNS-3515 and SNS-3595TOE Software VersionISE v2.0, running on Cisco Application Deployment Engine (ADE)Release 2.4 operating system (ADE-OS)KeywordsAAA, Audit, Authentication, Encryption, NAC, Profiling, NetworkDevice6
Cisco ISE1.2March 2017Acronyms and AbbreviationsThe following acronyms and abbreviations are used in this Security Target:Table 2: AcronymsAcronyms 1.3DefinitionAdministration, Authorization, and AccountingAdvanced Encryption StandardCommon Criteria for Information Technology Security EvaluationCommon Evaluation Methodology for Information Technology SecurityCommand Line InterfaceConfiguration ManagementDiffie-HellmanFederal Information Processing StandardHashed Message Authentication CodeHyper-Text Transport Protocol SecureInternet ProtocolInformation TechnologyLightweight Directory Access ProtocolNetwork Access ControlOperating SystemOrganizational Security PoliciesProtection ProfileCollaborative Protection Profile for Network Devices (NDcPP)Random Number GeneratorSecurity Group AccessSecurity Group tagsSecure Shell (version 2)Security TargetTransport Control ProtocolTransport Layer SecurityTarget of EvaluationTOE Security FunctionVirtual Private NetworkWireless LAN ControllerTerminologyThe following terms are used in this Security Target:Table 3: AcronymsTermEndpointsDefinitionAn endpoint role is a set of permissions that determine the tasks that the devicecan perform or services that can be accessed on the Cisco ISE network. Endpointscan be users, personal computers, laptops, IP phones, printers, or any other devicesupported on the ISE network7
Cisco ISEMarch 2017TermDefinitionGroup memberA group member role is a set of permissions that determine the tasks a user (byvirtue of being a member of a group) can perform or the services that can beaccessed on the ISE network.NodeA node is an individual instance of ISE.PersonaThe persona of a node determines that service provided by a node. The TOE canbe configure as any of the following personas: Administration – allows the user to perform all of the administrativeoperations on the TOE. All of the authentication, authorization, auditing,and so on are managed. There can be one or two maximum nodeinstances running the Administration persona and can take any one of thefollowing roles; standalone, primary, or secondary. Policy Service – provides network access, posture, guest services, clientprovisioning, and profiling services. This persona evaluates the policiesand makes all of the decisions. There can be one or more instance of anode configured as a Policy Service. Monitoring – functions as the log collector and stores log messages fromall of the Administration and Policy Service personas. There can be oneor two node instances running the Monitoring persona.RoleThe role identity determines of the TOE is a standalone, primary, or secondarynode.ServiceA service is a specific feature that a persona provides, such as network access,posture, security group access, and monitoringUserA user role is a set of permissions that determine what tasks a user can perform orwhat services can be accessed on the ISE network. The user identity includesusername, password, and group association.1.4TOE OverviewThe TOE is an identity and access control platform that enables organizations to enforcecompliance and security within the network infrastructure. The TOE includes four hardwareoptions: Cisco Identity Services Engine Appliance 3415, Cisco Identity Services Engine Appliance3495, Cisco Identity Services Engine Appliance 3515 and Cisco Identity Services EngineAppliance 3595.1.4.1 TOE Product TypeThe Cisco Identity Services Engine (ISE) is a network device identity, authentication, and accesscontrol policy platform that enables enterprises to enforce compliance, enhance infrastructuresecurity, and streamline service operations. ISE allows enterprises to gather real-time contextualinformation from networks, users, and devices. The administrator can then use that information tomake proactive governance decisions by tying identity to various network elements including8
Cisco ISEMarch 2017access switches, wireless LAN controllers (WLCs), virtual private network (VPN) gateways, anddata center switches.1.4.2 Supported Non-TOE Hardware/ Software/ FirmwareThe TOE supports (in some cases optionally) the following hardware, software, andfirmware in its environment:Table 4: IT Environment ComponentsComponentAdministrative ConsoleRequiredYesUsage/Purpose Description for TOEperformanceThis console provides the connection to the ISEappliance for administration and management. Theconsole can connect directly to ISE or over thenetwork via a browser or SSHv2 connection.The TOE supports the following browsers: Mozilla Firefox version 39 and later Google Chrome version 43 and later Microsoft Internet Explorer 9.x, 10.x and 11.x - Ifusing Internet Explorer 10.x, enable TLS 1.1 andTLS 1.2, and disable SSL 3.0 and TLS 1.0(Internet Options Advanced.Remote AuthenticationStoreNoThe TOE supports local authentication orauthentication via a remote authentication store,including LDAP and Active Directory.Syslog TargetYesThe TOE must offload syslogs to an external entity,which can be another iteration of ISE or a syslogserver that supports TLS-protected transfer.1.5 TOE DESCRIPTIONThis section provides an overview of the Cisco Identity Services Engine (ISE) v2.0 Target ofEvaluation (TOE) and a brief description of the capabilities of the ISE product. ISE is aconsolidated policy-based access control system that combines authentication, authorization,accounting (AAA), posture, profiler, and guest management in one appliance.There are two types of license of ISE - Base and Advanced. For the purposes of this evaluation, allclaimed functionality is included in both license types. The Base license includes AAA services,guest lifecycle management, compliance reporting and end-to-end monitoring and troubleshooting.The Advanced license expands on the Base license and enables policy decision based on user anddevice compliance. The Advanced license features include device profiling, posture services, andsecurity group access enforcement capabilities.9
