Release Notes For Cisco Identity Services Engine, Release 2
Release Notes for Cisco Identity Services Engine,Release 2.1Revised: February 18, 2021ContentsThese release notes describe the features, limitations and restrictions (caveats), and related informationfor Cisco Identity Services Engine (ISE), Release 2.1. These release notes supplement the Cisco ISEdocumentation that is included with the product hardware and software release, and cover the followingtopics: NoteThe documentation set for this product strives to use bias-free language. For purposes of thisdocumentation set, bias-free is defined as language that does not imply discrimination based on age,disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, andintersectionality. Exceptions may be present in the documentation due to language that is hardcodedin the user interfaces of the product software, language used based on RFP documentation, orlanguage that is used by a referenced third-party product., page 2 New Features in Cisco ISE, Release 2.1, page 2 Context Visibility, page 4 System Requirements, page 13 Installing Cisco ISE Software, page 17 Upgrading to Release 2.1, page 18 Cisco Secure ACS to Cisco ISE Migration, page 22 Known Limitations in Cisco ISE, Release 2.1, page 22 Features Not Supported in Cisco ISE, Release 2.1, page 26 Cisco ISE License Information, page 26 Deployment Terminology, Node Types, and Personas, page 26 Requirements for CA to Interoperate with Cisco ISE, page 28 Cisco ISE Installation Files, Updates, and Client Resources, page 29Cisco Systems, Inc.www.cisco.com
IntroductionNote Using the Bug Search Tool, page 32 Cisco ISE, Release 2.1.0.474 Patch Updates, page 33 Cisco ISE, Release 2.1 Open Caveats, page 50 Resolved Caveats, page 56 Documentation Updates, page 59 Related Documentation, page 59The documentation set for this product strives to use bias-free language. Forpurposes of this documentation set, bias-free is defined as language that does notimply discrimination based on age, disability, gender, racial identity, ethnic identity,sexual orientation, socioeconomic status, and intersectionality. Exceptions may bepresent in the documentation due to language that is hardcoded in the user interfacesof the product software, language used based on RFP documentation, or languagethat is used by a referenced third-party product.IntroductionThe Cisco ISE platform is a comprehensive, next-generation, contextually-based access control solution.It offers authenticated network access, profiling, posture, BYOD device onboarding (native supplicantand certificate provisioning), guest management, device administration (TACACS ), and security groupaccess services along with monitoring, reporting, and troubleshooting capabilities on a single physicalor virtual appliance. Cisco ISE is available on two physical appliances with different performancecharacterization, and also as software that can be run on a VMware server. You can add more appliancesto a deployment for performance, scale, and resiliency.Cisco ISE has a scalable architecture that supports standalone and distributed deployments, but withcentralized configuration and management. It also allows for configuration and management of distinctpersonas and services. This feature gives you the ability to create and apply services where they areneeded in the network, but still operate the Cisco ISE deployment as a complete and coordinated system.For more information about the features that are supported in Cisco ISE 2.1, see Cisco Identity ServicesEngine Admin Guide, Release 2.1.New Features in Cisco ISE, Release 2.1 Ability to Download Core Files and Heap Dumps for Troubleshooting, page 3 Certificate Page Navigation Changes/Enhancements, page 3 Customizable Alarms, page 4 Customizable Dashboard, page 4 Context Visibility, page 4 Easy Connect, page 4 Enable or Disable IPv6 on Each Interface, page 4 Feed Service Enhancements, page 4 Google Chromebook Onboarding Support, page 5Release Notes for Cisco Identity Services Engine, Release 2.12
