Applications Of SDN In Cisco - Networking Academy
Applications of SDN inCiscoSoftware Defined Networking Webinar SeriesSpeakers: Serges NanfackHostess: Kara Sullivan22 February 2017
Use the Q and A panel toask questions.Welcome to the 3rdsession of theSoftware DefinedNetworking webinarseries! Use the Chat panel tocommunicate with attendeesand panelists. A link to a recording of thesession will be sent to allregistered attendees. Please take the feedbacksurvey at the end of thewebinar. 2015 Cisco and/or its affiliates. All rights reserved.Cisco Confidential2
SD-WAN: iWANOverviewSam ByersSystem Engineer, Cisco 2014 Cisco and/or its affiliates. All rights reserved.Cisco Confidential3
Intelligent WAN Solution /4G-LTEBranchInternetWAASPublicCloudPfRControl and Management AutomationTransportIndependent Consistent operational model Dynamic Application best path basedon policy Load balancing for full utilization ofbandwidth Improved availabilitySimple provider migrations Scalable and modular design IPsec routing overlay designApplicationOptimizationIntelligentPath ControlApplication visibility withperformance monitoringApplication accelerationand bandwidth optimizationSecureConnectivity Certified strong encryption Comprehensive threat defense Cloud Managed Security for securedirect Internet access
Hybrid WAN DesignsTraditional and iWANTraditional HybridIWAN HybridActive/StandbyWAN PathsPrimary With BackupActive/ActiveWAN PathsData CenterTwo IPsec TechnologiesGETVPN/MPLSDMVPN/InternetTwo WAN RoutingDomainsMPLS: eBGP or StaticInternet: iBGP, EIGRP or OSPFRoute RedistributionRoute Filtering Loop PreventionData CenterASR 1000ASR 1000SP VISP ADMVPNGETVPNMPLSInternetOne IPsec OverlayASR 1000ASR 1000DMVPNISP ASP VDMVPNDMVPNMPLSInternetOne WANRouting DomainiBGP, EIGRP, or OSPFISRBranchISRBranch
SD-WAN AutomationPerformance Router (PfR)Automated Discovery, Service Exchange, Peering & Coordination across the WAN DomainLearningNetwork Discoversthe Apps (NBAR2)or based on DSCPNetwork Discoverssite topology,connected networksand ect ApplicationPerformanceSmart Probes fordiscoveryUsing UnifiedPerformanceMonitors (AVCInfrastructure)Also used if thereis no ed oningress on theremote siteWAN Edgepeers, learns linkperformance(per DSCP),Sendsperformancefeedback to PeersManagescongestion (localCAC, RemoteCAC*)
SDN Orchestration with APIC-EMAddressing the whole branch, not just the WAN.Customized Deploymentwith SDNPrime AppCustomTemplatesPrescriptive Deploymentwith SDNBranch ServicesPartnersAutomationCisco IWAN AppModelTemplatesPlug & Play WorkflowWhole isioningSecurityPolicyPath SelectionPolicyApplicationPolicyBranch-Level PolicyIWANSwitchingWirelessREST APIsAPIC-EM Services orySvcDevice Abstraction LayerOnePK/OpenflowCLIPnPSvcAPIC-EM
iWAN Branch Services RoutersISR4000 Series - IWAN AX Ready, Next Generation BranchAPPLIANCE LEVEL PERFORMANCE Service-Aware Dataplane Resilient Service Virtualization Multi-gigabit FabricAPPLICATION CENTRIC App/User policy-driven deployment APIC-EM Automation: deploy in minutes Pay-as-you-grow Up-to-75% cost savingsINTEGRATED IWAN SERVICES IOS Firewall, VPN, IPSec, PfRV3, NBAR2,AVC, AppNav, VRF, MPLS Scalable on-chip service provisioningISR44511-2GbpsISR4431500Mbps/1GbpsISR 4351200/400MbpsISR 4331100/300MbpsISR432150/100Mbps
iWAN Aggregation Border RoutersASR1000 - IWAN AX ready, high performance routersCOMPACT, POWERFUL ROUTER Line-rate performance 2.5G to 200G withservices enabled Crypto performance from 2G to 60G Flexible I/O: SPAs and Ethernet LCsBUSINESS-CRITICAL RESILIENCY Separate control and data planes Hardware and software redundancy In-service software upgradesASR1001-XModular ASR1006 2.5G Upgradeable to 5G, 10G, 20G Up to 8G Crypto ThroughputASR1002-X Modular, Redundant up to 200G Up to 60G Crypto ThroughputINTEGRATED IWAN SERVICES IOS Firewall, VPN, IPSec, PfRV3, NBAR2,AVC, AppNav, VRF, MPLS Scalable on-chip service provisioning 5G Upgradeable to 10G, 20G, 36G Up to 4G Crypto Throughput
Introduction to ACIDana TurnerConsulting Systems Engineerdanaturn@cisco.com
WebOutside(Tenant VRF)AppDBQoSQoSQoSFilterServiceFilterAPICACI FabricNon-Blocking Penalty Free OverlayApplication PolicyInfrastructureController
ACI and Today’s 3-Tier applicationsAppNetworkProfile“The Application / iceCould be many VMsP Defined PolicyDBQoSPFilterMostly physicalresourcesCould be mix of physical/virtual machines13