Cisco ISEMarch 2017There are seven policy models that can be configured in Cisco ISE to determine how networkaccess is granted to the users requesting access to the network resources. The policies are a set ofconditions that must be met in order for access to be granted. The policy models are as follows: Authentication Policy – defines the protocols that are used to communicate with thenetwork devices, the identity sources used for authentication, and the failover options. Authorization Policy – defines the authorization policies and profiles for specific usersand groups of users that have access to the network resources. The policies associate ruleswith specific user and group identities to create the corresponding profiles. Wheneverthese rules match the configured attributes, the corresponding authorization profile thatgrants permission is returned by the policy, network access is authorized accordingly. Profiler Policy - provides the unique functionality in discovering, locating, anddetermining the capabilities of all the attached endpoints (a.k.a identities) on the network.The profiler collects an attribute or a set of attributes of all the endpoints on the networkand classifies them according to their profiles. Client Provisioning Policy – like the Profiler policy, the TOE looks at various elementswhen classifying the type of login session through which users access the internal network,including: Client machine operating system and version Client machine browser type and version Group to which the user belongs Condition evaluation results (based on applied dictionary attributes)After Cisco ISE classifies a client machine, it uses client provisioning resourcepolicies to ensure that the client machine is set up with an appropriate agent version,up-to-date compliance modules for antivirus and antispyware vendor support, andcorrect agent customization packages and profiles, if necessary. Posture Policy - allows the administrator to check the state (posture) for all the endpointsthat are connecting to the network with the corporate security policies for compliancebefore clients are granted access to protected areas of the network. Guest Management – allows guest (visitors, contractors, consultants, or customers) toperform an HTTP or HTTPS login to access a network whether that network is a corporateintranet or the public Internet. The ISE Guest service allows any user with privileges(sponsor) to create temporary guest accounts and to sponsor guests. When a guest userfirst attaches to the local network, either through a wireless or wired connection, the useris placed in a segregated network with limited access. The ISE Guest service supportsdefault and customizable guest login portals. The entire process, from user accountcreation to guest network access, is stored for audit and reporting purposes. It is noted thatthe guest account is only active for the time specified when the account is created. Security Group Access Policy - establishes clouds of trusted network devices to buildsecure networks. Each device in the ISE SGA cloud is authenticated by its neighbors(peers). Communication between the devices in the SGA cloud is secured with acombination of encryption, message integrity checks, and data-path replay protectionmechanisms.1.6 TOE Evaluated ConfigurationThe ISE architecture supports both stand-alone and distributed deployments. In a distributedconfiguration, one machine assumes the primary role and another “backup” machine assumes thesecondary role.10
Cisco ISEMarch 2017The administrator can deploy ISE nodes with one or more of the Administration, Monitoring, andPolicy Service personas, each one performing a different vital part in the overall network policymanagement topology. Installing ISE with an Administration persona allows the administrator toconfigure and manage the network from a centralized portal.The TOE architecture includes the following components: Nodes and persona types – A Cisco ISE node can assume the Administration, PolicyService, or Monitoring personas. It can provide various services based on the persona thatit assumes. Network resources – The clients that are provided authentication services by ISE Endpoints – Devices through which the administrators can log in and manage the TOE.Figure 1: Typical TOE DeploymentThe evaluated configuration will include one or more ISE instances in a network. A typicaldeployment will include network devices utilizing the ISE authentication, authorization andaccounting (AAA) features, remote administrator, local administrative console and a remoteauthentication store. Both the remote administrator and local administrator console capabilitiesmust be supported.11