New Features in Cisco ISE, Release 2.1 Guest Enhancements, page 5 IP SGT Mapping and Mapping Groups, page 5 Livelog Page Enhancements, page 5 Persistent Machine Access Restriction (MAR) Cache, page 6 MDM Enhancements, page 6 Time Interval For Compliance Device ReAuth Query, page 6 NIC Bonding for High Availability, page 6 ODBC Identity Source, page 7 Option to View the Process and Thread Utilization in Cisco ISE, page 7 Posture Enhancements, page 7 Profiler Enhancements, page 7 pxGrid Certificate Template for the Internal Cisco ISE CA, page 8 pxGrid Client Authentication Settings, page 8 Report List for Work Centers, page 8 SAML Identity Source Enhancements, page 8 SAML Signing Certificate, page 9 SAML SSO Support for Certificate Provisioning Portal, page 9 Smart Licensing, page 9 Support for Elliptical Curve Cryptography (ECC) Certificates, page 9 Support for SNMP Traps, page 11 TACACS Device Administration Enhancements, page 11 Third-Party Device Support Enhancements, page 11 , page 11 TrustSec ACI Integration, page 13 TrustSec Matrix Workflow Process, page 13 TrustSec Matrix Enhancements, page 13Ability to Download Core Files and Heap Dumps for TroubleshootingThe show logging CLI command lists the system and application log files. The core files and heapdumps can be listed by using this command. You can now use the copy command to move these files toa repository.Certificate Page Navigation Changes/EnhancementsThe Certificate Authority (CA) Certificates page lists all the certificates related to the internal Cisco ISECA. In previous releases, these CA certificates were present in the Trusted Certificates store and are nowmoved to the CA Certificates page. These certificates are listed node wise in this page. You can expandRelease Notes for Cisco Identity Services Engine, Release 2.13
New Features in Cisco ISE, Release 2.1a node to view all the ISE CA certificates of that particular node. The Administration node has the rootCA, node CA, subordinate CA, and OCSP responder certificates. The other nodes in the deploymenthave the node CA, subordinate CA, and OCSP certificates.Customizable AlarmsYou can customize alarms and configure email notifications to be sent to different recipients for eachalarm. You can also globally define email recipients who will receive notifications for all alarmsconfigured in the system.Customizable DashboardYou can create a new dashboard and add any of the dashlets that you need to the dashboard.You can customize the tabs, dashlets, and layout. You can drag and drop dashlets, export data from adashboard as an Excel or PDF file, and provide role-based access control for the dashlets.Context VisibilityThe Context menus display graphical information about endpoints based on a variety of configurableattributes. Endpoint data can be segmented by features, applications, BYOD, and other categories,depending on your license. The Context menus use a central database, gathers information from databasetables, caches, and buffers, which makes updates to context dashlets and list content very fast. You canuse controls on context visibility pages to filter the data that is displayed, and by applying multiplefilters, progressively narrow the displayed data for particular endpoints.Easy ConnectEasy Connect enables you to easily connect users from a Windows based endpoint to a network in asecured manner and monitor those users by authenticating them through an Active Directory (AD)Domain Controller (DC) and not by Cisco ISE. With Easy Connect, Cisco ISE collects userauthentication information from the Active Directory (AD) Domain Controller. With Easy Connect,Cisco ISE issues a CoA (change of authorization) to the network access device (NAD) after the user isauthenticated by Active Directory. Authenticated users are then shown in the Cisco ISE live sessionsview, and can be queried from the session directory.Enable or Disable IPv6 on Each InterfaceThis release of Cisco ISE provides an option from the CLI to enable or disable IPv6 at the interface level.Feed Service EnhancementsIf you are unable to connect the Cisco ISE deployment to the Cisco feed service, you can download theprofiler policies and OUI updates offline and import them to the Cisco ISE Primary Administration Nodeusing an offline feed update.Release Notes for Cisco Identity Services Engine, Release 2.14
New Features in Cisco ISE, Release 2.1Google Chromebook Onboarding SupportSupport for onboarding of managed Chromebook devices on a corporate network. Chromebook devicesmust download the Cisco Network Setup Assistant extension from the Chrome Web Store to start theonboarding process.NoteCisco ISE supports onboarding of Chromebook devices that are managed by Google console.Unmanaged Chromebook devices are not supported.Guest EnhancementsSupport for SMS Proxy—Guest now supports SMS text through a proxy. The SMS gateway providesHTTP API access to SMS providers, and uses a proxy if a proxy server is defined in Administration System Proxy.From First Logon—A Guest Type can be configured to start a user’s account duration