Application Network Profiles (ANP) – what’s that ?Application Network profiles are a group of EPGs and thepolicies that define the communication between them.Application Network ProfileEPG - WEBEPG - APPEPG - DB POLICY icies
ACI Fabric provides the next generationof analytic capabilitiesPetStore EventTriggered Eventsor QueriesActions:No new hosts or VMsEvacuate hypervisorsRe-balance clustersPer application, tenants, andinfrastructure: Health scoresLatencyAtomic countersResource consumptionPetStore DevPetStore ProdPetStore QA Leaf 1 and 2 Spine 1 – 3 Atomic counters Leaf 2 and 3 Spine 1 – 2 Atomic counters Leaf 3 and 4 Spine 2 – 3 Atomic countersAPICIntegrate with workload placement ormigrationVXLANPer-Hop VisibilityPhysical andVirtual as One
Northbound Rapid integration with existingAPImanagement rManagementOrchestrationFrameworks OpenStack Tenant- and application-awareObject-OrientedCentralized AutomationRESTful XML / JSONSouthboundAPI Publish data model Open source Enables application portability*Only straight chains supported at FCSOpen EcosystemFrameworkComprehensiveProgrammability andSystem Access
APICACI SpineNodesInsiemeFabricControllerACI LeafNodes ACI Fabric provides:‒Decoupling of endpoint identity, location, and associated policy, all of which are independent from the underlying topology‒Full normalization of the ingress encapsulation mechanism used: 802.1Q VLAN, IETF VXLAN, IETF NVGRE‒Distributed Layer 3 gateway to ensure optimal forwarding for Layers 3 and 2‒Support for standard bridging and routing semantics without standard location constraints (any IP address anywhere)‒ Service insertion and redirection‒Removal of flooding requirements for IP control plane (ARP, GARP)
Each node will beassigned loopback IPaddress(es) advertisedthrough IS-ISIP fabric withintegratedoverlayIP un-numbered40 Gb links ACI Fabric is based on an IP fabric supporting routing to the edge with an integrated overlay for host routing‒ All end-host (tenant) traffic within the fabric is carried through the overlay The fabric is capable of supporting an arbitrary number of tiers and/or partial mesh if required Why choose an integrated overlay?‒ Mobility, scale, multi-tenancy, and integration with emerging hypervisor designs‒ Data traffic can now carry explicit meta data that allows for distributed policy (flow-level control without requiring flow-levelprogramming)APIC
App TierAApp rServerChain“Security 5” Helps enable administrativeseparation between applicationtier policy and service definitionStage 1 .instinst . ServiceAdminStage NinstinstFirewallLoad BalancerendService ProfilebeginServiceGraph“Security 5” Chain Defined APIC as central point of networkcontrol with policy coordination Automation of service bringup/tear-down throughprogrammable interfacePolicy RedirectionProviders Elastic service insertionarchitecture for physical andvirtual services
Device Package Service automation requires avendor device package. It is a zipfile containingDevice Specification dev type “f5” service type “slb” param name “vip” dev ident “210.1.1.1” validator “ip” hidden “no” locked “yes” APIC – Policy ElementDevice ModelAPIC Device specification (XML file) Device scripts (Python)APIC Script InterfaceDevice-Specific Python Scripts APIC interfaces with the deviceusing device Python scripts APIC uses the deviceconfiguration model provided inthe package to pass appropriateconfigurations to the deviceDevice Interface: REST/CLIScript EngineAPIC NodeService Device
NetworkAdminVirtual IntegrationAPICAPIC Integrated gateway forVLAN, VxLAN, andNVGRE networks fromvirtual to physical Normalization for NVGRE,VXLAN, and VLANnetworks Customer not restricted byACI FabricVLANVXLANVMwareMicrosoftRed ANNVGREVLANVXLANESXHyper-VKVMVMwareMicrosoftRed HatVLANPHYSICALSERVER
ACI Operational Simplicity – GUI Drag and DropAccelerating Time to Deploy ApplicationEasy to Use, Policy Driven, Automated DeploymentDrag & DropTenantTenant Sales Deployed Network VRF Deployed Firewall DeployedApps DeployedACI rityPolicy“Now we can spin upSalesan environmentin 17 minutes(from 4.5 months)”Application- Vince Spina, DC Architect
Unified point of data center network automationand management:Layer anagement̶ Application-centric network policies̶ Data model-based declarative provisioning̶ Application, topology monitoring, and troubleshootingOpen RESTful API̶ Third-party integration (Layer 4 - 7 services, storage,compute, WAN, etc.)APICStorage SMEServer SME Network SME̶ Image management (Spine / Leaf)̶ Fabric inventory Single APIC cluster supports one million endpoints, 200,000 ports, 64,000 tenants Centralized access to all fabric information - GUI,CLI, and RESTful APIs Extensible to compute and storage managementPolicy-BasedProvisioningSecurity SMEApp. SMEOS SME