Cisco ISEMarch 20171.7 Physical Scope of the TOEThe Cisco ISE software runs on the Cisco Application Deployment Engine (ADE) Release 2.4operating system (ADE-OS). The Cisco ADE-OS and Cisco ISE software run on a dedicated CiscoISE 3400/3500 Series appliance. All models include the same security functionality.Table 5: TOE ModelsHardwareModelCisco IdentityServices EngineAppliance 3415Cisco IdentityServices EngineAppliance 3495Cisco IdentityServices EngineAppliance 3515Cisco IdentityServices EngineAppliance 3595ProcessorCisco UCSC220M3, SingleIntel Xeon E52609 4 coreprocessorCisco UCSC220M3, DualIntel Xeon E52609 4 coreprocessor (8 corestotal)Cisco UCSC220M4, SingleIntel Xeon E5-26206 core processorCisco UCS 220M4,Dual Intel XeonE5-2640 8 coreprocessorMemory16 GB32 GB16 GB64 GBHard disk1x600Gb disk2x600Gb disk1x600Gb disk4x600Gb diskRAIDYes (SoftwareRAID level 0(single drivestriped))Yes (RAID 1)Yes (SoftwareRAID level 0(single drivestriped))Yes (RAID 0 1)Expansion slots- Two PCIeslots (on a risercard)- Two PCIe slots(on a riser card)- Two PCIe slots(on a riser card)- Two PCIe slots(on a riser card)Serial port (RJ45 Connector)1111USB 2.0 ports2200USB 3.0 ports00221-GB EthernetManagementPort1111Video ports111112
Cisco ISEMarch 20171.8 Logical Scope of the TOEThe NDcPP-compliant TOE is comprised of several security features. Each of the security featuresidentified above consists of several security functionalities, as identified below.1.2.3.4.5.6.7.Security auditCryptographic supportIdentification and authenticationSecure ManagementProtection of the TSFTOE accessTrusted path/channelsThese features are described in more detail in the subsections below.1.8.1 Security AuditThe TOE’s Audit security function supports audit record generation and review. The TOE providesdate and time information that is used in audit timestamps. The events generated by the TOEinclude indication of the logging starting and stopping, cryptographic operations, attempts to logonto the TOE, all commands/ web-based actions executed by the Security Administrator, and othersystem events.The TOE can store the generated audit data on itself and it can be configured to send syslog eventsto other devices, including other iterations of ISE, using a TLS protected collection method. Logsare classified into various predefined categories. The TOE also provides the capability for theadministrator to customize the logging output by editing the categories with respect to their targets,severity level, etc. The logging categories help describe the content of the messages that theycontain. Access to the logs is restricted only to the Security Administrator, who has no access toedit them, only to copy or delete (clear) them. Audit records are protected from unauthorisedmodifications and deletions.The logs can be viewed by using the Operations - Reports page on the ISE administrationinterface, then select the log from the left side and individual record (message). The log recordincludes the category name, the message class, the message code (type of event), the message text(including a date/time stamp, subject (user) associated with the event, outcome of the event, etc.)and the severity level associated with the message. The previous audit records are overwritten whenthe allocated space for these records reaches the threshold.1.8.2 Cryptographic SupportThe TOE provides cryptography support for secure communications and protection of information.The cryptographic services provided by the TOE include: symmetric encryption and decryptionusing AES; asymmetric key generation; cryptographic key establishment using RSA-based keyestablishment schemes and DH key establishment; digital signature using RSA; cryptographichashing using SHA1 (and other sizes); random bit generation using DRBG and keyed-hash messageauthentication using HMAC-SHA (multiple key sizes). The TOE implements the secure protocols- SSH and TLS/HTTPS on the server side and TLS on the client side. The algorithm certificatereferences are listed in the table below –Table 6: CAVP Certificate References13
Cisco ISEAlgorithmMarch 2017DescriptionMode SupportedCAVP Cert. #AESUsed for symmetricencryption/decryptionCBC (128 and 256 bits)4459SHS (SHA-1, SHA-256and SHA-512)Cryptographichashing servicesByte Oriented3672HMAC (HMAC-SHA-1,HMAC-SHA-256 andHMAC-SHA-512)Keyed hashingservices and softwareintegrity testByte Oriented2959DRBGDeterministic randombit generation servicesin accordance withISO/IEC 18031:2011CTR DRBG (AES 256)1446DSASignature VerificationFIPS PUB 186-4, “DigitalSignature Standard (DSS)”1192RSASignature Verificationand key transportFIPS PUB 186-4 KeyGeneration (2048-bit key)2440CVL – KAS-FFCKey AgreementNIST Special Publication800-56A11681.8.3 Identification and AuthenticationAll users wanting to use TOE services are identified and authenticated prior to being allowed accessto any of the services other than the display of the warning banner. Once a user attempts to accessthe management functionality of the TOE, the TOE prompts the user for a user name and passwordfor remote password-based authentication. The identification and authentication credentials areconfirmed against a local user database or an optional