when that userlogs on. This allows a sponsor to create and distribute logon credentials ahead of time, instead of aspeople arrive for a meeting.New SAML Server support—Cisco ISE end-user web portals now support PingIdentity (Cloud),PingFederate (CPE), Azure Active Directory, SecureAuth, and servers running generic SAML 2.0.Single portal for credentialed and SAML SSO login—The login portal can be configured to providethe option to log in with credentials, or to click a link that redirects the user to an SSO portal page. Thelink that the user clicks to redirect to an SSO provider can be customized.Sponsor Approval Filtering—A sponsor can be limited to approving accounts based on the sponsor’semail address, or all pending accounts. Currently this feature is supported only for internal sponsors andSAML SSO sponsors.Workcenter menu—The Guest menu has been removed, and all the options related to Guest portal arelisted under the Guest heading under Work Centers.Shorter default username and password—The guest default username is four alpabetic and passwordis four numeric characters. Short, easy to remember usernames and passwords are adequate forshort-term guests. You can change the username and password length in ISE, if you desire.IP SGT Mapping and Mapping GroupsWhile adding an IP SGT static mapping, you can use an existing mapping group or map the IPaddress/hostname to a SGT individually and specify the SXP VPN groups and target devices.You can import or export the IP SGT static mappings.While adding a mapping group, you can select the SGT and specify the SXP VPN groups and the deviceson which the mappings must be deployed.Livelog Page EnhancementsYou can do the following in the RADIUS, TACACS, and RADIUS Sessions Live Logs page: Hide all or some columnsRelease Notes for Cisco Identity Services Engine, Release 2.15
New Features in Cisco ISE, Release 2.1 Change column width Change the order of columns Filter the data by time range, number of records, refresh interval and also set quick and advancedfiltersPersistent Machine Access Restriction (MAR) CacheCisco ISE stores the MAR cache content, calling-station-ID list, and the corresponding time stamps toa file on its local disk when you manually stop the Cisco ISE application services. Cisco ISE does notstore the MAR cache entries of an instance when there is an accidental restart of its application services.Cisco ISE reads the MAR cache entries from the file on its local disk based on the cache entry time tolive when the Cisco ISE application services get restarted. When the run-time services of an Cisco ISEinstance come up after a restart, Cisco ISE compares the current time of that instance with the MARcache entry time. If the difference between the current time and the MAR entry time is greater than theMAR cache entry time to live, then Cisco ISE does not retrieve that entry from disk. Otherwise, CiscoISE retrieves that MAR cache entry and updates its MAR cache entry time to live.MDM Enhancements Cisco ISE now supports Microsoft Intune and Microsoft SCCM as external MDM servers. Thefollowing versions of SCCM are supported with this release:– Windows 2008 R2 and SCCM 2008 R2– Windows 2012 R2 and SCCM 2012 R2 Attributes from MDM servers can now be published to pxGrid.Time Interval For Compliance Device ReAuth QueryWhen the endpoint is authenticated or re-authenticated, ISE uses a cache to get the MDM variables forthat endpoint. If the age of cached value is older than the value of Time Interval For Compliance DeviceReAuth Query, then ISE makes a device query to the MDM server to get new values. If the compliancestatus changed, then ISE triggers a CoA. The valid range is from 1 to 1440 minutes. The default valueis 1 minute.NoteThis feature is introduced as a part of Release 2.1 Patch 4.NIC Bonding for High AvailabilityCisco ISE supports bonding of two Ethernet interfaces into a single virtual interface to provide highavailability for the physical interfaces. The NIC bonding feature in Cisco ISE does not support loadbalancing or link aggregation features. The bonding of interfaces ensures that Cisco ISE services are notaffected when there is: Physical interface failure Loss of switch port connectivity (shut or failure)Release Notes for Cisco Identity Services Engine, Release 2.16