Topology discoverythrough LLDP usingACI-specific TLVs (ACIOUI)Loopback and VTEP IPaddresses allocated from“infra VRF” through DHCPfrom APICAPICAPIC ClusterAPICAPIC ACI Fabric supports discovery, boot, inventory, and systems maintenanceprocesses through the APIC‒Fabric discovery and addressing‒Image management‒Topology validation through wiring diagram and systems checks
NEXUS 9000 ACI PLATFORMSACI LEAVESACI SPINESACI 3128TX95049396PX9336PQNX-OS and ACIChoice of FabricArchitecturesBest Price / Performance10G / 40G / 100G
Shiyue Cheng, CCIEConsulting Systems EngineerCommercial East Area 2010 Cisco and/or its affiliates. All rights reserved.
Technology can connect us, empower us, and drive us. At Meraki we believeby simplifying powerful technology we can free passionate people to focuson their mission and reach groups previously left in the darkness.Technology that simply works 2010 Cisco and/or its affiliates. All rights reserved.27
Cisco Meraki: a complete cloud-managed networking solution- Wireless, switching, security, MDM, phones and cameras centrally managed over the web- Built from the ground up for cloud management- Integrated hardware, software, and cloud servicesLeader in cloud-managed networking- Among Cisco’s fastest-growing portfolios: over 100% annual growth- Tens of millions of devices connected worldwideRecognized for innovation- Gartner Magic Quadrant, InfoWorld Technology of the Year, CRN Coolest TechnologiesTrusted by thousands of customers worldwide: 2010 Cisco and/or its affiliates. All rights reserved.28
Security - UTMNG Firewall, Client VPN,Site to Site VPN, IDS/IPS,Anti-Malware, GeoNetworkingFirewallNAT/DHCP, 3G/4GCellular,ApplicationControlIntelligent WAN(IWAN)Web Caching, TrafficShaping, ContentFiltering 2010 Cisco and/or its affiliates. All rights reserved.29
Enabling transport independence, intelligent path control, application optimization, and secure connectivity for multi-sitedeployments.TransportIndependence IPSec overlay (Auto VPN) Scalable (Cloud Controller) Traffic distribution over multiplepathways (Internet, cellular,MPLS-to-VPN failover) 2010 Cisco and/or its affiliates. All rights reserved.ApplicationOptimizationIntelligent PathControl App visibility & control (Merakidashboard, group-basedpolicies, traffic analytics) Dynamic Path Selection Uplink chosen by link latency,data loss, etc. (performancebased routing) Application QoS & bandwidthoptimization (Traffic shaping)SecureConnectivity Intuitive, automatic,scalable VPN solution toconnect remote branchsites (Auto VPN) Uplink assigned by trafficprotocol, subnet, source,destination, etc. (PbR, policybased routing)30
Transport IndependenceConsistent deployment models simplify operationsIWAN HybridInternet 4GData CenterData CenterMX 400MX 400SP VISP AAuto VPNAuto VPNMPLSInternetIWAN Dual InternetData CenterMX 400MX 400MX 400ISP BISP AMX 400ISP AISP CDSLCableAuto VPNAuto VPNAuto VPNAuto VPNInternetInternetInternetInternet4GBranch 2010 Cisco and/or its affiliates. All rights reserved.BranchBranch31
Dual-active path: Dual-active VPN Dual-active VPN & MPLSDynamic Path Selection:Ensures that the best VPN tunnel is used basedWAN 2Secure VPN tunnel (active)Latency / loss thresholdWAN 1Secure VPN tunnel (active)Latency / loss thresholdon latency and loss performance metricsPolicy-based routing (PbR) :Allows uplinks to be intelligently assigned basedon traffic protocol, subnet, source, destination,etc.Data 2010 Cisco and/or its affiliates. All rights reserved.Based on L3 / L4 categorization, this datanormally travels out WAN 1 (PbR), butMX detects optimal path is WAN 2 basedon latency / loss on WAN 132
Q&A 2014 Cisco and/or its affiliates. All rights reserved.Cisco Confidential33
Interested in Joining Cisco Networking Academy? Go to netacad.com Scroll Down toGet Started Click Find an Academy Need Help?karsulli@cisco.com 2015 Cisco and/or its affiliates. All rights reserved.Cisco Confidential34
Cisco Meraki: a complete cloud-managed networking solution - Wireless, switching, security, MDM, phones and cameras centrally managed over the web - Built from the ground up for cloud management - Integrated hardware, software, and cloud services Leader in cloud-managed networking - Among Cisco’s fastest-growing portfolios: over 100% annual .