remote authentication store (part of the ITEnvironment). Other authentication options include public key authentication. For remotepassword-based authentication to the administration application, an Active Directory identitysource (remote authentication store) is required in order to perform the association of the credentialsto an ISE Role Based Access Control role. For the SSH public key authentication method, thepublic keys configured by the EXEC CLI command "crypto key import" command will be used forsignature verification. The user information is from the local user database. In all cases only afterthe Administrator presents the correct identification and authentication credentials will access tothe TOE functionality be granted. The TOE uses X.509v3 certificates as defined by RFC 5280 tosupport authentication for TLS/HTTPS connections.The TOE provides the capability to set password minimum length rules. This is to ensure the useof strong passwords in attempts to protect against brute force attacks. The TOE also acceptspasswords composed of a variety of characters to support complex password composition. During14
Cisco ISEMarch 2017authentication, no indication is given of the characters composing the password.1.8.4 Security ManagementThe TOE provides secure administrative services for management of general TOE configurationand the security functionality provided by the TOE. All TOE administration occurs either througha secure session, a terminal server or a local console connection. The TOE provides the ability toperform the following actions: Administer the TOE locally and remotely Configure the access banner Configure the cryptographic services Update the TOE and verify the updates using digital signature capability prior to installingthose updates Specify the time limits of session inactivityAll of these management functions are restricted to the Security Administrator of the TOE, whichcovers all administrator roles (see table for FMT SMR.2 in Section 6.1). The SecurityAdministrators of the TOE are individuals who manage specific type of administrative tasks. TheSecurity Administrators are dependent upon the admin role assigned to them, which limits thenetwork access or tasks they can perform (a role-based access approach).The primary management interface is the HTTPS Cisco ISE user interface. The Cisco ISE userinterface provides an integrated network administration console from which you can managevarious identity services. These services include authentication, authorization, posture, guest,profiler, as well as monitoring, troubleshooting, and reporting. All of these services can be managedfrom a single console window called the Cisco ISE dashboard. The navigation tabs and menus atthe top of the window provide point-and-click access to all other administration features. ACommand Line Interface (CLI) is also supplied for additional administration functionality likesystem-level configuration in EXEC mode and other configuration tasks in configuration mode andto generate operational logs for troubleshooting. This interface can be used remotely over SSHv2.1.8.5 Protection of the TSFThe TOE can terminate inactive sessions after a Security Administrator configurable time-period.Once a session has been terminated the TOE requires the user to re-authenticate to establish a newsession. The TOE provides protection of TSF data (authentication data and cryptographic keys).In addition, the TOE internally maintains the date and time. This date and time is used as the timestamp that is applied to TOE generated audit records. This time can be set manually. The TOE isalso capable of ensuring software updates are from a reliable source. Finally, the TOE performstesting to verify correct operation.In order for updates to be installed on the TOE, an administrator must use the digi
TOE Reference Cisco Identity Services Engine (ISE) v 2.0 TOE Models ISE 3400 series: SNS-3415 and 3495; ISE 3500 series: SNS-3515 and SNS-3595 TOE Software Version ISE v2.0, running on Cisco Application Deployment Engine (ADE) Release 2.4 operating system (ADE-OS) Keywords AAA, Audit, Authenticat
Cisco Identity Services Engine (ISE) 181 Cisco Platform Exchange Grid (pxGrid) 182 Cisco ISE Context and Identity Services 184 Cisco ISE Profiling Services 184 Cisco ISE Identity Services 187 Cisco ISE Authorization Rules 188 Cisco TrustSec 190 Posture Assessment 192 Change of Authorization (CoA) 193 Configuring TACACS Access 196
ISE Search Filters Introduction This document describes how Identitity Service Engine (ISE) and Active Directory (AD) communicate, protocols that are used, AD filters, and flows. Prerequisites Requirements Cisco reccomends a basic knowledge of : ISE 2.x and Active Directory integration . External identity authentication on ISE. Components Used
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
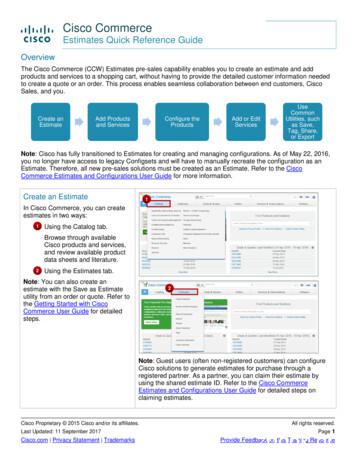
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
2019 HPVC Rules September 23, 2018 Page 2 of 55 . Safety Inspection and Demonstration 16 Safety Video 16 Modifications Affecting Safety 16 Disqualification of Unsafe Vehicles 17 Entry and Registration 17 Team Eligibility 17 Team Member Eligibility and Certification 17 Vehicle Design, Analysis, and Construction 17 Driver Requirement Exceptions 17 Submittal of Final Entries 18 Late Entries 18 .