New Features in Cisco ISE, Release 2.1 Switch line card failureODBC Identity SourceCisco ISE supports Open Database Connectivity (ODBC)-compliant relational databases. The followingdatabase engines are supported: Microsoft SQL Server Oracle PostgreSQL SybaseODBC identity source can be used in an identity store sequence and for Guest and Sponsorauthentications. It can also be used for BYOD flow.You must configure the required stored procedures to authenticate users against an ODBC identitysource. The values that are returned and the tasks that are required of the stored procedure vary based onthe authentication protocol used.While adding an ODBC identity source, you can also add the required attributes and user groups. CiscoISE allows you to fetch the attributes and user groups from ODBC database. You can use these attributesand user groups in the authorization policies.Option to View the Process and Thread Utilization in Cisco ISEA new CLI command, show cpu usage, is introduced in this release. This command lists the CPU usagefor each component such as policy services, PSC, profiler, TACACS , and so on.Posture Enhancements Anti-malware condition to check the installation of an anti-malware program on the client and tocheck if the latest anti-malware definition file of the selected vendor is updated on the client. Itsupports both MAC and Windows OS. USB mass storage Cisco predefined condition to check if a USB mass storage device is connectedto an endpoint. OESIS version 4 to check and remediate endpoint compliance.Profiler Enhancements Profiler related options are grouped under the Profiler Work Center menu (Work Centers Profiler),so that the administrator can easily access all the options related to Profiling service at one location. Supports the NMAP scan action to run the SMB discovery script that is provided by NMAP. Identifies the services running on an endpoint using the service version information probe. Allows the use of custom ports for automatic and manual NMAP scan actions. Skips the NMAP host discovery of known endpoints.Release Notes for Cisco Identity Services Engine, Release 2.17
New Features in Cisco ISE, Release 2.1 Profiles endpoints that are running McAfee agents as corporate devices, by using the McAfeeePolicy Orchestrator (McAfee ePO) security management software. Cisco ISE provides an in-builtNMAP scan action (MCAFeeEPOOrchestratorClientscan) to check if the McAfee agent is runningon an endpoint using NMAP McAfee script on the configured port. Provides the Active Directory probe to improve the fidelity of OS information for Windowsendpoints. Allows the export of probe data from the GUI. Facilitates the offline update of feed services when Cisco ISE is not directly connected to the Ciscofeed server.pxGrid Certificate Template for the Internal Cisco ISE CATo deploy pxGrid service easily, Cisco ISE provides a certificate template that signs an end entity's CSRand has the client and server EKUs on the certificate. From the Certificate Provisioning Portal, you canpaste the CSR text from the pxGrid client and sign the keys using the pxGrid template. Cisco ISE nodescan also use this function for pxGrid certificates. As a Cisco ISE administrator, you can revoke thepxGrid certificates.pxGrid Client Authentication SettingsYou can enable username/password based authentication for pxGrid clients. A pxGrid client can registeritself with the pxGrid controller by sending the username via REST API. The pxGrid controllergenerates a password for the pxGrid client during client registration. The administrator can approve ordeny the connection request.Report List for Work CentersReports that are tagged for different work centers appear in the Reports menu under each Work Center.SAML Identity Source EnhancementsCisco ISE is SAMLv2 compliant and supports all SAMLv2 compliant IdPs that use Base64-encodedcertificates. The IdPs listed below have been tested with Cisco ISE: Oracle Access Manager (OAM) Oracle Identity Federation (OIF) SecureAuth PingOne PingFederate Azure Active DirectorySAML SSO is supported for Guest, Sponsor, My devices, and Certificate Provisioning portal.You can add a load balancer in front of Cisco ISE nodes to simplify the configuration on the IdentityProvider side and optimize the load on ISE nodes.Release Notes for Cisco Identity Services Engine, Release 2.18