sdn.301 security protocol3(sp3) sdn.401 security protocol4(sp4) sdn.701 messagesecurity protocol sdn.702 directoryspecs forusewith msp key management sdn.601 keymanagement profile sdn.902 kmp definitionof servicesprovided bykmase sdn.903 kmp servicesprovided bykmase sdn,906 kmp traffickey attribute negotiation access control sdn.801 .
SDN 40-24-100C aND SDN 40-24-480C DImENSIoNS Catalog Number Dimensions - mm (in) h w D SDN 5-24-100C 123.0 (4.85) 50.0 (1.97) 111.0 (4.36) SDN 10-24-100C 123.0 (4.85) 60.0 (2.36) 111.0 (4.36) SDN 20-24-100C 123.0 (4.85) 87.0 (3.42) 127.0 (4.98) SDN 5-24-480C 123.0 (4.85) 50.0 (1.97) 111.0 (4.36) SDN 10-24-480C 123.0 (4.85) 60
Cisco ASA 5505 Cisco ASA 5505SP Cisco ASA 5510 Cisco ASA 5510SP Cisco ASA 5520 Cisco ASA 5520 VPN Cisco ASA 5540 Cisco ASA 5540 VPN Premium Cisco ASA 5540 VPN Cisco ASA 5550 Cisco ASA 5580-20 Cisco ASA 5580-40 Cisco ASA 5585-X Cisco ASA w/ AIP-SSM Cisco ASA w/ CSC-SSM Cisco C7600 Ser
SDN Waypoint Enforcement Insight #1: 1 SDN switch Policy enforcement Insight #2: 2 SDN switches Fine-grained control Legacy devices must direct traffic to SDN switches Ensure that all traffic to/from an SDN-controlled port always traverses at least one SDN switch
Supported Devices - Cisco SiSi NetFlow supported Cisco devices Cisco Catalyst 3560 Cisco 800 Cisco 7200 Cisco Catalyst 3750 Cisco 1800 Cisco 7600 Cisco Catalyst 4500 Cisco 1900 Cisco 12000 Cisco Catalyst 6500 Cisco 2800 Cisco ASR se
Cisco Nexus 1000V Cisco Nexus 1010 Cisco Nexus 4000 Cisco MDS 9100 Series Cisco Nexus 5000 Cisco Nexus 2000 Cisco Nexus 6000 Cisco MDS 9250i Multiservice Switch Cisco MDS 9700 Series Cisco Nexus 7000/7700 Cisco Nexus 3500 and 3000 CISCO NX-OS: From Hypervisor to Core CISCO DCNM: Single
Cisco Nexus 7706 Cisco ASR1001 . Cisco ISR 4431 Cisco Firepower 1010 Cisco Firepower 1140 Cisco Firepower 2110 Cisco Firepower 2130 Cisco FMC 1600 Cisco MDS 91485 Cisco Catalyst 3750X Cisco Catalyst 3850 Cisco Catalyst 4507 Cisco 5500 Wireless Controllers Cisco Aironet Access Points .
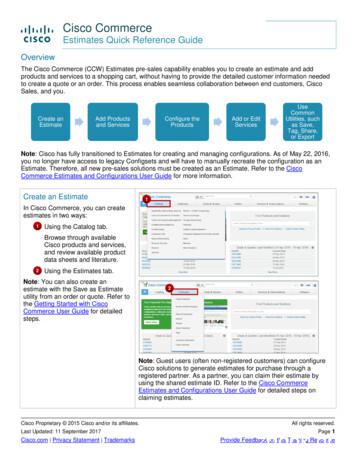
Sep 11, 2017 · Note: Refer to the Getting Started with Cisco Commerce User Guide for detailed information on how to use common utilities for a record in Cisco Commerce. See Cisco Commerce Estimates and Configurations User Guide for more information.File Size: 664KBPage Count: 5Explore furtherSolved: Cisco Serial Number Lookups - Cisco Communitycommunity.cisco.comHow to view and/or update your CCO profilewww.cisco.comSolved: How do I associate a contract to my Cisco.com .community.cisco.comHow do I find my Cisco Contract Number? - Ciscowww.cisco.comPower calculator tool - Cisco Communitycommunity.cisco.comRecommended to you b