New Features in Cisco ISE, Release 2.1While adding an IdP, you can add the attributes and user groups. These attributes and user groups can beused in the authorization policies. You can configure the Identity attribute and logout settings in theAdvanced Settings tab.SAML Signing CertificateFrom the System Certificates page of the Admin Portal, you can set up a certificate for SAML signinguse. SAML certificate can be a wildcard or non-wildcard certificate. SAML certificate is replicated toall the nodes in the deployment.SAML SSO Support for Certificate Provisioning PortalWhile configuring the Certificate Provisioning Portal settings in the Admin portal, you can now selectan identity provider such as Oracle Access Manager as an external identity store to allow for single signon across all Cisco ISE end user portals. When an IdP user launches the Certificate Provisioning Portal,the user is redirected to the IdP login page for authentication. If authentication is successful, the user isredirected back to the Certificate Provisioning Portal.Reports and audit logs include information about users logging in via the SAML SSO as well as otheridentity sources.Smart LicensingCisco offers Smart Licensing, which enable you to monitor ISE software licenses and endpoint licenseconsumption easily and efficiently. When Smart Licensing is activated from Cisco ISE, it monitors theconsumption of licenses and notifies the administrator about the license usage. When licenses areavailable and not consumed, the administrator is notified of available licenses. When consumptionexceeds the amount of licenses available, an alarm is activated and the administrator is notified throughalarms and notifications.When Smart Licensing is activated, the Smart Call Home (SCH) feature is enabled by default. Thisfeature monitors Cisco ISE devices in your network and notifies you via e-mail about critical events. Italso provides real-time alerts with remediation advice for issues that are detected. SCH monitors andsends event notifications for configuration, inventory, Telemetry, crash, hardware, and environmentissues.The Anonymous Reporting feature of SCH provides minimal health information about the Cisco ISEdevices in your network.You can choose to enable only Anonymous Reporting or enable the full set of features offered by SCH.Support for Elliptical Curve Cryptography (ECC) CertificatesCisco ISE CA service now supports client side certificates based on Elliptical Curve Cryptography(ECC) algorithms. ECC offers increased security and better performance than other cryptographicalgorithms while providing the same level of security as other systems with a much smaller key size.Cisco ISE CA service supports ECC certificates for devices connecting through the BYOD flow. Youcan also generate ECC certificates from the Certificate Provisioning Portal.Release Notes for Cisco Identity Services Engine, Release 2.19
New Features in Cisco ISE, Release 2.1If the BYOD flow with Enrollment over Secure Transport (EST) protocol is not working properly, checkthe following: NoteCertificate Services Endpoint Sub CA certificate chain is complete. To check whether the certificatechain is complete:1.Choose Administration System Certificates Certificate Authority CertificateAuthority Certificates.2.Check the check box next to the certificate that you want to check, and then click View.Ensure that the CA and EST services are up and running. If the services are not enabled, go toAdministration System Certificates Certificate Authority Internal CA Settings toenable the CA service.This release of Cisco ISE does not support EST clients to authenticate directly against the EST serverthat resides in Cisco ISE.When an Android or Windows endpoint onboards and the request is for an ECC-based certificate, an ESTflow is triggered internally within Cisco ISE. If you have upgraded to Cisco ISE 2.1 from an ISE version prior to 2.0, replace the ISE Root CAcertificate chain after the upgrade. To do this:1.Choose Administration System Certificates Certificate Management CertificateSigning Requests.2.Click Generate Certificate Signing Requests (CSR).3.Choose ISE Root CA from the Certificate(s) will be used for drop-down list.4.Click Replace ISE Root CA Certificate Chain.The following table lists the operating systems and versions that support ECC along with the curve typesthat are supported. If your devices are not running a supported operating system or on a supportedversion, you can use RSA-based certificates instead.Operating SystemSupported VersionsSupported Curve TypesWindows8 and laterP-256, P-384, and P-512Android4.4 and laterAll curve types (except Android 6.0,which does not support the P-192curve type).NoteNoteWindows 7 and Apple iOS do not natively support ECC for EAP-TLS authentication. This release ofCisco ISE does not support the use of ECC certificates on MAC OS X devices.Release Notes for Cisco Identity Services Engine, Release 2.110Android 6.0 requiresMay 2016 patch tosupport ECCcertificates.
New Features in Cisco ISE, Release 2.1Support for SNMP TrapsSNMP traps help you to monitor the status of Cisco ISE processes. Without accessing the Cisco ISEserver, if you want to monitor the Cisco ISE processes, you can configure a MIB browser as an SNMPhost in Cisco ISE. You can then monitor the status of Cisco ISE processes from the MIB browser.TACACS Device Administration Enhancements The Device Administration Deployment page lists the PSNs in your deployment and allows you tocentrally view the device administration system without referring to each node in the deploymentsection. You can collectively enable the device admin service for multiple PSNs. New fields such as Shared Secret and Retire Shared Secret have been included in the TACACSauthentication settings to authenticate users. Support for authentication protocol services, such as PAP/ASCII, CHAP, and MS-CHAPv1, in FIPSand non-FIPS modes. Support for new common task types such as Shell, WLC, Nexus, and Generic. The TACACS Ports field allows you to configure a maximum of four TCP ports using which CiscoISE nodes and their interfaces listen for TACACS requests.Third-Party Device Support EnhancementsIf a device supports neither dynamic nor static URL redirect, Cisco ISE provides an Auth VLAN bywhich it simulates URL redirect. Auth VLAN is based on unique DHCP/DNS server attributes youdefine in ISE.Additionally, SNMP-based Change of Authorization (CoA) support has been added to support networkaccess devices that lack support for RADIUS CoA.If you enable the ACL (Filter-ID) option while creating an authorization profile, Cisco ISE does notappends ".in" to the ACL for non-Cisco devices. By default,".in" is appended to the ACL for Ciscodevices. When you upgrade to Cisco ISE 2.1 from an earlier release, ".in" is not appended to ACL fornon-Cisco devices.Cisco ISE 2.1 has been tested with the vendor devices listed in the following table:Table 1Vendor Devices Tested With Cisco ISE 2.1Supported/Validated Use CasesDeviceTypeWireless802.1X/ MABProfilerwithout ProfilerCoAwith CoA PostureGuest/BYODVendorCoA TypeURL RedirectTypeAruba 7000,InstantAPRADIUSStatic URL Motorola RFS 4000 RADIUSDynamic URL HP 830RADIUSStatic URL Ruckus ZD 1200RADIUS— ——Release Notes for Cisco Identity Services Engine, Release 2.111
New Features in Cisco ISE, Release 2.1Table 1Vendor Devices Tested With Cisco ISE 2.1Supported/Validated Use CasesURL RedirectType802.1X/ MABProfilerwithout ProfilerCoAwith CoA PostureGuest/BYODRADIUSAuth VLANprovided by ISE RADIUSAuth VLANprovided by ISE SNMPDynamic URL RADIUSAuth VLANprovided by ISE RADIUSAuth VLANprovided by ISE RequiresCoAsupportRequires CoAsupport. For URLredirect, if the wireddevice has no URLredirect, utilizesCisco ISE AuthVLAN. Wirelessdevices have not beentested with AuthVLAN.DeviceTypeVendorCoA TypeWiredHP A5500HP 3800 and 2920(ProCurve)Alcatel 6850Brocade ICX 66101JuniperEX3300-24pFor additional third-party NADs, you must identify the deviceproperties and capabilities and create custom NAD profiles in CiscoISE.1. Brocade switch (ICX6610-24 SW: Version 08.0.20aT7f3) requires a session ID to send a Change of Authorization (CoA) request. Advanced flows suchas BYOD, Guest, and Posture using MAB authentication do not work properly because accouting information and session ID are not collected and henceChange of Authorization (CoA) cannot be issued.NoteIn Cisco ISE, a session cannot be created in the session cache when Network Access Device does not sendcalling station ID in the Access-Request. As a result, scenarios which relies on the session attribute lookuplike guest, posture, BYOD are currently not supported with such network access devices.Threat-Centric NACThreat Centric Network Access Control (TC-NAC) feature enables you to create authorization policiesbased on the threat and vulnerability attributes received from the threat and vulnerability adapters.Threat severity levels and vulnerability assessment results can be used to dynamically control the accesslevel of an endpoint or a user.You can configure the vulnerability and threat adapters to send high fidelity Indications of Compromise(IoC), Threat Detected events, and CVSS scores to Cisco ISE, so that threat-centric access policies canbe created to change the privilege and context of an endpoint accordingly.Cisco ISE supports the following adapters: SourceFire FireAMP QualysRelease Notes for Cisco Identity Services Engine, Release 2.112
System RequirementsNoteOnly the Qualys Enterprise Edition is currently supported for TC-NAC flows.TrustSec ACI IntegrationCisco ISE allows you to synchronize SGTs and SXP mappings with the Internal Endpoint Groups(IEPGs), External Endpoint Groups (EEPGs), and endpoint (EP) configuration of Cisco ApplicationCentric Infrastructure (ACI).Cisco ISE supports packets coming from the ACI domain to the TrustSec domain by synchronizing theIEPGs and creating correlating read-only SGTs in ISE. These SGTs are used to map the endpointsconfigured in ACI and create correlating SXP mappings in ISE. These SGTs are displayed on theSecurity Groups page (with the value "ACI" in the Learned From field). You can view the SXP mappingson the All SXP Mappings page.ACI supports the packets coming from the TrustSec domain to the ACI domain by synchronizing theSGTs and creating correlating EEPGs.TrustSec Matrix Workflow ProcessThe Matrix Workflow feature provides the ability to roll out new policy in a phased manner. A newpolicy is created as the staging matrix. This feature includes an approval workflow, where the stagingpolicy cannot be deployed until it is approved. After approval, the staging matrix can be deployed on alimited set of devices. This is useful for evaluating the policy before full deployment. The staging matrixcan be edited, if required. The deployment can continue on to the next set of devices or to all devices.Once the staging matrix is fully deployed, the staging matrix can be set as the new production matrix.TrustSec Matrix EnhancementsCisco ISE allows you to import and export the egress policy in CSV format. You can export the file to alocal drive or a remote repository. The exported file can be encrypted by using an encryption key.You can include the empty cells (which do not have any SGACL configured) in the exported file. Whenthis option is enabled, the whole matrix is exported and the empty cells are marked with the “Empty”keyword in the SGACL column.While importing the egress policy, you can overwrite the existing policy with the one that you areimporting. If empty cells are included in the imported file, the existing policy in the correspondingmatrix cells will be deleted.System Requirements Supported Hardware, page 14 FIPS Mode Support, page 15 Supported Virtual Environments, page 15 Supported Browsers, page 15 Supported Cipher Suites, page 15Release Notes for Cisco Identity Services Engine, Release 2.113
System RequirementsNote Supported Devices and Agents, page 16 Support for Microsoft Active Directory, page 17 Supported Anti-Virus and Anti-Malware Products, page 17For more details
Support for SMS Proxy —Guest now supports SMS text throug h a proxy. The SMS gateway provides HTTP API access to SMS providers, and uses a proxy if a proxy server is defined in Administration System Proxy. From First Logon—A Guest Type can be configured t
Oct 27, 2014 · Cisco ISR 4400 Series Cisco ISR 4300 Series Cisco ISR 4431 Cisco ISR 4321 Cisco ISR 4451 Cisco ISR 4331 Cisco ISR 4351 Table 1 Cisco IOS XE 3S–to–Cisco IOS Release Number Mapping Cisco IOS XE 3S Release Cisco IOS Release 3.14 15.5(1)S 3.13S 15.4(3)S 3
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
Cisco 2951 2 2 Cisco 3925 4 4 Cisco 3945 4 4 Cisco 3925E 3 3 Cisco 3945E 3 3 Cisco 1841 1 1 Cisco 2801 2 1 Cisco 2811 2 1 Cisco 2821 2 1 Cisco 2851 2 1 Cisco 3825 4 2 Cisco 3845 4 4 Table 1A provides relevant software information Router Chassis Software Release Minimum Software Package Cisco 1921 15.0(1)M2 IP Base
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
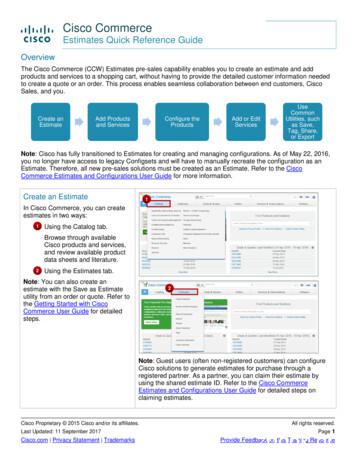
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b
Apr 05, 2017 · Cisco 4G LTE and Cisco 4G LTE-Advanced Network Interface Module Installation Guide Table 1 Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Cisco 4G LTE NIM and Cisco 4G LTE-Advanced NIM SKUs Description Mode Operating Region Band NIM-4G-LTE-LA Cisco 4G LTE NIM module (LTE 2.5) for LATAM/APAC carriers. This SKU is File Size: 2MBPage Count: 18Explore furtherCisco 4G LTE Software Configuration Guide - GfK Etilizecontent.etilize.comSolved: 4G LTE Configuration - Cisco Communitycommunity.cisco.comCisco 4G LTE Software Configuration Guide - Ciscowww.cisco.comCisco 4G LTE-Advanced Configurationwww.cisco.com4G LTE Configuration - Cisco Communitycommunity.cisco.comRecommended to you b